- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- TEAP for Windows 10 using Group Policy and ISE TEAP Configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 08-25-2020 05:29 PM
With Windows 10 build 2004 and ISE 2.7 Patch 2 TEAP (EAP Chaining) is now supported. It seems currently TEAP can only be configured manually for non-domain joined workstations. This is due to the TEAP option not available under the group policy configuration, for domain managed workstations. However I was able to push a group policy that enables TEAP, by exporting a group policy, changing some XML content related to the Windows Supplicant TEAP configuration, then importing again.
The process below outlines how to configure a TEAP group policy and push out to domain joined machines. The following is required:
- All machines updated to Windows 10 Build 2004
- ISE upgraded to 2.7 Patch 2
- Domain joined machine (Used to generate XML config) that has the following:
- Wired autoconfig service enabled
- Network Adapter authentication tab configurable
- Root CA certificate for trust installed (Root CA that signed the RADIUS certificate ISE will present)
- Domain joined machine or group of machines to push group policy to
- Domain controller (Example was on Server 2016 Standard with latest updates installed (2020-07 Cumulative Update (KB4565511) and 2020-07 Servicing Stack Update (KB4565912))
Generate XML File
1. Login to domain joined machine that will be used to generated the XML and ensure the defined options above have been enabled/imported
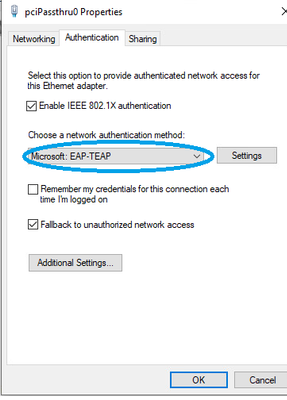
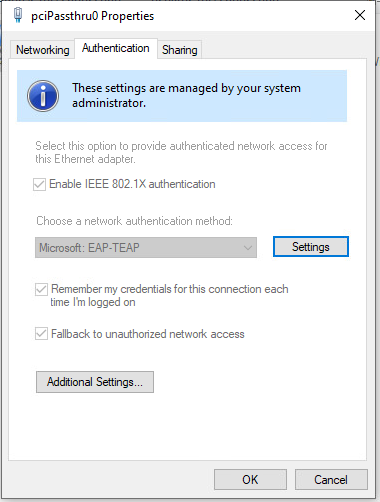
2. Under the Authentication tab on the Network Adapter properties set the Choose a network authentication drop down to Microsoft EAP-TEAP.
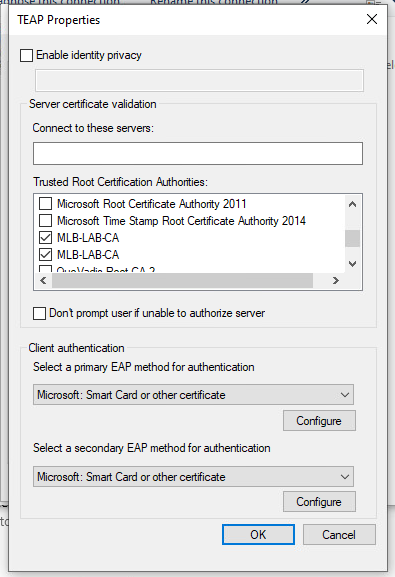
3.Click the Settings button next to the drop down
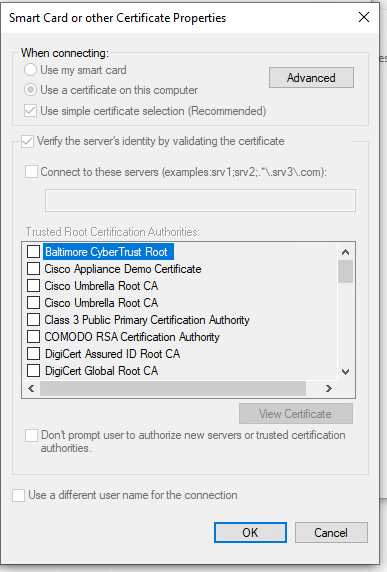
• Leave Enable identity privacy enabled with anonymous as the identity.
• Select the check mark next to the root CA server(s) under Trusted Root Certification Authorities that are used to sign the certificate for EAP authentication on the ISE PSN
• Under Client Authentication, set both the primary and secondary EAP method for authentication to Microsoft: Smart Card or other certificate
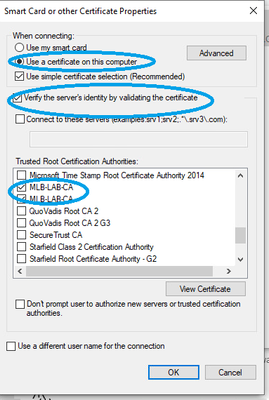
4.Under each EAP method drop down, click the Configure button.
• Use a certificate on this computer is the default setting.
• Leave Verify the server’s identity by validating the certificate enabled.
• Connect to these servers is optional (just like above).
• Select the check mark next to the root CA server(s) under Trusted Root Certification Authorities that are used to sign the certificate for EAP authentication on the ISE PSN.
• Click OK.
• Repeat for secondary method.
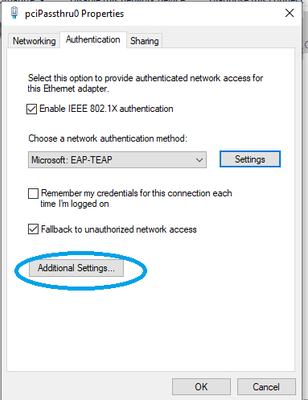
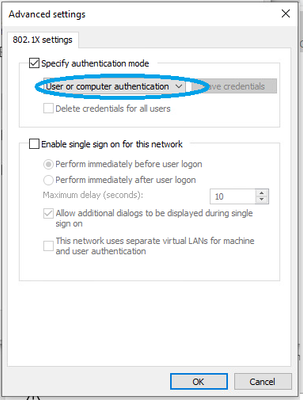
5. Return to Authentication tab and click the Additional Settings button.
• Enable Specify authentication mode
• Set the drop down to the appropriate setting. I am using User or computer authentication so that both are authenticated (computer on boot to login screen, computer and user when user logs in).
• Click OK.
• Click OK to exit the LAN connection properties.
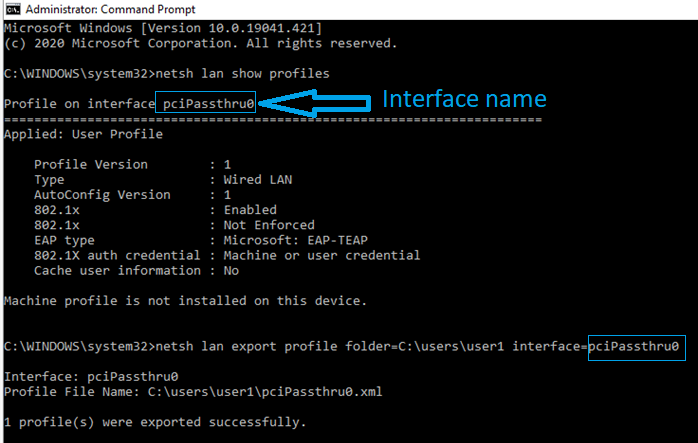
6. Open a command prompt as administrator and execute the following commands:
netsh lan show profiles - Note down the interface name
netsh lan export profile folder=PATH_TO_FOLDER interface="INTERFACE_NAME"
An XML file will be generated with the required TEAP configuration. The interface name will be the name of the file in the location path set.
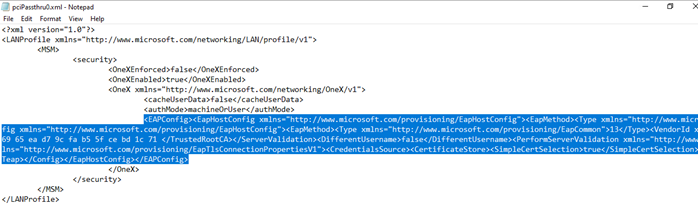
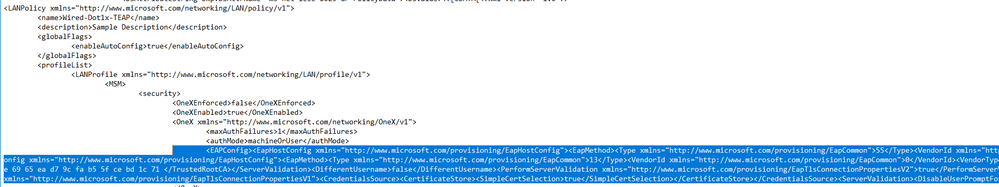
7. Open up the XML file and copy everything within <EAPConfig> ..... </EAPConfig> Store in a text file to be made available later
Create Group Policy to push TEAP configuration to Workstations
***To note the group policy is applied to all machines, you can configure this policy to only apply to certain groups.
1.Login to Domain Controller and open up Group Policy Management
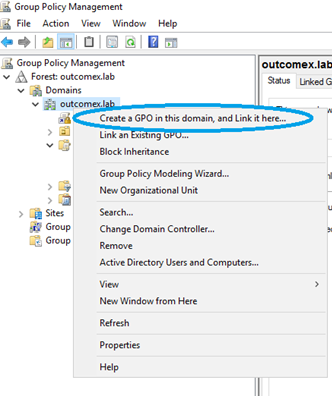
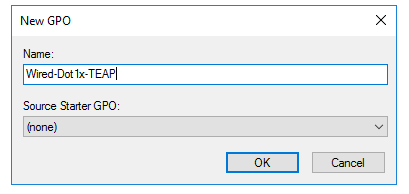
2. Right click on the domain and select Create a GPO in this domain, and link it here
Name the new GPO
3. Right click on the newly created Policy and click Edit, navigate to:
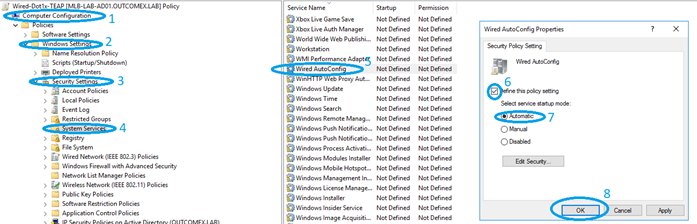
- Computer Configuration -> Policies -> Windows Settings ->Security Settings -> System Services
- Double Click Wired AutoConfig service, select the define this policy setting and set the service startup mode mode to Automatic
4. Navigate to:
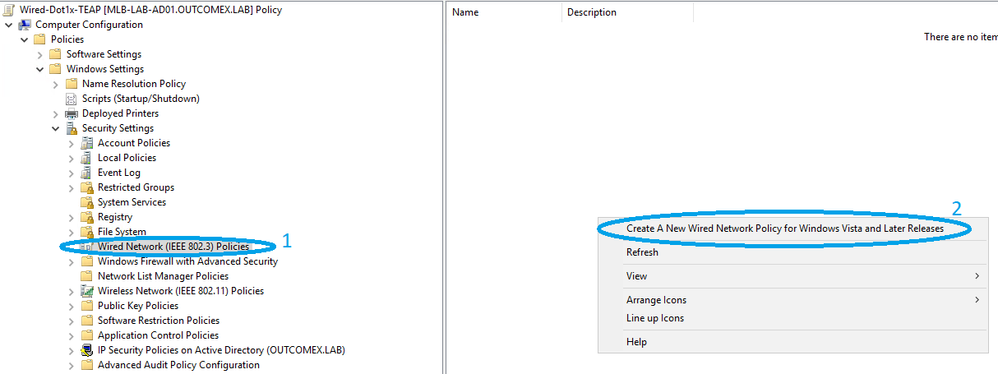
- Computer Configuration -> Policies -> Windows Settings ->Security Settings -> Wired Network (IEEE 802.3) Policies
- Right click in right area and select Create A New Wired Network Policy for Windows Vista and Later Releases
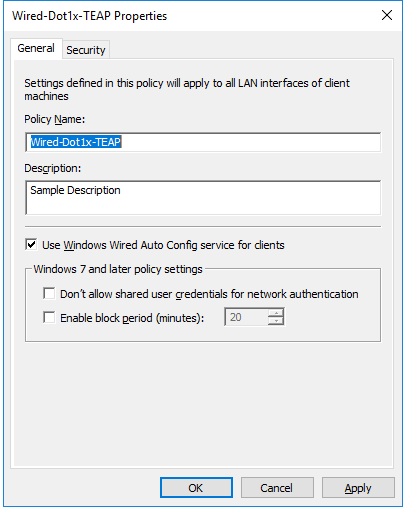
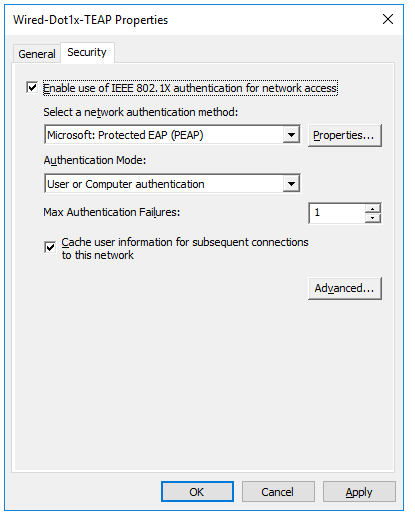
5. Name the Policy and move to Security tab and select the following (This is dummy configuration)
- Select tick box Enable use of IEEE 802.11X authentication for network access
- Select PEAP as the network authentication method
- Select User or Computer authentication as the authentication mode
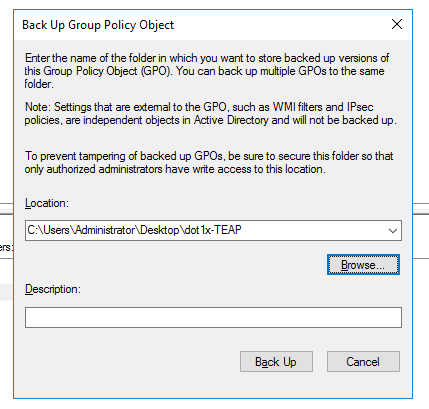
6. Right click on the Group Policy created and select Back Up...
Select the location to save the backup and click Backup
7. Navigate to the folder where the backup was saved and open up the Backup.xml file in notepad.
8. Replace the <EAPConfig> ... </EAPConfig> section with the generated EAPConfig created and saved previously:
Existing
Replaced
Ensure you save the notepad file
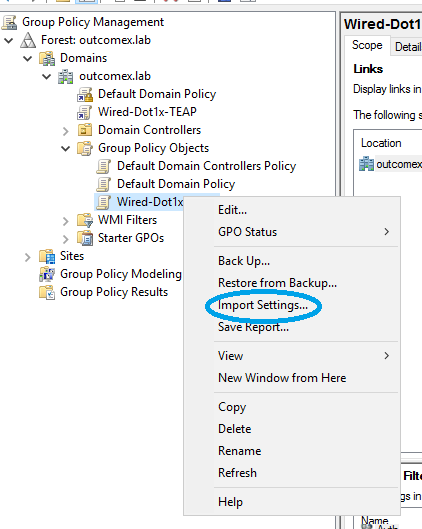
9. Right click on the Group Policy again and select Import Settings
- Don't worry about backing up the policy this has already been completed, click next -> next
- Select the location where the backup was created previously and contains the edited Backup.xml file
- Select Next -> Finish -> OK
- You will see the GPO status is Succeeded
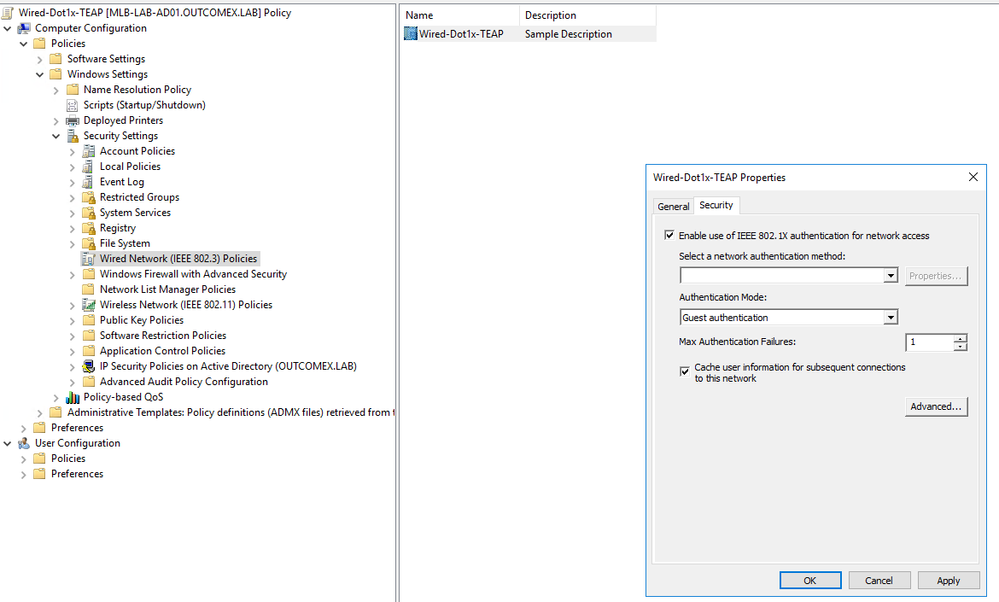
10. Navigate back to the Wired Network (IEEE 802.3) Policies and edit the Policy that was created. You will see that it will not display the TEAP configuration because it is unsupported but will display some similar to this:
Confirming Domain Joined Workstation has received TEAP configuration:
1. Login to test workstation that has a user & machine certificate and has been enabled to receive the group policy. Open up a cmd and execute the following command:
gpupdate /force - This will force a group policy update
gpupdate /scope /computer /v - This confirms the group policy has been applied, look under Applied Group Policy Objects:
2. Navigate to the wired network adapter under Authentication and you will see Microsoft: EAP-TEAP is selected as the authentication method. If you navigate around the rest of the Authentication settings will match what was created via the XML.
Configure ISE for TEAP
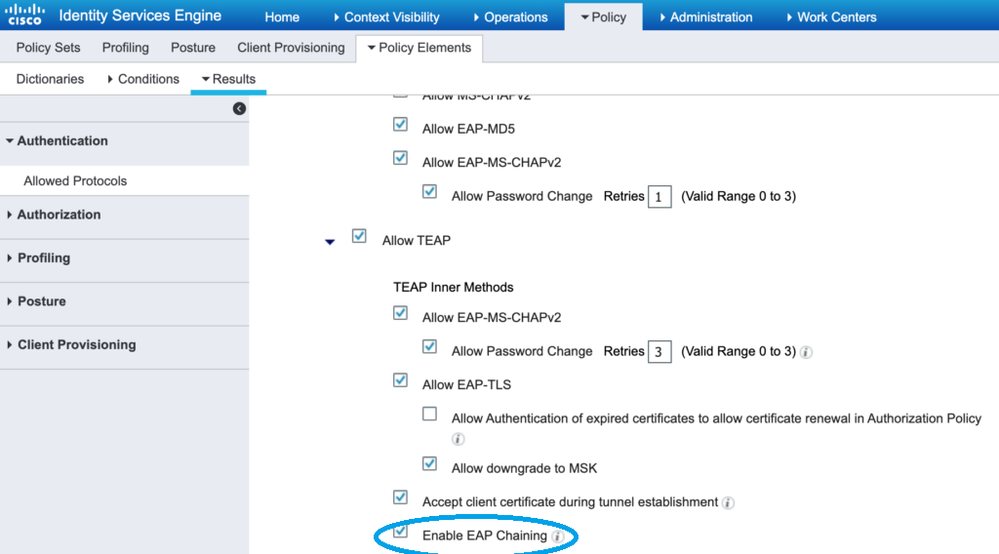
1. Navigate to Policy -> Policy Elements -> Results -> Authentication -> Allowed Protocols, Select the Allowed Protocols service that is used in your existing Policy.
- Ensure Allow TEAP is ticked, and Enable EAP Chaining tick box is also selected
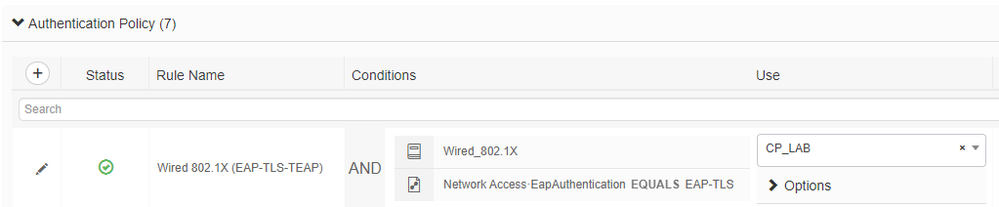
2. Navigate to your wired dot1x policy and ensure their is an EAP-TLS authentication Policy
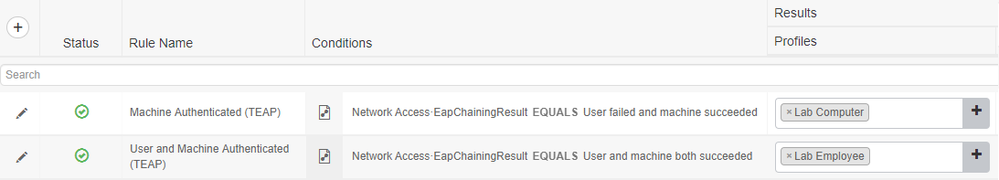
3. Create two authorization policies. The first rule will be the machine authentication. The condition will check if the machine is authenticated but the user is not. The second rule will be the user and machine authentication. The condition for this rule will check if the user and the machine has successfully authenticated. Both rules use the Network Access · EapChainingResult attribute.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For wireless:
I created a SSID inside the GPO, then I followed the same proccess for Ethernet.
Write the following to gother the XML eap configuration from your PC:
netsh wlan export profile folder=c:\WIFI-TEAP name=SSID_NAME
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@AminRadin when I did this the SSID showed up on WIndows 11 as "New Profile" - even though the XML file had the SSID name.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I follow setup steps 10 as below in windows server 2019 :
10. Navigate back to the Wired Network (IEEE 802.3) Policies and edit the Policy that was created.
You will see that it will not display the TEAP configuration because it is unsupported but will display some similar to this:
but i still see it display TEAP configuration , it's not empty , any possible reason!?
or how can i modify my setting in windows server 2019 ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@alexchang014 you cannot modify these settings once you import the XML. This is a limitation of Windows Server 2019 and lack of support for TEAP GPO. When using Windows Server 2019, the only way to effectively update these parameters is by importing the XML file as described in this document.
The better alternative to modify these settings via Windows Server GPO GUI is to spin-up a Windows Server 2022 VM -- join it to your domain -- and then permit this server to manage your domain's Group Policy. This way, you can create / modify / delete this EAP-TEAP settings using GPO - and EAP-TEAP will be included in the dropdown.
We ended up doing this and it worked fine. To be clear, this server's sole purpose was to update the GPO for our organization with the latest features offered by Windows Server 2022.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is there a working solution for Windows 10 TEAP?
If we disable the root-ca on the GPO, the TEAP config is applied to Windows10 device, but it's asking user to accept the certificate also if the internal root-CA is on the trusted root of the User/Computer cert store.
It's not clear if we export the xml from a windows10 device and import it on the GPO it will work or not, unable to find any documentation on both Cisco/Microsoft.
thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
And like I mentioned you can always deploy a Windows Server 2022 and manage the GPO from there all via the GUI, no XML import required.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Shorty we're telling that Windows Server 2022 GPO is not working for Win10 Devices. Works with Win11, but not Win10.
Are you having the GPO working with Win10 Client and Windows Server 2022 using the GPO GUI?
Very strange
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
CiscoU9834 can you please, try to have a look to my issue ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I had the same issue. Deployed EAP-TEAP to hundreds of Windows 11 devices but then I couldn’t push the same configuration out to Windows 10 devices..
Our Windows server admin ended up using WMI Filters to deploys a separate GPO configuration for Windows 10 devices which configures EAP-TLS. When these devices get updated to Windows 11 they will automatically receive the EAP-TEAP configuration.
Create these in the WMI filter section in GPO and Apply to the GPO on the WMI filter section on the bottom:
Win 10 WMI filter
select * from Win32_OperatingSystem where Version like "10.0.1%" and ProductType="1"
Win 11 WMI filter
select * from Win32_OperatingSystem where Version like "10.0.2%" and ProductType="1"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello anyone, can help me please?
I have tested TEAP on domain machine and working fine then I generated the XML File. when i import the XML File on the GPO my Wi-Fi SSID get erased in the GPO view. My laptop receives the GPO, but no actual Wi-Fi profiles
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @ashashut,
I'd faced the same issue. The workaround I could found was installing RSAT on a Windows 10 22h2 machine and create the GPO through there, without editing the XML file directly.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hey, we found a workaround for ws2019, it works for both win10 and win11. You need to configure the correct connection on your computer, export the xml and then create a powershell script e.g. netsh wlan add profile filename=\\xxx\xxx\xxx\wireless_example.xml user=all. The xml configuration file and powershell script must be on a sharable drive so that any computer in the domain can access it. Then in the GPO we create a policy for the computer->policies->windows settings and create a powershell script run on startup. Over a period of a few weeks no problems.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@a.sali Did you ever get a meaningful response from Microsoft?
We got it to work with Ethernet now(with the XML Export ....), but unfortunately this method is not working for the WiFi-Profile.
As you described the GPO is not applying with W10 with correctly configured TEAP-settings. If we uncheck the trusted CAs, the GPO is applying, but that is not a solution.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: