- Cisco Community
- Technology and Support
- Service Providers
- Service Providers Knowledge Base
- ASR9000/XR: BNG deployment guide
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-06-2012 08:01 AM
- Introduction
- Access models
- Using Control Polices
- Address assignment options
- Applying configuration to a subscriber
- Quality of Service
- Multicast and video distribution
- Call Admission Control
- AAA
- Subscriber Services
- Redundancy and fan out
- Wholesale Models
- High Scale Deployment Best Practices
- Related Information
Introduction
Broadband deployments are complex because of the options you have, varying needs in terms of deployments, the combination of technologies and many other reasons. In this article we'll go over the various designs, options and service deliverables that you can achieve with the ASR9000 BNG solution.
Access models
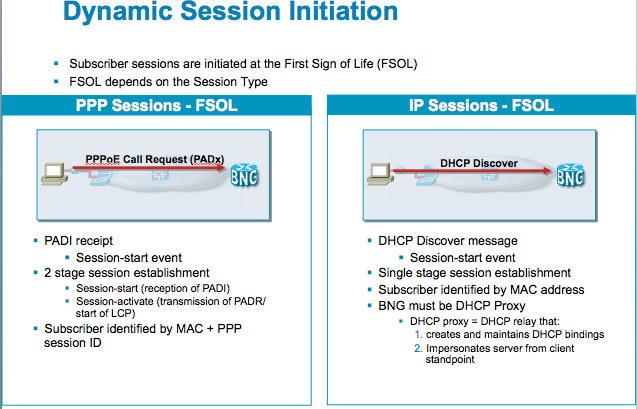
One of the decissions to be made when running BNG is the type of access that is preferred. There are 2 key options for the ASR9000 which is PPPoE (PPP over Ethernet) or IP sessions. Both can run on single or double tagged subinterfaces.
PPPoE sessions are triggered by the reception of a PADI and IP sessions are created by using DHCP as a session trigger.
In XR4.2.1 we can also use the "packet trigger" which means that an unclassified L3 address can be used to start a new session.
Also one has to decide on the Access interface, whether that is a single physical interface or access via bundles with multiple members. When choosing bundles the next decission is whether the members run in an active/active mode (that is all members are forwarding traffic) or in an active standby mode (whereby there is one link not forwarding traffic and only taking over when one of the member(s) fails).
Bundles vs Phyiscal interfaces
In the ASR9000 the use of a phyiscal interface, whether that be a GigabitEthernet or a TenGigabitEthernet interface are terminated on the linecard, this significantly increases the scale as effectively every linecard becomes its own controller of the sessions.
When you are running bundles, the sessions are then maintained on the RSP.
The LC's currently have their own Control Policy Engine, PPP manager and AAA processes. But they lack IGMP and LI today. This means that if you are planning to use LI or IGMP or parameterized QOS LC based subscribers should not be the choice for you.
You can use bundle interfaces with one member and disabling LACP to pull the subs to the RSP so that you have access to these features:
interface GigabitEthernet0/0/0/0
bundle id 100 mode on
When you are using bundle interfaces, all features enabled on the subscriber are programmed to the NP's where the bundle has members on.
So running a bundle with 2 members effectively creates the subscriber on both NPU's for those members, because of the phenomenal failover support it has.
For downstream loadbalancing we can use destination based hashing, which is the subscriber's ip address, so we always hash the traffic from one subscriber over 1 member, but the subscribers would be spread over the members based on their destination address.
The following configuration takes care of that:
interface Bundle-Ether100
bundle load-balancing hash dst-ip
When one member fails, the traffic is carried over to the other member seemlessly.
For the upstream direction, we can't control how the traffic arrives to us, which is controlled by the access layer device, whether that be your metro device or DSLAM.
Linecard based subscribers
This is an XR 5.1.1 deliverable. LC subs will increase the scale even further as it distributed the control plane to the LC as opposed to the RSP.
Hardware requirements
The hardware you require for BNG on the ASR9000 is:
- Any typhoon linecard such as the A9K-MOD80-SE, A9K-24x10, 36x10 and MOD160.
- A9K-RSP440-SE
Note that for both the RSP and the linecard we need to have the "SE" or Service Edge variant.
Also the ASR9001 will support BNG.
Trident linecards are not supported for subscriber termination, but they can be used as core facing linecard for transport
The MOD80 is a 2NP based linecard. Per NP we support 32k sessions with 64k per linecard.
Per Port we support up to 8K sessions when they are running QOS. This because of the QOS architecture within the NP that won't allow more then 8k parent shapers per phyiscal port. (that restriction is partially lifted in XR4.3.1 which allows for QOS chunk allocation more dynamically. You still have 32k parent shapers, but you can instruct a subinterface to use a chunk. This means a limitation of 8k per vlan, 32k per NPU)
These retrictions apply regardless of whether you are using LC or RSP based subscribers.
All linecards that run BNG need to be of the Typhoon kind (NP4). Your core facing interfaces if not running BNG can be Trident based or SIP700 based. However if you are using L2TP, then your core facing LC's need to be NP4 also. This is because the L2TP decap is not implemented in SIP or Trident which is handled by the core facing LC in the downstream direction.
Radius Source Ports
Each LC is assigned a source port range for radius, so while all LC's present themselves as a single NAS-ID, the source ports they are using effectively identify the node within the system. This is transparent for your use and nothing needs to be configured for that.
However it is imperative that your radius server supports extended source-ports (so the combination of source-port + radius-request-ID) defines a unique request. This is the same in IOS otherwise you can only support a call window of 256 (as the radius ID is only an 8 bit field). So check your radius-server capability!
For example see this radius request received on a radius-server:
Tue Apr 5 16:55:45 2011: [17224] message received from 3.0.0.234/49080.12 code=4, length=361
Tue Apr 5 16:55:45 2011: [17224] Acct-Interim-Interval = 60
Tue Apr 5 16:55:45 2011: [17224] Acct-Status-Type = Stop
Tue Apr 5 16:55:45 2011: [17224] Cisco-avpair = "if-handle=167774432"
Tue Apr 5 16:55:45 2011: [17224] Cisco-avpair = "client-mac-address=0010.9441.0001"
Tue Apr 5 16:55:45 2011: [17224] Acct-Session-Id = "00000054“
This radius (accounting) request was sent from UDP Port 49080 and its radiusID is number 12
You can check in LPTS in IOS-XR where that source port is mapping to:
RP/0/RSP1/CPU0:A9K-BNG#show lpts pifib hardware entry br location 0/1/CPU0 | i 49080
Tue Apr 5 17:22:52.941 EST
(VRF:0) any.49080 , any.any UDP any 48 deliver 48
If you decode 48 into binary: 48 =======> 0 0 0 0 1 1 0 0 0 0 (Binary of 48)
The "1" represent the RSP's in the middle slot of a 10 slot chassis!
PPPoE vs DHCP/IP-sessions
Broadband access has natively been using PPP based access, which originates from the dial days, whereby modems dialing into a modem-bank/access server allowing the transmission of data packets by encapsulating them in PPP packets. When access evolved to higher speeds using DSL (effectively ATM over the phone line), PPP was still used in the flavor of PPPoA (PPP over ATM).
Now that the aggregation point's uplinks are transitioning from ATM based to Ethernet based and the fact that there is Ethernet directly to the home, PPPoE has made a strong hold in the access layer.
Still with DSL in the first mile, DSLAM's may convert the PPPoA session into PPPoE towards the aggregator leaving PPP with a (well deserved) strong precense in the access.
In a transition to an all ethernet, there is no need per-se to run PPP at the access. PPPoE requires a client (which nowadays come natively in many operating systems however), which created the opportunity for a more simple approach of direct IP access using DHCP as a signal to trigger the session creation.
Drrivers of PPPoE are:
- Ability to run multistack, each Layer 3 protocol is negotiated separately via their CP (Control Protocol) during the NCP phase (Network Control Protocol)
- Authentication natively build in via protocols such as CHAP, PAP, MS-CHAP etc
- Link control (~negotiable options during LCP)
- Keepalives
- Ability to aggregate multiple lines together into a single link such via MLP (Multilink PPP)
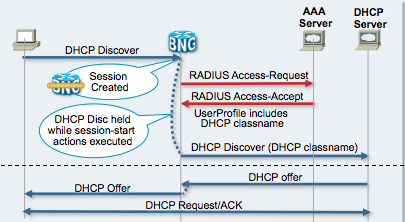
IP sessions don't have an authentication natively build in as there is no concept of username/password here, but with BNG deployments there are options now by having the BNG construct a username out of options of the DHCP discover or other fields such as MAC address, access interface, VLAN etc.
First Sign of Life comparison between PPPoE and IPoE sessions
Access Interfaces
This is the basic configuration to be setup in order to get PPPoE and IP sessions running.
Note that PPP and IPoE sessions can co-exist on the same parent interface as well as on the same subinterface.
This this is a base configuration example to setup the FSOL handling for PPPoE or IP sessions.
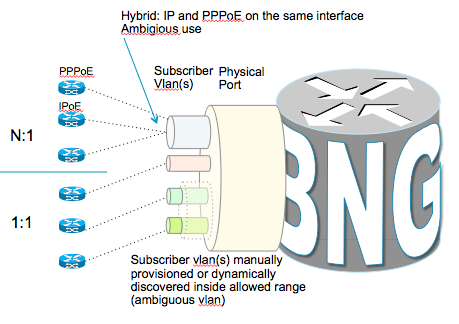
Using ambigious vlans
Originally for double tagged traffic, also known is QinQ or QiQ, we had to explicitly configure the inner and outer vlan combination for each possible termination point. In ASR9000/XR we can define ambigious ranges allowing us to specify the outer vlan only and an inner range.
The most common deployment scenario for QIQ is whereby the outer vlan represents the dslam and the inner vlan represents the subscriber, obviously configuring 64k subinterfaces is not very easy to manage and the Ambigious vlan support greatly reduces operational overhead, large configs and provides for much more simplicity:
Configuration example:
interface Bundle-Ether1.50
service-policy type control subscriber PPP_IP_PM1
pppoe enable bba-group default
encapsulation ambiguous dot1q { any | <vlan range> }
dot1ad { any | <vlan range> }
dot1q <vlan#> second-dot1q { any | <vlan range> }
dot1ad <vlan#> second-dot1q { any | <vlan range> }
DHCP/IP sessions
PPP sessions have a native keepalive build in. If keepalives are not sent between the BNG and the client, the sessions are automatically torn down. IP sessions don't have a native keepalive mechanism and some implementations opted for an ICMP or ARP keepalive methodology to detect absent IP sessions as opposed to relying on (potentially long) DHCP lease timers.
ASR9000 does not have ICMP or ARP keepalives for IP sessions rather instead we have a different mechanism of lease-proxy which is elaborated on in this section.
Restart handling
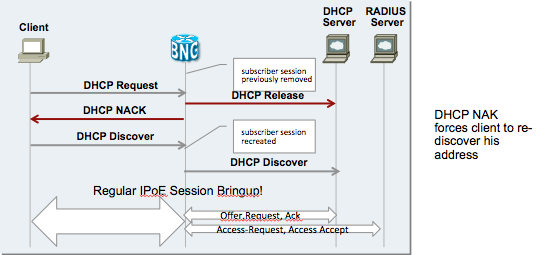
Problem domain 1:
IPoE sessions are initiated upon receipt of a DHCP discover and can be terminated prior client’s IP address lease expires/is released by:
- CoA Account-Logoff/PoD
- Session Administratively cleared
- Reload
Need a way to recreate session if client lease is still valid:
Once we have marked the Binding in the dhcp proxy on the BNG as "stale" due to one of the reasons mentioned above, a subsequent DHCP request from the client (eg on renew) is NAK'd to the client who will then faill back to a discovery mode upon which we can recreate the session.
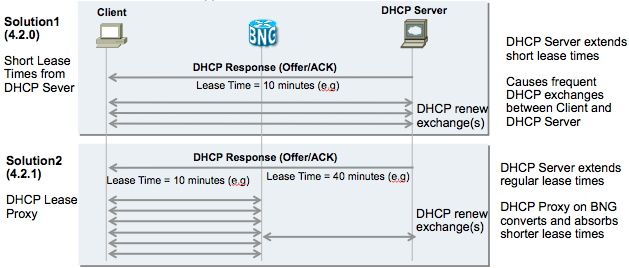
To support a sort of keepalive mechanism we can shorten the lease time, which will require the session to renew its lease at half the lease time. So we effectively have a keepalive mechanism at half-lease time in this scenario.
This inherently increases the load on the dhcp server because the BNG will forward the renew requests to the dhcp server and when Acknowledged it will maintain the binding and the session.
A smoother solution is the concept of "lease proxy". This means that eventhough the server offers a lease, in this example of 40 minutes, the BNG advertises a lease to the client of a configurable time, in this example 10 minutes.
Every 5 minute interval the client will renew, but now the BNG intercepts and re-acknowledges the lease to the client, as opposed to relying on the dhcp server to ack the renew.
At half the lease time, here 20 minutes, we renew with the dhcp server to maintain proper state.
DHCP lease limits
Lease limit and Lease proxy for DHCP subscribers
Lease limit for a given proxy profile can be specified for:
per remote id:
eg.,
dhcp ipv4
profile dhcp-red proxy
limit lease per-remote-id 1000
per circuit-id:
eg.,
dhcp ipv4
profile dhcp-green proxy
limit lease per-circuit-id 1000
or
per interface:
eg.,
dhcp ipv4
profile dhcp-blue proxy
limit lease per-interface 1000
Note that per circuit-id and per remote-id options are confined to any given access
interface. In other words, per circuit id limit on a given access interfaces doesn't affect
or influence the circuit-id limit configured for any other access interface
Lease proxy:
DHCP lease proxy is also known as DHCP split lease. With this implementation, the DHCP proxy
ie., BNG router will renew the lease of the client without contacting the DHCP server. The
lease proxy value configured is assumed to be lower than the server lease. Following terminologies
are used:
i) Client<->Proxy is the client lease
ii) Proxy<->Server is the proxy lease
ASR9K is the DHCP proxy
Lease proxy benefits include:
a) shorter client lease times and longer proxy lease
b) Proxy can respond faster to renews at the network edge
c) Reduces load on centralized DHCP servers for renewal processing
Configuration:
dhcp ipv4
profile dhcp-red proxy
RP/0/RSP0/CPU0:BNG1(config-dhcpv4-proxy-profile)#lease proxy client-lease-time ?
<300-4294967295> Value of lease proxy client-time in seconds
dhcp ipv4
profile dhcp-red proxy
lease proxy client-lease-time 300
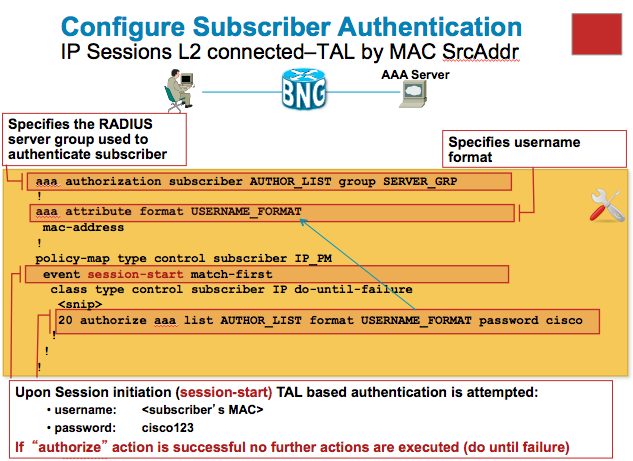
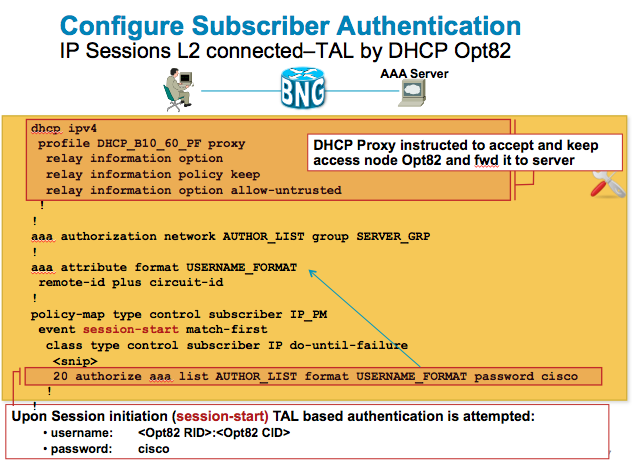
Example TAL (Transparent Autologon) use case 1
TAL or transparent autologon is one of the most commonly used access scenarios for IP sessions.
You can authenticate the user on mac address or option 82 information. The following use cases depict on how to set that up with the ASR9000 BNG implementation.
Example TAL use case 2
IP sessions and security forwarding
When your access interface is configured for IP it by nature can start forwarding IP already. A session that takes a static source ip can start forwarding traffic just fine then.
This could be a security issue and this has been done at the explicit request from some our initial adopters of A9K BNG.
Downstream traffic can only flow on AMBIGUOUS vlans when we have a session since the mapping from destination IP to mac and vlan is only held by the dhcp binding. In UNAMB scenarios, we could technically send traffic down to the sub.
UPstream traffic can be mitigated by either using:
- uRPF
- ACL
ACL being a far less pps implication then uRPF.
also uRPF will not necessarily capture all issues, especially when an ip source is chosen in the same range as the unnumbered or designated address of this access interface.
When you apply an ACL, make sure it allows DHCP to go through.
Packet trigger or unclassified Source
This implementation allows for IPoE subscribers to be established based on
a received packet from an IP source on the access interface when the "unclassified
source" is enabled. Typically, the sessions will be restricted to packets originating
from a particular network. Multiple matching criteria may be specified to match packets
from discontiguous networks. In addition, the packets may be subject to radius based
AAA for a successful session bringup. An access interface may be configured to support
both DHCP and PKT triggered sessions
In an ideal network, the subscriber would first send an ARP request to the access
interface and if the packet matching criteria are met, this in itself is a sufficient
condition to bringup the IPoE session. However, if there is a burst of traffic with
unique flows, this could overwhelm the BNG router in terms of processing each packet
to determine if it is a IPoE (PKT) candidate. The software limits the amount of in-flight
requests to 200. In cases where traffic rates for IPoE-PKT sessions are high (>120 pps) and
there are also parallel DHCP based sessions creates in progress, it may be desirable to
configure static policer on the line cards. Based on testing results, a policer rate of
200 per LC is shown to handle this stress condition satisfactorily.
Configuration:
RP/0/RSP0/CPU0:BNG1#config
Wed Jun 13 14:20:40.883 PDT
RP/0/RSP0/CPU0:BNG1(config)#lpts punt police location 0/0/cpu0 protocol unclassified rsp rate 200
aaa attribute format ip-plus-mac
format-string length 253 "%s:%s" addr client-mac-address
!
interface Bundle-Ether10.41
ipv4 address 21.1.1.1 255.255.255.0
service-policy type control subscriber ipsub_policy1
encapsulation dot1q 30
ipsubscriber ipv4 l2-connected
initiator dhcp
initiator unclassified-source
!
!
policy-map type control subscriber ipsub_policy1
event session-start match-first
class type control subscriber class-dhcp do-all
1 activate dynamic-template ipsub_template
3 authorize aaa list default identifier circuit-id password dhcp123
5 activate dynamic-template acct-default
!
class type control subscriber class-pkt do-until-failure
1 activate dynamic-template ipsub_template
3 authorize aaa list default format ip-plus-mac password abc123
5 activate dynamic-template acct-default
!
!
end-policy-map
!
class-map type control subscriber match-any class-pkt
match source-address ipv4 192.1.0.0 255.255.0.0
end-class-map
!
dynamic-template
type ipsubscriber ipsub_template
ipv4 unnumbered Loopback1
!
!
Using Control Polices
One integral part of the BNG solution in XR is the use of control policies.
With control policies you are able to manage the sessions life while various events on the session are triggered.
You can handle these events or ignore them depending on your configuration and deployment needs.
User authentication/control
One key action in the control policy is obviously the authentication.
These can be executed via the command under the event/class:
- 10 authorize aaa list default identifier source-address-mac password cisco
- 10 authenticate aaa list default
Both of these will trigger a RADIUS access-request message, but the difference between the two is with the authorize statement we can compose the username ourselves regardless of what is received on the line, where as the authenticate statement uses the PPP chap or pap username and password received. The authenticate option for that reason only applies to PPP based sessions.
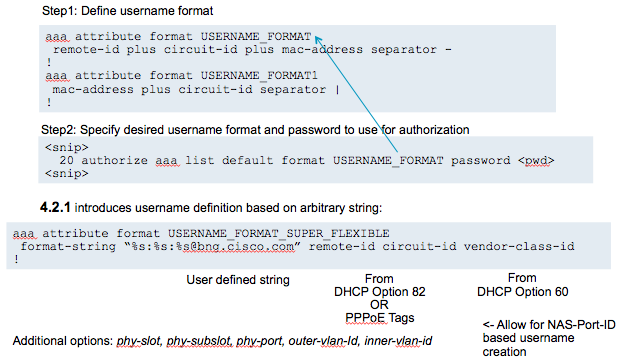
You can define the username in the authorize statement either inline as per example above or you can construct the username via a "formatted" way:
Note that an authentication does NOT have to succeed in order for BNG to bring up the session.
The activation of a dynamic template will create the subscriber interface regardless of the authentication result.
A failed authentication will result in an unauthenticated state and you'll be able to apply HTTP-redirect or restricted access on the session.
Nas identification
Source IP
Is by default selected of the interface's address that is used to reach the radius-server.
This is configurable to be overriden from this default.
RP/0/RSP0/CPU0:A9K-BNG(config)#radius source-interface <interface name>
Or per default configuration:
RP/0/RSP0/CPU0:A9K-BNG#show run | i radius-server
Fri Mar 16 12:40:15.791 EDT
Building configuration...
radius-server host 3.0.0.38 auth-port 1645 acct-port 1646
radius-server attribute list LIST
RP/0/RSP0/CPU0:A9K-BNG#sh route 3.0.0.38
Routing entry for 3.0.0.0/8
Known via "connected", distance 0, metric 0 (connected)
Installed Feb 22 15:42:37.812 for 3w1d
Routing Descriptor Blocks
directly connected, via MgmtEth0/RSP0/CPU0/0
Route metric is 0
No advertising protos.
RP/0/RSP0/CPU0:A9K-BNG#sh run int mgmtEth 0/rsP0/CPU0/0
Fri Mar 16 12:40:26.121 EDT
interface MgmtEth0/RSP0/CPU0/0
ipv4 address 3.0.0.233 255.0.0.0
!
RADIUS:
Thu Mar 15 11:55:12 2012: [18848] NAS-IP-Address = 3.0.0.233
Nas-Port-ID
Attribute 87 can be filled with the configuration like this:
aaa attribute format NAS-PORT-ID
circuit-id plus remote-id
!
aaa radius attribute nas-port-id format NAS-PORT-ID
Nas-ID
Attribute 32 is the BNG's hostname, always and only configurable when changing the router's hostname.
Example:
RP/0/RSP0/CPU0:A9K-BNG#sh run | i host
hostname A9K-BNG
RADIUS:
Thu Mar 15 11:55:12 2012: [18848] NAS-Identifier = "A9K-BNG"
Nas-PORT
Attribute 5
Is computed very flexibly configured on a per session type basis:
aaa radius attribute nas-port format e <format> [type <0-44>]
Format (32bits): entered as a string of letters:
Zero : 0
One : 1
Slot : S
Adapter : A
Port : P
(Outer) VLAN Id : V
Session-Id : U
Inner VLAN ID: Q
Ex “SSSSAAPPPPPVVVVVVVVVVVVVVVVVVVVV”
Type
ETHERNET 15
PPPOEOE 32
PPPOEOVLAN 33
PPPOEOQINQ 34
VIRTUAL_PPPOEOE 35
VIRTUAL_PPPOEOVLAN 36
VIRTUAL_PPPOEOQINQ 37
If type is omitted it will apply and be used for any session without a more specific type definition.
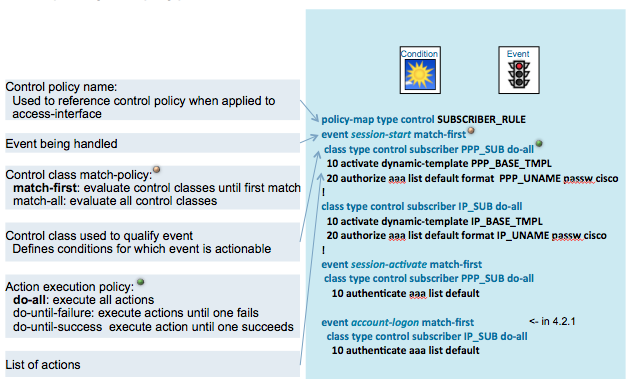
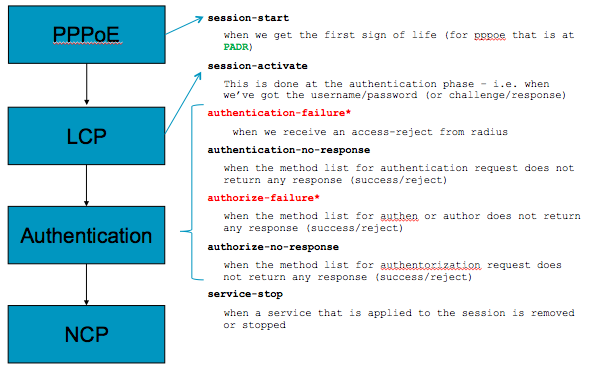
Control policy Events, Classes and Actions
The folllowing pictures shows how everything ties together in a control policy:
The diagram below shows where the various events would be triggered for a PPPoE session.
Note that the session activate event is only applicable to PPP sessions.
You need to make sure that the session-start event has a template defined with the lcp paramters
which are used during LCP.
the power of the solution, amongst many others, is the differentiation you can do between authentication failures as well as no response,
so you can act upon a faulty username differently then a radius-server not responding.
Failover for that reason can be embedded in the control policy like this:
event session-activate match-first
class type control subscriber CLASS do-until-failure
10 activate dynamic-template TPL
20 authenticate aaa list default
event authentication-failure
class ...
10 "apply http redirect"
On authentication failure we an apply a layer 4 redirect service while keeping the session active.
event authentication-no-response
10 authenticate aaa list failover-list
If there was no response from radius, we can try a different radius-server list
Using Class-Maps
The class map definition allows you to control how the event triggered is handled.
Either the event is handled for the first class that is matched, or ALL classes for this event are evaluated as part of the event definition directive.
Example:
class-map type control subscriber match-any IP_SUB
match protocol dhcpv4
! The above would match specifically on IP subscribers only
class-map type control subscriber match-any PPP_SUB
match protocol ppp
! This example would match specifically on PPP subscribers only
Using these example classes allows you to have a single control policy that can handle events and use different actions per access category.
Available Match Criteria:
- Domain name: domain <string>
- Protocol: protocol { dhcpv4 | ppp }
- Source address: source-address { ipv4 | mac }
- User name: username <string>
- Authentication Status: authen-status { authenticated | unauthenticated }
- To negate match criteria: not <>
Available Match policies (as part of the class-map definition):
- match-any: match any of match clauses
- match-all: match all match clauses
If you only have 1 match clause in your class-map it obviously doesn't make a difference whether you choose match-all or match-any.
Also the class-maps allow for very extensive control of the event handling whereby you can handle a particular event differently for an unauthenticated ppp subscriber vs an authenticated ip subscriber or any combination of that of course!
Handling failed authentications
When an authentication fails for a subscriber against radius, we can still bring the user up by activating a dynamic template.
So the order of actions executed during an event is very important along with using do-until-success/failure etc.
For instance the following actions:
event session-start do-all
10 activate dynamic-template TPL
20 authorize aaa list default mac-address password cisco
would bring up the subscriber even with failed authentication.
In this example where the actions are effectively reversed:
event session-start do-until-failure
10 authorize aaa list default mac-address password cisco
20 activate dynamic-template TPL
would not bring up a user after authentication failure.
Alternatively, you can pull in the event for authorization failure and disconnect the service like this:
event authorization-failure do-all
10 disconnect
Or you can use the authorization failure to apply HTTP-Redirect and start a timer, so effectively allowing the user to login within that time before he is getting disconnected.
Account Logon
If the user failed authentication and has a restricted access service applied, we can force the user to go the web portal to provide credentials and try to login again, pay their bill etc.
The model is here that the user goes to a web page to provide credentials that are then send via a coa account logon to the BNG.
The BNG will generate an access request to authenticate using these credentials.
If it succeeds new attributes can be send in that access-accept to remove the restricted access or HTTP-R service.
How IP sessions /DHCP interact with AAA
Address assignment options
Obviously in order for a subscriber to have access to the network, an address has to be handed out. There are different options available for this that'll be listed out here.
Local pools (PPPoE)
When you have PPPoE based sessions, the easiest implementation is to define a local pool from which the addresses are handed out to the subscriber during IPCP
The associated configuration is:
pool vrf default ipv4 POOL
address-range 199.1.1.1 199.1.255.255
Multiple ranges can be provided and addresses in that range can be excluded.
Which can be monitored via this command:
RP/0/RSP0/CPU0:A9K-BNG#show pool ipv4
Allocation Summary
---------------------------------------------------
Used: 1
Excl: 0
Free: 65278
Total: 65279
Utilization: 0%
Pool VRF Used Excl Free Total
---------- ---------- ----- ----- ----- -----
POOL default 1 0 65278 65279
The Pool can either be referenced directly on the dynamic template which is activated to the subscriber during its event handling in the control policy like this:
This is the template that holds the base configuration for subscribers when this template gets activated on the session:
dynamic-template
type ppp TPL
ppp authentication chap
ppp ipcp dns 1.2.3.4 1.2.3.3
ppp ipcp peer-address pool POOL
ipv4 unnumbered Loopback1000
This template can then be referenced in an event handling of the control policy as with this example:
policy-map type control subscriber sub
event session-start match-first
class type control subscriber CLASS do-until-failure
10 activate dynamic-template TPL
Alternatively the POOL can also be referenced via Radius Attributes during the Access-Accept as per following example:
- With a Cisco-Avpair
user1@domain.com Password = "cisco"
Service-Type = Framed-User,
Framed-Protocol = PPP,
Cisco-avpair = "ipv4:addr-pool=POOL",
- Using an Ascend Attribute (number 218):
Ascend-Assign-IP-Pool = POOL
- Using an IETF Attribute (number 88):
Framed-Pool = POOL
- Alternatively, but uncontrolled is the use of the Framed-IP-Address magic number 255.255.255.254 which will instruct the NAS to do a "pool pick" from any pool available.
Using this method of locally defined pools on the BNG is by far preferred because it allows us to create a summary route and advertise the pool in its whole. This reduces significant amount of routing updates, but has the limitation that a full block is assigned to the BNG regardless of whether it needs it or not.
Pool advertisement
Can be done via the following methodology:
First define a summary route for the pool range:
router static
address-family ipv4 unicast
199.1.0.0/16 Null0
Next inject that summary route into your eg IGP via a redistribution command
router ospf CORE
redistribute static
When users come online they will have a /32 in the routing table which is then followed for forwarding rather then the summary route to NULL0.
Another "disadvantage" of this methodology is that you'll be drawing all 199.1.x.x traffic to the BNG regardless of whether there is a session or not. However the ingress LC's NPU will drop the packets in hardware in that case.
Radius based pools (PPPoE)
Instead of assigning a pool on the BNG, you can also outsource the pool management to a radius-server.
IT is recommended to have the radius server select a pool per BNG device, this in order to keep the model of summary advertisement.
If the pool attributes are distributed between different BNG's, you're required to inject the /32's which will put unnecessary burden on your IGP.
In this case you probably want to consider STUB areas to keep the /32's only floating in your OSPF STUB area and summarize them at the area border.
Radius based pools rely on the accounting mechanism from AAA to learn whether addresses are in use or not.
This requires a strong Accounting back end on the radius-server and obviously proper delivery of your AAA records.
Don't implement radius pools without AAA System accounting.
Static address assignment (PPPoE/IPoE)
Requires you most of the times to inject /32's into the IGP for proper routing if not part of a summary.
The way to achieve this is via the radius attribute Framed-IP-Address (IETF number 8).
IP sessions
IP sessions address assignment is done via a DHCP Server. IOS-XR release 4.3.0 will come with an on board dhcp server.
In today's model the dhcp server is responsible for handing out addresses which are picked based on the "giAddr" field in the dhcp discover which is filed in by the DHCP Proxy component of the ASR9000.
Static addresses are defined within the dhcp server.
The advertisement is here more simple since the unnumbered interface to the subscriber session provides the subnet it is serving hence the inclusion of this unnumbered interface in your IGP will take care of the proper routing:
In this example we set the dhcp server to 81.1.1.2, the giAddr for pool selection is set to the red value to instruct the dhcp server where to pick an address from. The giAddr selection in this example is based on the dhcp option 60, vendor Class which is matching a hex string.
dhcp ipv4
profile AutoSelectGiaddr proxy
class MATCHALL
match option 60 hex 68656C6C6F mask 0
helper-address vrf default 81.1.1.2 giaddr 10.1.1.254
!
class HardPhone1
match option 60 hex 4861726450686F6E6531 mask 0
helper-address vrf default 81.1.1.2 giaddr 10.1.1.254
!
class HardPhone2
match option 60 hex 4861726450686F6E6532 mask 0
helper-address vrf default 81.1.1.2 giaddr 172.28.15.254
!
relay information option
relay information policy replace
relay information option remote-id testme
relay information option allow-untrusted
!
interface Bundle-Ether100.2 proxy profile AutoSelectGiaddr
This combined with the following template configuration, the subscriber is unnumbered to loopback interface number 12.
dynamic-template
type ipsubscriber IPSUB
ipv4 unnumbered Loopback12
Which has then address in the same pool range as the giAddr and the dhcp server will want to set the default-router option to this value.
RP/0/RSP0/CPU0:A9K-BNG#sh run int lo12
Fri Mar 16 10:52:33.265 EDT
interface Loopback12
ipv4 address 172.28.15.254 255.255.255.0
Including Loopback 12 (passively) in your IGP will provide for proper downstream routing!
More information on the DHCP configlet is in the BNG training guide
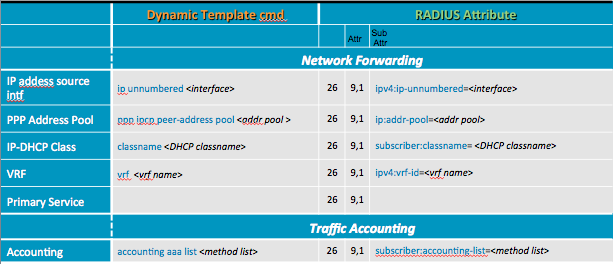
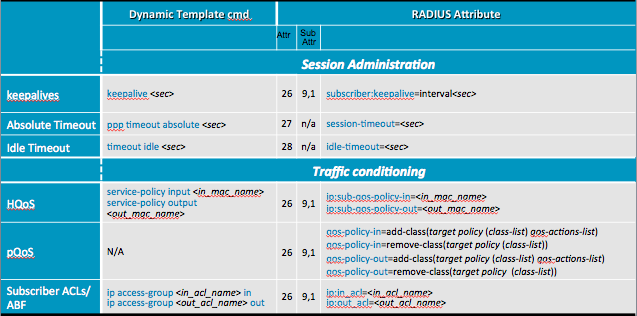
Applying configuration to a subscriber
Configuration can be applied to a subscriber via 3 methods and in order of preference from lowest to highest:
- Dynamic Template
- Radius/Access-Accept (also known as Policy PULL)
- COA (also known as Policy PUSH)
So that means that local template configuration can be overridden by RADIUS, which can be overidden by COA.
Here are a few examples on how to match a CLI Configuration to a radius attribute, full documentation is available in the XR configuration guide.
PPP timer configuration
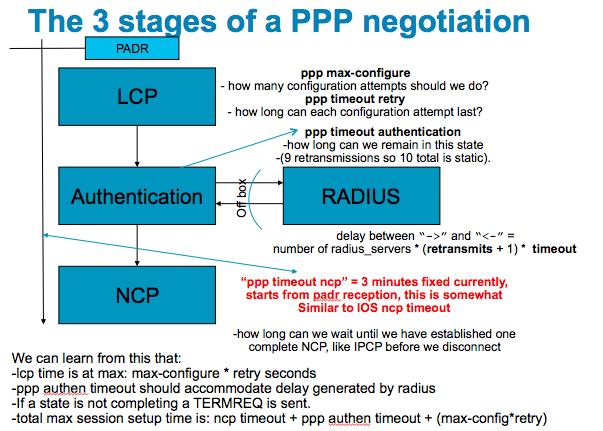
It is very important for any BNG implementation to properly define your PPP timer configuration to make sure that sessions establish, also under load and that we are not prematurely timing out, or working on establishment while the peer already gave up.
The picture below shows the different stages of PPP and which timers apply that need evaluation.
The referenced timers can be configured on the dynamic template for PPP subscribers:
dynamic-template type ppp <tmpl_name>
ppp max-configure <#>
ppp max-failure <#>
ppp timeout retry <sec>
ppp lcp delay <sec>
ppp lcp renegotiation ignore
ppp authentication { pap | chap | ms-chap }
keepalives { disable | <sec> }
ppp max-bad-auth <#>
ppp timeout authentication <sec>
ppp ipcp peer-address pool <poolname>
ppp ipcp mask <mask>
ppp ipcp { dns | wins } <server ip>
ppp ipcp renegotiation ignore
ipv4 unnumbered <interface>
Quality of Service
QOS application to the session can be done via static configuration in the dynamic template, or the policy-map name can be referenced via Cisco AVP's in RADIUS access-accept or COA requests.
This requires the configuration of the policy-map to be present in the XR configuration.
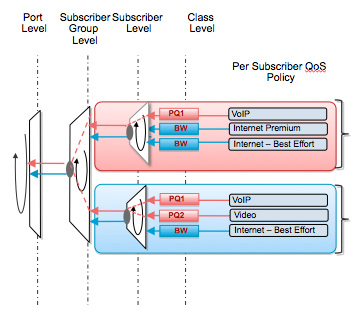
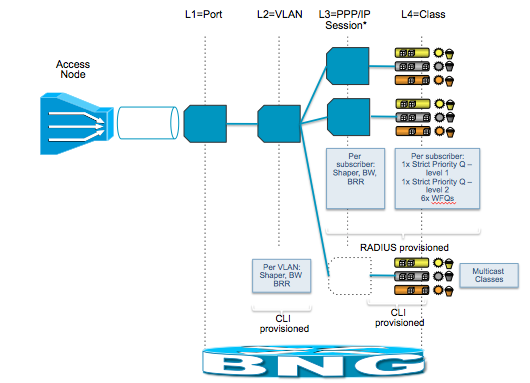
QOS can be applied at the port level, vlan level (subinterface) and at the session level with classes in a hierarchical manner.
This constitutes the 4 layers of QOS.
The following pictures shows the basics of the 4 layer QOS:
Which can be further expanded on in this picture:
Parameterized QOS
Parameterized QOS is a very powerful option in ASR9000 BNG. It allows you to construct the policy-map and its values from the AAA server.
pQOS only requires the class-map definitions to be present in XR configuration.
You can setup hierarchical policy-maps without a problem using pQOS.
Note however that if you have defined a static policy-map via configuration to the dynamic template or from radius
then you cannot override it or modify it with pQOS.
If you desire to use pQOS the initial policy-map needs to be pQOS'd also.
You can modify pQOS policies on a per class basis and while the session is active add or remove classes dynamically as you go!!
To see pQOS in action and the benefits see this video on demand BNG demo on YOUtube
VSA definition
Understanding the format of the Vendor Specific Attribute for Parameterized QOS (pQOS).
VSA 9,1 is Cisco-Avpair
TARGET:
sub – The QoS policy attached to the subscriber session. This implies that the CoA/Access-Accept target must be a subscriber session.
CLASS:
(class-default)
This example identifies the class “class-default” on the parent-policy.
(class-default,voip)
This example identifies a leaf class “voip”. This class will be added to or removed from a nested child policy specified under the class “class-default” of the policy attached to the target.
(class-default,voip-aggregate,voip-1)
This example specifies a leaf class “voip-1”. This class will be added to or removed from a nested child policy specified under the class “voip-aggregate” of the policy which is in turn nested under “class-default” of the policy attached to the target
ACTIONS:
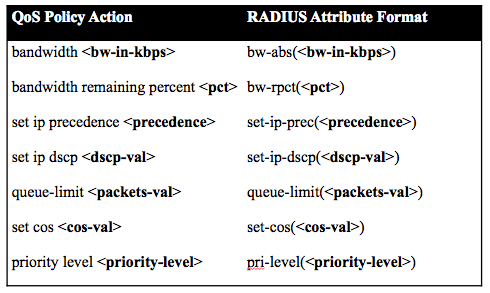
See this next section on how to map IOS-XR MQC (modular Qos configuration) actions to the parameterized QOS equivalent.
Supported pQOS actions:
Examples
Policing
CLI Equivalent: police <bps> <burst-normal> <burst-max> <burst-size> conform-action <action> exceed-action <action> violate-action <action>
police(CIR,CBS,PIR,PBS,conform-action,exceed-action,violate-action)
VSA value: qos-policy-in:add-class(sub,(voip),police(200000,9216,0,0,transmit,drop,drop) )
Shaping
CLI Equivalent: shape <shape-rate>
VSA value: qos-policy-out:add-class(sub,(class-default),shape(14700))
For complete COA examples check the Change of Authorization document
Multicast and video distribution
Coming soon!!
Call Admission Control
Unlike IOS, ASR9000/XR BNG has no explicit call admission control configuration as that is natively build into the system.
When resources are running slow or the system experiences internal back pressure to do slow responses on function calls
the number of in flight sessions increases which are then throttled back down at the access interface.
Most of the time you may want to control the number of in flight sessions so you can streamline the number of radius access requests that are being sent to the RADIUS server.
The way to monitor and control the in flight sessions is via this command :
RP/0/RSP0/CPU0:A9K-BNG#show pppoe summary total location 0/rsP0/CPU0
....<output omitted>...
==============================
Flow Control
==============================
Limit 2000
In Flight 0
Dropped 0
Disconnected 1
Successful 9
Limit means the number of in lfight sessions you want to control on a per node basis. A node constitutes a pppoe processing entity which is either the LC for phyiscal interface based sessions or the RSP when using bundle interfaces. This number is configurable via the followingcommand:
RP/0/RSP0/CPU0:A9K-BNG(config)#pppoe in-flight-window 2000
Default value is 200, recommended for RP-based subscribers. Recommended value for LC-based subscribers is 50.
In Flight is the number of sessions we are currently handling and have not fully established yet. A fully established session is the signal from the session control entity that the subscriber interface is up and forwarding
Dropped are the sessions when the in flight session number exceeds the Limit set.
Disconnected how many sessions ahve been disconnected for normal reasons, eg send a PADT etc.
Successful is the number of sessions that we successfully established over time on this node
AAA
Throttling
This feature supports throttling of access (authentication and authorization) and accounting records
that are sent to the radius server. Throttling rate can be configured separately for access
and accounting requests. When the threshold is reached for a server, no more requests of that type
will be sent. A retransmit timer is started when the threshold limit is reached. After expiry of
the retransmit timer, the queue is checked to see if the outstanding requests is less than the
configured limit. If so, then the request is sent out to the radius server
AAA throttling can be configured globally or at the server group level. Throttling configured
for the server group will take precedence
configuration:
radius-server throttle access 100 access-timeout 3 accounting 150
aaa group server radius my-grp
server 1.74.11.103 auth-port 1812 acct-port 1813
server 1.76.30.103 auth-port 1812 acct-port 1813
throttle access 200 access-timeout 3 accounting 120
!
Subscriber Services
Services constitute a set of features under a common umbrella.
These features are enabled together constituting the service defintion.
For instance you can allow users to access or deny parts of the network, or modify its qos parameters.
Services are defined via the dynamic template in IOS-XR.
dynamic-template type { ppp | ipsubscriber | service } <tmpl_name>
<attribute-list>
There are 3 types of templates:
ppp: for configuration on PPP sessions (both PTA and LAC)
ipsubscriber: for configuration on IpoE sessions
service: contains configuration commands for all types of sessions
The following is an example of a service definition:
dynamic-template
type service SERVICE_1
service-policy output testme
ipv4 access-group lab-video ingress
The following set describes a few RADIUS/COA templates to activate or deactivate services on a subscriber.
|
Operation |
RADIUS attributes set to achieve that operation |
|
Account Logon |
attribute 44 “<string>” attribute 1 "<username> Cisco-avpair = "subscriber:password=<subscriber password> Cisco-avpair = "subscriber:command=account-logon" |
|
Account Logoff |
attribute 44 “<string>” Cisco-avpair = "subscriber:command=account-logoff" |
|
Account Update |
attribute 44 “<string>” Cisco-avpair = "subscriber:command=account-update” <radius attributes to set/update> |
|
Service Activate |
attribute 44 “<string>” Cisco-avpair = "subscriber:command=activate-service" Cisco-avpair = "subscriber:service-name=<service-name>” |
|
Service De-activate |
attribute 44 “<string>” Cisco-avpair = "subscriber:command=deactivate-service" Cisco-avpair = "subscriber:service-name=<service-name>” |
Attribute 44, or accounting session ID is always used for fastest lookup of the subscriber session.
The subscriber password is a special encoded string by providing a seed authenticator together with a hashed MD5 password of that seed.
COA tool is available on the forum for Windows, MAC/OSX and Linux.
Redundancy and fan out
Redundancy is obviously very important these days and while IOS-XR supports process restart and process crashes without affecting the subscribers there are additional options available to increase your density and protect against failures.
Cluster and Satellite are part of the ASR9000's nV concept (Network Virtualization).
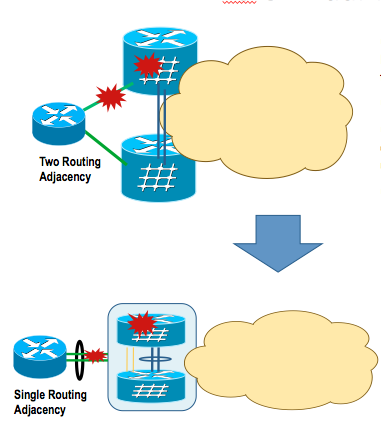
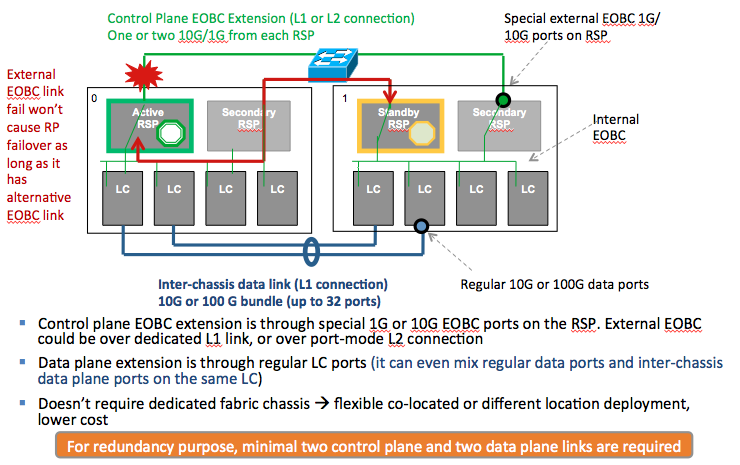
Cluster
Cluster is the concept of binding two physical chassis together into 1 logical unit. The control plane is extended via RSP on board 1 or 10G interfaces while the data plane is extended via 1 or more physical interfaces on the linecards.
So when building a bundle from the access side, if you link them to each individual chassis you'll have an active active bundle with failover between chassis!
Also the physical ASR's don't need to be on the same location. Only the control plane extension needs to have minimum latency (~<20msec).
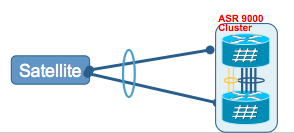
Satellite
Allows for port extension into a simple 1RU chassis with large 1G port fan out.
The Satellite connects via 1 or multiple 10G uplinks ot the ASR9000 host.
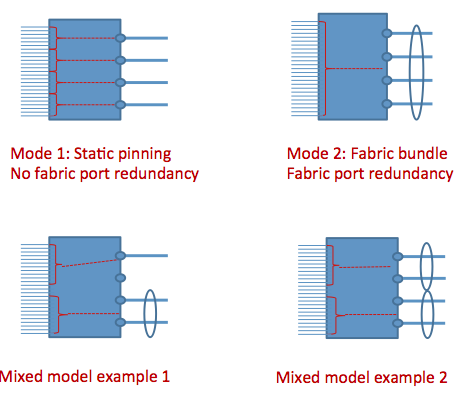
You can statically pin ports to an uplink or share an uplink via a bundle to multiple ports.
Satellite interfaces appear in teh ASR9000 config as if they were physically on the ASR9000.
Satellite interconnection options:
Configuration example:
nv
satellite 100 •ß define satellite ID
description my lovely satellite
type asr9000v
satellite 101 •ß define satellite
description your lovely satellite
type asr9000v
interface TenGigE 0/2/0/2
nv
satellite-fabric-link satellite 100
remote-ports
GigabitEthernet 0/0/0-9
interface bundle-ethernet 10
nv
satellite-fabric-link satellite 101
remote-ports
GigabitEthernet 0/0/10-19
On top of these bundle interfaces you can enable BNG.
Cluster and Satellite together
Wholesale Models
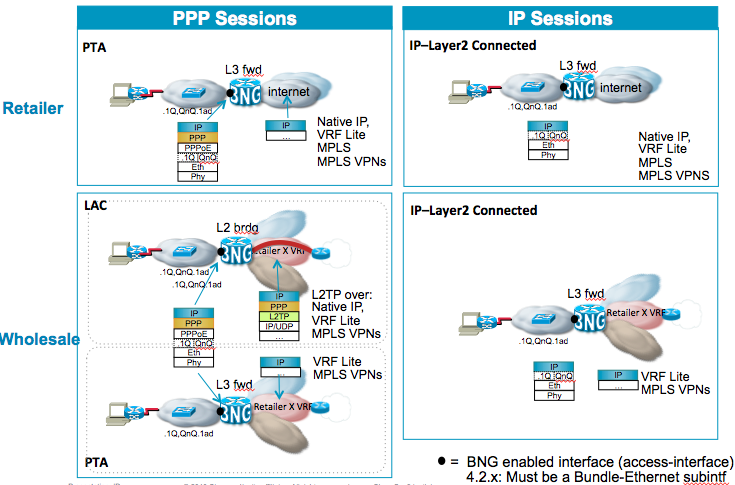
Most of the documentation here has been talking about locally terminating the subscribers on the BNG for regular access. Obviously there deployment models whereby a provider may like to just provide the initial termination on behalf of the wholesale provider.
Per access technology there are different options available.
PPP
PPP sessions can either be locally terminated, also known as PTA, or forwarded to the wholesale provider with 2 main options:
- L2TP tunneling
- RAMPLS
IP sessions
IP sessions only have one option for wholesaling which is inserting the subscribers in a VRF and using MPLS VPN to transport the data traffic to the wholesale provider.
RAMPLS
(Remote Access into MPLS-VPN) Is the concept of terminating the subscriber sesisions locally on the BNG and insert them in a specific vrf. This vrf is a separate routing context and using MPLS-VPN to transport the users traffic to the wholesale provider.
L2TP
Layer 2 Tunnelling Protocol is the concept of transporting the PPP session over to the wholesale provider's LNS.
ASR9000 can only function as LAC which basically means that after authentication we are creating a tunnel or inserting the user into an existing tunnel over to the LNS.
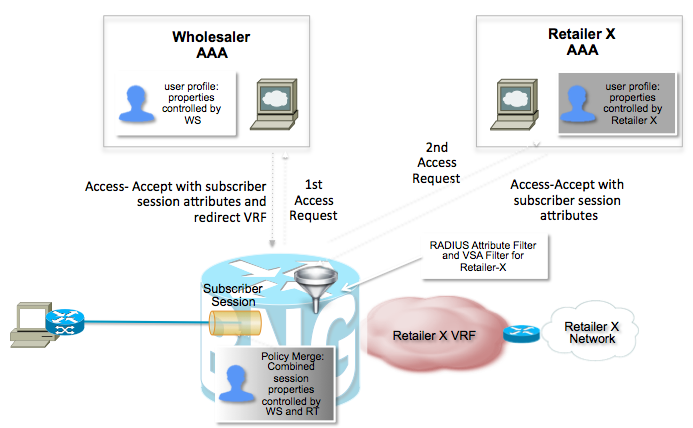
Doubledip
L2TP has as key advantage that the subscriber's PPP session is sent over to the LNS. This allows the LNS to have full control over the PPP session including authentication.
RAMPLS doesn't have such an option as the only Authentication stage is done on the BNG one time.
The concept of "double dip" is a phenomenal extension allowing you to use a local radius server on teh BNG and then contact the wholesale provider's AAA server and merge the profiles together:
On the ASR9000 BNG you can filter the attributes from the retailer to make sure that they don't override the user's vrf for instance like this:
radius-server attribute list RETAILER_X_ATTR_LIST
attribute <accepted or rejected attribute-list>
!
aaa group server radius RETAILER_X_SG
authorization reply { accept | reject } RETAILER_X_ATTR_LIST
vrf RETAILER_X_VRF
server-private 10.10.10.100 auth-port 1645 acct-port 1646
!
!
This server group referenced can be used in a control policy as an additional authenticate/authorize action under the session-start event for instance.
High Scale Deployment Best Practices
If your BNG deployments is high scale, these are some of the best practices to follow:
ICMP Unreachables
ICMP unreachables can significantly increase the CPU utilisation on line cards, especially if security access lists are enabled on seubscriber interfaces. You can disable the generation of ICMP unreachables in subscriber access interface configuration or dynamic template configuration:
ipv4 unreachables disable
or in radius profile:
Cisco-avpair="ipv4-icmp-unreachable=1"
ARP
In deployment scenarios with IP unnumbered and loopback interfaces with multiple secondary IP addresses, the ARP table size grows very quickly. Since on subscriber interfaces the MAC to IPv4 mapping is known through either DHCP or PPPoE, ARP entries are not required. On XR release 5.3.3 and later you can prevent the creation of ARP entries associated with subscriber interfaces by configuring:
subscriber arp scale-mode-enable
For more information on high scale ARP, refer to: https://supportforums.cisco.com/document/12766486/troubleshooting-arp-asr9000-routers.
Related Information
- BNG demo on YOUtube
- Using COA (Change of Authorization) tool
- Debugging PPPoE sessions
- Configuration Walkthrough
- Training guide
Special thanks to Sabrina Pittarel for some of the great visualizations seen in this document
and Nanjangud Sreekanta Prasad providing packet trigger and dhcp lease limit sections
Xander Thuijs, CCIE #6775
Sr. Tech Lead ASR9000
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hey artsiom!
I believe you can use the radius attr session-timeout for that which should also work on ipsubs. If not, you could use a control policy too, to start a timer and at the expiration of that call action "10 disconnect".
What happens with ipsubs in that case is that the dhcp binding will remain, but gets marked for NACK on renew request, and the ipsubscriber context/interface is terminated.
This means that traffic from the sub will hit the access interface, and if you dont have an acl on that access interface, he may get routed properly, depending on the unnumbered/address on the access interface.
Because clients will retain their lease, I found providing timeouts on ipsubs somewhat tricky, so for that reason it might be better to after the session timeout apply an HTTP redirect on the user or so to get him to a portal to relogon or pay a bill?
cheers!
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Xander,
It is tricky i agree.
My goal is to implement Radius-driven control on some (not all) users by time (a kind of temporary access). For some of users i need to force them to re-authenticate after some time and i thought "disconnect" should force the re-authentication. It seems that session-timeout attribute does't work for IPoE...didn't work for the first time, but i'll redo the tests.
In case of Control-Policy i need to have some signalling event of the user's session dependant on Radius attribute (some marker of such temporary sessions to match by control policy) to implement "10 disconnect". Do you have anything in mind about that?
Thank you,
Artsiom
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hey artsiom,
I see 3 possible options here:
1) apply a Session-Timeout radius attribute
2) define a service, on service activation event, class-match ont hat service name and start a timer, on timer expiration handle that event with a disconnect. This service can be activated via a VSA (subscriber:sa=SERVICENAME) during access-accept
3) same as "2" but then with an http-redirect service as opposed to a disconncet action.
cheers!
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander,
I want to configure BNG IPOE session, but it is not coming up, would please see the configuration and help
radius-server host 172.16.212.4 auth-port 1812 acct-port 1813
key 7 143F3D2C2E34271F3D716B637640
!
!
aaa accounting network SESS_ACCNT_LIST start-stop group radius_grp1
aaa group server radius radius_grp1
server 172.16.212.4 auth-port 1812 acct-port 1813
!
dhcp ipv4
profile IP-PROFIL proxy
lease proxy client-lease-time 1000
helper-address vrf default 172.16.212.13 giaddr 10.0.0.10
relay information option
relay information policy keep
relay information option allow-untrusted
!
interface GigabitEthernet0/0/0/0.515 proxy profile IP-PROFIL
!
dynamic-template
type ipsubscriber TPL
timeout idle 3600
ipv4 verify unicast source reachable-via rx
ipv4 unnumbered Loopback100
ipv4 access-group BNG_ACL_IN ingress
ipv4 access-group BNG_ACL_OUT egress
!
!
ipv4 access-list BNG_ACL_IN
10 permit ipv4 any any
!
ipv4 access-list BNG_ACL_OUT
10 permit ipv4 any any
!
!
interface Loopback100
ipv4 address 10.155.254.254 255.255.255.255
!
!
interface GigabitEthernet0/0/0/0
!
interface GigabitEthernet0/0/0/0.515
ipv4 point-to-point
ipv4 unnumbered Loopback100
service-policy type control subscriber BNG_PM
encapsulation dot1q 515 second-dot1q 2001
ipsubscriber ipv4 l2-connected
initiator dhcp
!
!
interface GigabitEthernet0/0/0/0.516
description RADIUS INTERFACE
ipv4 address 10.0.0.10 255.255.255.252
encapsulation dot1q 516
router static
address-family ipv4 unicast
0.0.0.0/0 134.19.214.1
172.16.212.0/28 10.0.0.9 description RADIUS
!
!
lldp
!
ssh server v2
aaa attribute format NAS-PORT-ID
circuit-id plus remote-id
!
aaa attribute format USERNAME-FORMAT
circuit-id plus remote-id
!
aaa radius attribute nas-port format e SSAAPPPPQQQQQQQQQQVVVVVVVVVVUUUU
aaa radius attribute nas-port-id format NAS-PORT-ID
aaa accounting subscriber default group radius
aaa authorization subscriber default group radius
aaa authentication subscriber default group radius
!
class-map type control subscriber match-any BNG-CLASS
match protocol dhcpv4
end-class-map
!
!
policy-map type control subscriber BNG_PM
event session-start match-first
class type control subscriber BNG-CLASS do-until-failure
10 activate dynamic-template TPL
15 authorize aaa list AUTHOR_LIST format USERNAME-FORMAT password cisco
!
!
event session-activate match-first
class type control subscriber BNG-CLASS do-until-failure
20 authenticate aaa list default
!
!
end-policy-map
!
end
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
ip sessions dont have a session-activate event, so you could remove that from the control policy. also the authenticate directive will take a username/pass from the line, which applies to pppoe, but not to ip sessions.
you have configured for linecard based subscribers (terminating on a gig (sub) interface).
this can work if you have the right version of XR sw (512+). otherwise you need to configure it on a bundle (sub) interface. can be with one member and lacp disabled if your peer doesn't support bundles.
for this problem shows and debugs are necessary to identify why this doesnt succeed. could be the radius profile, could be the dhcp transaction, so a debug of:
debug dhcp ipv4 proxy pack/ev/er
debug radius detail
debug subscriber manager policy (class)
and a show subscr ses all det (internal)
show dhcp ipv4 proxy bind
are minimally necessary.
best also to raise such questions as a new thread in teh xr os and platforms so that more people see this and it gets more attention.
cheers!
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander
Thank you very much for help, I removed show tech vsm location 0/0/CPU0 terminal from the configuration, and it seems authentication is successful, but I do not know what kind of information should radius send to bras in order client could receive ip from the dhcp server. Please see the debugs
343467760 rctx 0x5011f5b0
LC/0/0/CPU0:Sep 22 07:52:25.718 : radiusd[312]: Successfully sent packet and started timeout handler for rctx 0x5011f5b0
RP/0/RSP0/CPU0:FTTXBNG(config-dhcpv4-proxy-profile)#no helper-address vrf default 172.16.212.13 giaddr 10.155.254.25LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: rctx found is 0x5011f5b0
4LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: Picking the rad id 175:0 sockfd 0x5013B0F0
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: rctx 0x5011f5b0 added successfully
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: rib lookup result found 1073735512
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: Cannot get IP address, error: No error
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Send Access-Request to 172.16.212.4:1812 id 175, len 607
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: authenticator 49 D6 88 55 20 15 B6 2C - 76 67 EC AB 89 6E 9A 4A
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Cisco AVpair [1] 35 client-mac-address=d067.e531.5f61
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Vendor,Unknown [26] 36 Unsupported[2] 30
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Vendor,Cisco [26] 41
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Vendor,Cisco [26] 50
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Cisco AVpair [1] 44 remote-id-tag=Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Vendor,Unknown [26] 36 Unsupported[1] 30
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Vendor,Cisco [26] 51
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Cisco AVpair [1] 45 circuit-id-tag=Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Vendor,Cisco [26] 34
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Acct-Session-Id [44] 10 04000105
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: Cisco AVpair [1] 28 dhcp-vendor-class=MSFT 5.0
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: NAS-Port [5] 6 16015408
LC/0/0/CPU0:Sep 22 07:52:31.726 : radiusd[312]: RADIUS: NAS-Port-Id [87] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Vendor,Cisco [26] 65
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: cisco-nas-port [2] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: User-Name [1] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Service-Type [6] 6 Outbound[0]
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: User-Password [2] 18 *
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: NAS-Port-Type [61] 6 IPOEOQINQ[0]
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Called-Station-Id [30] 30 Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Calling-Station-Id [31] 30 Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Event-Timestamp [55] 6 1411372325
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Vendor,Cisco [26] 29
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Cisco AVpair [1] 23 dhcp-client-id=Pge1_a
LC/0/0/CPU0:Sep 22 07:52:31.727 : radiusd[312]: RADIUS: Nas-Identifier [32] 9 FTTXBNG
LC/0/0/CPU0:Sep 22 07:52:31.728 : radiusd[312]: RADIUS: NAS-IP-Address [4] 6 10.0.0.10
LC/0/0/CPU0:Sep 22 07:52:31.728 : radiusd[312]: Updating last used server
LC/0/0/CPU0:Sep 22 07:52:31.728 : radiusd[312]: Got global deadtime 0
LC/0/0/CPU0:Sep 22 07:52:31.728 : radiusd[312]: Using global deadtime = 0 sec
LC/0/0/CPU0:Sep 22 07:52:31.728 : radiusd[312]: Updated timer thread rad_ident 175 remote_port 1812 remote_addr 0xac10d404, socket 1343467760 rctx 0x5011f5b0
LC/0/0/CPU0:Sep 22 07:52:31.728 : radiusd[312]: Successfully sent packet and started timeout handler for rctx 0x5011f5b0
RP/0/RSP0/CPU0:FTTXBNG(config-dhcpv4-proxy-profile)#no helper-address vrf default 172.16.212.13 giaddr 10.155.254.254LC/0/0/CPU0:Sep 22 07:52:33.049 : dhcpd[153]: DHCPD: TP563: L3 packet event received
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD: TP2514: L3 RX: vrfid 0x60000000 (1610612736), ifh 0x4000980 (67111296), ifhsec 0x0 (0)
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD PACKET: TP564: L3 Packet RX from addr = 0.0.0.0, port = 68, application len 362, vrf 0x60000000 (1610612736), tbl 0xe0000000 (3758096384)
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: ---------- IPv4 DHCPD --- dhcpd_iox_l3_conn_hlr -------
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: VRF name (id): default (0x60000000)
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: L3 src: 0.0.0.0
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: L3 dst: 255.255.255.255
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: L3 src port: 68
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: L3 dst port: 67
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: L3 input Intf: GigabitEthernet0_0_0_0.515
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Output Intf: Null
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: FROM: L3
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: NETWORK_ORDER
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan Info
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan EtherType 1: 0x8100
LC/0/0/CPU0:Sep 22 07:52:33.050 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan Priority 1: 0 (0x0)
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan Format 1: 0 (0x0)
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan ID 1: 515 (0x203)
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan EtherType 2: 0x8100
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan Priority 2: 0 (0x0)
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan Format 2: 0 (0x0)
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: metadata: Vlan ID 2: 2001 (0x7d1)
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300:
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: op: BOOTREQUEST
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: chaddr: d067.e531.5f61
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: xid: 0x272e354b
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: flags: 0x0000 (unicast)
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: ciaddr: 0.0.0.0
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: yiaddr: 0.0.0.0
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: siaddr: 0.0.0.0
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: giaddr: 0.0.0.0
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: cookie: 0x63825363
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: MESSAGE_TYPE: DISCOVER
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: CLIENT_IDENTIFIER data: "0x01-d0-67-e5-31-5f-61"
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: HOST_NAME data: "azrt-ceo003"
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: VENDOR_CLASS_IDENT data: "MSFT 5.0"
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: PARAMETER_REQUEST data: "0x01-0f-03-06-2c-2e-2f-1f-21-79-f9-2b"
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: RELAY_INFORMATION
LC/0/0/CPU0:Sep 22 07:52:33.051 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: RELAY_INFORMATION: CIRCUIT_ID: Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:33.052 : dhcpd[153]: DHCPD_PACKET: pktRx id 300: option: RELAY_INFORMATION: REMOTE_ID: Ethernet0/0/5:4846-fbe9-b9f0
RP/0/RSP0/CPU0:FTTXBNG(config-dhcpv4-proxy-profile)#LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: rctx found is 0x5011f5b0
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: Picking the rad id 176:0 sockfd 0x5013B0F0
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: rctx 0x5011f5b0 added successfully
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: rib lookup result found 1073735512
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: Cannot get IP address, error: No error
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Send Access-Request to 172.16.212.4:1812 id 176, len 607
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: authenticator 49 D6 88 55 20 15 B6 2C - 76 67 EC AB 89 6E 9A 4A
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Vendor,Cisco [26] 41
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Cisco AVpair [1] 35 client-mac-address=d067.e531.5f61
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Vendor,Unknown [26] 36 Unsupported[2] 30
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Vendor,Cisco [26] 50
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Cisco AVpair [1] 44 remote-id-tag=Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Vendor,Unknown [26] 36 Unsupported[1] 30
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Vendor,Cisco [26] 51
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Cisco AVpair [1] 45 circuit-id-tag=Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Vendor,Cisco [26] 34
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Cisco AVpair [1] 28 dhcp-vendor-class=MSFT 5.0
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: Acct-Session-Id [44] 10 04000105
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: NAS-Port [5] 6 16015408
LC/0/0/CPU0:Sep 22 07:52:36.736 : radiusd[312]: RADIUS: NAS-Port-Id [87] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Vendor,Cisco [26] 65
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: cisco-nas-port [2] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: User-Name [1] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Service-Type [6] 6 Outbound[0]
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: User-Password [2] 18 *
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: NAS-Port-Type [61] 6 IPOEOQINQ[0]
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Called-Station-Id [30] 30 Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Calling-Station-Id [31] 30 Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Event-Timestamp [55] 6 1411372325
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Vendor,Cisco [26] 29
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Cisco AVpair [1] 23 dhcp-client-id=Pge1_a
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: Nas-Identifier [32] 9 FTTXBNG
LC/0/0/CPU0:Sep 22 07:52:36.737 : radiusd[312]: RADIUS: NAS-IP-Address [4] 6 10.0.0.10
LC/0/0/CPU0:Sep 22 07:52:36.738 : radiusd[312]: Updating last used server
LC/0/0/CPU0:Sep 22 07:52:36.738 : radiusd[312]: Got global deadtime 0
LC/0/0/CPU0:Sep 22 07:52:36.738 : radiusd[312]: Using global deadtime = 0 sec
LC/0/0/CPU0:Sep 22 07:52:36.738 : radiusd[312]: Updated timer thread rad_ident 176 remote_port 1812 remote_addr 0xac10d404, socket 1343467760 rctx 0x5011f5b0
LC/0/0/CPU0:Sep 22 07:52:36.738 : radiusd[312]: Successfully sent packet and started timeout handler for rctx 0x5011f5b0
RP/0/RSP0/CPU0:FTTXBNG(config-dhcpv4-proxy-profile)#LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: rctx found is 0x5011f5b0
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: Picking the rad id 177:0 sockfd 0x5013B0F0
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: rctx 0x5011f5b0 added successfully
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: rib lookup result found 1073735512
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: Cannot get IP address, error: No error
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Send Access-Request to 172.16.212.4:1812 id 177, len 607
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: authenticator 49 D6 88 55 20 15 B6 2C - 76 67 EC AB 89 6E 9A 4A
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Vendor,Cisco [26] 41
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Cisco AVpair [1] 35 client-mac-address=d067.e531.5f61
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Vendor,Unknown [26] 36 Unsupported[2] 30
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Vendor,Cisco [26] 50
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Cisco AVpair [1] 44 remote-id-tag=Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Vendor,Unknown [26] 36 Unsupported[1] 30
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Cisco AVpair [1] 45 circuit-id-tag=Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Vendor,Cisco [26] 51
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Cisco AVpair [1] 28 dhcp-vendor-class=MSFT 5.0
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Vendor,Cisco [26] 34
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Acct-Session-Id [44] 10 04000105
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: NAS-Port [5] 6 16015408
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: NAS-Port-Id [87] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:41.746 : radiusd[312]: RADIUS: Vendor,Cisco [26] 65
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: cisco-nas-port [2] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: User-Name [1] 59 Ethernet0/0/5:4846-fbe9-b9f0:Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: Service-Type [6] 6 Outbound[0]
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: User-Password [2] 18 *
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: NAS-Port-Type [61] 6 IPOEOQINQ[0]
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: Called-Station-Id [30] 30 Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: Calling-Station-Id [31] 30 Ethernet0/0/5:4846-fbe9-b9f0
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: Event-Timestamp [55] 6 1411372325
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: Vendor,Cisco [26] 29
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: Cisco AVpair [1] 23 dhcp-client-id=Pge1_a
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: Nas-Identifier [32] 9 FTTXBNG
LC/0/0/CPU0:Sep 22 07:52:41.747 : radiusd[312]: RADIUS: NAS-IP-Address [4] 6 10.0.0.10
LC/0/0/CPU0:Sep 22 07:52:41.748 : radiusd[312]: Updating last used server
LC/0/0/CPU0:Sep 22 07:52:41.748 : radiusd[312]: Got global deadtime 0
LC/0/0/CPU0:Sep 22 07:52:41.748 : radiusd[312]: Using global deadtime = 0 sec
LC/0/0/CPU0:Sep 22 07:52:41.748 : radiusd[312]: Updated timer thread rad_ident 177 remote_port 1812 remote_addr 0xac10d404, socket 1343467760 rctx 0x5011f5b0
LC/0/0/CPU0:Sep 22 07:52:41.748 : radiusd[312]: Successfully sent packet and started timeout handler for rctx 0x5011f5b0
RP/0/RSP0/CPU0:FTTXBNG(config-dhcpv4-proxy-profile)#LC/0/0/CPU0:Sep 22 07:52:46.756 : radiusd[312]: rctx found is 0x5011f5b0
LC/0/0/CPU0:Sep 22 07:52:46.756 : radiusd[312]: Reached retry count for the server 3,Trying to move to next server
LC/0/0/CPU0:Sep 22 07:52:46.756 : radiusd[312]: rad_nas_reply_to_client: Received response from id : 177,packet type 1
LC/0/0/CPU0:Sep 22 07:52:46.756 : radiusd[312]: rad_nas_reply_to_client: Sending failover message to client
As you see Bras is sending access-request, but receiving failover message,
What could be reason?
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
let me try to help. We have IPoE running on our BNGs.
Why is there this line in your debugs?
RP/0/RSP0/CPU0:FTTXBNG(config-dhcpv4-proxy-profile)#no helper-address vrf default 172.16.212.13 giaddr 10.155.254.254
Can you please show us "sh run dhcp ipv4" and sh run interface "access-interface"?
Can you ping the DHCP server with source IP for the subscribers?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Smailmilak,
I have tried helper address giaddr both subscriber and another source. At the moment it subscriber ip. 10.155.255.254 - this will be pool of the ip subscribers in the dhcp server 172.16.212.13. And I can ping dhcp server from this source.
RP/0/RSP0/CPU0:FTTXBNG#sh run dhcp ipv4
Wed Sep 24 20:23:53.863 UTC
dhcp ipv4
profile IP-PROFIL proxy
class class-default
helper-address vrf default 172.16.212.13 giaddr 10.155.255.254
!
limit lease per-circuit-id 24000
lease proxy client-lease-time 1000
helper-address vrf default 172.16.212.13 giaddr 10.155.255.254
relay information option
relay information policy keep
relay information option allow-untrusted
!
interface GigabitEthernet0/0/0/0.515 proxy profile IP-PROFIL
!
==============================================
RP/0/RSP0/CPU0:FTTXBNG#ping 172.16.212.13 source 10.155.255.254
Wed Sep 24 20:26:07.530 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.212.13, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/3 ms
RP/0/RSP0/CPU0:FTTXBNG#
=====================================
Thanks for help
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi
Can you explain what kind of attribute should work between BNG and Radius in order the client can receive ip address.
IN our case client send request for DHCP, BNG forwards to Radius for authentication which is successful. Next is authorization step that radius should send some attributes in radreply message that BNG will understand and will let Client to relay dhcp request to dhcp server. SO step is unseccessfull in my case. Can you help please on BNG-RADIUS mutual working ?
I mean what configuration should I write on BNG , which on Radius ?
Best Regards
Tural
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Tural,
there is no need for an attribute in case of IPoE. Only when you are using PPPoE you need to use an attribute so that the subsriber can get an IP address from the address pool (localy defined).
When you are using IPoE you need only AAA for authorization and QoS, and that is it.
There are of course some other attributes (framed-route, service activation etc).
What you can try is to disable AAA, so that you can be sure that it's not something RADIUS related. Without AAA we can concetrate on DHCP.
Use this config:
policy-map type control subscriber BNG_PM
event session-start match-first
class type control subscriber BNG-CLASS do-until-failure
10 activate dynamic-template TPL
You forgot to give us the configuration of your access-interface and loopback.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi
So the client will receive ip after succeful authorization and QOS step?
this is my all config
radius-server host 172.16.212.4 auth-port 1812 acct-port 1813
key 7 143F3D2C2E34271F3D716B637640
!
!
aaa accounting network SESS_ACCNT_LIST start-stop group radius_grp1
aaa group server radius radius_grp1
server 172.16.212.4 auth-port 1812 acct-port 1813
!
dhcp ipv4
profile IP-PROFIL proxy
lease proxy client-lease-time 1000
helper-address vrf default 172.16.212.13 giaddr 10.0.0.10
relay information option
relay information policy keep
relay information option allow-untrusted
!
interface GigabitEthernet0/0/0/0.515 proxy profile IP-PROFIL
!
dynamic-template
type ipsubscriber TPL
timeout idle 3600
ipv4 verify unicast source reachable-via rx
ipv4 unnumbered Loopback100
ipv4 access-group BNG_ACL_IN ingress
ipv4 access-group BNG_ACL_OUT egress
!
!
ipv4 access-list BNG_ACL_IN
10 permit ipv4 any any
!
ipv4 access-list BNG_ACL_OUT
10 permit ipv4 any any
!
!
interface Loopback100
ipv4 address 10.155.254.254 255.255.255.255
!
!
interface GigabitEthernet0/0/0/0
!
inteeface Loopback 100
ipv4 address 10.155.255.254/32
lnterfaceGigabitEthernet0/0/0/0.515
ipv4 point-to-point
ipv4 unnumbered Loopback100
service-policy type control subscriber BNG_PM
encapsulation dot1q 515 second-dot1q 2001
ipsubscriber ipv4 l2-connected
initiator dhcp
!
!
interface GigabitEthernet0/0/0/0.516
description RADIUS INTERFACE
ipv4 address 10.0.0.10 255.255.255.252
encapsulation dot1q 516
router static
address-family ipv4 unicast
0.0.0.0/0 134.19.214.1
172.16.212.0/28 10.0.0.9 description RADIUS
!
!
lldp
!
ssh server v2
aaa attribute format NAS-PORT-ID
circuit-id plus remote-id
!
aaa attribute format USERNAME-FORMAT
circuit-id plus remote-id
!
aaa radius attribute nas-port format e SSAAPPPPQQQQQQQQQQVVVVVVVVVVUUUU
aaa radius attribute nas-port-id format NAS-PORT-ID
aaa accounting subscriber default group radius
aaa authorization subscriber default group radius
aaa authentication subscriber default group radius
!
class-map type control subscriber match-any BNG-CLASS
match protocol dhcpv4
end-class-map
!
!
policy-map type control subscriber BNG_PM
event session-start match-first
class type control subscriber BNG-CLASS do-until-failure
10 activate dynamic-template TPL
15 authorize aaa list AUTHOR_LIST format USERNAME-FORMAT password cisco
!
!
event session-activate match-first
class type control subscriber BNG-CLASS do-until-failure
20 authenticate aaa list default
!
!
end-policy-map
!
end
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ok, a couple of things. Try it out and reply back.
First DHCP
dhcp ipv4
profile IP-PROFIL proxy
lease proxy client-lease-time 1000
helper-address vrf default 172.16.212.13 giaddr 10.155.254.254
interface Loopback100
ipv4 address 10.155.254.254 "SUBNET MASK OF YOUR POOL"
This is how it's working on our BNG.
Now AAA
policy-map type control subscriber BNG_PM
event session-start match-first
class type control subscriber BNG-CLASS do-until-failure
10 activate dynamic-template TPL
15 authorize aaa list AUTHOR_LIST format USERNAME-FORMAT password cisco
end-policy-map
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Nicolas,
I tried but not working, I guess something on Radius side, but do not know how to guide him, what AV Pair he has to send for QOS and etc..
Because traffic is not sended to DHCP, today I disabled aaa, dhcp server receives packet, but with AAA enabled dhcp server doesnot receive any packet, what could be reason ?
Best Regards
Tural
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So it's working with AAA? Client is getting an IP address?
Problem is when you add authorization?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
No problem is when I add AAA authorization
Without AAA authorization dhcp request is relayed to the dhcp server.
when I add AAA authorization no any traffic is coming to DHCP server.
Best Regards
Tural
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: