- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ZBFW Self-Zone Integration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-01-2013 08:38 PM - edited 03-08-2019 06:50 PM
Hello Everyone,
Today I am going to cover a topic that most people is confused about or have some questions about it, this is the Self-Zone integration with ZBFW.
We are going to start by mentioning some basic stuff regarding ZBFW
Class-maps:
What we use to match the traffic
Policy-maps:
What we use to set an action on the traffic previously matched.
Service-Policy:
Where we aply the Policy-map (the actions)
Actions on a Policy-map:
Pass:
Equal to a permit on an ACL, Unidirectional, no information being saved on the stateful table of the firewall.
Drop:
Equal to a deny on an ACL.
Inspect:
Bidirectional, keeps the information regarding the session being inspection on the FW stateful table.
**************************************************************************************************************************************************************
The Self-Zone:
Is the FW zone that includes all of the Router interfaces IP addresses (even for interfaces not attached to any specific zone).
You must think of the self-zone as the router itself so when we configure a policy including the Self-zone is related to:
-Traffic to the router
-Traffic from the router
So when someone asks the following
What Traffic Should I Consider When I Deal With The Self-Zone?
You should answer:
-Managment plane traffic (SSH,Telnet,etc)
-Control plane traffic(Routing Protocols)
Another common question is:
Why would you even consider to use the Self-Zone?
Well, if you want to protect your network from any kind of attack you configure a FW to prevent attacks from reaching your network but if you leave your router without the Self-Zone anyone could get into the router and change the configuration, open backdoors,etc.
In order to avoid this vulnerabilities using the Self-Zone is a MUST.
*************************************************************************************************************************************************************
Key Facts about the Self-Zone:
- By default there is no policies for the Self-Zone so traffic from and to the router will be allowed
- You do not have to manually create the Self-Zone. By default it's created, you just need to call it.
- As soon as you configure one zone-pair that involves the Self-Zone traffic from any zone to the Self or from the Self to any zone will be filtered
- Traffic from a host behind a router interface that does not belong to any ZBFW zone will be allowed to reach the Router IP addresses (Self-Zone)
- We cannot Inspect a class-map that we matched via a layer 7 protocol/application (We can only inspect layer 4 class-map matches)
- Before version 15.1 OSPF and EIGRP neighbor relationships were allowed without the need of a policy if using the self-zone but after 15.1 we now must PASS this protocols (RIP and BGP as depend of UDP and TCP respectively will always need a policy allowing the traffic if using the self-zone)
- For IPSec VPN sessions we only need to PASS the control channel negotiations (Isakmp) so UDP 500 and UDP 4500 if NAT-T is required (As you can see ESP/AH is not required to configure in order to bring the tunnel up.
**************************************************************************************************************************************************************
Lab Scenario
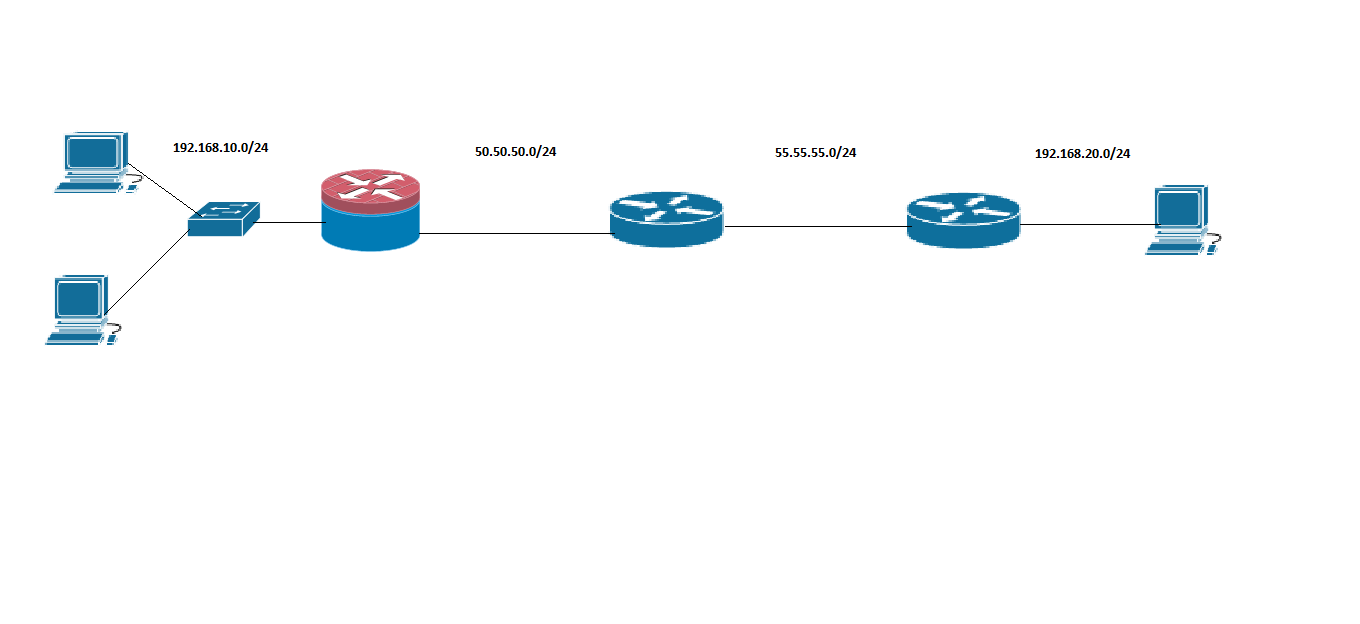
As usual Step number one: "Determine what needs to be allowed"
From Self and Inside
All traffic should be Allowed
From Self and Outside:
In this case we have a L2L between the FW at 50.50.50.1 (in the left) and the 55.55.55.2 (in the right) of the image.
We also are running OSPF between the FW and the ISP (Router in the middle).
Managment access to the router is configured via SSH and Telnet.
We must implement the Self-Zone without dropping any of this connections.
Configuration:
First lets work from Inside to Self and Self to Inside:
ip access-list extended Self_and_Inside
permit ip any any
class-map type inspect Inside_Self
match access-group name Self_and_Inside
policy-map type inspect Inside_Self
class Inside_Self
inspect
Policy-map type inspect Self_Inside
class Inside_Self
inspect
zone-pair security Self_to_Inside source Self destination Inside
service-policy type inspect Self_Inside
zone-pair security Inside_to_Self source Inside destination Self
service-policy type inspect Inside_Self
***As we can see we are allowing everything and then we are inspecting it. We even use the same class-map***
Now let's configure the interaction between the Outside zone and the Self-Zone:
1-Match the VPN traffic to the router(No need to match UDP 4500 as NAT-T is not being used)
ip access-list extended VPN_Self
permit udp any host 50.50.50.1 eq 500 (Isakmp)
2-Match the OSPF Traffic to the router
ip access-list extended OSPF_Self
permit ospf any host 50.50.50.1
3-Match the OSPF traffic from the router
ip access-list extended OSPF_From_Self
permit ospf host 50.50.50.1 any
4-Match the VPN traffic from the router
ip access-list extended VPN_From_Self
permit udp host 50.50.50.1 eq 500 any
Ip access-list ext Managment_In
permit tcp any host 50.50.50.1 eq 22
permit tcp any host 50.50.50.1 eq 23
ip access-list extended Managment_Out
permit tcp host 50.50.50.1 eq 23 any
permit tcp host 50.50.50.1 eq 22 any
Class-Map Setup
class-map type inspect match-any Self-Out
match access-group name OSPF_From_Self
match access-group name VPN_From_Self
match access-group name Managment_Out
class-map type inspect match-any Out-Self
match access-group name OSPF_Self
match access-group name VPN_Self
match access-group name Managment_In
Note:The match protocol command (A layer 7 matching) can only be used with the self-zone if the policy action is set to PASS, otherwise the router will not take the configuration.
Policy-Map setup
policy-map type inspect Self_Out
class Self-Out
pass
policy-map type inspect Out_Self
class Out-Self
pass
Service-Policy Setup
zone-pair security Out-To-Self source Outside destination Inside
service-policy type inspect Out_Self
zone-pair security Self-To-Out source Self destination Outside
service-policy type inspect Self_Out
Any questions you have you can email me at julio17carvajal@hotmail.com or jcarvaja@cisco.com
Regards,
Julio Carvajal
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Excellent doc Julio !
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
Thank u for your comment Tony,
Regards
Julio
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For Self_Out, it should same as Self_Inside.
I mean Self_Any should always be permitted, so we can make configuration simpler by no define the policy for Self_Any(pass by default).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How to apply this self zone to interface ??
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Because zone based firewalls require quite a bit of effort to write the first time I have written a Config Wizard for 890 series routers to speed the process up. I often use this for other routers as well, just copying the ZBF bit out.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
amazing Julio !!! thank you !!!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: