- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Using Let's Encrypt Certificates with Cisco Firepower
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-29-2023 10:31 AM - edited 10-29-2023 10:38 AM
Table of Contents
- Table of Contents
- Summary
- Obtain the Certificate from Let's Encrypt
- Convert to PKCS12 Format
- Create the Cert Enrollment Object
- Verify Certificate is on the FTD
- Review the ID certificate and the CA Chain
- Examine the Identity certificate
- Check the Certificate Authority Certificate
- Assign the Certificate to the RA-VPN Interface
- Verify
- Renewal
- References
- Automation
Summary
In this configuration guide we will take the full chain of certificates and the private key from Let's Encrypt and install it onto our FTD for Remote Access VPN usage.
Obtain the Certificate from Let's Encrypt
Please take a look at this document. This explains how to use Let's Encrypt to obtain a certificate.
Convert to PKCS12 Format
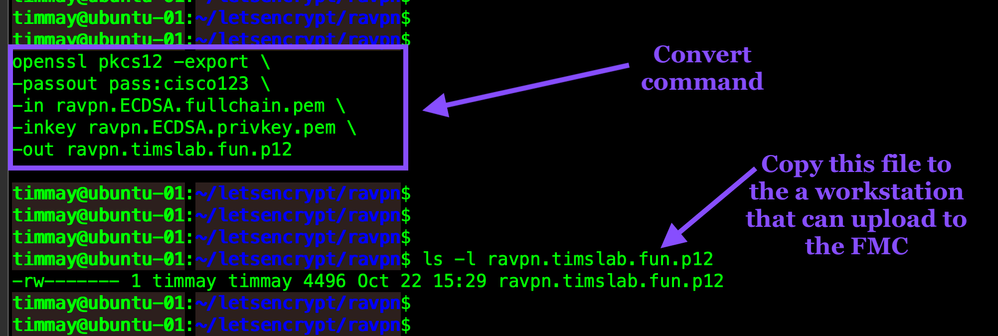
Let's Encrypt provides a Private Key and a full chain of certificates. We will use OpenSSL to convert the certificates and private key into a PKCS#12 file. PKCS12 is a standardized format for creating a 'container' file that will include certificates and a private key. This is a fairly simple process and the command parameters will be explained below.
NOTE: Im using the backslash so that a single command spans multiple lines. This cool linux feature increases readability and allows us to look at the parameters easily.
openssl pkcs12 -export \
-passout pass:cisco123 \
-in fullchain.pem \
-inkey privkey.pem \
-out ravpn.timslab.fun.p12
openssl - the executable
pkcs12 - the OpenSSL module that will be used
-export - This option specifies that a PKCS#12 file will be created rather than parsed.
-passout - Pass phrase source to encrypt any outputted private keys with. passout can accept several types of input for the password so we use pass: to prefix the real password. See the Pass Phrase Options section in this document for specifics.
-in - The filename to read certificates from.
-inkey - The filename to read private keys from.
-out -This specifies filename to write the PKCS#12 file to. This will be a binary file.
Create the Cert Enrollment Object
Now that we have the PKCS#12 file we need to get in onto the FTD, we will do this via a Cert Enrollment Object.
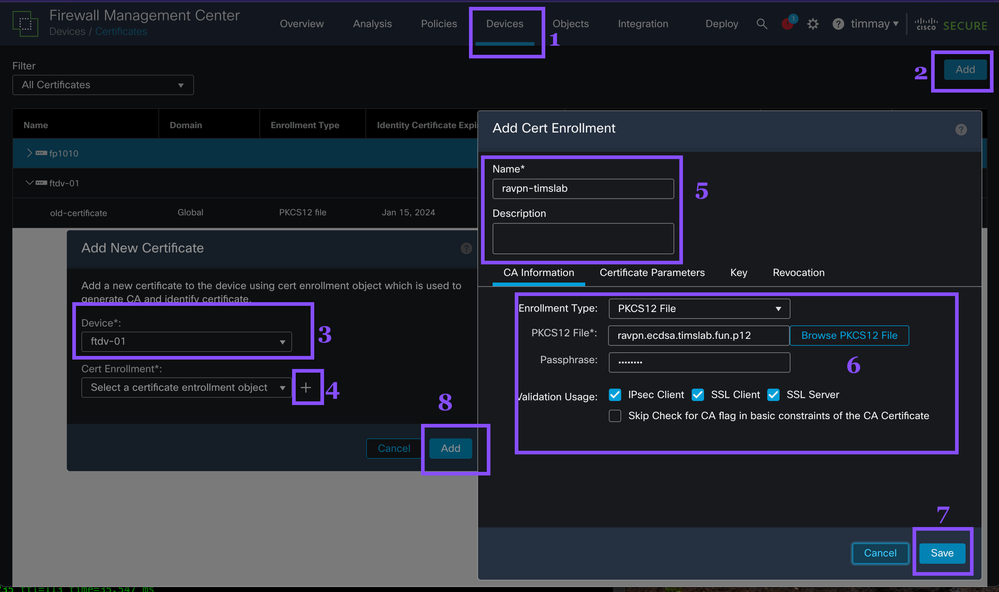
FMC -> Devices -> Certificates -> Add
First we need to Add the new certificate then choose the FTD the certificate will be deployed to.
Next click the + sign at the Cert Enrollment field to open the Add Cert Enrollment dialog.
In the Add Cert Enrollment dialog, add a Name, a description is optional. On the CA Information tab select PKCS12 for the Enrollment Type. Then choose the file that was created in the OpenSSL step above, then enter the password, in our example we used cisco123 for the password.
Finally select SSL Server, then click Save.
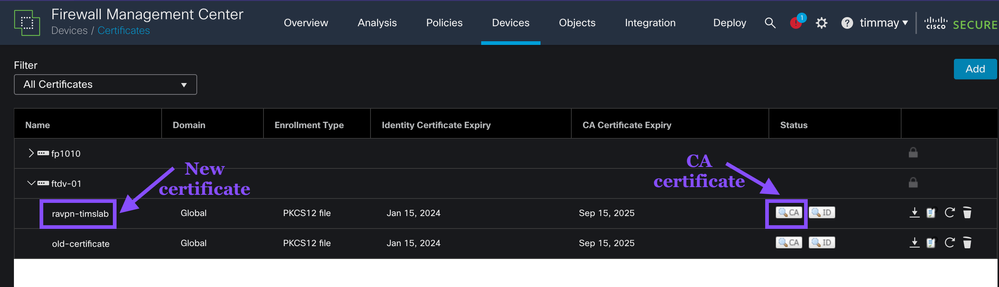
Verify Certificate is on the FTD
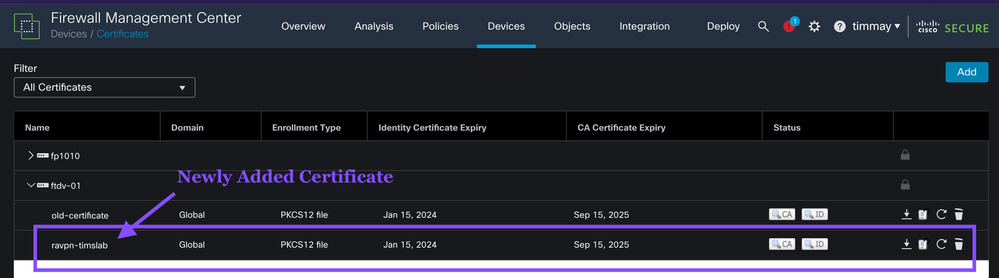
FMC -> Devices -> Certificates
Verify the certificate is on the FTD appliance. If you have more than one FTD, be sure to select the correct FTD, and then verify that the new certificate is listed.
Review the ID certificate and the CA Chain
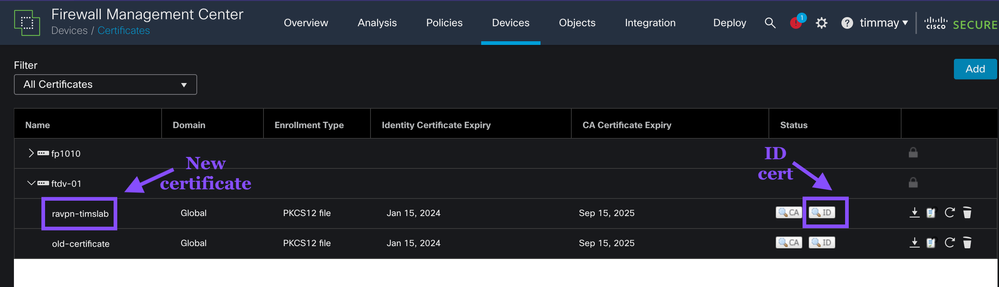
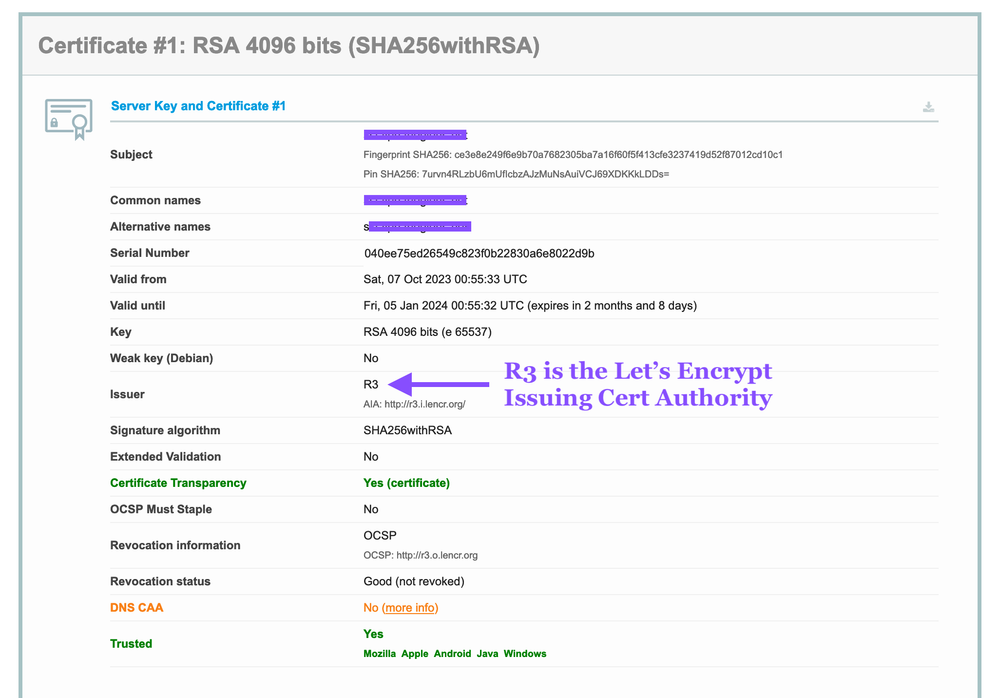
Lets review the ID certificate first.
FMC -> Devices -> Certificates
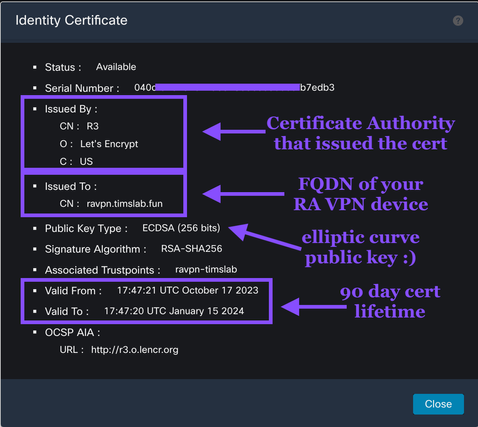
Examine the Identity certificate
Notice the Issued By field. The Certificate Authority that issued this certificate is R3. This is a production Subordinate CA at Let's Encrypt. Also double check the CN is the same as the public facing FQDN for your RA VPN. We use a 256-bit elliptic curve public key because shorter keys elliptic keys are strong! Finally Let's Encrypt only issues certificates with a 90 day lifetime. 90-day lifetime may seem short now (Oct2023) but will be the standard soon.
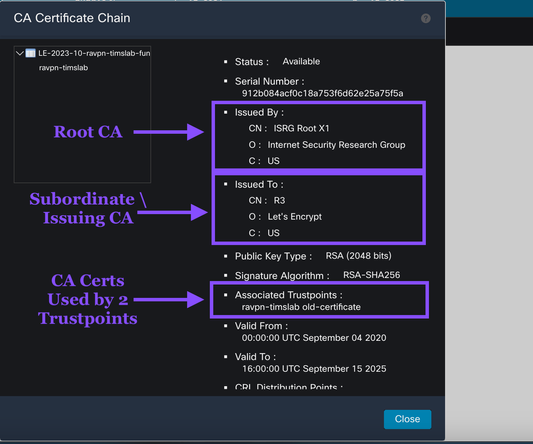
Check the Certificate Authority Certificate
When we look at the CA Certificate Chain we see two things that are notable.
Issued By ISGR Root X1, this is the Let's Encrypt Root Certificate Authority. The Root issues certificates to Subordinate Certificate Authorities. The Root does not issue certificates to end users or devices.
Issued To R3, this is the Subordinate or Issuing Certificate Authority. The Issuing CA issues certificates to end users like us.
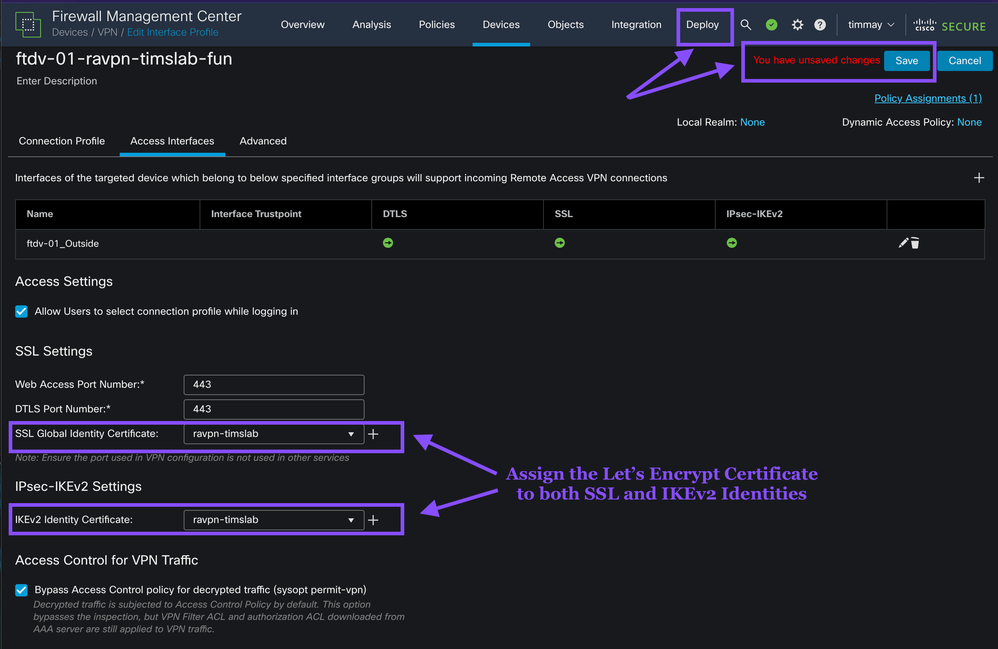
Assign the Certificate to the RA-VPN Interface
FMC -> Devices -> Remote Access
Select the RA VPN Connection Profile you will assign the Let's Encrypt certificate to.
Click Save, then Deploy the changes
Verify
There are several ways you can verify the new Identity Certificate has been installed.
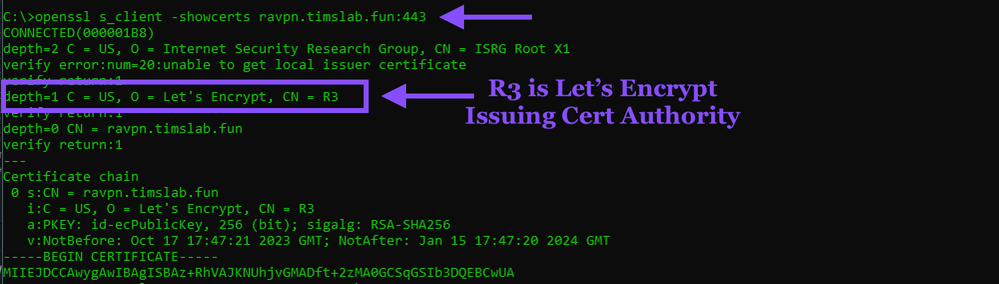
Use Qualys SSL Labs Test and verify the Certificate in the output
OR
Use OpenSSL on your Client to query the FTD RA VPN
Renewal
Let's Encrypt issues certificate with a lifetime of 90 days. Typically I like to renew my Let's Encrypt certificate at 75 days.
Let's Encrypt and Certbot are not specifically built for RA VPN so renewal is a manual process, just start here and you will have a new cert and have it installed in less than 15 minutes.
References
Certificate Validation (This is a really good doc)
Automation
Shortly I will begin working on code to automate this process and will post the Github link here.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for this very useful document @Tim Glen . Looking forward to your automation code!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very interested in your automated solution for the uploading of the certificates on the FMC @Tim Glen
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Automation would be a game changer!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Automation for FMC would be incredible - did you ever get anywhere with that @Tim Glen ?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: