On Cisco Secure Firewall there are two ways to do SSL Decryption (two actions in the SSL Policy).
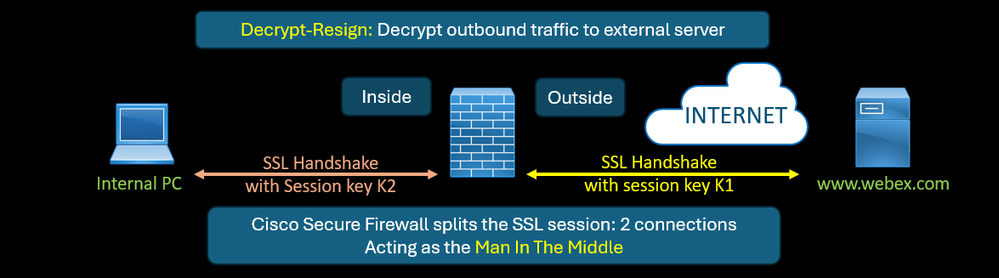
Decrypt-Resign: for outbound connection (from an inside PC to an external server).
- Used for traffic to external servers, not under your control, you dont have control of the private key of the certificate
- Cisco Secure Firewall splits the original session into two: client<—>FW<—>server with two session (encrypted) keys, one between the internal client and the firewall, and another between the firewall and the external server
- The original server certificate is spoofed and resigned by Cisco Secure Firewall.
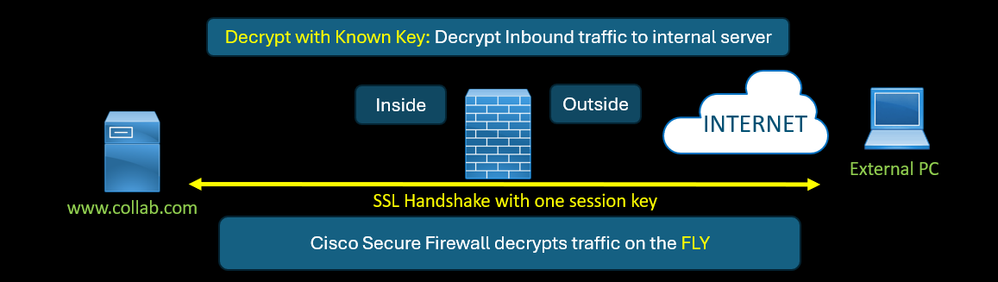
Decrypt with Known Key: for inbound connection (from an external PC to your internal server).
- Used for traffic coming to your internal servers, under your control, you have access to the private key of the certificate
- Server’s Private Key and certificate are uploaded to Cisco Secure Firewall.
- Cisco Secure Firewall decrypts the client-server taffic on the fly with the same session (encrypted) key.
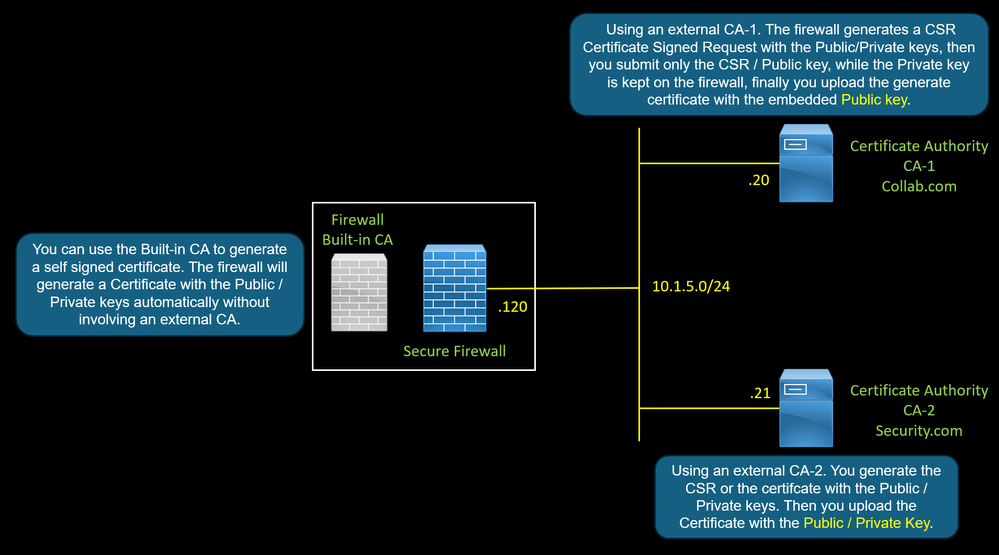
For the Outbound Traffic, The firewall uses a certificate with the role of CA Certificate of Authority to perform SSL Decryption for outbound traffic.
There are three methods to generate this certificate.
1. Method 1 : You can use a self-signed certificate. The firewall will generate a Certificate with the Public / Private keys automatically without involving an external CA.
2. Method 2 : Using an external CA. The firewall generates a CSR Certificate Signed Request with the Public/Private keys, then you submit only the CSR / Public key, while the Private key is kept on the firewall, finally you upload the generate certificate with the embedded Public key.
3. Method 3 : Using an external CA. You generate the CSR or the certifcate with the Public / Private keys. Then you upload the Certificate with the Public / Private Key.