- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- URL Filtering on the Cisco Catalyst 8000V (Multi-Tenancy)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 07-14-2022 09:21 AM
- Introduction
- Benefits
- Documentation
- Prerequisites
- Image Download Links
- Limitations
- Supported Platforms
- License Requirements
- Step-By-Step Configuration
- URL Filtering Use Case: Employee Internet + Guest Access (Multi-Tenant)
- Enable iox and configure application hosting
- Configure Port Groups
- Activate virtual service and configure profile
- Configure allow and block list (Optional)
- Enable multi-tenancy and configure web-filter profile
- Attach allow list and block list to the profile
- Configure and attach block page (Optional)
- Configure data plane policy
- Verification
- Check virtual service
- Check the UTD engine status
- Check the UTD engine configuration
- Browse to blocked/allowed website
- Check URL Filtering logging events
- Show UTD engine packet statistics
- Troubleshooting
Introduction
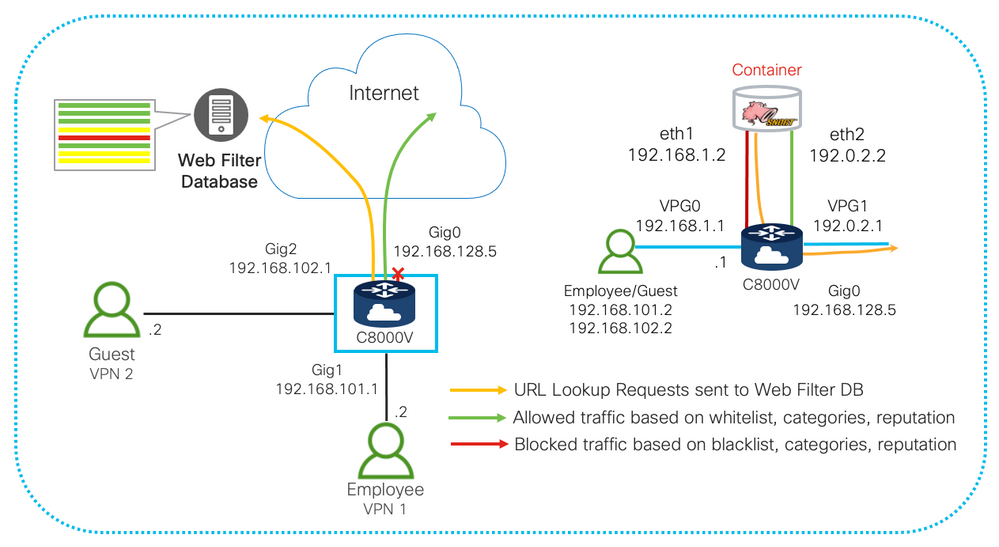
URL Filtering is an On-Premise content filtering solution that is available on the Cisco Catalyst 8000V, CSR 1000V, and ISRv virtual routers running IOS XE (Autonomous Mode). The URL filtering feature comes with the UTD engine which is a container-based security application that can be downloaded officially from Cisco and installed on your virtual router. The available control plane cores and memory can be leveraged by the UTD engine application to run Snort IDS/IPS, URL Filtering, or both. In this document, we will focus primarily in deploying and configuring URL Filtering with multi-tenancy on a Cisco Catalyst 8000V virtual router.
If you are looking for configuring URL Filtering for single tenant, please refer to the link here.
Benefits
- Content Filtering for BYOD
- 82+ Web Categories with dynamic updates from Webroot/BrightCloud
- Block based on Web Reputation score
- Create custom Blacklists and Whitelists
- Customizable Block Page
- Supports VRF and IPv6
Documentation
This configuration example is meant to be interpreted with the aid of the official documentation from the configuration guide located here:
Prerequisites
- 4 GB additional memory (8 GB total on Catalyst 8000V, CSR 1000V, or ISRv for urlf-low and urlf-medium profiles)
- 8 GB additional memory (12 GB total on Catalyst 8000V, CSR 1000V, or ISRv for urlf-high profile)
- XE 16.3.1 and above on CSR 1000V
- XE 16.6.1 on CSR 1000V for Multi-tenancy
- XE 16.8.1 and above on ISRv
- XE 17.4.1 and above on Catalyst 8000V
Image Download Links
Catalyst 8000V - https://software.cisco.com/download/home/286327102/type/282046477/release/Cupertino-17.8.1a
UTD Engine for IOS XE - https://software.cisco.com/download/home/286327102/type/286285284/release/17.8.1a
Limitations
- HTTPS traffic can be blocked, but customized block page cannot be sent on user browser.
- Categories allow and block are mutually exclusive, only one can be active at a time.
Supported Platforms
This application is only supported on the ISRv, CSR 1000V and Catalyst 8000V.
License Requirements
SEC-K9 license or DNA Essentials
Step-By-Step Configuration
URL Filtering Use Case: Employee Internet + Guest Access (Multi-Tenant)
Enable iox and configure application hosting
Download and copy the UTD engine software to the virtual router's flash. The file name should be similar to this:
secapp-utd.17.08.01a.1.0.1_SV2.9.18.1_XE17.8.x86_64.tar (latest version may vary). If you have not enabled iox on your virtual router, do that before installing the UTD engine service. Once done, install the virtual service using the IOx commands as shown below. Installation may take some time but you can check the installation status with the command "show app-hosting list".
Note: Make sure that the UTD engine software is the same version as the software image you are using for your virtual router. For example, you would need to use an IOS XE 17.8.X virtual router image in order to use UTD Engine 17.8.X image. Otherwise, the UTD engine installation will fail.
iox
app-hosting install appid utd package bootflash:secapp-utd.17.08.01a.1.0.1_SV2.9.18.1_XE17.8.x86_64.tar
Configure Port Groups
The UTD engine runs as a Linux Container Application. Virtual Port Group (VPG) interfaces are used to communicate between container and data plane.
Configure two port groups. One for management traffic. This VPG will be used to source logs to the log collector. The second port group is for data. This VPG will be used to send and receive packets that are diverted from the data plane to the UTD engine container for URL Filtering and Lookup.
interface VirtualPortGroup0
description Management interface
ip address 192.168.1.1 255.255.255.252
interface VirtualPortGroup1
description Data interface
ip address 192.0.2.1 255.255.255.252
Activate virtual service and configure profile
Next step is to activate the virtual service and configure matching guest IPs on the same subnet for the container side. Make sure to start the service when done configuring.
app-hosting appid utd
app-vnic gateway0 virtualportgroup 0 guest-interface 0
guest-ipaddress 192.168.1.2 netmask 255.255.255.252
app-vnic gateway1 virtualportgroup 1 guest-interface 1
guest-ipaddress 192.0.2.2 netmask 255.255.255.252
app-resource package-profile urlf-low
start
Configure allow and block list (Optional)
This following section is to configure whether you want to create a whitelist to allow certain websites or a blacklist to block certain websites from being accessed.
parameter-map type regex wlist
pattern www.google.com
pattern www.cisco.com
parameter-map type regex blist
pattern www.facebook.com
pattern www.instagram.com
Enable multi-tenancy and configure web-filter profile
This section is to configure the URL profile for the Web Filter. We can also specify categories to allow/block to add as an additional layer of security. We can also create alerts in the form of log messages whenever the UTD engine encounters a hit when filtering traffic. The configuration below will block the following categories: alcohol/tobacco, fashion/beauty, and financial services. You can see the full list of categories available by pressing "?" when in the blocked categories configuration. As mentioned in the Limitations section, blocked and allowed categories are mutually exclusive meaning that the UTD engine will only block categories or allow categories at any given time.
Webroot also associates a reputation score to websites ranking them from trustworthy to high risk which we can configure when creating the URL profile. In the configuration below, the UTD engine will block URL websites marked as moderate risk which is defined as a website with reputation scores ranging from 1-60. Below is a table of Webroot's Reputation scores for websites.
| Score Range | Description |
| 1-20 | High Risk |
| 21-40 | Suspicious |
| 41-60 | Moderate Risk |
| 61-80 | Low Risk |
| 81-100 | Trustworthy |
As a last line of defense, we can use the "fail-close" command, meaning that when UTD engine goes down for what ever reason, no traffic will be allowed to leave.
utd multi-tenancy
utd engine standard multi-tenancy
web-filter url profile URL-FILTER-POLICY
categories block
alcohol-and-tobacco
fashion-and-beauty
financial-services
alert all
reputation
block-threshold moderate-risk
Attach allow list and block list to the profile
Now we can attach the blacklist and whitelist we created previously to the URL profile.
utd engine standard multi-tenancy
web-filter url profile URL-FILTER-POLICY
blacklist
parameter-map regex blist
whitelist
parameter-map regex wlist
Configure and attach block page (Optional)
You can create a block page profile to redirect the user who requested the blocked traffic to a block page. You can either configure an in-line blocker which consists of a text banner, point to an uploaded file which can be displayed on the browser, or redirect the user to a block server.
utd engine standard multi-tenancy
web-filter block page profile BLOCK-URL-FILTER-POLICY
text “WHAT ARE YOU DOING!!!”
web-filter url profile URL-FILTER-POLICY
block page-profile BLOCK-URL-FILTER-POLICY
Note: HTTPS traffic can be blocked, but customized block page cannot be sent on user browser (HTTP only).
Configure data plane policy
Now we have set up the minimum configurations for our URL filter policy. The last step is to configure the data plane to use the URL filter policy on either a specified interface or on all interfaces on the virtual router depending on your network topology.
utd engine standard multi-tenancy
utd global
logging syslog
!
utd engine standard multi-tenancy
policy utd-policy
vrf 1
vrf 2
all-interfaces
fail close
web-filter url profile URL-FILTER-POLICY
Once the data plane policy has been configured, the tunnel between the C8000V and the UTD engine container will change to the UP state. If using the serial console to make configurations, the UTD engine service node will change its health status from Down -> Red -> Green, meaning that the UTD engine has applied the configuration changes and is running successfully. For any additional changes to the configuration while the UTD engine is running, the UTD engine health status will switch to RED and will turn back to GREEN once the configuration changes have been applied.
Verification
Check virtual service
Verify that the UTD container is active
c8kv-utd-MT# sh app-hosting list
App id State
---------------------------------------------------------
utd RUNNING
Check the UTD engine status
Check the UTD engine status and system health.
c8kv-utd-MT# show utd engine standard status
Engine version : 1.0.1_SV2.9.18.1_XE17.8
Profile : URLF-Low
System memory :
Usage : 3.90 %
Status : Green
Number of engines : 1
Engine Running Health Reason
=======================================================
Engine(#1): Yes Green None
=======================================================
Overall system status: Green
Signature update status:
=========================
Current signature package version: 29.0.c
Last update status: None
Last successful update time: None
Last failed update time: None
Last failed update reason: None
Next update scheduled at: None
Current status: Idle
Check the UTD engine configuration
Check the UTD engine configuration and policy.
c8kv-utd-MT# sh utd engine standard config
UTD Engine Standard Configuration:
Multi-tenancy: Enabled
URL-Filtering Cloud Lookup: Enabled
URL-Filtering On-box Lookup: Enabled
File-Reputation Cloud Lookup: Disabled
File-Analysis Cloud Submission: Disabled
UTD TLS-Decryption Dataplane Policy: Disabled
Flow Logging: Disabled
UTD VRF table entries:
VRF: 2 (2)
Policy: utd-policy
Webfilter Profile: URL-FILTER-POLICY
VRF: 1 (1)
Policy: utd-policy
Webfilter Profile: URL-FILTER-POLICY
VirtualPortGroup Id: 1
UTD threat-inspection profile table entries:
UTD threat-inspection profile table is empty
UTD threat-inspection whitelist profile table entries:
UTD threat-inspection whitelist profile table is empty
UTD web-filter profile table entries
Web-filter URL profile: URL-FILTER-POLICY
Whitelist:
Entries: 2
Blacklist:
Entries: 2
Categories Action: Block
Entries: 3
Block Profile: BLOCK-URL-FILTER-POLICY
Block text size: 23
Reputation Block Threshold: Moderate risk
Alerts Enabled: Whitelist, Blacklist, Categories, Reputation
Debug level: Error
Conditional debug level: Error
Source DB Failure Action: Fail-open
TLS-Decrypt Inject Block: Enabled
UTD TLS-Decryption profile table entries
UTD TLS-Decryption profile table is empty
UTD File analysis table entries
UTD File analysis profile table is empty
UTD File reputation table entries
UTD File reputation profile table is empty
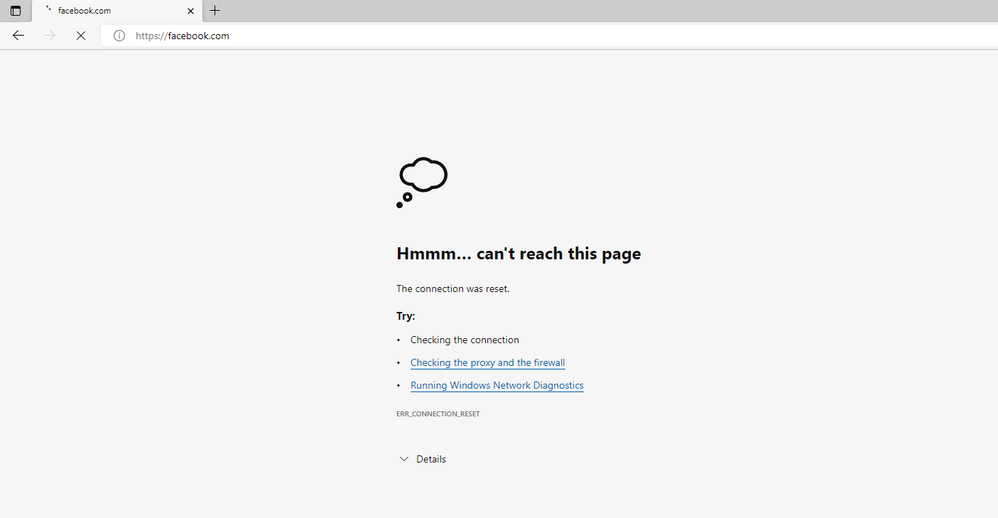
Browse to blocked/allowed website
Now that the UTD engine has been configured for URL Filtering, verify its URL engine policy by navigating to a blocked website either found under the blacklist or blocked categories if configured. You should see an error message on your browser similar to the one below and should not be able to reach the website.
Check URL Filtering logging events
Check if there have been any events such as whitelist/blacklist hits recorded by the UTD engine.
c8kv-utd# sh utd engine standard logging events
2022/07/12-19:48:03.491996 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Drop [**] UTD WebFilter Blacklist [**] [URL: www.facebook.com] [VRF: 0] {TCP} 10.29.43.237:51654 -> 157.240.28.35:443
2022/07/12-19:48:03.519479 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Drop [**] UTD WebFilter Blacklist [**] [URL: www.facebook.com] [VRF: 0] {TCP} 10.29.43.237:51655 -> 157.240.28.35:443
2022/07/12-19:48:25.495177 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Drop [**] UTD WebFilter Blacklist [**] [URL: www.facebook.com] [VRF: 0] {TCP} 10.29.43.237:51689 -> 157.240.28.35:443
2022/07/12-19:48:25.737126 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Drop [**] UTD WebFilter Blacklist [**] [URL: www.facebook.com] [VRF: 0] {TCP} 10.29.43.237:51691 -> 157.240.28.35:443
2022/07/12-19:50:02.570667 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Pass [**] UTD WebFilter Whitelist [**] [URL: www.cisco.com] [VRF: 0] {TCP} 10.29.43.237:51732 -> 173.37.145.84:443
2022/07/12-19:50:08.821623 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Pass [**] UTD WebFilter Whitelist [**] [URL: www.google.com/] [VRF: 0] {TCP} 10.29.43.237:51742 -> 172.253.122.104:80
2022/07/12-19:50:09.291195 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Pass [**] UTD WebFilter Whitelist [**] [URL: www.google.com] [VRF: 0] {TCP} 10.29.43.237:51746 -> 172.253.122.104:443
2022/07/12-19:50:09.526087 UTC [**] [Hostname: c8kv-utd-MT] [**] [Instance_ID: 1] [**] Pass [**] UTD WebFilter Whitelist [**] [URL: www.google.com] [VRF: 0] {TCP} 10.29.43.237:51747 -> 172.253.122.104:443
Show UTD engine packet statistics
c8kv-utd-MT# show utd engine standard statistics
*************Engine #1*************
===============================================================================
Memory usage summary:
Total non-mmapped bytes (arena): 0
Bytes in mapped regions (hblkhd): 0
Total allocated space (uordblks): 0
Total free space (fordblks): 0
Topmost releasable block (keepcost): 0
===============================================================================
Packet I/O Totals:
Received: 4072
Analyzed: 4072 (100.000%)
Dropped: 0 ( 0.000%)
Filtered: 0 ( 0.000%)
Outstanding: 0 ( 0.000%)
Injected: 470
===============================================================================
Breakdown by protocol (includes rebuilt packets):
Eth: 4072 (100.000%)
VLAN: 0 ( 0.000%)
IP4: 4072 (100.000%)
Frag: 0 ( 0.000%)
ICMP: 0 ( 0.000%)
UDP: 7 ( 0.172%)
TCP: 4065 ( 99.828%)
IP6: 0 ( 0.000%)
IP6 Ext: 0 ( 0.000%)
IP6 Opts: 0 ( 0.000%)
Frag6: 0 ( 0.000%)
ICMP6: 0 ( 0.000%)
UDP6: 0 ( 0.000%)
TCP6: 0 ( 0.000%)
Teredo: 0 ( 0.000%)
ICMP-IP: 0 ( 0.000%)
IP4/IP4: 0 ( 0.000%)
IP4/IP6: 0 ( 0.000%)
IP6/IP4: 0 ( 0.000%)
IP6/IP6: 0 ( 0.000%)
GRE: 0 ( 0.000%)
GRE Eth: 0 ( 0.000%)
GRE VLAN: 0 ( 0.000%)
GRE IP4: 0 ( 0.000%)
GRE IP6: 0 ( 0.000%)
GRE IP6 Ext: 0 ( 0.000%)
GRE PPTP: 0 ( 0.000%)
GRE ARP: 0 ( 0.000%)
GRE IPX: 0 ( 0.000%)
GRE Loop: 0 ( 0.000%)
MPLS: 0 ( 0.000%)
ARP: 0 ( 0.000%)
IPX: 0 ( 0.000%)
Eth Loop: 0 ( 0.000%)
Eth Disc: 0 ( 0.000%)
IP4 Disc: 0 ( 0.000%)
IP6 Disc: 0 ( 0.000%)
TCP Disc: 0 ( 0.000%)
UDP Disc: 0 ( 0.000%)
ICMP Disc: 0 ( 0.000%)
All Discard: 0 ( 0.000%)
Other: 0 ( 0.000%)
Bad Chk Sum: 0 ( 0.000%)
Bad TTL: 0 ( 0.000%)
S5 G 1: 0 ( 0.000%)
S5 G 2: 0 ( 0.000%)
Total: 4072
===============================================================================
Action Stats:
Alerts: 10 ( 0.246%)
Logged: 10 ( 0.246%)
Passed: 0 ( 0.000%)
Troubleshooting
For troubleshooting issues, please refer to the documentation below for additional troubleshooting commands and tips.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: