- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Threat Centric NAC Service: Integrate Cisco ISE with Secure Endpoint
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 08-02-2024 02:23 PM
- Introduction
- Cisco ISE + Cisco Secure Endpoint Integration Architecture.
- Cisco ISE Standalone and Cisco Secure Endpoint Integration Flow
- Cisco ISE Distributed Deployment and Cisco Secure Endpoint Integration Flow
- Policies
- Components Used
- Cisco Secure Endpoint
- Cisco ISE Configuration
- Enabling Threat Centric NAC Service
- Configuring Policies
- Validation
Introduction
Cisco Identity Services Engine (ISE) is aligned with Zero Trust. Cisco Zero Trust is a comprehensive approach for securing access across your users, devices, applications, and environment. Cisco Zero Trust involves 3 solutions called Workforce, Workplace and Workloads. Workplace is about giving right privileges/access to the users and devices connecting to the network over wired, wireless, VPN and/or 5G. Workforce is about providing right level of access privileges to the users and/or devices accessing your protected applications. Workloads is to apply policies and have audit for securing your on-prem or cloud applications. Cisco ISE is aligned with Workplace-Cisco Zero Trust solution where users and devices gets right privileges/access when they connect to the network. Cisco ISE provides intent-based policy and compliance solution on top of AAA. Cisco ISE can be integrated with Threat Centric NAC vendors such as Cisco Secure Endpoint (formerly AMP), Qualys, Nexpose and Tenable to assess vulnerabilities and/or threats associated with the endpoint connecting to your network and give secure access according to the policy definitions. As a Security/Network administrator, you can check for compliance of an endpoint and continuously verify the trust of an endpoint based on vulnerabilities and/or threats associated to give the proper privileges to the network whenever they connect.
Cisco® Secure Endpoint integrates prevention, detection, threat hunting, and response capabilities in a unified solution leveraging the power of cloud-based analytics. Secure Endpoint will protect your Windows, Mac, Linux, Android, and iOS devices through a public or private cloud deployment.
Cisco Secure Endpoint is a single-agent solution that provides comprehensive protection, detection, response, and user access coverage to defend against threats to your endpoints. The SecureX™ platform is built into Secure Endpoint, as well as Extended Detection and Response (XDR) capabilities. The newly introduced Cisco Secure MDR for Endpoint combines Secure Endpoint’s superior capabilities with security operations expertise to dramatically reduce the mean time to detect and respond to threats.
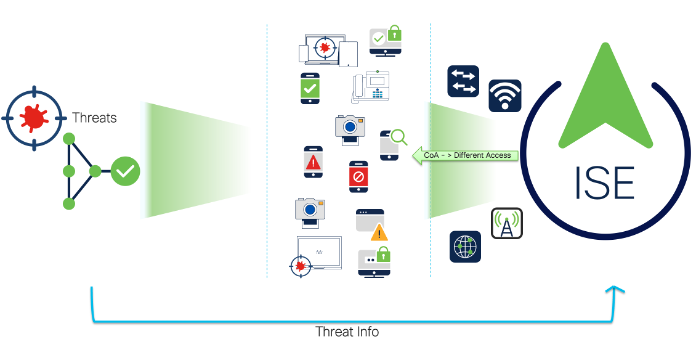
When Cisco Secure Endpoint integrated with Cisco ISE, Cisco ISE and Cisco Secure Endpoint can share the information of Threats and Malware associated with the endpoint so that Cisco ISE can allow endpoints based on the threats’ Course of Action. Cisco Secure Endpoint does not use Cisco platform Exchange Grid (pxGrid) for ISE integration, instead it uses Structured Threat Information Expression (STIX). STIX is an information exchange language and used to exchange cyber threat intelligence with organizations. It allows a common framework for organizations to share cyber threat information and adapt quicker to computer-based attacks. Cisco Threat Centric NAC using Cisco Secure Endpoint in the Cloud also falls into the Rapid Threat Containment category. Cisco Security Solutions and Ecosystem and CSTA partner solutions that fall into this category use Adaptive Network Control (ANC) mitigation actions to respond to or contain threats by issuing mitigation actions either from pxGrid, ISE EPS RESTful API or STIX. Cisco Threat Centric NAC using Cisco Secure Endpoint perform threat detection and malware analysis. The ISE STIX integration provides visibility into compromised hosts and provides manual ANC mitigation or Change of Authorization (CoA) actions the security administrator can take with regards to an organization’s security policy
Cisco ISE Threat Centric NAC service can dynamically provide differentiated privileges to endpoints based on Threats or vulnerability information.
_______________________________________________________________________________________________
Threat information associated to the endpoint shared by Cisco Secure Endpoint
Cisco Secure Endpoint detects and shares the Threat Impact Level interms of Severity and corresponding Course of Action information so that Cisco ISE allows you to write policies based on Course of Action and dynamically raise CoA if there is any change to the endpoint’s Threat severity or Course of Action. Below attributes are shared by Cisco Secure Endpoint to Cisco ISE.
- Threat Type
- Threat Severity – Unknown, Insignificant, Distracting, Painful, Damaging or Catastrophic
- Threat Course of Action – Internal Blocking, Monitoring or Eradication
- Confidence level – High, Medium or Low
- Threat detected Timestamp
_______________________________________________________________________________________________
Cisco ISE + Cisco Secure Endpoint Integration Architecture.
When Cisco ISE is integrated with Cisco Secure Endpoint, Cisco secure endpoint module (standalone/Secure Client) installed on the endpoint can scan or automatically detect the threat associated with endpoint and shares the info to Cisco ISE (specifically PSN running with Threat Centric NAC service) so that endpoint gets updated with latest information sent by Cisco Secure Endpoint and raises CoA to give differentiated privileges based on the policies written.
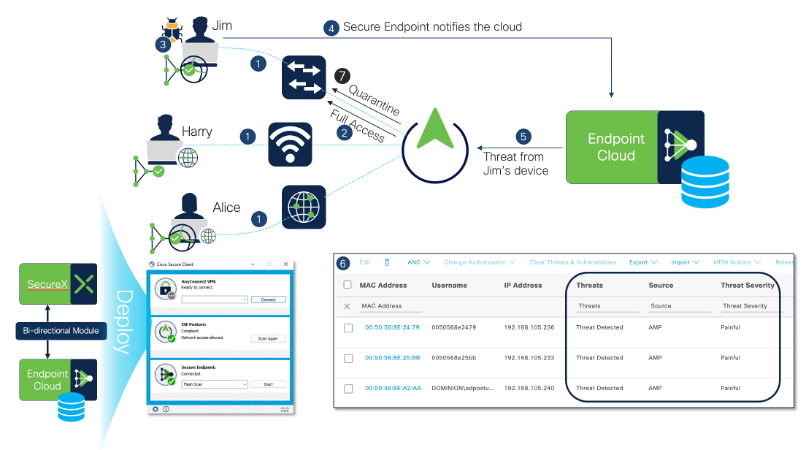
Cisco ISE Standalone and Cisco Secure Endpoint Integration Flow
Below flow of events explains how it works at high-level with Cisco ISE standalone node.
- Endpoint connects to network over wired, Wireless or VPN and authenticates against ISE.
- Cisco ISE might give Full Access or Corporate access based on the policies.
- Cisco Secure Endpoint agent module (either in standalone or deployed with Cisco Secure Client)scans the endpoint or automatically detects malware or vulnerability associated with the endpoint.
- Cisco Secure endpoint notifies the Endpoint Cloud.
- Cisco Secure Endpoint Cloud updates the ISE about threat information.
- Cisco ISE updates the endpoint with threat information shared.
- Cisco ISE issues CoA to give Quarantine or different privilges based on the policies written using threat’s Course of Action
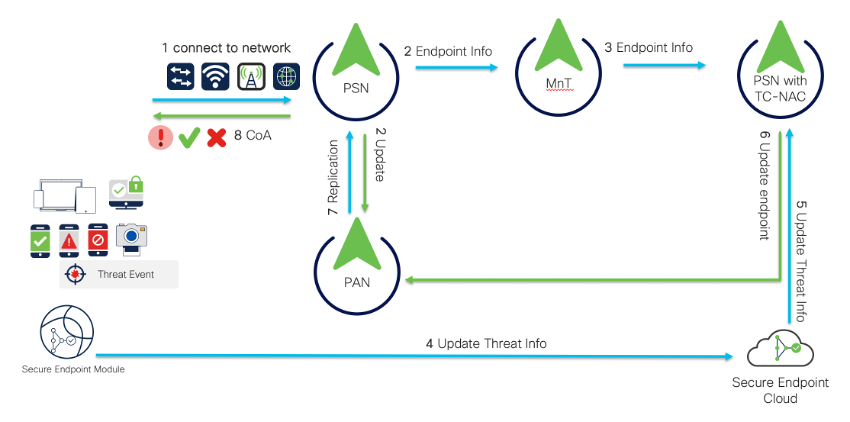
Cisco ISE Distributed Deployment and Cisco Secure Endpoint Integration Flow
When Cisco ISE and Cisco Secure Endpoint was integrated, below flow of events explains how Cisco ISE can give differentiated privileges based on the threat info updated by Cisco Secure Endpoint.
- Endpoint connects to network over WiFi, Wired, VPN or 5G network and authenticates against PSN in a deployment.
- PSN updates the endpoint information to MnT and PAN
- TC-NAC adaptor instance enabled in the PSN gets the endpoint session information from MnT.
- When endpoint tries to download any malware file or service or application, Cisco Secure Endpoint agent module (either in standalone mode or integrated with cisco secure client) will detect the maliciousness/threat and updates the Cisco Secure Endpoint Cloud
- Since ISE was already integrated Cisco Secure Endpoint Cloud, Cisco ISE gets that threat information from Cisco Secure Client Cloud.
- PSN with TC-NAC adaptor instance updates the endpoint with threat information to PAN node.
- PAN node replicates the same endpoint info to rest of the nodes over replication.
- Once the threat information is updated on the endpoint, PSN to which endpoint got authenticated, raises CoA to match the policies based on the Threat’s Course of Action.
Policies
Example Policies1:
Example Policies2:
It is recommended to write threat-based policies under Global/Local Exceptions. Global/Local Exception policies would help you to give differentiated privileges irrespective of how you construct policy sets. You can write policies using Threat dictionary. You could give differentiated privileges based on the Threat severity mentioned in example policies1 above. Or you could give restricted/deny/Quarantine privielges based on any threat severit mentioned in example policies2 above.
Components Used
- Cisco ISE 3.4
- Cisco Secure Endpoint Cloud
- Cisco Secure Endpoint agent 8.4.0.30201
- Windows 11 client
Cisco Secure Endpoint
- Login to Cisco Secure Endpoint Cloud using respective cloud datacenter cloud.
- Americas -- https://console.amp.cisco.com
- Europe – https://console.eu.amp.cisco.com
- Asia Pacific – https://console.apjc.amp.cisco.com
- Enter your login email/login ID for your Secure Endpoint Organization. Then you will be prompted for your password
- Make sure you have required licenses for your organization to deploy Cisco Secure Endpoint and integrate with Cisco ISE.
- Cisco Secure Endpoint agent can be deployed to Windows, macOS, Android, Linux and iOS devices. By default, Cisco Secure Endpoint Cloud has below Groups for deploying agents and managing endpoints. Groups allow the computers in your organization to be managed according to their function, location, or other criteria determined by the administrator. When you first log into Secure Endpoint, a Default Group will already have been created for you. Clicking on a group in the list will expand details on that group, including the policies assigned to it and the members of the group. You can also create new groups, edit existing ones, and delete groups. Navigate to Management > Groups to see below groups.
- Audit
- Domain Controller
- Protect
- Server
- Triage
- This document uses Protect group to deploy the cisco secure endpoint agent and managing it.
- Navigate to Management > Policy to review the policies written for Protect Group.
- Review Policies written for Protect Group.
- Navigate to Management > Deployment > Download Connector to download executable files manually or deploy them through cloud or any software management centers. This document doesn’t describe how to deploy Cisco Secure Endpoint agent to clients. For more information, you can refer to Cisco Secure Endpoint documentation.
Cisco ISE Configuration
Considering you have already deployed a Cisco Secure Endpoint Agent to Endpoint to detect any malicious/malware files being downloaded to the endpoint and stop the incidents reported to Cisco Secure Endpoint cloud and thereby Cisco ISE over Threat Centric NAC integration. This section will give you details on how to integrate Cisco Identity Services Engine with Cisco Secure Endpoint Cloud
Enabling Threat Centric NAC Service
In order to enable Threat Centric NAC service, you must have Premier licenses available. Ensure that your ISE deployment has required premier licenses available. For eg., if x no. of endpoints (Sessions) are supposed to be going through the vulnerability assessment, then you must have those many number of premier licenses which includes all features along with compliance. Refer to https://cs.co/ise-licensing for more information.
- Login to ISE admin portal with super admin privileges
- In order to enable Threat Centric NAC service, you must have Premier license available. Ensure that your ISE deployment has required premier licenses available.
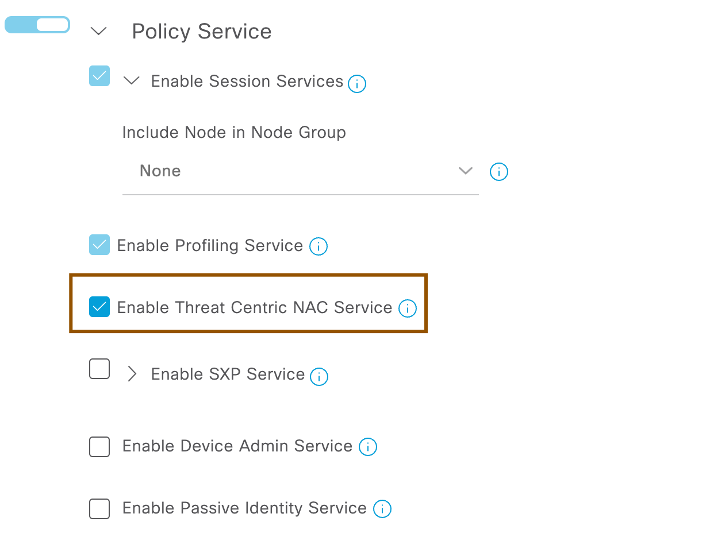
- Navigate to Administration > System > Deployment > <ISE PSN Node> and enable “Enable Threat Centric NAC Service” check box
NOTE: You can enable Threat Centric NAC Service on one single PSN in your ISE Deployment. - Wait for few minutes for the ISE to bring up the Threat Centric NAC service. You can check the service status by login to CLI of PSN node where Threat Centric NAC Service is enabled and executing command “show application status ise”. Make sure the “TC-NAC MongoDB Container”, “TC-NAC core Engine Container”, “VA Database” or “VA Service” is in running state.
Integrating Cisco Secure Endpoint
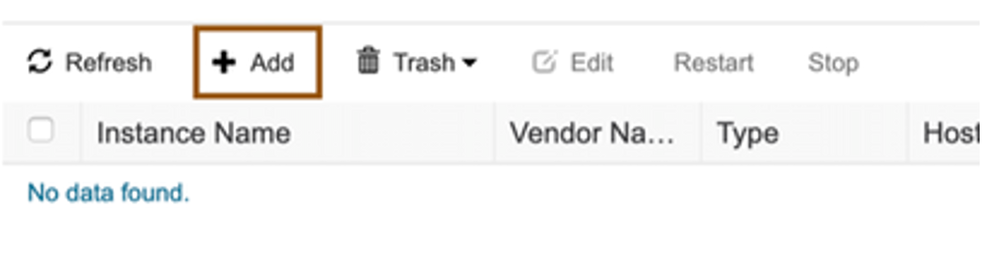
- Navigate to Administration > Threat Centric NAC > Third Party Vendors and click ADD.
- Select “Tenable Security Center : VA” as the vendor and provide Instance Name (eg., Tenable) for ISE Policy reference.
- It takes few seconds for the Secure Endpoint adaptor to come up and shows as “Ready to configure”
- Click Ready to configure, enter socks proxy optional configuration if your Cisco ISE needs socks proxy to reach Secure Endpoint cloud.
- Click Next, select the datacenter to which you want to integrate your cisco ISE with
- Cisco ISE will give you URL to authorize the IRF adaptor from Cisco Secure Endpoint cloud upon clicking Next.
- URL will take you to Cisco Secure Endpoint cloud to authorize the IRF adaptor. You might have to login in to Cisco Secure Endpoint Cloud to authorize IRF adaptor. In this example, Protect Group is selected so that Cisco ISE gets the events when computers or devices belonging to the group gets the malicious/malware/threat events. Click Allow.
- Upon successful IRF authorization, you will be redirected to Cisco ISE Threat Centric NAC Configuration page. Make sure it shows “Configuration Successful”. Click Finish by leaving Advanced Settings as is.
- Make sure Connection Status and Status shows Connected & Active respectively for Secure Endpoint Cloud threat centric NAC adaptor as shown below.
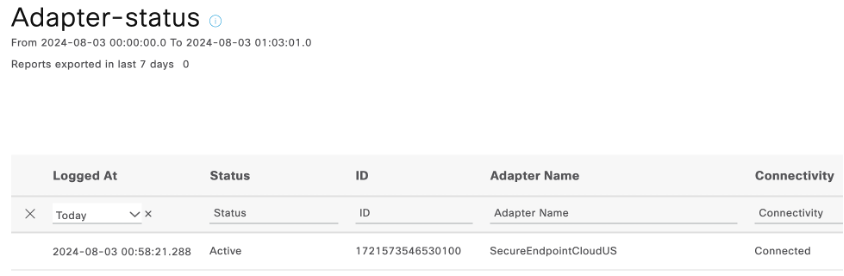
- Navigate and run Operations > Reports > Reports > Threat Centric NAC > Adapter Status report to confirm the connectivity status.
This confirms Cisco ISE can receive events over STIX for any threat events encountered by endpoints being managed by Protect Cisco Secure Endpoint Group.
Configuring Policies
- (optional)Navigate to Administration > Identity Management > Identities > Users, click on Add to configure an internal user. Provide Details like username and password and submit the configuration. You can also make use of other identity sources users to authenticate the user. This document makes use of Active directory user for authentication purpose in validation section
- Navigate to Work Centers > Network Access > Network Resources > Network Devices, click on ADD to configure Network Access device. Provide details such as name, IP address of WLC (in this example) and shared secret.
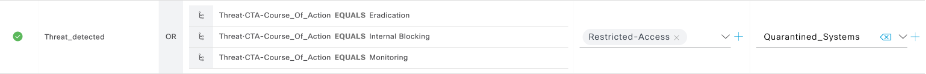
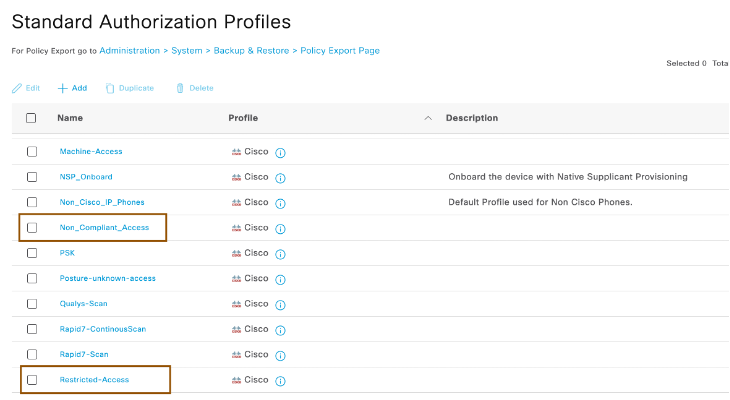
Similarly, you can configure all your NADs. - In order to give differentiated privileges for devices based on their threat’s Course of Action such as Monitoring/Blocking/Eradication, you can create different authorization profiles with different VLANs/ACLs/dACL..etc as per your requirement. Below Non_Compliant_Access and Restricted-Access authorization profile are going to be used for Monitoring/Internal Blocking threat’s Course of Action.
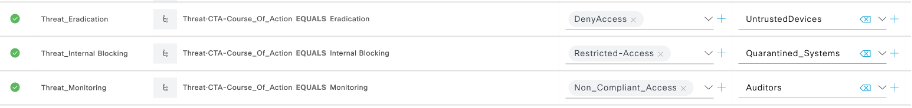
- Configure authorization policies under global exception policies. i.e. when an
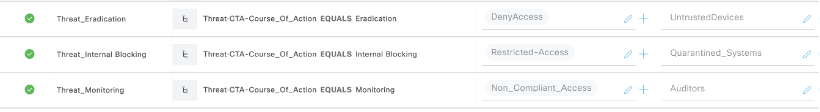
- Endpoint Threat’s Course of Action = Monitoring associate Non_Compliant_Access
- Endpoint Threat’s Course of Action = Internal Blocking associate Restricted_Access
- Endpoint Threat’s Course of Action = Eradication associate Deny Access
Optionally, you can associate different Security Groups as shown above too.
- For endpoints which doesn’t have any threat incident, you can give corporate or compliant access as shown below.
- Now Cisco ISE can receive threat events whenever endpoint belonging to Protect group encounters a threat incident.
Validation
- Authenticate the device using the user credentials created in earlier section or authenticate the user with AD credentials(if AD is already integrated with cisco ISE)
- Considering the Cisco Secure Client agent is installed and deployed from Cisco Secure Client cloud, make sure Secure Endpoint agent shows Connected Status
- In order to simulate threat incidents, you can download Malware Test file from https://www.eicar.org/download-anti-malware-testfile/
- Scroll down to download malware file.
- Click EICAR.COM-ZIP or EICAR.COM2-ZIP to download malware files.
- No matter how many times you try to download, Cisco Secure Endpoint agent automatically detects that malware file is being download and it will not allow the client to download.
- You can also try to download netcat 1.11 or 1.12 from https://eternallybored.org/misc/netcat
- Secure Endpoint agent automatically detects and quarantines the downloaded files.
- Open Secure Endpoint and click settings window
- Navigate to Secure Endpoint window and Advanced tab, click Event History to know these events.
- You can see that Cisco Secure Endpoint could detect and quarantine the malicious files being downloaded.
- You can find these events from Cisco Secure Endpoint cloud as well. Login to secure endpoint cloud, navigate to Events page.
- The same threat events are going to be shared to Cisco ISE over Threat Centric NAC integration. Login to Cisco ISE, navigate and run operations > Reports > Reports > Threat Centric NAC Threat-Events report. You can see threat incidents such as below.
- Navigate to Context Visibility > Endpoints > Compromised Endpoints dashboard to know the threat incidents stored in endpoint’s database.
- Click the Endpoint’s MAC address from the same window and go to Threats window to see the Threat events received and stored.
- Optionally, you can periodically scan the endpoint under Compliant-Access or Restricted-Access authorization profile created earlier to assess the vulnerabilities periodically in order to give differentiated access based on the latest scans.
- Optionally, you can also make use of DataConnect feature in order to get the config and operational data out of Cisco ISE by connecting your ODBC clients to Cisco ISE database. You can refer to https://developer.cisco.com/docs/dataconnect for more details.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: