- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- simple GET VPN configuration with IOS CA Server
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 10-08-2010 05:08 AM
Introduction
A configuration exemple of GET VPN using Certificates as the authentication method between GM and KS and IOS Server as CA Authority.
C1 is the KS, C2 and C3 are the GM.
You may find attached the base configuration (with all the MPLS backbone + VPN configured, as well as client routing/adressing). and the final config of all the routers.
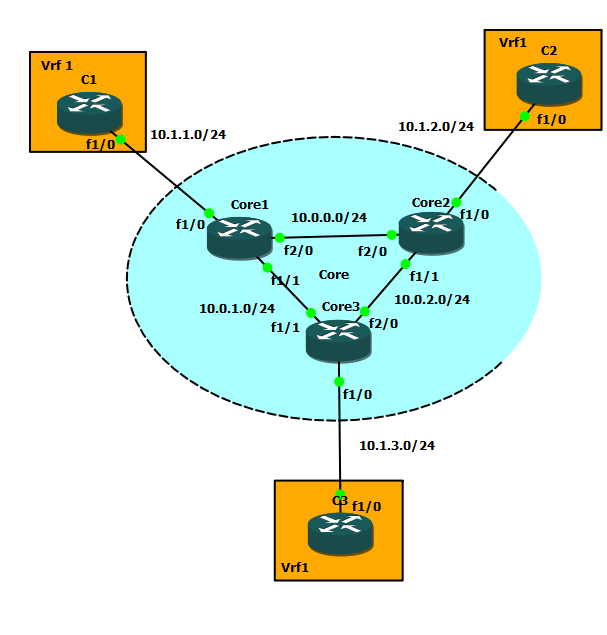
Configuration of the IOS CA-Server
First, we'll configure the CA Server on C1 and enroll the routers on it:
!we generage a rsa key pair for the CA
c1(config)#crypto key generate rsa general-keys label carsa exportable modulus 512 % They will be replaced. % The key modulus size is 512 bits % Generating 512 bit RSA keys, keys will be exportable...[OK] c1(config)# *Oct 4 17:24:40.303: %SSH-5-DISABLED: SSH 1.5 has been disabled *Oct 4 17:24:41.227: RSA key size needs to be atleast 768 bits for ssh version 2 c1(config)# *Oct 4 17:24:41.243: %SSH-5-ENABLED: SSH 1.5 has been enabled !We export the keys to nvram but you may export it elsewhere to restore your CA server on another router
c1(config)#crypto key export rsa carsa pem url nvram: 3des cisco123 % Key name: carsa Usage: General Purpose Key Exporting public key... Destination filename [carsa.pub]? Writing file to nvram:carsa.pub Exporting private key... Destination filename [carsa.prv]? Writing file to nvram:carsa.prv c1(config)#ip http server !SCEP enrollment needs HTTP server on
c1(config)#crypto pki server carsa c1(cs-server)#database url nvram: c1(cs-server)#database level names !We store the certificate name in addtion to crypto material (by default)
core1(cs-server)#issuer-name CN=c1 L=MYDESK C=BE ! L = location, C = country c1(cs-server)#no shut %Some server settings cannot be changed after CA certificate generation. % Please enter a passphrase to protect the private key % or type Return to exit Password: cisco123 !remember this password, you'll need it in SCEP challenge
Re-enter password: cisco123 % Generating 1024 bit RSA keys, keys will be non-exportable...[OK] % Exporting Certificate Server signing certificate and keys... % Certificate Server enabled. c1(cs-server)# *Oct 4 17:36:57.087: %PKI-6-CS_ENABLED: Certificate server now enabled. c1(cs-server)#do write Building configuration... [OK] c1(cs-server)#exi c1(config)#
Enrollment of the routers on our IOS CA Server
c2(config)#crypto ca trustpoint carsa ! No revocation check as we didn't defined any CRL in the IOS CA config
c2(ca-trustpoint)#revocation-check none c2(ca-trustpoint)#enrollment url http://10.1.1.2:80 c2(ca-trustpoint)#exi c2(config)#crypto ca authenticate carsa Certificate has the following attributes: Fingerprint MD5: F9060FED EFDD437B 0971B86E 2CC79D65 Fingerprint SHA1: 9261C779 35420504 12F77C07 B0EF5938 66F3DC48 % Do you accept this certificate? [yes/no]: yes Trustpoint CA certificate accepted. c2(config)#crypto ca enroll carsa % % Start certificate enrollment .. % Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it. !password dedfined when 'no shutting' the ca-server
Password: cisco123 Re-enter password: cisco123 % The subject name in the certificate will include: c2 % Include the router serial number in the subject name? [yes/no]: no % Include an IP address in the subject name? [no]: no Request certificate from CA? [yes/no]: yes % Certificate request sent to Certificate Authority % The 'show crypto pki certificate verbose carsa' commandwill show the fingerprint. c2(config)# ! The following logs indicate that our router is requesting a certificate
*Oct 4 17:46:27.135: CRYPTO_PKI: Certificate Request Fingerprint MD5: 4D9971C8 F02B5822 B4062ABE E4FD370A *Oct 4 17:46:27.147: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 1CD7E7FA B4A4016E 5A7D4F9E FEDD64BD D3234946 c2(config)#
Do the same for C3.
Now we have to accept the certificate request on the IOS CA Server
C1#sh crypto pki server carsa requests Enrollment Request Database: Subordinate CA certificate requests: ReqID State Fingerprint SubjectName -------------------------------------------------------------- RA certificate requests: ReqID State Fingerprint SubjectName -------------------------------------------------------------- Router certificates requests: ReqID State Fingerprint SubjectName -------------------------------------------------------------- 1 pending B50C87B6E5AD25927EFDB485EF0003ED hostname=C2 C1#crypto pki server carsa grant 1 C1#sh crypto pki server carsa requests Enrollment Request Database: Subordinate CA certificate requests: ReqID State Fingerprint SubjectName -------------------------------------------------------------- RA certificate requests: ReqID State Fingerprint SubjectName -------------------------------------------------------------- Router certificates requests: ReqID State Fingerprint SubjectName -------------------------------------------------------------- 1 granted B50C87B6E5AD25927EFDB485EF0003ED hostname=C2
And after some second we should see on C2's console:
*Oct 4 18:17:32.151: %PKI-6-CERTRET: Certificate received from Certificate Authority
You may note that if you enrolled the two routers you whould have had 2 pending request.
Here the CA Server is the KS, but if it were a GM, we should have enrolled to itself.
GETVPN Configuration
Now we can configure the GETVPN, starting by configuring a isakmp policy using rsa-sig and other parameters that we want, on the KS & GMs routers:
C1(config)#crypto isakmp policy 100
C1(config-isakmp)#auth rsa-sig C1(config-isakmp)#hash sha C1(config-isakmp)#group 5 C1(config-isakmp)#exi
Configuration of KS Router:
C1(config)#crypto ipsec transform-set TSET1 esp-aes !creation of an IPSEC transform set and profile
C1(cfg-crypto-trans)#mode transport C1(cfg-crypto-trans)#exi C1(config)#crypto ipsec profile P1
C1(ipsec-profile)#set transform-set TSET1 C1(ipsec-profile)#exi C1(config)#ip access-list extended private-traffic !The ACL that will be pushed to GM defined ciphered traffic
C1(config-ext-nacl)#deny udp any eq 848 any eq 848 ! we do not want GDOI to be ciphered
C1(config-ext-nacl)#permit ip 10.1.0.0 0.0.255.255 10.1.0.0 0.0.255.255 C1(config-ext-nacl)#exi C1(config)#crypto gdoi group GETVPN1 C1(config-gdoi-group)#identity number 1234 ! Should be the same on GMs
C1(config-gdoi-group)#server local C1(gdoi-local-server)#rekey ? ! In a real environment, define your rekeying options for better security
address Define the rekey packet format algorithm Set the rekey encryption algorithm authentication Identify the rekey authentication keypair lifetime Define the rekey lifetime retransmit Define the rekey retransmission parameters transport Specify the rekey distribution method C1(gdoi-local-server)#sa ipsec 1 C1(gdoi-sa-ipsec)#profile P1
C1(gdoi-sa-ipsec)#match address ipv4 private-traffic C1(gdoi-sa-ipsec)#exi C1(gdoi-local-server)#address ipv4 10.1.1.2 !IP interface used for GDOI
C1(gdoi-local-server)#exi C1(config-gdoi-group)#exi
Now we can configure the GMs, configuration is more easy:
C2(config)#crypto gdoi group GETVPN1 C2(config-gdoi-group)#identity number 1234 C2(config-gdoi-group)#server address ipv4 10.1.1.2 C2(config-gdoi-group)#exi C2(config)#crypto map GETMAP 10 gdoi % NOTE: This new crypto map will remain disabled until a valid group has been configured. C2(config-crypto-map)#set group GETVPN1 C2(config-crypto-map)#exi C2(config)#int F1/0 C2(config-if)#crypto map GETMAP
Now make some traffic to trigger up the VPN (such as a ping between GM)
Verification commands
Some verification commands
On KS:
C1#sh crypto gdoi GROUP INFORMATION Group Name : GETVPN1 (Multicast) Group Identity : 1234 Group Members : 2 IPSec SA Direction : Both Group Rekey Lifetime : 86400 secs Rekey Retransmit Period : 10 secs Rekey Retransmit Attempts: 2 IPSec SA Number : 1 IPSec SA Rekey Lifetime: 3600 secs Profile Name : P1 Replay method : Count Based Replay Window Size : 64 SA Rekey Remaining Lifetime : 3300 secs ACL Configured : access-list private-traffic Group Server list : Local C1#sh crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 10.1.1.2 10.1.2.2 GDOI_IDLE 1005 ACTIVE 10.1.1.2 10.1.3.2 GDOI_IDLE 1006 ACTIVE IPv6 Crypto ISAKMP SA !!!!!!!!!!!! C2#sh crypto gdoi ipsec sa SA created for group GETVPN1: FastEthernet1/0: protocol = ip local ident = 10.1.0.0/16, port = 0 remote ident = 10.1.0.0/16, port = 0 direction: Both, replay: Disabled
C1#sh crypto gdoi ks members Group Member Information : Number of rekeys sent for group GETVPN1 : 0 Group Member ID : 10.1.2.2 Group ID : 1234 Group Name : GETVPN1 Key Server ID : 10.1.1.2 Group Member ID : 10.1.3.2 Group ID : 1234 Group Name : GETVPN1 Key Server ID : 10.1.1.2 C1#sh crypto gdoi ks po C1#sh crypto gdoi ks policy Key Server Policy: For group GETVPN1 (handle: 2147483650) server 10.1.1.2 (handle: 2147483650): # of teks : 1 Seq num : 0 kek policy : FALSE TEK POLICY (encaps : ENCAPS_TRANSPORT) spi : 0xFA94E73B access-list : private-traffic transform : esp-aes alg key size : 16 sig key size : 0 orig life(sec) : 3600 remaining life(sec) : 411 tek life(sec) : 3600 elapsed time(sec) : 3189 override life (sec): 0 antireplay window size: 64 C1#sh crypto session Crypto session current status Interface: FastEthernet1/0 Session status: UP-IDLE Peer: 10.1.2.2 port 848 IKE SA: local 10.1.1.2/848 remote 10.1.2.2/848 Active Interface: FastEthernet1/0 Session status: UP-IDLE Peer: 10.1.3.2 port 848 IKE SA: local 10.1.1.2/848 remote 10.1.3.2/848 Active
On GMs:
C2#sh crypto gdoi gm Group Member Information For Group GETVPN1: IPSec SA Direction : Both ACL Received From KS : gdoi_group_GETVPN1_temp_acl Group member : 10.1.2.2 vrf: None Registration status : Registered Registered with : 10.1.1.2 Re-registers in : 3001 sec Succeeded registration: 1 Attempted registration: 5 Last rekey from : 0.0.0.0 Last rekey seq num : 0 Multicast rekey rcvd : 0
C2#sh crypto ipse sa interface: FastEthernet1/0 Crypto map tag: GETMAP, local addr 10.1.2.2 protected vrf: (none) local ident (addr/mask/prot/port): (10.1.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (10.1.0.0/255.255.0.0/0/0) current_peer 0.0.0.0 port 848 PERMIT, flags={origin_is_acl,} #pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10 #pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 10.1.2.2, remote crypto endpt.: 0.0.0.0 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/0 current outbound spi: 0xFA94E73B(4204062523) PFS (Y/N): N, DH group: none inbound esp sas: spi: 0xFA94E73B(4204062523) transform: esp-aes , in use settings ={Transport, } conn id: 1, flow_id: SW:1, sibling_flags 80000000, crypto map: GETMAP sa timing: remaining key lifetime (sec): (303) Kilobyte Volume Rekey has been disabled IV size: 16 bytes replay detection support: N Status: ACTIVE C2#sh crypto session Crypto session current status Interface: FastEthernet1/0 Session status: UP-ACTIVE Peer: 0.0.0.0 port 848 IKE SA: local 10.1.2.2/848 remote 10.1.1.2/848 Active IPSEC FLOW: permit ip 10.1.0.0/255.255.0.0 10.1.0.0/255.255.0.0 Active SAs: 2, origin: crypto map C2#sh crypto gdoi gm acl Group Name: GETVPN1 ACL Downloaded From KS 10.1.1.2: access-list permit ip 10.1.0.0 0.0.255.255 10.1.0.0 0.0.255.255 ACL Configured Locally:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: