- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- SecureX and the Evolution of Security Orchestration Automation and Response - Meet the Authors FAQ
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
01-27-2021
05:33 PM
- edited on
01-27-2021
08:07 PM
by
Hilda Arteaga
![]()
- Introduction
- Q: What's the difference between Netflow and IPFIX. Why does GUI on Cisco products still have Netflow and not IPFIX, if IPFIX is a newer technology?
- Q: What book would you recommend before CyberOps Professional OCG becomes available?
- Q: What do you advise as the starting path for Ethical hacking?
- Q: Some businesses are averse to using Cloud-based products that require giving access to their environment. Does SecureX support an on-prem cloud connector? Also does SecureX integrate with 3rd party security products like firewalls?
- Q: Does SecureX support 3rd party security products?
- Q: Which version of Python is in workflow?
- Related Information
This event had place on Wednesday 20th, Janaury at 9:30 hrs PDT
Introduction
In this session, Cisco Press authors discuss the evolution of Security Orchestration Automation and Response (SOAR). And how cybersecurity professionals have traditionally tried to use different security solutions and tools to streamline security operations in three key areas: threat and vulnerability management, incident response, and security operations automation. Then they discuss how solutions like Cisco Secure X have gone beyond the traditional Security Information Event Management (SIEM) and SOAR solutions in a more modern approach to accelerate time to detect and investigate threats, while maintaining contextual awareness.
Join the security top experts to learn more about how these new capabilities allow organizations to accelerate threat investigations and incident management by aggregating and correlating global intelligence and local context in one view. And how Cybersecurity analysts can now use pre-built workflows aligned to common use cases for building your own workflow to eliminate friction in your processes and automate routine tasks. In addition, they will mention some key content of their book Cisco Next-Generation Security Solutions: All-in-one Cisco ASA Firepower Services, NGIPS, and AMP.
This event provides an opportunity to interact with the authors in real-time and learn more about them, their story, the story behind their publications, and how they became renowned experts.
You can find the slides of the session here, and the video here.
 Aaron Woland is a Principal Engineer in Cisco’s Advanced Threat Security & Integrations group and works with Cisco’s largest customers all over the world. His primary job responsibilities include security design, solution enhancements, standards development, advanced threat solution design, endpoint security, and futures. He has over 20 years of experience in the IT industry. Aaron has collaborated on several Cisco Press publications and he has published many papers and design guides. Aaron is a Hall of Fame Elite Member for distinguished speakers at Cisco Live. He holds several certifications: GHIC, GCFE, GSEC, Certified Ethical Hacker, MCSE, VCP, CCSP, CCNP, CCDP, and a CCIE (#20113) among others.
Aaron Woland is a Principal Engineer in Cisco’s Advanced Threat Security & Integrations group and works with Cisco’s largest customers all over the world. His primary job responsibilities include security design, solution enhancements, standards development, advanced threat solution design, endpoint security, and futures. He has over 20 years of experience in the IT industry. Aaron has collaborated on several Cisco Press publications and he has published many papers and design guides. Aaron is a Hall of Fame Elite Member for distinguished speakers at Cisco Live. He holds several certifications: GHIC, GCFE, GSEC, Certified Ethical Hacker, MCSE, VCP, CCSP, CCNP, CCDP, and a CCIE (#20113) among others. Omar Santos is an active member of the cyber security community, where he leads several industry-wide initiatives and standards bodies. His active role helps businesses, academic institutions, state and local law enforcement agencies, and other participants dedicated to increasing the security of their critical infrastructures. Omar is the author of more than twenty (20) books and video courses, as well as numerous white papers, articles, and security configuration guidelines and best practices. He is a principal engineer of the Cisco Product Security Incident Response Team (PSIRT), where he mentors and leads engineers and incident managers during the investigation and resolution of cyber security vulnerabilities.
Omar Santos is an active member of the cyber security community, where he leads several industry-wide initiatives and standards bodies. His active role helps businesses, academic institutions, state and local law enforcement agencies, and other participants dedicated to increasing the security of their critical infrastructures. Omar is the author of more than twenty (20) books and video courses, as well as numerous white papers, articles, and security configuration guidelines and best practices. He is a principal engineer of the Cisco Product Security Incident Response Team (PSIRT), where he mentors and leads engineers and incident managers during the investigation and resolution of cyber security vulnerabilities. Cisco Next-Generation Network Security Solutions gives visibility and control to anticipate and meet threats, wherever they appear. And it introduces these products and solutions, and offers expert guidance for planning, deploying, and operating them
Cisco Next-Generation Network Security Solutions gives visibility and control to anticipate and meet threats, wherever they appear. And it introduces these products and solutions, and offers expert guidance for planning, deploying, and operating themYou can download the slides of the presentation in PDF format here.
Q: What's the difference between Netflow and IPFIX. Why does GUI on Cisco products still have Netflow and not IPFIX, if IPFIX is a newer technology?
A: NetFlow is a technology created by Cisco that allows you to collect and analyze network flow metadata. The IPFIX is a vendor neutral implementation of NetFlow. It was based on NetFlow version 9. Most of the Cisco products support both NetFlow and IPFIX.
Q: What book would you recommend before CyberOps Professional OCG becomes available?
A: There are no current other books. That’s why Omar suggest to do hands on exercises, but the unfortunate reality is that there are no books for the professional certification yet.
Q: What do you advise as the starting path for Ethical hacking?
A: [Aron Woland] I used to teach the Certified Ethical Hacker course / certification and I always liked the CeH - as a sort of - broad view of what's avail. Omar may have other thoughts, too. Besides the basic OS, and scripting skills and then going into Capture the flags are great verbal points from Omar.
Q: Some businesses are averse to using Cloud-based products that require giving access to their environment. Does SecureX support an on-prem cloud connector? Also does SecureX integrate with 3rd party security products like firewalls?
A: There is no on-prem version today.
Q: Does SecureX support 3rd party security products?
A: Yes it does. Many out of the box, and more get added regularly. For Orchestration, as long as it supports a standard API you can work with it (basically).
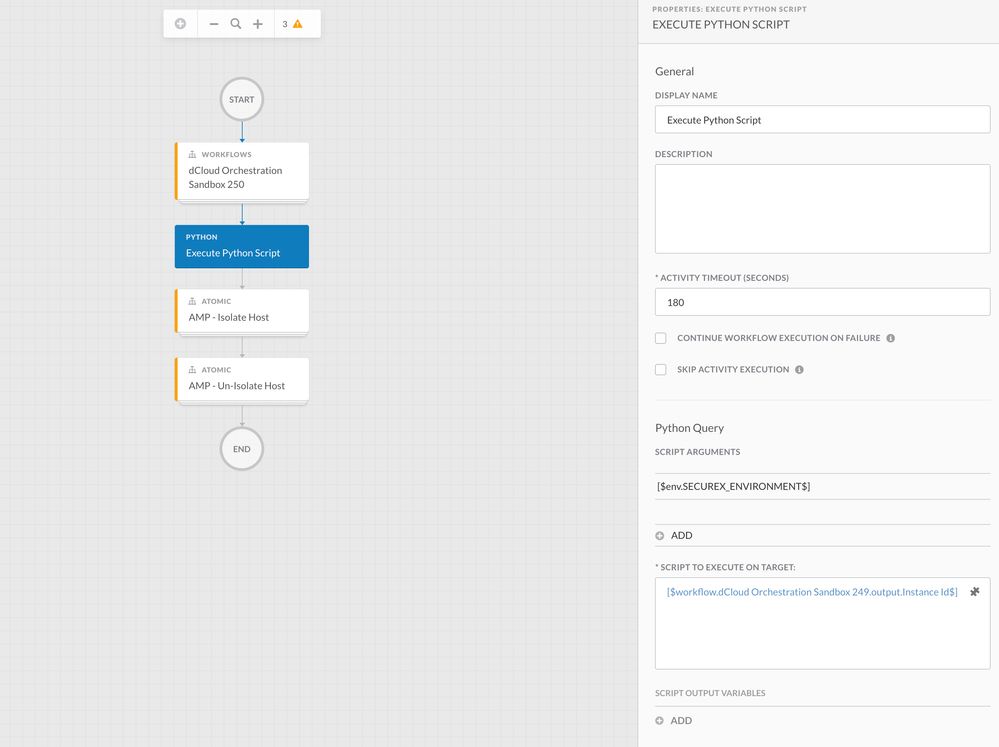
Q: Which version of Python is in workflow?
A: There is “no version of python” in workflows. Workflows are built with Atomic Actions and they are the constructs to create workflows.
This documentation provides more detail https://ciscosecurity-sx-00-integration-workflows.readthedocs-hosted.com/en/latest/orchestration/getting_started.html
If you execute a Python script in workflow, it will be on the target system. So whatever the python version that is installed on the target system:
Related Information
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: