Introduction
This document describes a scenario where user wants to implement routing between 2 Site to Site VPN Tunnels.
Hardware Used
ASA 5520
Topology
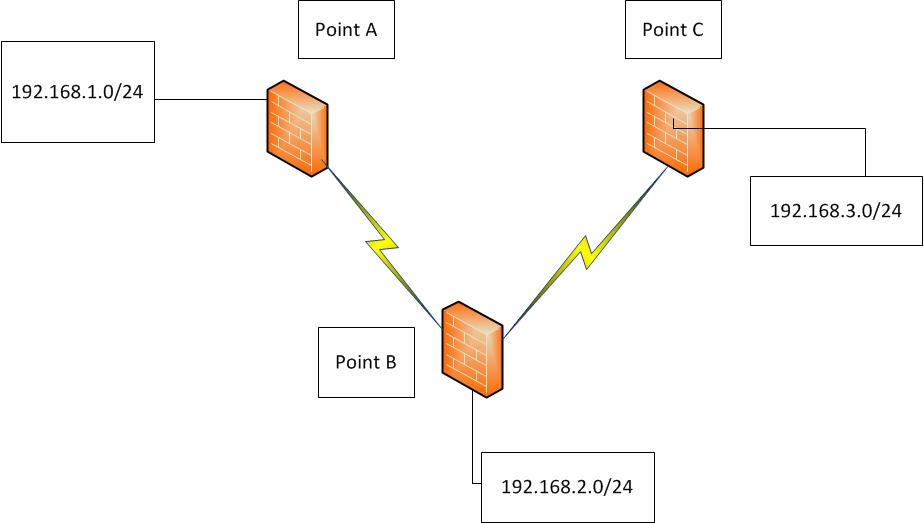
Problem
All Firewalls used are Cisco ASA 5520.The VPN tunnels between Point A and Point B, Point B and Point C are up.User have enabled Same security level intra interface permit command.
How do user enable traffic originating from LAN Subnets behind Point A to reach LAN Subnets behind Point C without having to create a seperate tunnel between Point A and Point C.User has been trying to establish routing between two Site to Site vpn tunnels, both of which are terminating on the same outside interface of Cisco ASA.
Solution
2 spoke networks connected with L2L VPN will communicate with each other:
- User need to configure the "same-security-traffic permit intra-interface"
- User need to configure the remote networks A and C to the "crypto map x match address <ACL>" ACLs which will enable the traffic to flow from the one L2L VPN to the other L2L VPN
- User need to configure appropriate NAT rules for traffic flow.
You need to do NAT0 and VPN rules on each site to allow the traffic.The configurations will look something like below.User already probably have an existing NAT0 configuration and certainly the L2L VPN configuration.
Site A
access-list NAT0 remark NAT0 rule for SiteA to SiteC traffic
access-list NAT0 permit ip 192.168.1.0 255.255.255.0 192.168.3.0 255.255.255.0
nat (inside) 0 access-list NAT0
access-list L2L-VPN-CRYPTO-SITEB remark Interesting traffic for SiteA to SiteC
access-list L2L-VPN-CRYPTO-SITEB permit ip 192.168.1.0 255.255.255.0 192.168.3.0 255.255.255.0
Here
NAT0 = This ACL is to be used in the NAT0 rules that will exempt SiteA to SiteC traffic from NAT
nat = NAT0 configuration line
L2L-VPN-CRYPTO-SITEB = This ACL in the L2L-VPN configurations defines that the traffic from SiteA LAN to SiteC LAN should use the existing L2L-VPN towards SiteB
Site B
access-list OUTSIDE-NAT0 remark NAT0 rule for SiteA to SiteC traffic
access-list OUTSIDE-NAT0 permit ip 192.168.1.0 255.255.255.0 192.168.3.0 255.255.255.0
nat (outside) 0 access-list OUTSIDE-NAT0
access-list L2L-VPN-CRYPTO-SITEA remark Traffic for SiteA to SiteC through existing Tunnel between A-B
access-list L2L-VPN-CRYPTO-SITEA permit ip 192.168.3.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list L2L-VPN-CRYPTO-SITEC remark Traffic for SiteA to SiteC through existing Tunnel between B-C
access-list L2L-VPN-CRYPTO-SITEC permit ip 192.168.1.0 255.255.255.0 192.168.3.0 255.255.255.0
Here
OUTSIDE-NAT0 = This ACL is used in the NAT0 rules which will exempt SiteA to SiteC traffic from NAT. Here it is attached to the "outside" interface as the traffic will be entering and leaving through that interface at SiteB
nat = NAT0 configuration line
L2L-VPN-CRYPTO-SITEA (and SITEC) = Are the ACLs in the L2L-VPN configurations that defines that the traffic from SiteA LAN to SiteC LAN should use the existing L2L-VPN connections.
Site C
access-list NAT0 remark NAT0 rule for SiteC to SiteA traffic
access-list NAT0 permit ip 192.168.3.0 255.255.255.0 192.168.1.0 255.255.255.0
nat (inside) 0 access-list NAT0
access-list L2L-VPN-CRYPTO-SITEB remark Interesting traffic for SiteC to SiteA
access-list L2L-VPN-CRYPTO-SITEB permit ip 192.168.3.0 255.255.255.0 192.168.1.0 255.255.255.0
Here
NAT0 = This ACL is used in the NAT0 rules which will exempt SiteC to SiteA traffic from NAT
nat = NAT0 configuration line
L2L-VPN-CRYPTO-SITEB = This ACL in the L2L-VPN configurations defines the traffic from SiteC LAN to SiteA LAN should use the existing L2L-VPN towards SiteB
Source Discussion
Routing Traffic between Two Site to Site VPN Tunnels