- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Using Let's Encrypt Certificates with Cisco ASA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 11-04-2023 04:02 PM
Table of Contents
- Table of Contents
- Summary
- Obtain the Certificate from Let's Encrypt
- Convert to PKCS#12 File
- Convert Binary to Base64 Format
- Short Digression
- Import the PKCS#12 File
- Assign the Trustpoint to the SSL Interface
- Verify
- Renewal
- Automation
Summary
In this configuration guide we will take the full chain of certificates and the private key from Let's Encrypt and install it onto our Cisco ASA for Remote Access VPN usage.
You must have a working RA VPN configured on an ASA in order to use this guide. This guide will only help you assign a Let's Encrypt certificate to a working RA VPN. We will not go over how to configure RA VPN on ASA.
Obtain the Certificate from Let's Encrypt
Please take a look at this document. This explains how to use Let's Encrypt to obtain a certificate.
Convert to PKCS#12 File
Let's Encrypt provides a Private Key and a full chain of certificates. We will use OpenSSL to convert the certificates and private key into a PKCS#12 file. PKCS12 is a standardized format for creating a 'container' file that will include certificates and a private key. This is a fairly simple process and the command parameters will be explained below.
NOTE: Im using the backslash so that a single command spans multiple lines. This cool linux feature increases readability and allows us to look at the parameters easily.
openssl pkcs12 -export \
-passout pass:cisco123 \
-in fullchain.pem \
-inkey privkey.pem \
-out asa-ravpn.timslab.fun.p12
openssl - the executable
pkcs12 - the OpenSSL module that will be used
-export - This option specifies that a PKCS#12 file will be created rather than parsed.
-passout - Pass phrase source to encrypt any outputted private keys with. passout can accept several types of input for the password so we use pass: to prefix the real password. See the Pass Phrase Options section in this document for specifics.
-in - The filename to read certificates from.
-inkey - The filename to read private keys from.
-out -This specifies filename to write the PKCS#12 file to. This will be a binary file.
Convert Binary to Base64 Format
The ASA supports PKCS#12 in Base64 format but NOT in binary, so with one easy command, we will convert the binary file to Base64.
openssl base64 -in asa-ravpn.timslab.fun.p12 -out asa-ravpn.timslab.fun.b64
openssl - the executable
base64 - the OpenSSL module that will be used
-in - The filename to read the PKCS#12 file from.
-out - The filename to write the Base64 file to
Short Digression
I've seen a lot of PEM based certificate and key files and this output file looks similar but is missing the headers I've always seen. Is this file a PEM file?
The output file is an Base64 encoded ASCII. The output file is not binary.
A PEM file is Base64 encoded and may look similar to the output file.
PEM files are not required to have a Header and Footer. The output files do not have a Header and Footer.
The output file may be called a PEM file.
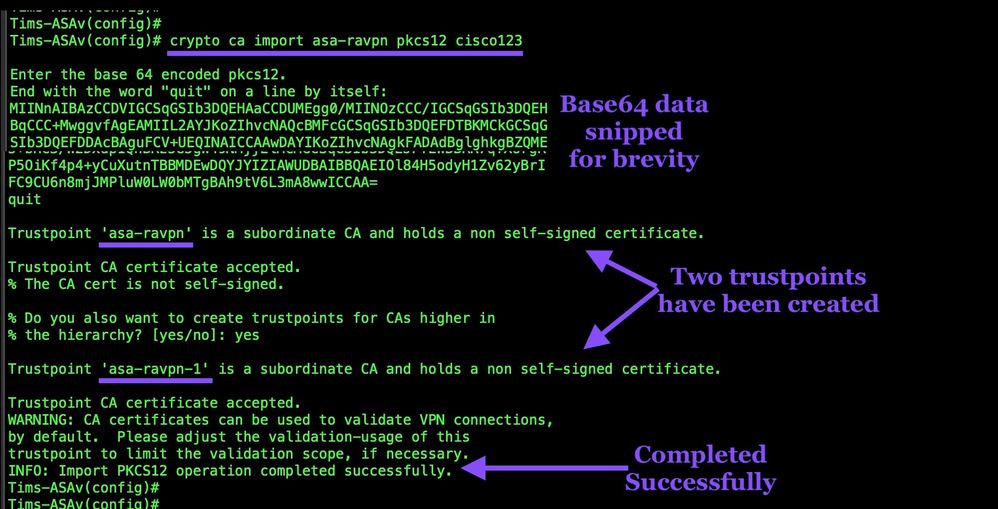
Import the PKCS#12 File
Use this command to import the text based PKCS#12 file and create trustpoints. Be sure to note that when we created the PKCS#12 from the Let's Encrypt data we used the password cisco123 to encrypt the data. Be sure to use the proper password or the import will fail.
crypto ca import asa-ravpn pkcs12 cisco123
Assign the Trustpoint to the SSL Interface
Now we will assign the newly created Trustpoint to the Outside Interface.
In my lab the WebVPN is configured to use the Outside Interface, in your environment be sure to configure the proper interface.
ssl trust-point asa-ravpn Outside
Verify
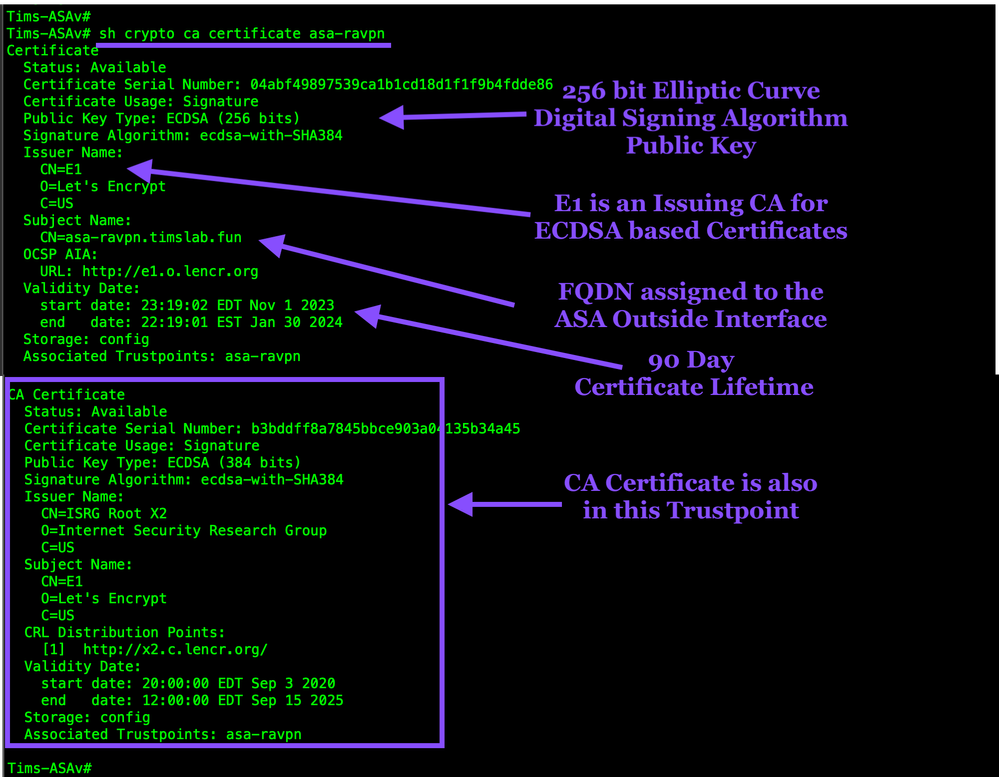
Check the certificates in the ASA trustpoint
show crypto ca certificates asa-ravpn
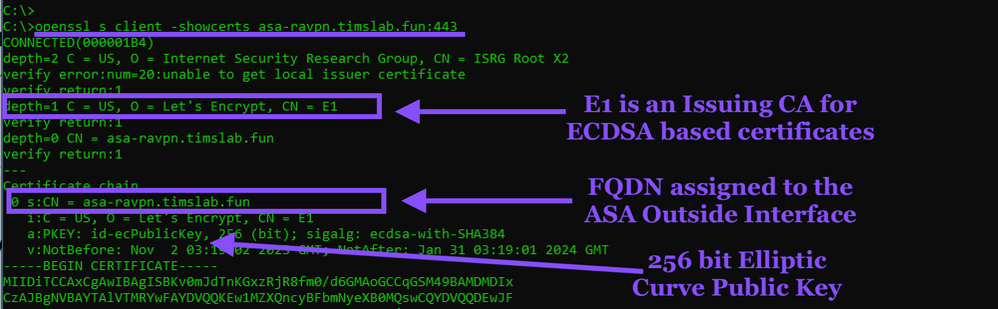
Use OpenSSL to interrogate the certificate exposed to the Internet
openssl s_client -showcerts asa-ravpn.timslab.fun:443
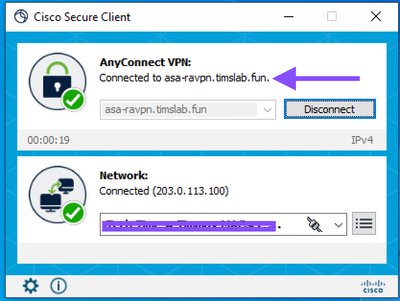
Use AnyConnect to connect to the RA VPN
Renewal
Let's Encrypt issues certificate with a lifetime of 90 days. Typically I like to renew my Let's Encrypt certificate at 75 days.
Let's Encrypt and Certbot are not specifically built for RA VPN so renewal is a manual process, just start here and you will have a new cert and have it installed in less than 15 minutes.
Automation
Shortly I will begin working on code to automate this process and will post the Github link here.
That's it! Please let me know how this guide works out and if you have any questions.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Good write-up, looking forward to the automation portion.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Any progress on providing steps to automate this process?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi @Tim Glen Any success in automating this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@tiwang - I wrote a comment on how I did this with ISE.
Automatic ISE Portal Certificate Renew with Letsencrypt - how to guide - Cisco Community
The concepts should also work for ASA, but I have not looked at the REST API SDK for the ASA - if there is support for uploading certs to the ASA then my procedure should work too. certbot does all the hard work - my shell script is simply a post-renew 'hook' script that gets called if (and only if) the certificate was renewed. In ISE I also took care of deleting the old junk expired certs - because if you don't, then you will have a graveyard full of certs.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Here is my sample script to import certbot certificate to Cisco ASA.
It is automatically triggered by Certbot’s deploy hook immediately after renewal.
certbot-to-asa
https://github.com/hshimomura/certbot-to-asa
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Awesome, Thank You for sharing
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: