- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Using Stealthwatch to monitor and alert on suspicious/out-of-scope WebEx Usage
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-02-2020 06:23 AM - edited 07-02-2020 06:55 AM
The relevant supporting information to create the alarm and custom application definition can be found from Cisco here:
https://help.webex.com/en-us/WBX264/How-Do-I-Allow-Webex-Meetings-Traffic-on-My-Network
Note that while these directions are WebEx specific, the basics covered here can be applied to any network-based service associated with a known range of IP addresses and ports to enable monitoring and alerting within Stealthwatch.
Solution
Setup: Create a Host Group representing the relevant WebEx IP space.
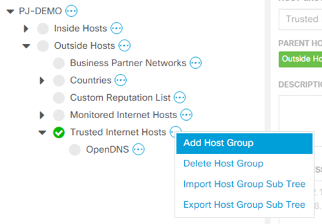
- Navigate to the Host Group editor in the main dashboard menu bar under Configure > Host Group Management.
- Best practice for this would be creating a Trusted Internet Hosts host group as a child of the default Outside Hosts host group (if you do not already have a similar host group defined) and creating a WebEx host group underneath it.
- Add the following IP ranges to the new WebEx Host Group:
64.68.96.0/19
66.114.160.0/20
66.163.32.0/19
170.133.128.0/18
173.39.224.0/19
173.243.0.0/20
207.182.160.0/19
209.197.192.0/19
216.151.128.0/19
114.29.192.0/19
210.4.192.0/20
69.26.176.0/20
62.109.192.0/18
69.26.160.0/20
150.253.128.0/1
-
And click Save to make the change.

Now that you have classified this IP space, you can begin building policies around it.
For our purposes, we are going to create a Custom Security Event (CSE) to alert when traffic occurs between 6pm and 8:30am between any host within your monitored organization, and WebEx, on the ports and protocols used by the service.
WebEx Clients will attempt to initiate communication over the following ports:
- 9000/UDP
- 5004/TCP
- 443/TCP
- 80/TCP
To create the alert:
- Navigate to Policy Management, in the main dashboard menu bar under Configure > Policy Management.
- Locate and select Create New Policy > Custom Security Event.
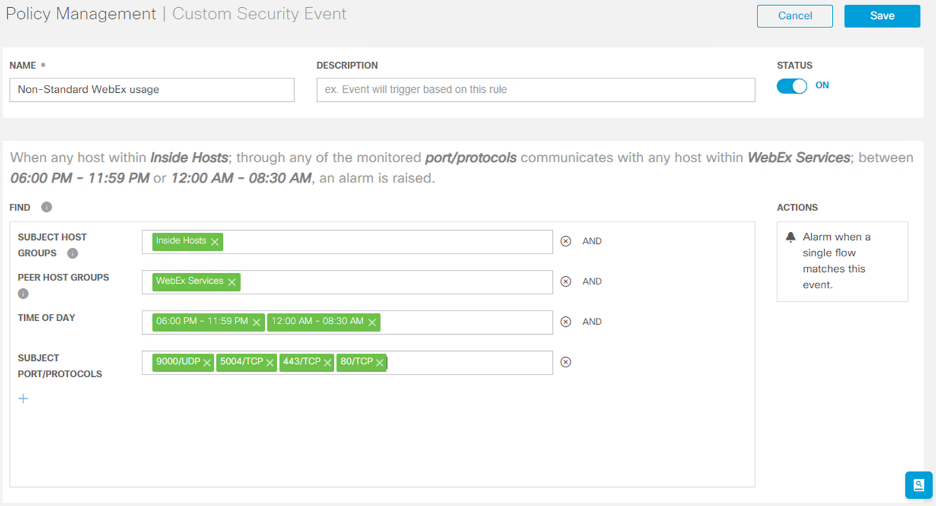
- Define a Name and, optionally, a description.
- Toggle the Status to ON.
- In the blank field below, click + to begin adding alarm parameters.
- Subject Host Groups: Browse and select Inside Hosts
- Peer Host Groups: Browse to and select the previously defined WebEx host group.
- Time of Day: To cover the above off-business hours, you will need to split the defined into separate time ranges, 6PM to 11:59PM, and 12AM to 8:30AM.
- Subject Port/Protocols: 9000/UDP, 5004/TCP, 443/TCP, 80/TCP
- Click Save to commit your changes and have Stealthwatch begin monitoring.
As indicated by the explanatory text above the editing box, now when any host within Inside Hosts; through any of the monitored port/protocols communicates with any host within WebEx Services; between 06:00 PM - 11:59 PM or 12:00 AM - 08:30 AM, an alarm is raised.
Hosts triggering this alarm will create Policy Violation alerts, displayed in the Top Alarming Hosts widget on the Security Insight Dashboard, as well as in named security events in the Alarms by Type and Today’s Alarms widgets.


Defining a Custom Application
Since you have defined a host group for WebEx Services and also know the ports used in communicating with them, you can also have Stealthwatch treat this traffic as a known Application type, allowing you to do additional analysis and reporting on it.
Note: Doing this will create an Application type outside of that provided by having a Flow Sensor in line doing DPI-based application identification.
- To define a Custom Application, in the main dashboard menu bar select Configure > Applications.
- Click the Add Custom Application button.
- Enter a name for this Application.
- Next, you will add the port and protocol attributes associated to the WebEx services to this application type, in the form of "Rules".
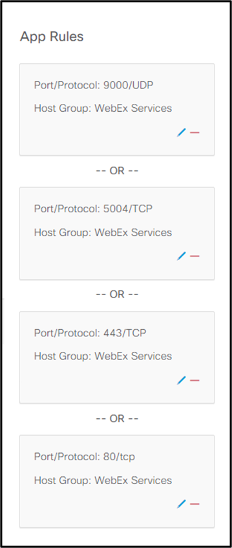
A single defined Application can have multiple rules associated to it. When defining a rule, criteria is "AND-ed" together. Each subsequent rule added in the application definition is treated as an "OR" condition. - Enter a single Port/Protocol attribute.
- Relevant ports and protocols are: 9000/UDP, 5004/TCP, 443/TCP, 80/TCP
- For Server, click the drop-down field, select Host Group and browse to and select the defined WebEx Services host group.
- Leave the DPI Classification field empty.
- Click the Add to Rules button.
- Repeat the above process to define each port/protocol and host group pair as an additional rule. When you are done, it should look something like below.
- When complete, click Save, and then Apply.
- Starting from the point that the Application is saved and applied, all traffic observed by Stealthwatch matching those parameters will be classified as the defined application, and it becomes available as an Application “type” in Flow Queries and is available to you in a myriad of different reports, as well as within policies.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: