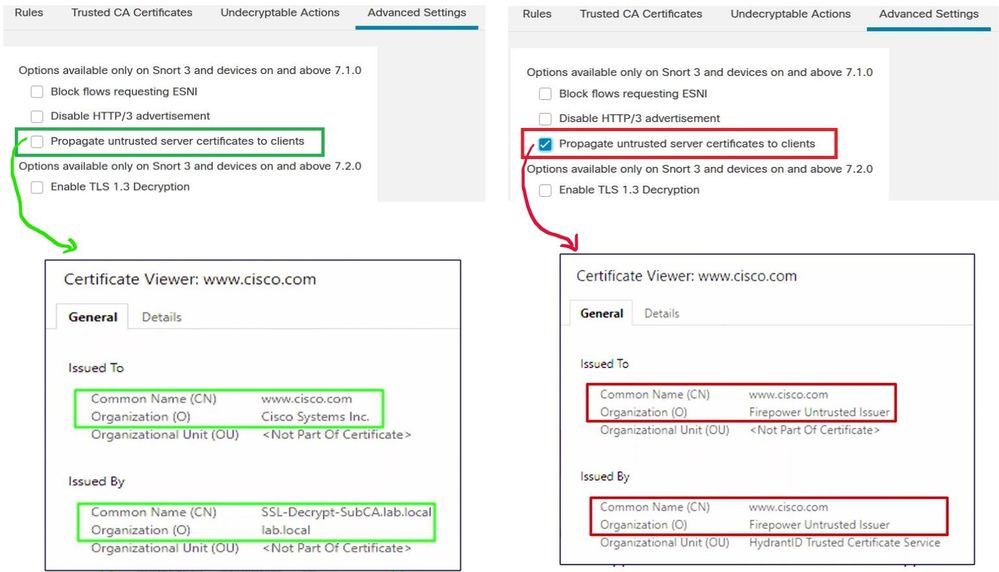
On Firepower Threat Defense, there is an option in the Advanced Setting of SSL policy called " Propagate untrusted server certificates to clients "
This option applies only to traffic matching a Decrypt - Resign rule action.
What does this option mean?
Like the web browser, The firewall comes with a predefined set of Trusted CAs .
There is a scenario where the firewall does not trust the server certificate it gets from the external server because the CA that signed it is not present in the predefined trusted CA certificates list.
In this case, using the decrypt resign action in an SSL policy rule, the server certificate can be presented to the client into different ways.
Either it can send the server certificate as trusted because the FTD spoofed the original server certificate and signs it with your internal CA, in this case we want the client actually do not notice that FTD is sending untrusted server certificate.
Or the other option is to force Firepower to create voluntarily a spoofed certificate that will not be trusted by the clients because the FTD is not trusting the server certificate, so the client is aware about that.
At the right with the option "propagate untrusted server certificate to the clients" UNCHECKED, the client receive a server certificate signed by internal CA on the FTD. The client will not notice that.
At the left, we propagate untrusted server certificate to the client by checking the option , in this case Firepower just create a self-signed certificate that will not be trusted by the clients to warn the end user that the Firewall is not trusting the server certificate. The client will notice that and an error of untrusted certficate will be displayed in the web browser.