In order to take advantage of all the features offered by our corporate web filter it must be placed inline with the outgoing internet traffic. The corporate policy is all traffic from remote sites must be passed through the corporate firewall before it allowed out of the network. Another requirement is AnyConnect is used for remote access. These requirements present several challenges.
Example topography.
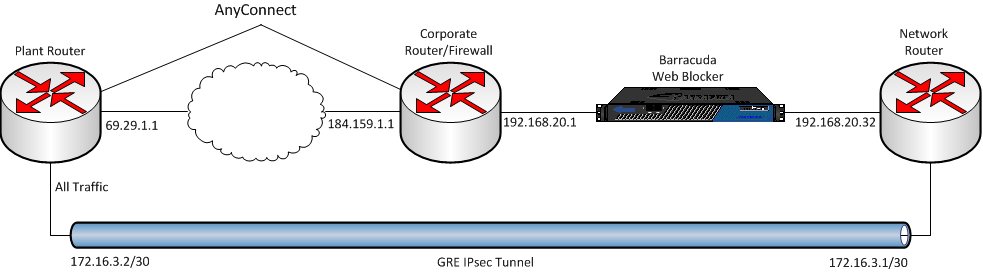
Following is how I attacked the challenges.
Corporate router/firewall
1. A static NAT had to be added to the corporate firewall so VPN tunnel can be established on back end router. Having the tunnel on the back end router will force outbound internet traffic to pass through the Barracuda web filter and the corporate firewall.
ip nat inside source static udp 192.168.20.32 500 184.159.1.1 500 extendable
ip nat inside source static udp 192.168.20.32 4500 184.159.1.1 4500 extendable
2. Allow the VPN traffic to pass through the firewall.
ip access-list extended VPN-hosts-ACL
permit udp host 69.29.1.1 host 192.168.20.32 eq isakmp
permit udp host 69.29.1.1 host 192.168.20.32 eq non500-isakmp
Notice the destination host is the internal IP of the back end router. This is because the external to internal NAT is done before the ACL is checked. You need to review the ingress flow of you router to determine when the natting takes place.
Configure the back end network router tunnel
crypto keyring Plant
pre-shared-key address 69.29.1.1 key cisco123
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp profile Plant
keyring Plant
match identity address 69.29.1.1 255.255.255.255
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec profile Plant
set transform-set ESP-3DES-SHA
interface Tunnel2
description tunnel to Plant
ip address 172.16.3.1 255.255.255.252
tunnel source FastEthernet0/1
tunnel mode ipsec ipv4
tunnel destination 69.29.1.1
tunnel path-mtu-discovery
tunnel protection ipsec profile Plant
Plant router configuration
1. Configure tunnel
crypto keyring pre-shared-keys
pre-shared-key address 184.159.1.1 key cisco123
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp profile Plant-Office
keyring pre-shared-keys
match identity address 192.168.20.32 255.255.255.255
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec profile Plant-Office
set transform-set ESP-3DES-SHA
interface Tunnel1
description tunnel to Main office
ip address 172.16.3.2 255.255.255.252
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source Dialer1
tunnel destination 184.159.1.1
tunnel mode ipsec ipv4
tunnel path-mtu-discovery
tunnel protection ipsec profile Plant-Office
Notice on the isakmp profile that the matching identity address is the internal IP of the destination tunnel.
2. Force all traffic through tunnel. This was implemented using SLA so the default gateway could be superseded by the tunnel gateway.
ip sla monitor 11
type echo protocol ipIcmpEcho 172.16.3.1 source-interface Tunnel1
timeout 500
ip sla monitor schedule 11 life forever start-time now
track 1 rtr 11 reachability
ip route 0.0.0.0 0.0.0.0 172.16.3.1 track 1
ip route 0.0.0.0 0.0.0.0 Dialer1 20
3. Since all traffic is forced through the tunnel, a local policy base route is required so SSH and AnyConnect traffic will route to the external interface.
ip access-list extended Local-PBR
permit tcp host 69.29.1.1 eq 22 any
permit tcp host 69.29.1.1 eq 8433 any
route-map VPN-PBR permit 10
match ip address Local-PBR
set interface Dialer1
ip local policy route-map Local-PBR
4. Configure plant router WEBVPN.
It should be noted that the AnyConnect VPN is made to the corporate firewall instead of the back end router because split tunneling is use on the VPN. Therefore only business related traffic passes through the VPN.
Since I'm not a certified Cisco engineer, so it took me a couple of days to get all this worked out but it works like a top. Hope this post will save some time for others that may have this same scenario.