- Cisco Community
- Technology and Support
- Service Providers
- Service Providers Knowledge Base
- ASR9000/XR CGv6 on VSM: CGN / NAT44 Deployment Guide
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-13-2013 01:56 AM - edited 04-24-2020 10:33 PM
- Introduction
- Introduction to NAT44
- Basic Deployment Scenario: NAT444
- Parameters to be considered before Deployment
- Performance and Scale
- Address Pool and Mapping
- VRF (Inside and Outside)
- Port Limit (Per-User)
- External Logging (Netflow and Syslog)
- NAT Session Timeouts (TCP, UDP, ICMP)
- Endpoint Independent and Dependent Filtering (EIF / EDF)
- Traffic Diversion (to VSM)
- Static Port Forwarding
- Application Layer Gateway (ALG)
- Redundancy
- NAT44 Licenses
- Summary of parameter values
- NAT44 Configuration / Feature Differences with ISM
- MTU and Fragmentation Considerations
- Specific Deployment Scenarios / Use-Cases
- Validation of Configuration
- Monitoring CGN Using SNMP
- Useful Deployment Tips
- Related Information
Introduction
Cisco's CGv6 (Carrier Grade IPv6) solution helps customer transitioning from IPv4 to IPv6 gradually, maintaining business continuity. VSM (Virtualized Services Module) on ASR9K is a Service Card which provides different CGv6 Applications. This is the next generation Service Card after ISM (Integrated Services Module). This document talks about how to deploy NAT44 (Network Address Translation - from IPv4 to IPv4), one of the applications fall under CGv6 suite of applications.
This document does NOT intend to cover details on VSM, how to install CGv6 software on VSM, how to trouble-shoot CGv6 issues, CGv6 Applications other than NAT44.
DISCLAIMER: This document contains some Public IP addresses to explain different deployment use-cases and features related to NAT44. The Public IP addresses are picked up randomly and matching of these addresses with any specific customer's or organization's public IP is purely coincidental. Please DO NOT use these public addresses in your NAT setup / deployment, unless the public IP addresses are not owned by you / your organization. Cisco is not responsible for any issues arising out of this.
Introduction to NAT44
This section introduces NAT44 and terminologies related to it.
1. Why NAT44 ?
IPv4 address is 32-bit long which means there can be 4,294,967,296 (i.e., 4 billions) unique addresses. However, population on earth has crossed 7 billions and is still growing. Also, nowadays, a single person can own multiple IP devices, each having its own IP address. Thus, we are running short of IPv4 addresses. In 2 of the 5 RIR (Regional Internet Registries), IPv4 address exhaustion is declared (in its last /8 stage).
Apat from moving to IPv6 (which uses 128-bit long IP address), an alternate mechanism is to use NAT44 where Private IP addresses can be re-used in different Private networks, but can be translated to a unique Public IP address when the packet enters Internet or Public network.
If you are a Service Provider and running short of Public IP addresses, NAT44 should be of great usefulness to you as an intermediate solution before you slowly convert your IPv4 network into IPv6.
2. NAT44 Overview
NAT44 literally means translating one IPv4 address to another IPv4 address. "Typically", first IPv4 address is "Private" IPv4 Address (defined by RFC 1918) and second IPv4 address is "Public" (non-Private) IPv4 address. As defined by RFC 1918, Private IPv4 addresses fall in the following blocks.
| Start IP Address | End IP Address | Comments |
|---|---|---|
| 10.0.0.0 | 10.255.255.255 | 10.0.0.0/8 prefix - contains 16,777,216 addresses |
| 172.16.0.0 | 172.31.255.255 | 172.16.0.0/12 prefix - contains 1,048,576 addresses |
| 192.168.0.0 | 192.168.255.255 | 192.168.0.0/16 prefix - contains 65,536 address |
However, it is to be noted that not always "Private" IPv4 address is to be translated to "Public" IPv4 address. There are deployment cases where NAT44 is used to convert "Private" IPv4 address (say, 192.168.x.x range) to another "Private" IPv4 address (say, 10.x.x.x range) as well.
NOTE: In this document, however, we will refer "Private" side as the pre-NAT side of the NAT device and "Public" side as the post-NAT side of the NAT device, irrespective of the actual IP address being used.
One more important point, although NAT indicates Network Address Translation, it is actually NAPT (Network Address and Port Translation). What it means is - in addition to IPv4 address, Layer 4 (UDP/TCP) port is also translated by NAT44.
NOTE: Unless mentioned otherwise, in this document, NAT44 will indicate translation of both IPv4 address and Port.
Following Layer 4 Protocols are supported by NAT44 implementation on VSM.
- UDP (IP Protocol 17) - UDP Port number (2 bytes) is translated along with IPv4 address.
- TCP (IP Protocol 6) - TCP Port number (2 bytes) is translated along with IPv4 address.
- ICMP (IP Protocol 1) - ICMP Identifier field (2 bytes) in Echo Request and Echo Response messages is used as (dummy) Layer 4 port.
- GRE (used with PPTP ALG, IP Protocol 47) - Call ID field (2 bytes) is used as (dummy) Layer 4 port.
Another useful property of NAT44 is multiple Private IP addresses can be mapped to one Public IP address. This is possible as all of the 65,536 ports (0 to 65,535) on any Private IP address are typically not used by Applications.
Following diagram shows how NAT44 works.
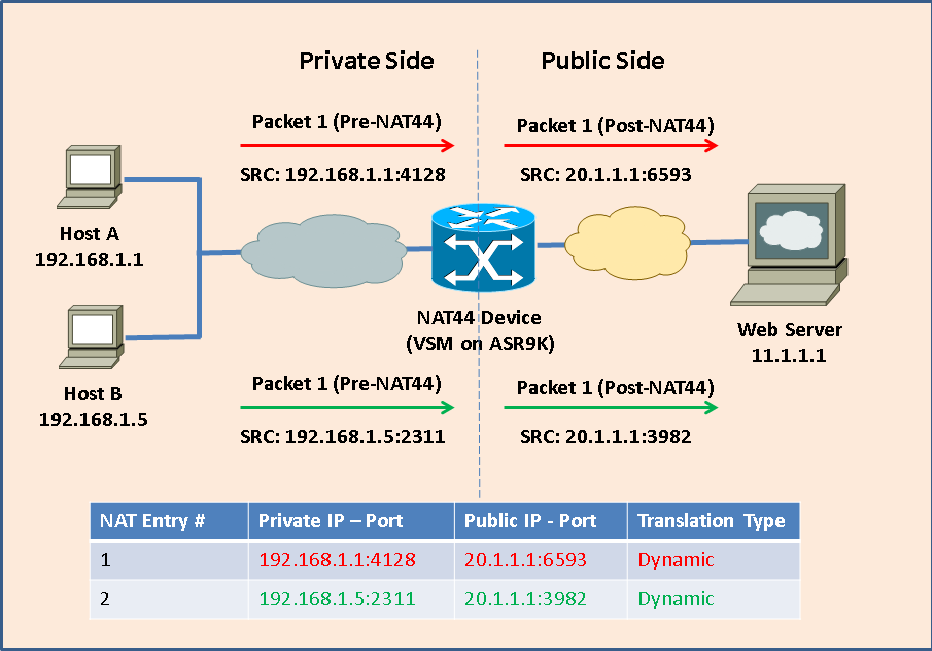
As shown above, the Private IP addresses 192.168.1.1 and 192.168.1.5 are translated to same Public IP address 20.1.1.1 (along with specific Layer 4 ports) by the NAT44 device (VSM on ASR9K). The translation entries are maintained in NAT DB at the NAT44 device.
3. Basic Terminologies
In this section, let us get introduced with different terminologies related to NAT44 deployment on VSM.
| Terminology | Definition / What it means |
|---|---|
| Inside / Subscriber Side / Access Side / Private Side | Private side of the NAT44 device (which usually contains Private IPv4 addresses) |
| Outside / Network Side / Core Side | Public side of the NAT44 device (which usually contains Public IPv4 addresses) |
| Inside-to-Outside (I2O) | Traffic flowing from Inside to Outside across NAT44 device |
| Outside-to-Inside (O2I) | Traffic flowing from Outside to Inside across NAT44 device |
| Stateful (SF) | Which preserves State or Database. E.g. - NAT44 is Stateful protocol. |
| Endpoint Independent Filtering (EIF) |
Any device (IP + Port) can send O2I traffic to a Public IP + Port which exists in NAT DB. VSM implements this behavior. It is also termed as "Full-Cone NAT". |
| Endpoint Dependent Filtering (EDF) |
Only the device (IP + Port) which has received I2O traffic can send O2I traffic to a public IP + Port which exists in NAT DB. Destination IP and port information is also maintained in NAT DB in this case. VSM implements this behavior (Address-Dependent as well as Address and Port-Dependent) |
| Port Parity Preservation |
Odd port should be translated to Odd port and Even port should be translated to Even port. VSM supports this. |
4. Standard Compliance
Following are the important RFCs that the NAT44 solution on VSM complies (most of the cases, fully) to.
| RFC Number / IETF Draft Name | Title of the Specification | Additional Comments |
|---|---|---|
| RFC 768 | User Datagram Protocol (UDP) | |
| RFC 792 | Internet Control Message Protocol (ICMP) | |
| RFC 793 | Transmission Control Protocol (TCP) | |
| RFC 959 | File Transfer Protocol (FTP) | |
| RFC 1812 | Requirements for IP Version 4 Routers | |
| RFC 3954 | Cisco System Netflow Services Export Version 9 | |
| RFC 4787 | Network Address Translation (NAT) Behavioral Requirements for Unicast UDP | |
| RFC 5382 | NAT Behavioral Requirements for TCP | |
| RFC 5424 | The Syslog Protocol | |
| RFC 5508 | NAT Behavioral Requirements for ICMP | |
| RFC 6888 | Common Requirements for Carrier Grade NATs (CGN) | Evolved from draft-nishitani-cgn |
Basic Deployment Scenario: NAT444
This section talks about one of the basic deployment scenario for NAT44 which is called "Double NAT44" or "NAT444".
5. Network Diagram
Following diagram depicts NAT444.
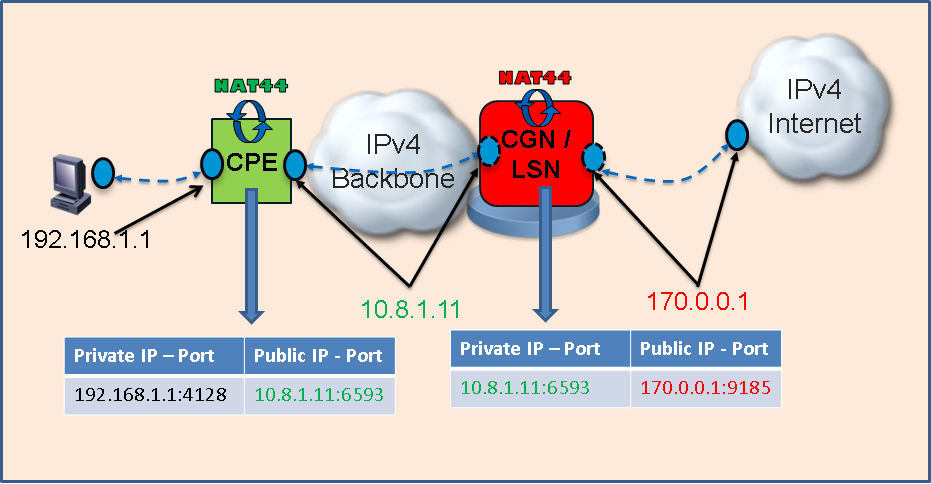
In the above diagram, there are 2 NAT44 instances shown (hence, it is termed as "Dual NAT44" or "NAT444").
- CPE (Customer Premise Equipment) NAT44 - This typically happens within customer premise. Each customer / end user is given one (or, more) IPv4 address (10.8.1.11 in the above example) by the Service Provider. There could be multiple devices within customer premise which will have IPv4 addresses in 192.168.1.x network (as shown in the above diagram). As an example, CPE NAT44 device translates IPv4 address/Port of 192.168.1.1:4128 to 10.8.1.11:6593, while sending the packet out to provider network. A NAT table is maintained at CPE NAT level as well. But, the scale of this is less (as there won't be too many end devices). As you can see, both Private-side and Public-side IP addresses used here are from RFC 1918 (i.e., Private IPv4 addresses).
- CGN (Carrier Grade NAT) or LSN (Large Scale NAT) - This happens within the Service Provider network. CGN device (as per the diagram) translates Private IPv4 address/Port of 10.8.1.11:6593 to a public IPv4 address/Port of 170.0.0.1:9185 before sending the packet to Internet. A relatively huge NAT table is maintained at CGN level as it may need to deal with millions of CPEs.
VSM with ASR9K will be positioned as CGN in Service Provider network.
6. NAT44 on VSM Configuration
Before we start configuring NAT44 on VSM, let us understand the following concepts related to NAT44 implementation on VSM.
- CGN Instance - On each VSM card, we can configure one CGN instance (<cgn1> in the diagram below).
- NAT44 Instance - On each VSM card, we can configure one NAT44 instance (<nat1> in the diagram below).
- ServiceInfra interface - ServiceInfra interface is a virtual interface which is used by the internal (to ASR9K) management / control traffic. We need 1 ServiceInfra interface per VSM card. ServiceInfra interface cannot be in any VRF (needs to be in default VRF).
- ServiceApp interface - ServiceApp interface is a virtual interface which is used to bring CGv6 Application (NAT44) data traffic to VSM card. We need 1 pair of ServiceApp interface for each VRF instance - 1 Inside ServiceApp interface (ServiceApp <x> in the diagram below) to bring Inside traffic to VSM (I2O direction) and 1 Outside ServiceApp interface (ServiceApp <y> in the diagram below) to bring Outside traffic to VSM (O2I direction).
NOTE: ServiceInfra and ServiceApp interfaces are used within the ASR9K router only and do not need to be announced/redistributed into IGP.
- Inside VRF instance - Within one NAT44 instance, we can have multiple Inside VRF instances. For each Inside VRF instance, we can have different NAT44 parameters configured. Inside ServiceApp must be within one unique Inside VRF. Outside ServiceApp may or may not be within a (Outside) VRF.
NOTEs: - We cannot have multiple Inside ServiceApps within same Inside VRF. - We can, however, have multiple Outside ServiceApps within same Outside VRF or default VRF. - Inside and Outside VRF cannot be same.
- Logical Partitioning inside VSM - Internally, VSM is divided into 2 Logic Partitions. Hence, in order to achive full throughput and scale limit (per VSM), you should have minimal of 2 Inside VRFs, 4 ServiceApp interfaces (2 in each partition), 2 Public IP address pool, etc. Traffic / subscribers which needs to avail NAT44 service also needs to be divided into 2 groups (each one associated to each Inside VRF). Following table shows the partitioning of ServiceApp interfaces between these 2 groups (which needs to be kept in mind during configuration).
| Logical Partition / Group 1 | Logical Partition / Group 2 |
|---|---|
| ServiceApp 1, ServiceApp 2 | ServiceApp 3, ServicApp 4 |
| ServiceApp 5, ServiceApp 6 | ServiceApp 7, ServiceApp 8 |
| ServiceApp 9, ServicApp 10 | ServiceApp 11, ServiceApp 12 |
| ... | ... |
| ServiceApp 253, ServiceApp 254 | ServiceApp 255, ServiceApp 256 |
NOTE: ServiceApp interafce pair needs to be selected from same Logical Partition (as per the above table). Otherwise, packets will be dropped. Using consecutive numbers for ServiceApp interface pair will be recommended (as shown above).
Following diagram provides summary / overview of NAT44 configuration for VSM.
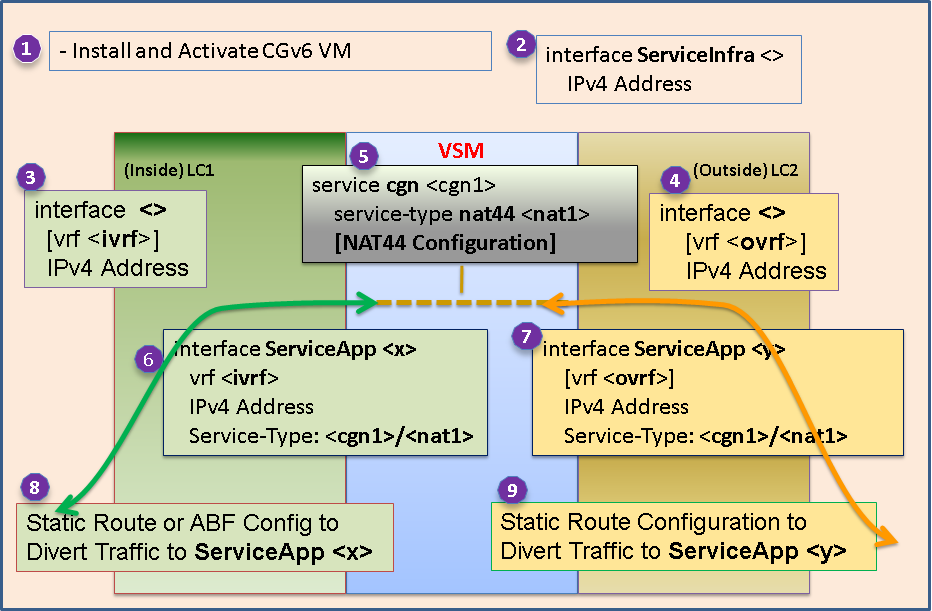
Below are sample configurations for each of the above steps.
| Step 1: Install and Activate CGv6 VM Configure on VSM Card at Slot 1 |
|---|
! Install CGv6 VM's OVA package ! ----------------------------- RP/0/RSP0/CPU0:ios# virtual-service install name cgn123 package /disk0a:/usr/vsmcgv6.ova node 0/1/CPU0 ! Configure and Activate CGv6 VM ! ------------------------------ RP/0/RSP0/CPU0:ios#conf t Fri Aug 2 18:10:25.525 UTC RP/0/RSP0/CPU0:ios(config)#virtual-service cgn123 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/0 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/1 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/2 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/3 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/4 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/5 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/6 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/7 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/8 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/9 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/10 RP/0/RSP0/CPU0:ios(config-virt-service)#vnic interface tenGigE 0/1/1/11 RP/0/RSP0/CPU0:ios(config-virt-service)#commit Fri Aug 2 18:11:34.285 UTC RP/0/RSP0/CPU0:ios(config-virt-service)#activate RP/0/RSP0/CPU0:ios(config-virt-service)#commit |
| Step 2: Configure ServiceInfra interface |
|---|
! Bring up 10-GE interfaces on VSM ! Must before configuring any ServiceInfra/App interfaces ! ------------------------------------------------------- interface TenGigE 0/1/1/0 no shut interface TenGigE 0/1/1/1 no shut interface TenGigE 0/1/1/2 no shut interface TenGigE 0/1/1/3 no shut interface TenGigE 0/1/1/4 no shut interface TenGigE 0/1/1/5 no shut interface TenGigE 0/1/1/6 no shut interface TenGigE 0/1/1/7 no shut interface TenGigE 0/1/1/8 no shut interface TenGigE 0/1/1/9 no shut interface TenGigE 0/1/1/10 no shut interface TenGigE 0/1/1/11 no shut ! Define Service Infra interface ! ------------------------------ interface ServiceInfra 1 ! Assign IPv4 address and netmask ipv4 address 100.1.1.1 255.255.255.252 ! Define service location service-location 0/1/CPU0 |
Please note that inside and outside VRFs are also need to be configured, as shown below.
vrf ivrf1
address-family ipv4 unicast
vrf ivrf2
address-family ipv4 unicast
vrf ovrf1
address-family ipv4 unicast
vrf ovrf2
address-family ipv4 unicast
Once the VRFs are configured, let us proceed with further configuration.
| Step 3 and 4: Configure Ingress and Egress LC Interfaces |
|---|
! Configure Ingress interfaces ! ---------------------------- interface TenGigE0/0/0/0 ! Add it to Inside VRF vrf ivrf1 ! Assign IP address to it ipv4 address 10.10.10.1 255.255.255.0 ! interface TenGigE0/0/0/1 vrf ivrf2 ipv4 address 10.10.11.1 255.255.255.0 ! Configure Egress interfaces ! -------------------------- interface TenGigE0/2/0/0 vrf ovrf1 ipv4 address 20.20.20.1 255.255.255.0 interface TenGigE0/2/0/1 vrf ovrf2 ipv4 address 20.20.21.1 255.255.255.0 |
| Step 5: Configure CGN and NAT44 Service parameters (Important ones are shown) |
|---|
! Define CGN Instance ! ------------------- service cgn cgn1 ! Define location service-location preferred-active 0/1/CPU0 ! Define NAT44 Service Type and instance (one per VSM card) service-type nat44 nat1 ! Define per-user Port limit for NAT44 instance portlimit 250 ! Enable Active FTP ALG alg ActiveFTP ! Define UDP protocol session timeout values protocol udp session initial timeout 240 session active timeout 600 ! Define inside VRF inside-vrf ivrf1 ! Define Public IP address Pool map outside-vrf ovrf1 address-pool 100.1.1.0/24 ! Define inside VRF inside-vrf ivrf2 ! Define Public IP address Pool map outside-vrf ovrf2 address-pool 100.1.2.0/24 |
| Step 6 and 7: Configure Inside and Outside ServiceApp interfaces |
|---|
! Define Inside Service App interfaces ! ------------------------------------ interface ServiceApp 1 ! Define VRF where it should belong to (optional) vrf ivrf1 ! Assign IPv4 address and netmask ipv4 address 1.1.1.1/30 ! Define CGN instance and service type in which it belongs to service cgn cgn1 service-type nat44 interface ServiceApp 3 vrf ivrf2 ipv4 address 1.1.2.1/30 service cgn cgn1 service-type nat44 ! Define Outside Service App interfaces ! ------------------------------------- interface ServiceApp 2 vrf ovrf1 ipv4 address 2.1.1.1/30 service cgn cgn1 service-type nat44 interface ServiceApp 4 vrf ovrf2 ipv4 address 2.1.2.1/30 service cgn cgn1 service-type nat44 |
| Step 8 and 9: Configure Traffic Diversion Rules |
|---|
! Define static route for Inside-to-outside traffic ! ------------------------------------------------- router static ! Specify the Inside VRF vrf ivrf1 ! Define address family address-family ipv4 unicast ! Re-direct all traffic to Inside Service App 0.0.0.0/0 ServiceApp 1 router static vrf ivrf2 address-family ipv4 unicast 0.0.0.0/0 ServiceApp 3 ! Define static route for Outside-to-inside traffic ! ------------------------------------------------- router static vrf ovrf1 address-family ipv4 unicast 100.1.1.0/24 ServiceApp 2 router static vrf ovrf2 address-family ipv4 unicast 100.1.2.0/24 ServiceApp 4 |
7. I2O Packet Flow on VSM
Following diagram shows the packet flow within ASR9K (including VSM) for Inside to Outside NAT44 traffic at a high-level.
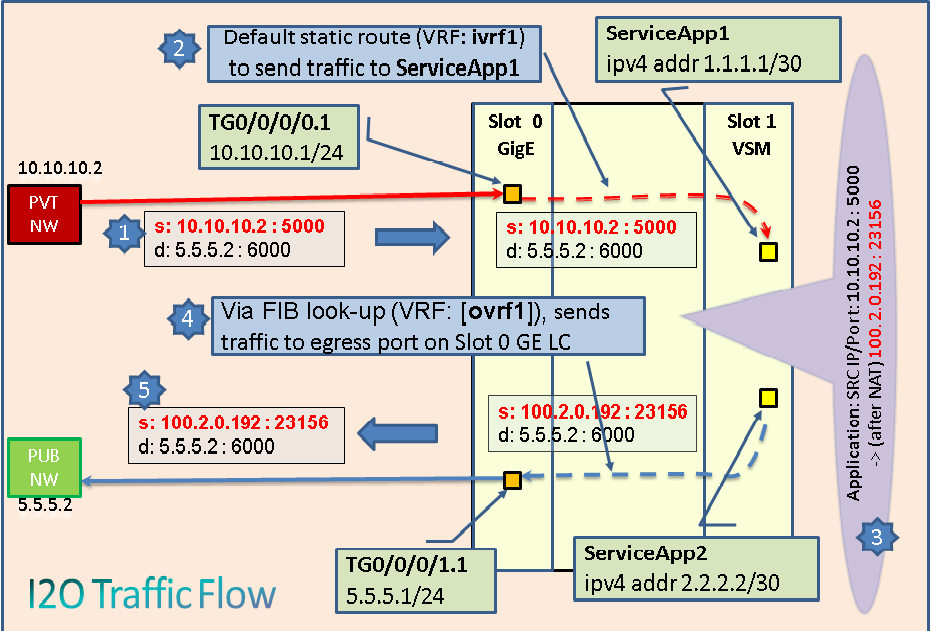
Step 1: Packet from Inside / Private side reaches ASR9K Ingress Line Card.
Step 2: Forwarding lookup (rule added by static route, ACL-based forwarding, etc.) should forward the packet to VSM card, via Inside ServiceApp 1 interface. Inside VRF (ivrf1) will be used during the forwarding lookup.
Step 3: NAT44 Application performs necessary action for the packet. As it is Inside-to-Outside packet, it first checks if there is a NAT entry exists for the source IP (10.10.10.2) and port (5000). If it does not exists, it allocates a Public IP (from the Public IP pool configured) and port and creates a NAT entry. From the NAT entry, it finds the corresponding Public IP (100.2.0.192) and port (23156) and replaces the existing Source IP and port with the same.
Step 4: After NAT translation is done, a forwarding lookup is done in Outside VRF (ovrf1) for the destination IP address (5.5.5.2) which forwards the packet to egress LC interface.
Step 5: Egress Line Card interface sends the packet out to Outside / Public side.
8. O2I Packet Flow on VSM
Following diagram shows the packet flow within ASR9K (including VSM) for Outside to Inside NAT44 traffic at a high-level.

Step 1: Packet from Outside / Public side reaches ASR9K Ingress Line Card.
Step 2: Forwarding lookup (rule added by static route, ACL-based forwarding, etc.) should forward the packet to VSM card, via Outside ServiceApp 2 interface. Outside VRF (ovrf1), if being configured, will be used during the forwarding lookup.
Step 3: NAT44 Application performs necessary action for the packet. As it is Outside-to-Inside packet, it first checks if there is a NAT entry exists for the Destination IP (100.2.0.192) and port (23156). If it does not exists, packet is dropped. Otherwise, from the NAT entry, it finds the corresponding Private IP (10.10.10.2) and port (5000) and replaces the existing Destination IP and port with the same.
Step 4: After (reverse) NAT translation is done, a forwarding lookup is done in Inside VRF (ivrf1) for the destination IP address (10.10.10.2) which forwards the packet to egress LC interface.
Step 5: Egress Line Card interface sends the packet out to Inside / Private side.
Parameters to be considered before Deployment
Before deploying NAT44 solution with VSM, you need to analyze the deployment scenario/requirement and come up with the appropriate values of different configurable parameters related to NAT44. Improper selection of the parameters may not address the deployment goals accurately.
9. Performance and Scale
These are possibly the most important parameters to be considered during deployment. These are not configurable parameters, but these will determine how many VSM cards will be needed for the NAT44 solution.
- Identify the performance and scale need for NAT44 solution
- Please check "CGv6 on VSM Feature Support" page, to find out the supported scale and performance values.
Based on the above two, find out how many VSM cards will be needed for the solution.
NOTE: For better NAT44 performance, Cisco recommends keeping the default physical interface MTU size on the customer-facing interfaces in NAT44 deployment.
10. Address Pool and Mapping
Identify the following for the deployment scenario.
- How many Public IPv4 addresses the customer has to form the Public IP pool ?
- How many (approximately) Private (Pre-NAT) IPv4 addresses the customer has ?
- Do you need to limit the ratio of Private to Public IP addresses ?
Based on the same, number of inside VRFs, address pools, many-to-one ratio can be configured as follows.
| Address Mapping related parameter configuration |
|---|
service cgn cgn1 service-type nat44 nat1 inside-vrf ivrf1 ! Define Public IP address Pool map outside-vrf ovrf1 address-pool 100.1.1.0/20 ! Define Many to one IP addresses maping map ip many-to-one 6 |
NOTE: Network address and Broadcast address in the subnet (as configuredby address-pool parameter) are also used as NAT'ed Public / Outside IP address.
11. VRF (Inside and Outside)
Identify the following VRF related information from deployment requirement.
- Whether Private side traffic comes / can / should come in VRF or not ?
- Whenther Public side traffic can / should go in a VRF or not ?
- Is there a overlap of Private IP addresses or not ?
- Are there different values of certain parameters (which are configured per-VRF) needed or not ?
- What is the Scale and Bandwidth requirement for each VRF
Above information will determine,
- How many Inside and Outside VRFs will be needed in the solution
- Which per-Inside VRF parameters need to be set
- How the Public IP pool needs to be divided
12. Port Limit (Per-User)
As NAT DB is shared among all users, there could be a situation where few users (Private IP owners) uses lots of NAT entries (in thousands) and because of the same, new users cannot create NAT entries. In order to keep control on creation of NAT entries by a single user, Port Limit parameter is introduced. Port limit indicates how many port numbers are allowed per Private / Inside IP address. If any flow arrives after Port Limit is reached, no NAT entry will be created for the same and the packets for the new flows will be dropped. The Port limit value will be same for all Private IP addresses.
NOTE: Port Limit is specified per Private / Inside IP address and NOT per Public / Outside IP address.
Find out the following:
- How many ports will be needed by a Private IP address holder ?
- How many Public IP addresses are available ?
Based on the above Port Limit can be configured as follows.
| Configuration of Port Limit |
|---|
service cgn cgn1 ! Define NAT44 Service Type and instance (one per VSM card) service-type nat44 nat1 ! Define per-user Port limit for NAT44 instance portlimit 250 |
13. External Logging (Netflow and Syslog)
As you have seen above, a NAT DB entry is created for each new flow (Private IP address and port) which keeps the mapping of Private / Inside IP address + Port and Public / Outside IP address + Port. The NAT DB entry is deleted when the flow terminates (because of timeout and any user intervention).
On VSM, we support millions of NAT translations with high (in thousands and millions) setup and deletion rate (Please refer to CGv6 on VSM Feature List for scale numbers). This produces huge amount of NAT translation entries / records which cannot be stored / saved on VSM or ASR9K because of limited disk space. Hence, there is a need of having external servers where these translations can be saved.
The creation and deletion of NAT transactions (also called "Logging Records") are very important to be saved to get association of different IP addresses. In almost all countries, it is mandated by the Lawful Agencies / Authorities that the Service Provide must provide these records accurately so that the agencies can find out the owner of these APIs for different reasons. Thus it becomes a very important feature for deployment of NAT44.
On VSM, we support the 2 formats of logging records - Netflow (version 9) and Syslog. Table below compares the two.
| Items for Comparison | Netflow Version 9 (NFv9) | Syslog |
|---|---|---|
| Standard Document |
RFC 3954 |
RFC 5424 |
| Text / Binary format | Binary | Text |
| Underlying Layer 4 protocol | UDP (Server usually uses Port 2055, 2056, 4432, 4739, 9995, 9996, 6343) | UDP (Server typically uses Port 514) |
| Average Logging Recod Size | 20 Bytes (with DBL and BPA disabled) | 70 Bytes (with DBL and BPA disabled) |
| Usage of Template | Uses Netflow Template | Does not use any template |
Logging records are sent to Logging Server (IP address and Port for which is configurable) either when the Logging packet is complete or timeout occurs. Logging packets are sent with ServiceInfra interface's remote IP (for e.g., 100.1.1.2 is the remote IP of 100.1.1.1) as Source address.
NOTE: External Logging Server IP address should be reachable via any ASR9K LC interface (NOT via Management Ethernet interface), in default VRF.
Destination-Based Logging (DBL)
In some countries, Lawful Agencies also require the Service Provider to provide the Destination IP address and Port (along with Source IP address and Port information) as part of Logging Record. This is termed as Destination-Based Logging (DBL).
NOTE: Including Destination (IP + Port) information in the Logging Record will increase the size of the Record.
DBL can be supported with Netflow v9 as well as with Syslog.
Bulk Port Allocation (BPA)
In order to reduce the size of the logging record, a feature called Bulk Port Allocation (BPA) is introduced.
Without BPA, for every new flow, a Port is allocated for the Public IP and a new logging record is created with Private IP + Port and Public IP + Port. Similarly, another Logging record is created when a flow or NAT entry is deleted.
Following table captures the working of it (without BPA) with some sample IP addresses and port numbers.
| Event | Inside Source IP + Port | Outside Source IP + Port | Logging Record | Additional Comments |
|---|---|---|---|---|
| A new flow arrives | 10.1.1.1:1000 | 170.0.0.5:8175 | 10.1.1.1:1000 <-> 170.0.0.5:8175 |
New port (8175) allocation happens. New logging record is created |
| Existing flow arrives | 10.1.1.1:1000 | 170.0.0.5:8175 | N/A |
No new Port allocation happens. No logging record is created |
| A new flow arrives (with new port, but same IP) | 10.1.1.1:2000 | 170.0.0.5:13591 | 10.1.1.1:2000 <-> 170.0.0.5:13591 |
New port (13591) allocation happens. New logging record is created. |
With BPA, for the first new flow, a bulk (group) of Ports are allocated (but only one port from the group is assigned for the new flow) for the Public IP and a logging record is created with Private IP and Public IP + Start Port + End Port. Next time, a new flow comes, a new port from the already allocated pool is taken and no logging record is created. Only when all the ports in the group are used, a new bulk is allocated and logging record is created. Similarly, when all the ports from a group is released, a (deletion) logging record is generated.
Following table captures the working of it (with BPA enabled) with sample IP addresses and port numbers.
| Event | Inside Source + Port | Bulk Port Allocation (size 64) | Outside Source IP + Port | Logging Record | Additional Comments |
|---|---|---|---|---|---|
| A new flow arrives | 10.1.1.1:1000 | Allocates Bulk Port range (8192 - 8255) for 170.0.0.5 | 170.0.0.5:8201 | 10.1.1.1 <-> 170.0.0.5:8192-8255 |
Bulk port allocation and new port (8201) assignment happens. New logging record is created. |
| Existing flow arrives | 10.1.1.1:1000 | N/A | 170.0.0.5:8201 | N/A |
No new Port allocation happens. No logging record is created. |
| A new flow arrives (with new port, but same IP) | 10.1.1.1:2000 | N/A | 170.0.0.5:8199 | N/A |
New Port (8199) allocation happens (from same port range). No logging record is created. |
| A new flow arrives (with new port, but same IP) | 10.1.1.1:5000 | N/A | 170.0.0.5:8236 | N/A |
New Port (8236) allocation happens (from same port range). No logging record is created. |
Following table illustrates the amount stoage space needed per second with varying translation creation + deletion rate for both Netflow and Syslog (with DBL disabled). It also shows the impact of BPA on the storage.
| NAT translation creation + deletion rate per second | Netflow without BPA | Syslog without BPA | Netflow with Bulk size 256 and 50% utilization | Syslog with Bulk size 256 and 50% utilization |
|---|---|---|---|---|
| 20,000 | 0.8 MB | 2.8 MB | 6.25 KB | 21.875 KB |
| 50,000 | 2 MB | 7 MB | 15.625 KB | 54.6875 KB |
| 100,000 | 4 MB | 14 MB | 31.25 KB | 109.375 KB |
| 500,000 | 20 MB | 70 MB | 156.25 KB | 546.875 KB |
| 1,000,000 | 40 MB | 140 MB | 312.5 KB | 1.093 MB |
NOTE: Both DBL and BPA cannot be enabled at the same time. This is because BPA requires logging record to be generated for a set of NAT entries whereas DBL requires logging record to be generated for each NAT entry. These are conflicting requirements.
Please collect the following information and accordingly determine External Logging related parameter configuration.
- What setup rate needs to be supported ?
- Do the Lawful Agencies mandate DBL ?
- What protocol (netflow or syslog) the external logging server support ?
- How many packets per second the logging server can support ?
- How many logging servers need to be configured ?
- How much space would be needed for storing logging record ? How much would the cost of disk space ?
Following table shows how to configure different external logging parameters.
| Configuration of External Logging Parameters |
|---|
service cgn cgn1 service-type nat44 nat1 inside-vrf ivrf1 ! Define Netflow V9 logging configuration external-logging netflow version 9 ! Define netflow server configuration server ! Define logging server address and port address 10.10.0.0 port 2055 ! Define Path MTU size path-mtu 1200 ! Define refresh rate refresh-rate 50 ! Define timeout timeout 50 ! Define Syslog logging configuration external-logging syslog server address 10.10.0.1 port 514 |
14. NAT Session Timeouts (TCP, UDP, ICMP)
As the new flows creates NAT entries, we need a way to delete those NAT entries as well. Protocols like UDP is connection-less and hence, there is no way to identify when a session / connection has ended by inspecting the packets. Also, in some cases, if no packet flows between the applications for a long period of time, there is no point in holding on to the NAT entries, as that will disallow creation of new NAT sessions.
Due the above reasons, NAT entries are deleted when session timeout happens.
For every protocol (TCP, UDP, ICMP), we have different types and values of session timeouts, as depicted below.
- TCP - It has two timeouts.
- Initial Timeout - It kicks in before the connection moves into Active state. Default: 120 sec.
- Active Timeout - It kicks in when the connection is in Active state. Default: 30 Minutes.
- UDP - It has two timeouts as well.
- Initial Timeout - It kicks in before the connection moves into Active state. Default: 30 sec.
- Active Timeout - It kicks in when the connection is in Active state. Default: 120 sec.
- ICMP - It has one timeout. Default: 60 sec.
If the timeout is configured to be too less, NAT sessions will be deleted too soon, resulting in changing of Public IP addresses. This may cause issues with the Applications.
If the timeout is configured to be too high, NAT sessions will remain in the system for long time (even though there is no data is flowing using the session) and it will restrict new sessions to be created as well (resulting in dropping of those packets).
Hence, timeout value needs to be set appropriately.
NOTE: These timeouts are set for the NAT44 instance (per VSM card) and cannot be configured differently for each Inside VRF.
You need to have some knowledge about the following, to determine the timeout values.
- Application traffic that is going through the network
- How sensitive it is with respect to change in IP address ?
- How periodically, it would generate packets
- How many NAT sessions are expected ?
Following table shows how to configure timeout values for different protocols.
| Configuration of Session Timeout (TCP, UDP, ICMP) |
|---|
service cgn cgn1 service-type nat44 nat1 ! Define UDP protocol session timeout values protocol udp session initial timeout 65535 session active timeout 65535 ! Define TCP protocol session timeout values protocol tcp session initial timeout 65535 session active timeout 65535 ! Define ICMP protocol session timeout value protocol icmp timeout 908 |
15. Endpoint Independent and Dependent Filtering (EIF / EDF)
Filtering behavior of NAT is explained in Section 5 of RFC 4787.
When an internal endpoint opens an outgoing session through a NAT, the NAT assigns a filtering rule for the mapping between an internal IP:port (X:x) and external IP:port (Y:y) tuple. The key behavior to describe is what criteria are used by the NAT to filter (Outside-to-Inside, O2I) packets originating from specific external endpoints. We have the following 3 options here:
- Endpoint-Independent Filtering (EIF) - NAT forwards any packet destined to X:x, regardless of the external IP address and port source.
- Endpoint-Dependent Filtering (EDF)
- Address-Dependent Filtering - NAT forwards any packet destined to X:x, provided it is coming from the external IP to which I2O packets were sent earlier.
- Address and Port-Dependent Filtering - NAT forwards any packet destined to X:x, provided it is coming from the external IP:port to which I2O packets were sent earlier.
All the behavior are explained in the following diagram with an example scenario.

As shown above, depending on the filtering policy and NAT session DB, O2I packets coming from specific IP and port will be either allowed to cross NAT device (VSM card) or dropped by CGv6 Application on VSM.
Table below shows how to configure CGv6 application on VSM to support different filtering policy.
| Configuration for Endpoint-Independent and Endpoint-Dependent Filtering |
|---|
! To configure Endpoint-Independent Filtering ! ------------------------------------------- service cgn cgn1 service-type nat44 nat1 inside-vrf ivrf1 ! Do not specify 'filter-policy' CLI for Endpoint-Independent Filtering |
! To configure Address Dependent Filtering ! ---------------------------------------- service cgn cgn1 service-type nat44 nat1 inside-vrf ivrf1 ! Filtering policy for Address Dependent Filtering filter-policy ignore-port |
! To configure Address and Port Dependent Filtering ! ------------------------------------------------- service cgn cgn1 service-type nat44 nat1 inside-vrf ivrf1 ! Filtering policy for Address and Port Dependent Filtering filter-policy |
16. Traffic Diversion (to VSM)
We can use different mechanisms to divert the traffic to VSM card (to specific ServiceApp interface).
Default Route
If the inside traffic is arriving on a (Inside) VRF and ALL traffic needs to undergo NAT44 operation, we can add a default route under the VRF to divert traffic to the Inside ServiceApp (as shown below).
| Configuration for Traffic Diversion using Default route |
|---|
! Define static route for Inside-to-outside traffic ! ------------------------------------------------- router static ! Specify the Inside VRF vrf insidevrf1 ! Define address family address-family ipv4 unicast ! Re-direct all traffic to Inside Service App 0.0.0.0/0 serviceapp 1 |
Static Route
In some cases, Outside ServiceApp interfaces reside in same / default VRF. Hence, in order to divert O2I traffic to specific Outside ServiceApp interfaces, static route can be used in the following way.
| Configuration for Traffic Diversion using Static Route |
|---|
router static address-family ipv4 unicast ! Diverting traffic for one Public IP pool to one Outside ServiceApp 100.1.1.0/24 serviceapp 2 ! Diverting traffic for another Public IP pool to another Outside ServiceApp 200.1.1.0/24 serviceapp 4 |
ACL-based Forwarding (ABF)
In certain deployment cases, default route may not work.
- Deployment Use-case 1: Customer wants to divert traffic coming from specific subscriber network (containing Private IP address) to VSM (for NAT44) and the remaining traffic (which may already contain Public IP address) need not go to VSM.
- Deployment Use-case 2: Customer wants to distribute subscriber traffic into different Inside VRFs which may go to same VSM card or different VSM cards (but, will certainly using different Public IP pool).
- Deployment Use-case 3: Subscriber / Access / Inside traffic comes in default / global VRF and we need to distribute the traffic to different Inside ServiceApps which are in different Inside VRFs.
NOTE: Typically, ABF is to be used in Private side / Subscriber side and NOT towards Public / Core / Network side.
In the above cases, ABF provides a very good solution. Below is sample configuration on how to use ABF for traffic diversion.
| Configuration for Traffic Diversion using ABF |
|---|
! Define IPv4 Access List ipv4 access-list nat44_abf ! Divert to ServiceApp 1 10 permit ipv4 10.0.100.0/24 any nexthop1 vrf ivrf1 ipv4 5.1.1.2 ! Divert to ServiceApp 3 20 permit ipv4 10.0.200.0/24 any nexthop1 vrf ivrf2 ipv4 6.1.1.2 100 permit ipv4 any any ! Configure Ingress Interface interface TenGigE0/5/0/2 vrf subscriber ipv4 address 10.1.1.1 255.255.255.0 ! Apply ABF on Ingress Interface ipv4 access-group nat44_abf ingress ! Define one Inside ServiceApp interface interface ServiceApp1 vrf ivrf1 ipv4 address 5.1.1.1/30 service cgn cgn1 service-type nat44 ! Define another Inside ServiceApp interface interface ServiceApp3 vrf ivrf2 ipv4 address 6.1.1.1/30 service cgn cgn1 service-type nat44 |
17. Static Port Forwarding
There is a very important point about Dynamic NAT44. All the NAT translations / sessions are created by I2O traffic. If O2I traffic reaches VSM for which there is no NAT entry, the packets will be dropped. This works fine for most of the cases as the session / traffic is initiated by Applications which reside on Private side.
However, there are cases, where a server resides on the Private side of the network. In this case, there are 2 issues.
- Clients (on Public side) cannot initiate session to this Server, as those (O2I) packets will be dropped by VSM.
- Clients do not know the Public IP of the Server (and cannot use Private IP to communicate either)
To address these problems related to Server sitting on Private side of the network, a new feature called "Static Port Forwarding" is introduced. Following diagram explains "Static Port Forwarding" feature functionality.
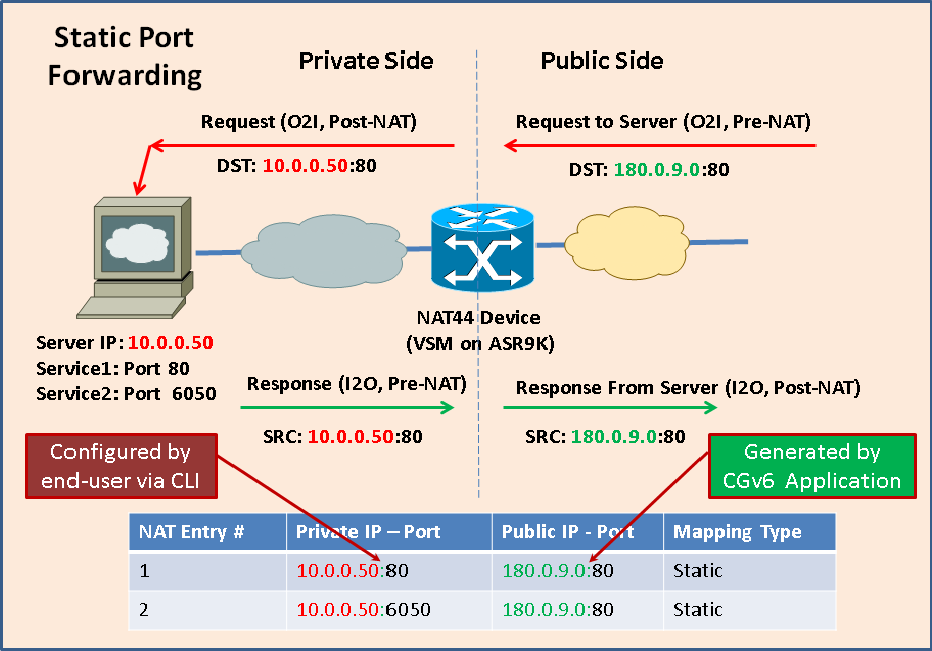
Using Static Port Forwarding, user can provide the Private IP address and Port (via CLI) and NAT44 Application on VSM generates (dynamically) the corresponding Public IP and Port. Also, these mapping are made permanent - i.e., they do not get timed out and get deleted. The Public IP and port generated by the Application can be added to DNS database and thus made available to all.
With this design, any device on Public side of network can now send traffic to the known Public IP and port (to reach the Server sitting inside Private network). Also, as the NAT entry is permanent, O2I traffic always finds the entry and using the same can translate the packet (without dropping it).
Staic Port Forwarding entries can be created separately for each protocol - TCP, UDP and ICMP. To know the maximum number of such entries, please check CGv6 on VSM Feature page.
NOTES:
- User cannot provide the Outside / Public IP and port while configuring Static Port Forwarding.
- Outside / Public IP is generated by the NAT44 Application and hence, can be random.
- Outside port is usually assigned same as Inside Port, unless the Outside port is already being used
As these are used for Servers located in Private network, it is desirable that the Public IP address remain constant across RP failover.
As Outside / Public IP address for a Static Port Forwarding entry is allocated by NAT44 application based on the instant situation of Public IP availability stock as well as the allocation algorithm's state, it is highly probable that if the Static Port Forwarding entry is deleted and re-added or, if the VSM card is reloaded), it may allocate a different Public IP address.
In order to keep the same Outside IP address, it is recommended to add the Static Port Forwarding configuration as a first thing after VSM card comes up and when there is no NAT traffic on the router / VSM card (could be in a "maintenance window"). That way, every time, VSM is reloaded, the Public IP addresses assigned for Static Port Forwarding entries will remain the same.
Try to find out the following, before using Static Port Forwarding.
- Will there be any Servers sitting in the Private side of the deployment network ?
- How many of those Servers will be ?
- Can the Public IP address of the Servers be random and can be published via DNS or similar mechanism ?
A sample configuration for Static Port Forwarding is shown below.
| Configuration for Static Port Forwarding |
|---|
service cgn cgn1 service type nat44 nat1 inside-vrf ivrf1 map address-pool 180.0.0.0/24 ! Define TCP related configuration protocol tcp ! Define Static Port Forwarding configuration static-forward inside address 10.0.0.50 port 6050 static-forward inside address 10.0.0.50 port 80 ! Define UDP related configuration protocol udp ! Define Static Port Forwarding configuration static-forward inside address 10.0.0.61 port 550 ! Define ICMP related configuration protocol icmp ! Define Static Port Forwarding configuration ! For ICMP, 'identifier' field in ICMP header is used for 'port' static-forward inside address 10.0.0.189 port 750 |
Following table shows the NAT entries corresponding to the above Static Port Forwarding entries (for TCP protocol).
| "show cgn nat44 <> inside--translation" output for Static Port Forwarding |
|---|
RP/0/RSP0/CPU0:VSM-Lab#show cgn nat44 nat44-1 inside-translation protocol tcp inside-vrf vrf1 inside-address 10.0.0.50 port start 25 end 8000 Fri Nov 1 13:44:44.874 UTC Inside-translation details --------------------------- NAT44 instance : nat44-1 Inside-VRF : vrf1 -------------------------------------------------------------------------------------------- Outside Protocol Inside Outside Translation Inside Outside Address Source Source Type to to Port Port Outside Inside Packets Packets -------------------------------------------------------------------------------------------- 180.0.9.0 tcp 80 80 static 1218 45 180.0.9.0 tcp 6050 6050 static 516 7162 |
NOTE:
- Outside IP (180.0.9.0) and Ports are assigned by the NAT44 Application when user supplies Inside IP (10.0.0.50) and Ports (80, 6025).
- "Translation Type" is shown as "static" (as opposed to "dynamic")
- Outside port is same as Inside port (usually, unless it is not available)
18. Application Layer Gateway (ALG)
Application Layer Gateway (ALG) is a device which has the capability of inspecting into a packet beyond layer 4 and can change Application layer content to meet certain need.
NAT44 changes IP address and Layer 4 (UDP/TCP/ICMP etc.) port. There are certain applications which embeds IP address and/or Port information in Application content. Now, the issue is while the packet traverses across a NAT44 device, layer 3 and 4 addresses get changed. However, in the Application layer, the content still contains old layer 3 and / or layer 4 addresses. This causes an issue in the Application as this is unexpected. Hence, the need of ALG functionality within a NAT device which while changing Layer 3 and 4 packet content, also changes Application content where Layer 3 and 4 addresses were embedded. With this change, end Application will be happy as it does not need to deal with 2 sets of addresses any more.
However, there are 2 ways this problem can be solved.
- Adding ALG functionality to NAT device - ALG functionality needs to be added to NAT device for each such Applicaton which embeds Layer 3 and/or 4 addresses in Application content.
- Changing the Application to deal with NAT device in the network - Application needs to assume that the Layer 3 and/or 4 address can get changed on the way (as there could be NAT device in the network) and hence, either avoid embedding Layer 3/4 addresses in Application content or find other mechanism to handle 2 sets of addresses.
The main challenges in adding ALG functionality to NAT device are:
- Every time a new Application is written which embeds Layer 3/4 address in Application content, all NAT devices need to be changed to address the new Application. This is not scalable as lot of new Applications are written everyday.
- In order to implement ALG for an Application, NAT device needs to understand the Application protocol as well as packet formt/content. Many Applications implement proprietary protocol and hence, do not want to make the same as public information. Hence, those Application packets will face issues with NAT device.
- There are applications (like, crypto) which do not want any intermediate device to understand / peek into the Application content and modify it. These packets should only be encoded/decoded by end Applications. These application packets would not be able to deal with intermediate NAT device.
On the contrary,
- Application can be written in such a way not to use Layer 3/4 addresses in Application content and to use Application-level ID, instead.
- There can be other mechanisms, e.g. - using STUN (Session Traversal Utilities for NAT) that applications can take to handle intermediate NAT device.
NOTE: Due to the above reasons, our solution does not encourage to support ALG within NAT44 functionality.
However, few basic ALG functionality is implemented with NAT44 Application. These are:
- Active FTP (File Transfer Protocol) - Passive FTP does not need ALG.
- RTSP (Real Time Streaming Protocol)
- PPTP (Point-to-Point Tunneling Protocol)
Following table show how to configure / enable different ALGs on VSM.
| Configuration of ALGs |
|---|
service cgn cgn1 service-type nat44 nat1 ! Enable Active FTP ALG alg ActiveFTP ! Enable RTSP ALG alg rtsp ! Enable PPTP ALG alg pptpAlg |
19. Redundancy
Redundancy is an integral part of CGN (Carrier Grade NAT). Majority of the Service Providers want Redundancy in their network to make it more resilient. It helps in minimizing the traffic outage when one device fails.
On VSM, we support 2 types of redundancy.
- N:1 ABF-based redundancy (N can be 1 as well)
- 1:1 Warm Stand-by Redundancy (starting from XR release 5.2.2)
N:1 ABF-Based Redundancy
In this case, there needs to be N Primary VSM card and 1 Backup VSM card. Value of N can be 1 as well, but typically would be 2 or 3. Following are different characteristics of this solution.
- Each VSM card needs to be configured independently
- Configuration (usually) should be similar (w.r.to parameters, number of ServiceApp interfaces, etc.)
- In ABF configuration, For each Primary VSM,
- ServiceApp interface on Primary VSM becomes 1st Next-Hop and ServiceApp interface on Back-up VSM becomes 2nd Next-hop
- Each VSM will have different Public IP address pools (Address Pool is not same in Primary and Backup)
- When one Primary VSM card fails, Backup VSM card receives all the traffic of Primary VSM card.
- When Primary VSM card comes up, all traffic again switches back to it from Backup VSM card (it causes, another traffic outage)
- Each VSM card can support full scale and bandwidth
Following table shows how the ABF Next-Hop configuration would look like for N:1 (N = 3) ABF-based Redundancy.
| ServiceApp interfaces | ABF Next-Hop 1 | ABF Next-Hop 2 |
|---|---|---|
| ServiceApp interfaces on Primary VSM 1 | ServiceApp interfaces on Primary VSM 1 |
ServiceApp interfaces on Backup VSM |
|
ServiceApp interfaces on Primary VSM 2 |
ServiceApp interfaces on Primary VSM 2 |
ServiceApp interfaces on Backup VSM |
|
ServiceApp interfaces on Primary VSM 3 |
ServiceApp interfaces on Primary VSM 3 |
ServiceApp interfaces on Backup VSM |
Following diagram depicts N:1 (N = 2) configuration with 1 set of ServiceApps.
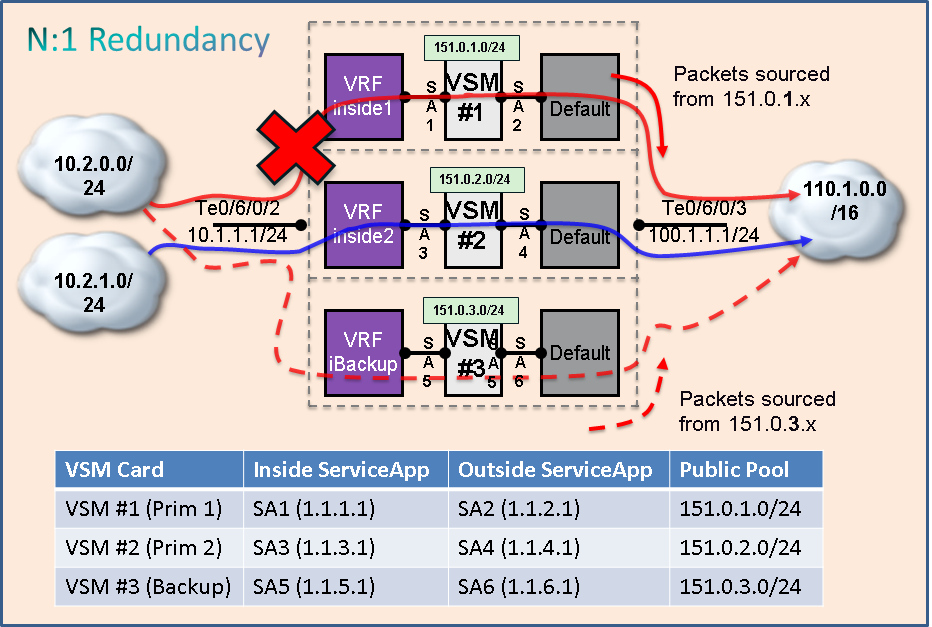
As shown in the diagram,
- before 1st failure, traffic coming from 10.2.0.0/24 subnet will go via Primary 1 VSM (Inside ServiceApp 1) which will use Public IP pool of 151.0.1.0/24.
- if and when Primary 1 VSM fails, traffic coming from 10.2.0.0/24 subnet will go via Backup VSM (Inside ServiceApp 5) which will use Public IP pool of 151.0.3.0/24.
- Instead of Primary 1 VSM, if Primary 2 VSM would have failed, traffic from 10.2.1.0/24 (not 10.2.0.0/24) should have switched to Backup VSM.
Following table captures the relevant ABF configuration for this sample setup.
| Sample Configuration for N:1 Redundancy using ABF |
|---|
|
! ABF rule for Inside to Outside traffic ipv4 access-list abf_2_1 10 permit ipv4 10.2.0.0/24 any nexthop1 vrf inside1 ipv4 1.1.1.2 nexthop2 vrf ibackup ipv4 1.1.5.2 20 permit ipv4 10.2.1.0/24 any nexthop1 vrf inside2 ipv4 1.1.3.2 nexthop2 vrf ibackup ipv4 1.1.5.2 30 permit ipv4 any any
! Static route for Outside to Inside traffic router static address-family ipv4 unicast 151.0.1.0/24 ServiceApp 2 151.0.2.0/24 ServiceApp 4 151.0.3.0/24 ServiceApp 6 |
1:1 Warm Stand-by Redundancy
In this mode, one VSM card acts as Primary and another as backup. Following are the properties of 1:1 Warm Stand-by redundancy.
- Easy to configure (Active and Stand-by locations are specified once)
- A single Public IP address pool is used
- Configuration is sent to both VSM cards
- NAT Application data traffic reaches to Active card only
- During switchover (usually takes few seconds), dynamic NAT entries get deleted (on failed VSM cards) and re-created on newly Active VSM card. Hence, there would be some traffic drop. Also, Private to Public IP/Port mapping gets changed during Switchover.
- When the previously Active VSM comes up, it stays as Stand-by and the traffic does not come back to it (until the Active VSM card fails)
- Each VSM can support full scale and throughput
Following diagram explains the working of 1:1 Redundancy for NAT44.

Please note that both Primary and Backup VSM cards share same ServiceApp interfaces and NAT44 configuration (including Public IP pool).
Following tables shows how to configure 1:1 VSM redundancy.
| Configuration for 1:1 Warm Standby Redundancy |
|---|
|
! Configure preferred-active and preferred-standby VSM service cgn cgn1 service-location preferred-active 0/1/cpu0 preferred-standby 0/2/cpu0 service-type nat44 nat1 inside-vrf inside1 map address-pool 151.0.1.0/24 ! Remaining configurration ... |
To check the health of the VSM card and trigger redundancy switchover, in case any failure occurs, following HA-specific test can be enabled:
- Data Path Test - It checks if the packet path from CGv6 Application to Fabric works fine or not.
If the test is enabled and any failure is detected by the test, the VSM card will be reloaded.
NOTE: By default, these tests run in the back-ground however, no acton is taken in case failure is detected. Using the following CLI, the test is enabled.
| Configuration of HA Data-Path tests |
|---|
! To enable Data Path Test service-cgv6-ha location 0/1/cpu0 datapath-test |
20. NAT44 Licenses
In order to use NAT44 functionality on ASR9K, Licenses needs to be purchased. Depending on the number of Stateful Translations needed by the solution, required number of NAT44 specific licenses can be purchased. This fits nicely with "Pay as you grow" model as well.
Following licenses need to be purchased for NAT44 and other CGv6 applications.
| License Part Number | License Description | Additional Comments |
|---|---|---|
| A9K-VM-LIC | Cisco ASR 9000 Application VM License | For launching (activating) any Application VM, this license is needed. When CGN software is ordered, one free A9K-VM-LIC will be provided along with it. |
| A9K-XLAT-LIC-5M | Cisco ASR 9000 CGN / NAT44 License (1 per 5 million translations) |
For 60 Millions translations, 12 of these licenses will be needed. Same license is applicable for both ISM as well as VSM cards. |
Details of the Licensing (how to install, etc.) can be obtained from ASR9K S/w License Operations White Paper.
21. Summary of parameter values
In the following table, all the useful parameters are listed along with their default and valid range of values. You can consult this table to come up with the parameter value for your deployment case.
| Parameter (CLI) | Defined at what level | Default Value | Range of Values | Supported from XR Release | Additional Comments |
|---|---|---|---|---|---|
|
alg ActiveFTP |
per NAT44 instance |
Disabled |
Enable / Disable | 5.1.1 | Active FTP ALG |
| alg pptpAlg |
per NAT44 instance |
Disabled | Enable / Disable | 5.1.1 | PPTP ALG |
| alg rtsp |
per NAT44 instance |
Disabled | Enable / Disable | 5.1.1 | RTSP ALG |
|
bulk-port-alloc size |
per Inside VRF | Disabled |
16, 32, 64, 128, 256, 512, 1024, 2048, 4096 |
5.1.1 | |
|
dynamic-port-range start |
per NAT44 instance | 1024 | 1 - 65535 | 5.1.1 |
Starting port number (for Public IP address) to be used for Dynamic NAT entries. |
| external-logging netflow v9 server path-mtu | per Inside VRF | 1500 bytes | 100 - 2000 | 5.1.1 | |
| external-logging netflow v9 server refresh-rate | per Inside VRF | 500 packets | 1 - 600 | 5.1.1 |
For sending NFv9 template |
| external-logging netflow v9 server timeout | per Inside VRF | 30 seconds | 1 - 3600 | 5.1.1 | For sending NFv9 template |
|
external-logging syslog server path-mtu |
per Inside VRF | 1500 bytes | 100 - 2000 | 5.1.1 | |
| map ip one-to-one | per Inside VRF | Disabled | 1 - 65535 | 5.1.1 | |
| portlimit | per NAT44 instance | 100 | 1 - 65535 | 5.1.1 | |
|
protocol udp session initial timeout |
per NAT44 instance | 30 sec | 1 - 65535 | 5.1.1 | |
|
protocol udp session active timeout |
per NAT44 instance | 120 sec | 1 - 65535 | 5.1.1 | |
|
protocol tcp session initial timeout |
per NAT44 instance | 120 sec | 1 - 65535 | 5.1.1 | |
|
protocol tcp session active timeout |
per NAT44 instance | 1800 sec | 1 - 65535 | 5.1.1 | |
| protocol tcp mss | per Inside VRF | 28 - 1500 bytes | 5.1.1 |
22. NAT44 Configuration / Feature Differences with ISM
| Parameter / Criteria | ISM Value | VSM Value | Additional Comments |
|---|---|---|---|
| Number of ServiceApp Interfaces | 244 | 256 | |
| Number of NAT44 Translations | 20 Millions | 60 Millions | |
| End-point Dependent Filtering | Not Supported | Supported | |
| TCP Sequence Check | Not Supported | Supported | |
| CLI: map ip many-to-one | Supported | Not Supported | Will be supported on VSM in future release |
| Minimum number of Public IPv4 addresses in a Pool | 4 (i.e., /30) | 32 (i.e., /27) |
Back to top
23. MTU and Fragmentation Considerations
Cisco recommends keeping the default physical interface MTU size on the customer-facing interfaces in NAT44 deployment.
Configure the MTU on physical VSM interfaces to 1518.
Specific Deployment Scenarios / Use-Cases
In this section, specific deployment scenarion / use-cases and presented which can be useful for some deployment.
24. Sample Applications over NAT44
Following table lists some of the important / well-known applications and their working status over NAT44 (on VSM).
NOTE:
- This list is not a complete/exhaustive list of applications that would work with NAT44.
- It also does not mean that any application not listed here will not work with NAT44.
| Application | Details of Application (Protocol / Port) | Working Status with NAT44 |
|---|---|---|
| HTTP | Typically HTTP server runs over TCP Port 80 | Works with NAT44 |
| Typically uses TCP, server ports: SMTP (25, 587), POP3 (110), IMAP (143) |
Works with NAT44 |
|
| FTP | Typically uses TCP port 20 (data) and port 21 (control) | Works with NAT44 |
| Telnet | Typically uses TCP port 23 | Works with NAT44 |
| SSH | Typically uses TCP port 22 | Works with NAT44 |
| VNC | Typically uses TCP port 5900, 5800, 5500 | Works with NAT44 |
| VPN Client (SSL) | Typically uses TCP | Works with NAT44 |
| VPN Client (PPTP+GRE) | Typically uses TCP and GRE | Works with NAT44 |
| VPN Client (IPSec) | Typically uses IPSec (via NAT-T) | Works with NAT44 (as NAT-T uses UDP) |
| Xbox Gaming | Works with NAT44 |
25. Multiple Outside ServiceApps sharing same Outside VRF
It is very common to have default VRF as Outside VRF and when there are multiple Inside VRFs mapped to the same. In the following table, a sample ServiceApp and VRF configuration is shown. Please note that in this case, multiple Outside ServiceApps share share a comon Outside VRF.
| Inside VRF | Inside ServiceApp | Outside VRF | Outside ServiceApp |
|---|---|---|---|
| ivrf1 | ServiceApp 1 | default or ovrf | ServiceApp 2 |
| ivrf2 | ServiceApp 3 |
default or ovrf |
ServiceApp 4 |
To handle this scenario, we need to specify "outsideServiceApp" parameter configuration to indicate what is the Outside ServiceApp to be used with the mapping. Static route rule for specific Public IP address pool should guide the traffic to specific Outside ServiceApp. Only these configurations are shown below. Rest of the configuration remain the same.
| Configuration for Shared / Common Outside VRF |
|---|
service cgn cgn1 service-type nat44 nat1 ! 1st Inside VRF inside-vrf ivrf1 ! MAP command using outsideServiceApp map [outside-vrf ovrf] outsideServiceApp ServiceApp2 address-pool 100.0.1.0/24 ! 2nd Inside VRF inside-vrf ivrf2 ! MAP command using outsideServiceApp map [outside-vrf ovrf] outsideServiceApp ServiceApp4 address-pool 100.0.2.0/24 router static [vrf ovrf] address-family ipv4 unicast ! Divert traffic to 1st Outside ServiceApp 100.0.1.0/24 ServiceApp 2 ! Divert traffic to 2nd Outside ServiceApp 100.0.2.0/24 ServiceApp 4 |
26. NAT Bypass
There is an use-case where traffic selected traffic coming onto ASR9K via a Private side interface needs to go via NAT44 application, whereas remaining traffic can bypass NAT44 and should get forwarded via regular forwarding rule. This is called NAT bypass.
To implement NAT bypass, let's consider this situation:
- Private Traffic enters ASR9K via one VRF (say, RED)
- Selected traffic gets diverted to VSM card's Inside ServiceApp which is in different VRF (say, BLUE) and after translation comes out of Outside ServiceApp and eventually goes out of ASR9K via core-facing interface which is in RED VRF.
- Rest of the traffic (which bypasses NAT44) goes out of ASR9K via same core-facing i/f in RED VRF.
Please note that other than NAT bypass, there could be other deployment scenario where preserving VRF (across VSM) becomes a necessity. But, the solution would be same / very similar.
The above scenario can be achieved using VSM with some additional ABF and Static Route and appropriate VRF configuration.
Let us take a look at the following diagram as a sample scenario.
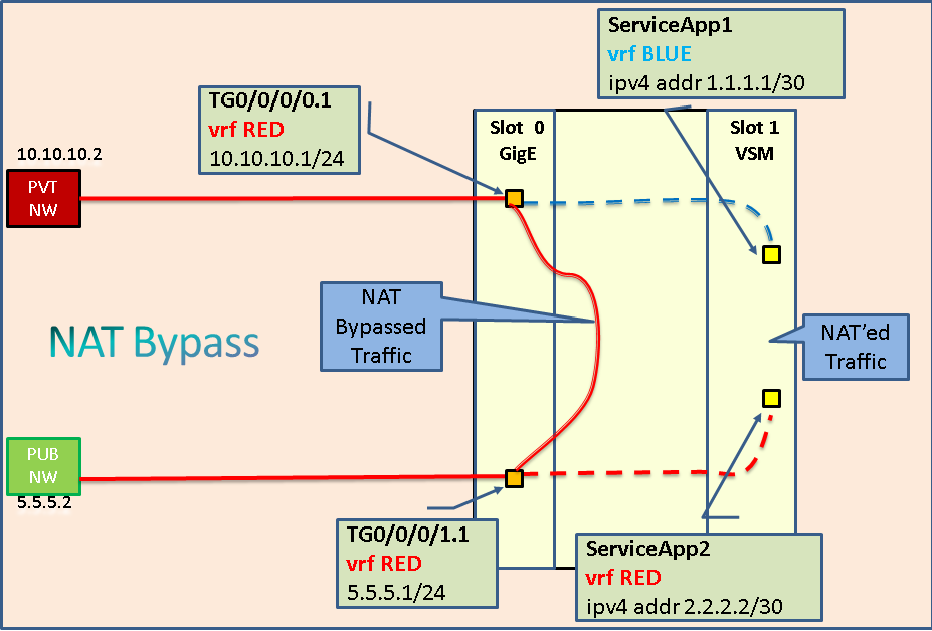
In the above diagram, traffic enters and exits out of ASR9K in RED VRF. Also, please note that Inside ServiceApp is in BLUE vrf whereas Outside ServiceApp is in RED VRF.
Following table shows the specific or additional configuration that is needed for appropriate traffic diversion.
| Additional Configuration to support NAT Bypass |
|---|
|
! Define ACL to divert traffic to ServiceApp 1 (RED to BLUE VRF) ipv4 access-list cgn_abf
! Divert traffic to ServiceApp 1 in BLUE VRF 10 permit ipv4 10.10.10.0/24 any nexthop1 vrf BLUE ipv4 1.1.1.2
20 permit ipv4 any any
! Apply ABF on Ingress LC interface interface TenGigE 0/0/0/0.1 vrf RED ipv4 address 10.10.10.1/24
! Apply Ingress ABF ipv4 access-group cgn_abf ingress
! We need a special static route to divert O2I traffic (after reverse NAT) ! to the right interface router static
! After reverse NAT, look-up is done in BLUE (Inside) VRF vrf BLUE
address-family ipv4 unicast
! Divert to TenGigE 0/0/0/0.1 interface 10.10.10.0/24 vrf RED 10.10.10.2 |
27. MPLS (Layer 3) VPN and NAT Interworking
An Multiprotocol Label Switching (MPLS) Layer 3 Virtual Private Network (L3VPN) consists of a set of sites that are interconnected by means of an MPLS provider core network. At each customer site, one or more customer edge (CE) routers attach to one or more provider edge (PE) routers.
MPLS VPNs are easier to manage and expand than conventional VPNs. When a new site is added to an MPLS VPN, only the edge router of the service provider that provides services to the customer site needs to be updated. The components of the MPLS VPN are described as follows:
- Provider (P) router — Router in the core of the provider network. PE routers run MPLS switching and do not attach VPN labels to routed packets. VPN labels are used to direct data packets to the correct private network or customer edge router.
- Provider Edge (PE) router — Router that attaches the VPN label to incoming packets based on the interface or subinterface on which they are received, and also attaches the MPLS core labels. A PE router attaches directly to a CE router.
- Customer edge (CE) router — Edge router on the network of the ISP that connects to the PE router on the network. A CE router must interface with a PE router.
Details on L3VPN can be obtained from ASR9K MPLS Layer 3 VPN Configuration Guide.
Service providers and enterprises that have network application services they want to offer or share with customers and partners will want to minimize any connectivity burden placed on the user of the service. It is desirable, even mandatory, to extend the offering to as many potential users as needed to achieve the desired goals or return.
By deploying NAT within the common MPLS VPN infrastructure, communications service providers can relieve some of the connectivity burden on customers and accelerate their ability to link more shared application services to more consumers of those services
There are two options for NAT deployment within the MPLS provider edge:
- Distributed with ingress NAT PEs
- Centralized with egress NAT PEs
Following diagram shows Distrbuted NAT scenario with Ingress NAT PEs.
With this design, scalability is maintained to a large extent while performance is optimized by distributing the NAT function over many edge devices. Each NAT PE handles traffic for sites locally connected to that PE. NAT rules and access control lists or route maps control which packets require translation.
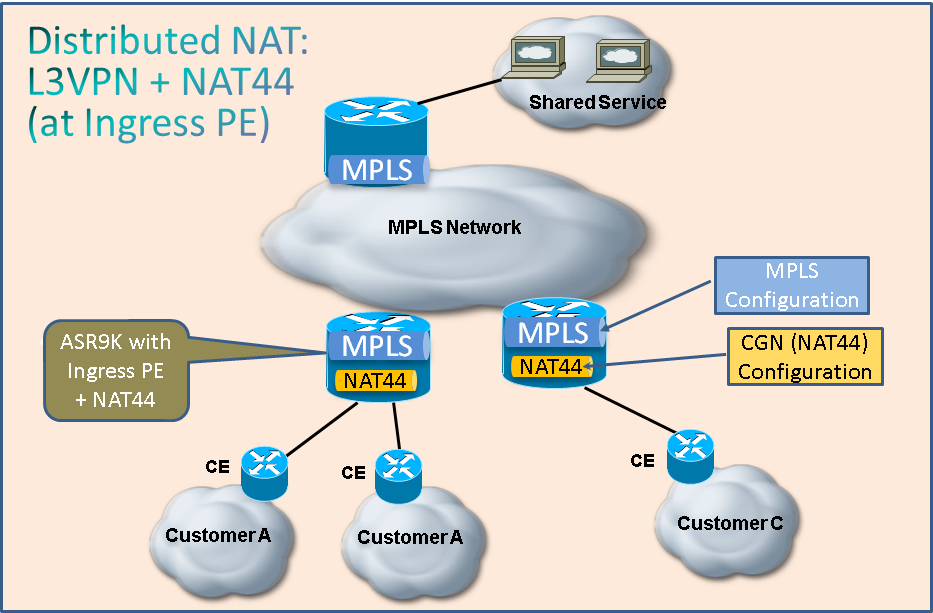
In the above case, at ingress PE router, customer private IP addresses are NAT'ed to public IP address by VSM card and then MPLS labels are added by it before the packet goes out of ASR9K. On the return path, MPLS label(s) are removed by MPLS-facing LC and IT packets are sent to VSM. VSM performs reverse NAT and sends the packet to LC which then sends it back to CE router.
Following diagram shows Distrbuted NAT scenario with Ingress NAT PEs.
With this design, scalability is reduced to some degree since the central PE must maintain routes for all customer networks that access the shared service. The application performance requirements must also be considered so that the traffic does not overburden the router that must translate the IP addresses of the packets. Because NAT occurs centrally for all customers using this path, IP address pools can be shared; thus, the total number of subnets required is reduced.

In the above case, in the egress PE router, first MPLS labels are removed by ingress LC and the IP packet is sent to VSM card. Customer private IP addresses are NAT'ed to public IP address by VSM card and the packets are forwarded to shared service network. In the reverse path, VSM translates Public destination IP to private IP addresses and then adds MPLS labels before sending it to egress LC. Egress LC swaps one label and sends the packet out of ASR9K towards MPLS network.
NOTE: MPLS labels should be removed by LC before sending the packet to VSM as IP packet. However, VSM can add the required MPLS labels before sending the packet to egress LC.
For sample MPLS VPN configuration, please refer to "Configuration Example: MPLS VPN on XR" document.
28. NAT Hairpining
Host behind a NAT device (on Private side) communicating with another host behind the same NAT device (on Private side) is called "NAT Hairpinning". Let us consider the following deployment use-case.
We have a server behind a NAT device which has a Public IP as well, created using Static Port Forwarding configuration. Now, this server can be accessed from hosts on public side of NAT device as well as Private side of the NAT device. When a host on Private side of the NAT device tries to communicate with the Server, it uses NAT Hairpinning. Following diagram depicts how NAT hairpinning works with NAT44 on VSM.
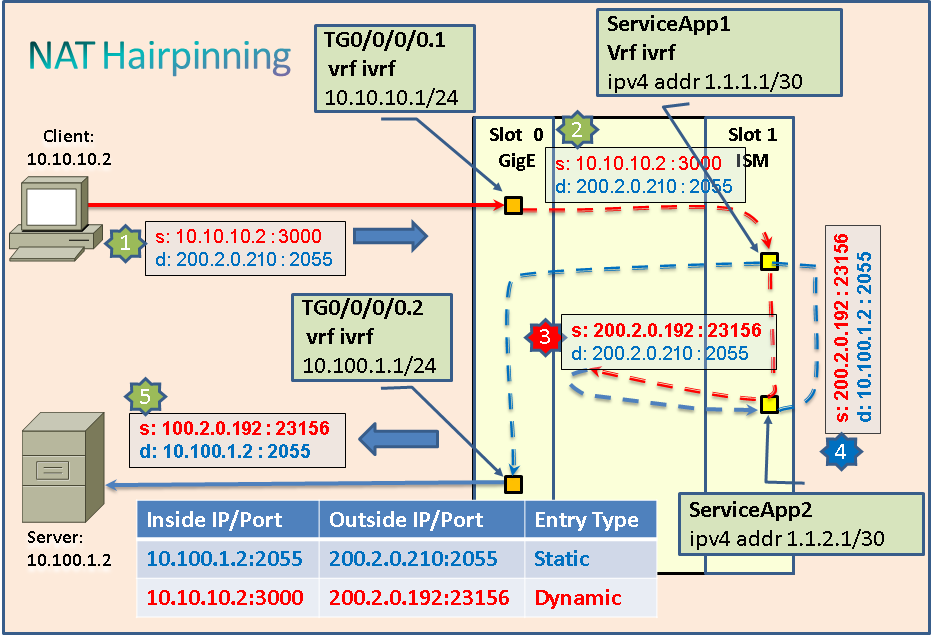
In this case, we first add a Static Port Forwarding entry for a service offered by the Server at 10.100.1.2:2055. Let's say, the Public IP pool configured is 200.2.0.0/24. NAT44 application allocates Public IP and port as 200.2.0.210:2055 (Please note that the port is preserved here). This Public IP and port is published / made available to the hosts. Let's the packet flow now when a host with Private IP 10.10.10.2 tries to access the service.
- Step 1: Host sends a packet (with Source IP 10.10.10.2 and port 3000) to Server's Public IP and port and the packet reaches ASR9K on TenGigE 0/0/0/0.1 which is in VRF ivrf.
- Step 2: Because of Static Route configuration in VRF ivrf, the packet is forwarded to VSM card via (Inside) ServiceApp 1 interface.
- Step 3: Application treats this as I2O packet. A new dynamic NAT entry is created by NAT44 application and it translates source IP/Port from (Private) 10.10.10.2:3000 to (Public) 200.2.0.192:23516. Please note that the Destination IP address and port are not touched here. The packet is sent out and because of Static route definition for Public IP pool, the packet comes back to VSM card via (Outside) ServiceApp 2.
- Step 4: Application treats this as O2I packet. As there is already a (Static) NAT entry exists for Destination IP and port, NAT44 application translates Destination IP address/Port from (Public) 200.2.0.210:2055 to (Private) 10.100.1.2:2055. Please note that the Source IP address and port are not touched here. The packet is sent out and via regular forwarding rule, it reaches egress i/f TenGigE 0/0/0/0.2.
- Step 5: The packet is forwarded to the Server with Source IP/Port as 200.2.0.192:23516 and Destination IP/Port as 10.100.1.2:2055 and the server consumes it.
Response from the Server will take the reverse path and it will use Dynamic NAT rule in first reverse NAT and then Static NAT rule in second NAT processing, to reach the host.
In this case, Static Port Forwarding configuration is used for Server as an use-case. But, it can be another host as well for which there is no Static Port Forwarding configuration. Only important thing is sender needs to know the Public IP and port of the receiver.
Please note that there is no specific NAT44 configuration is needed for this. Regular / basic NAT44 configuration will work here. Hence, no configuration is provided here.
29. Handling of Asymmetric I2O and O2I traffic with better performance
Unlike ISM card, we do NOT need to make any special configuration (like, dividing traffic into 2 sub-groups) for VSM. As long as I2O + O2I traffic do not exceed the capacity of the CGv6 Application instances, direction of traffic does not matter i.e., I2O and O2I traffic do not need to be equally balanced.
Validation of Configuration
Once NAT44 on VSM is configured, we need different ways (mainly, via "show" CLIs) to validate those. In this section, important NAT44 related CLIs are listed and also explained how those can be used for validation.
30. show run
As a first step, different "show run" output should be verified to ensure that configuration commands are rightly applied. Following commands can be used.
| 'show run' commands | Usage of it |
|---|---|
| show running-configuration or show run |
- Displays all the configuration on ASR9K. - If you have less configuration, this is better way to get all NAT44 configuration at one shot. - Otherwise (if you have lot of configuration, this may not be the best way to get all NAT44 configuration |
| show run service cgn * | - Displays only CGN related information |
| show run interface service* |
- Displays all ServiceInfra and ServiceApp interface configuration - Also includes Service-Mgmt and Service-Engine interface configuration (which can be ignored) |
| show run router static | - Displays all static route information. |
31. show virtual-service list
This CLI will list down the services that are installed and running on ASR9K chassis.
| Sample "show virtual-service list" CLI Output |
|---|
|
RP/0/RSP1/CPU0:SERVICE_PE2_1#show virtual-service list Tue Dec 24 15:35:50.161 UTC
Virtual Service List:
Name Status Package Name Node Name ______________________________________________________________________________ cgn1 Activated vsmcgv6.ova 0/1/CPU0 RP/0/RSP1/CPU0:SERVICE_PE2_1# |
32. show virtual-service detail
This CLI shows detail information about the CGv6 service VM (mainly, what h/w resources are given to it, etc.), as shown below.
| Sample "show virtual-service detail name <>" Output |
|---|
|
RP/0/RSP1/CPU0:SERVICE_PE2_1#show virtual-service detail name cgn1 Tue Dec 24 15:38:20.951 UTC
Virtual Service cgn1 Detail State : Activated Node name : 0/1/CPU0 Node status : Install Mgr Ready, SDR Mgr Ready Package information Name : vsmcgv6_ivybridge.ova Path : disk0:/vsmcgv6.ova Application Name : CGv6 Installed version : 1.0 Description : Carrier Grade NAT Signing Key type : Unknown Package Method : SHA1 Licensing Name : Not Available Version : Not Available
Activated profile name : None
Resource reservation Disk : 10000MB Memory : 32768MB CPU : 75 (system CPU %) VCPU : 60
Attached devices # Type Name Alias 1 Watchdog None None 2 CDROM hdc ide0-1-0 3 HDD hda DD_10GB_UM_local 4 Serial/aux None serial1 5 Serial/shell None serial0 6 NIC net1 net1 7 NIC net1 net1 8 NIC net1 net1 9 NIC net1 net1 10 NIC net1 net1 11 NIC net1 net1 12 NIC net1 net1 13 NIC net1 net1 14 NIC net1 net1 15 NIC net1 net1 16 NIC net1 net1 17 NIC net1 net1
Network interfaces: Name TenGigE0/1/1/0 TenGigE0/1/1/1 TenGigE0/1/1/2 TenGigE0/1/1/3 TenGigE0/1/1/4 TenGigE0/1/1/5 TenGigE0/1/1/6 TenGigE0/1/1/7 TenGigE0/1/1/8 TenGigE0/1/1/9 TenGigE0/1/1/10 TenGigE0/1/1/11
Resource admission (without profile) Disk space : 10000MB Memory : 32768MB CPU : 100% system CPU VCPUs : 60 (sockets:3 cores:10 threads:2)
RP/0/RSP1/CPU0:SERVICE_PE2_1# |
33. show cgn nat44 <> statistics
This is a very important CLI related to NAT44. A sample output of the CLI is shown below.
| Sample "show cgn nat44 <> statistics" CLI Output |
|---|
|
RP/0/RSP0/CPU0:#Show cgn nat44 nat statistics Fri Sep 16 23:12:40.018 UTCStatistics summary of NAT44 instance: 'nat' Number of active translations: 92400 Number of sessions: 30706 Translations create rate: 542Translations delete rate: 1206 Inside to outside forward rate: 147827 Outside to inside forward rate: 204847Inside to outside drops port limit exceeded: 10167470 Inside to outside drops system limit reached: 0Inside to outside drops resource depletion: 0 No translation entry drops: 9453431PPTP active tunnels: 3 PPTP active channels: 2PPTP ctrl message drops: 1246 Number of subscribers: 0Drops due to session db limit exceeded: 0 Pool address totally free: 499Pool address used: 1549 Pool address usage: ------------------------------------------------- External Address Ports Used 200.0.9.2 16 200.0.9.8 57 200.0.9.12 36 200.0.9.16 78 200.0.9.20 52 200.0.9.24 65 200.0.10.1 2 200.0.10.24 1 200.0.10.26 1 ------------------------------------------------- |
Following table explains the impotant fields from the above CLI and how it can be used for validation.
Please note that the values displayed by the CLI is valid at that instant for that particular VSM card. It may change at a later point of time.
| Field Name | Description | Additional Comments for Validation |
|---|---|---|
Number of active translations |
Number of NAT DB (Static + Dynamic) Entries | Monitoring this over a period of time will provide the NAT44 translation scale used in the VSM card. |
Number of sessions |
Number of Session DB (Static + Dynamic) Entries |
Monitoring this over a period of time will provide the NAT44 session scale used in the VSM card. |
Translations create rate |
Number of NAT44 translations created in last 1 second |
Monitoring this over a period of time will provide the NAT44 session setup rate on the VSM card. |
Translations delete rate |
Number of NAT44 translations deleted in last 1 second |
Monitoring this over a period of time will provide the NAT44 session teardown rate on the VSM card. |
Inside to outside forward rate |
Number of packets gone through NAT44 translation in I2O direction in last 1 second |
Monitoring this over a period of time will provide the NAT44 packet processing rate on VSM card (PPS) in I2O direction |
Outside to inside forward rate |
Number of packets gone through NAT44 translation in O2I direction in last 1 second |
Monitoring this over a period of time will provide the NAT44 packet processing rate on VSM card (PPS) in O2I direction |
Inside to outside drops port limit exceeded |
Number of I2O packets dropped because no NAT entries cannot be created for the specific users which has reached port limit. | If you have configured port limit value too less, you may hit this errors very often. You may need to consider to increase the port limit configuration in that case. |
Inside to outside drops system limit reached |
Number of I2O packets dropped because NAT DB or User DB is full. |
In case you are hitting this very often, you may need to check if you're hitting the scale limit and if so, you may need to go for another VSM card. |
Inside to outside drops resource depletion |
Number of I2O packets dropped because Layer 4 port could not be allocated. |
|
No translation entry drops |
Number of O2I packets dropped because there was no NAT entry existing. |
|
Number of subscribers |
Number of NAT Users | |
Drops due to session db limit exceeded |
Number of I2O packets dropped because Session DB is full. |
34. show cgn nat44 <> inside-translation
This command is helpful in seeing the list of all Outside / Public IP address + Port mapping for a specific Inside / Private IP address (and a Port range).
Following is a sample output of the command.
| Sample "show cgn nat44 <> inside-translation" CLI Output |
|---|
|
RP/0/RSP0/CPU0:McKinely#show cgn nat44 nat1 inside-translation protocol udp inside-vrf red inside-address 10.2.5.134 port start 1 end 4580 Wed May 15 14:25:09.713 UTC Inside-translation details --------------------------- NAT44 instance : nat1 Inside-VRF : red -------------------------------------------------------------------------------------------- Outside Protocol Inside Outside Translation Inside Outside Address Source Source Type to to Port Port Outside Inside Packets Packets -------------------------------------------------------------------------------------------- 100.200.2.75 udp 4500 65024 dynamic 9236 2213 100.200.2.75 udp 4501 65153 dynamic 2236 0 100.200.2.75 udp 4502 65152 dynamic 4232 1218 100.200.2.75 udp 4503 65155 dynamic 2236 7128 100.200.2.75 udp 4504 65154 dynamic 2235 1821 100.200.2.75 udp 4505 65157 dynamic 5236 3129 100.200.2.75 udp 4506 65156 dynamic 2238 8172 100.200.2.75 udp 4507 65159 dynamic 7238 2189 100.200.2.75 udp 4508 65158 dynamic 2236 3119 ... 100.200.2.75 udp 4576 65226 dynamic 1239 2178 100.200.2.75 udp 4577 65229 dynamic 8235 4171 100.200.2.75 udp 4578 65228 dynamic 2235 0 100.200.2.75 udp 4579 65231 dynamic 4230 4127 100.200.2.75 udp 4580 65230 dynamic 2235 0 RP/0/RSP0/CPU0:# |
Above table shows all Outside IP (100.200.2.75) and Port combination for Inside IP (10.2.5.134) and Port Range (1 through 4580).
NOTE:
- As one Inside address can only map to one Outside address, there are not multiple Outside addresses in 1st column.
- The number of entries in this table should not exceed Port Limit value.
35. show cgn nat44 <> outside-translation
This command is helpful in seeing the list of all Inside / Private IP address + Port mapping for a specific Outside / Public IP address (and a Port range).
Following is a sample output of the command.
| Sample "show cgn nat44 <> outside-translation" CLI Output |
|---|
|
RP/0/RSP0/CPU0:McKinely#show cgn nat44 nat1 outside-translation protocol udp outside-address 100.200.2.75 port start 1 end 65535 Wed May 15 14:17:44.640 UTC Outside-translation details --------------------------- NAT44 instance : nat1 Outside-VRF : default -------------------------------------------------------------------------------------------- Inside Protocol Outside Inside Translation Inside Outside Address Destination Destination Type to to Port Port Outside Inside Packets Packets -------------------------------------------------------------------------------------------- 10.2.5.134 udp 65024 4500 dynamic 4236 1216 10.2.5.134 udp 65025 4885 dynamic 9233 5161 10.2.5.134 udp 65026 4886 dynamic 4244 3491 10.2.5.134 udp 65027 4887 dynamic 1281 6018 10.2.5.134 udp 65028 4888 dynamic 2237 4187 ... 10.2.5.142 udp 65532 4882 dynamic 6261 3178 10.2.5.142 udp 65533 4881 dynamic 7282 0 10.2.5.142 udp 65534 4884 dynamic 1211 4178 10.2.5.143 udp 65535 4883 dynamic 1261 5189 RP/0/RSP0/CPU0:# |
Above table shows all Inside IPs (10.2.5.134, 10.2.5.142) and Port combination for Inside IP (100.200.2.75) and Port Range (1 through 65535). In this case, there are multiple Inside IP addresses are mapped to one Public IP address.
Monitoring CGN Using SNMP
The attached CGN_MIB_Parameters.xlsx sheet lists the parameters supported in the CGN implementation on VSM/ISM.
- Go through this Deployment Guide to clearly understand
- how different feature works
- what parameters are configurable and need to be considered for specific deployment
- what are the different deployment use cases.
- Go through "CGv6 on VSM: Features Supported Across IOS-XR Release" page to exactly know from which release specific features that you're interested in are supported. This will help you in selecting the right IOS-XR release.
- Select the configuration parameter values wisely, considering
- pros and cons,
- best-case and worst-case scenarios
- side effects
- Draw network diagram for deployment use-case including interface names (with VRF and IP address/subnet) and review for correctness.
- Try to find out what type of application traffic (VPN, Games, SIP, Video, etc.) may undergo NAT44 and whether there could be issues or not (not all applications are NAT friendly)
- If possible, try it in a lab setup, before actual deployment
- Estimate traffic throughput and nature of it (burstiness, average, etc.), scale of sessions/users and accordingly use correct number of VSM cards and related configuration.
- If possible, deploy in phases. First, send selected traffic (you can use ABF) through VSM and see if there are any issues. If not, you can send more and more traffic through VSM.
Related Information
- CGv6 on VSM: Features Supported Across IOS-XR Releases
- CGv6 on ISM: Features Supported Across IOS-XR Releases
- CGv6 on ISM: CGN / NAT44 Deployment Guide
- ASR9K Configuration Guides
- ASR9K Command Reference Guides
- ASR9K BNG Deployment Guide
- IANA Service Name and Transport Protocol Port Port Number Registry
- Configuration Example: MPLS VPN on IOS-XR
- Cisco ASR9000 S/w License Operations White Paper
- 0 -
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I know you worte down:
"...
- TCP - It has two timeouts.
- Initial Timeout - It kicks in before the connection moves into Active state. Default: 120 sec.
- Active Timeout - It kicks in when the connection is in Active state. Default: 30 Minutes.
..."
Just a minor typo, it should have read "seconds" instead of "minutes"
RP/0/RP0/CPU0:ASR9912(config-cgn)# service-type nat44 nat1
RP/0/RP0/CPU0:ASR9912(config-cgn-nat44)#protocol tcp
RP/0/RP0/CPU0:ASR9912(config-cgn-proto)#session active timeout ?
<1-65535> Timeout in seconds
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
In section about a ACL-based Forwarding (ABF), in table is configuration
ipv4 access-list nat44_abf
! Divert to ServiceApp 1
10 permit ipv4 10.0.100.0/24 any nexthop1 vrf ivrf1 ipv4 5.1.1.2
! Divert to ServiceApp 3
20 permit ipv4 10.0.200.0/24 any nexthop1 vrf ivrf2 ipv4 6.1.1.2
100 permit ipv4 any any
and later for ServiceApp3 there is a vrf named ivrf3.
interface ServiceApp3
vrf ivrf3
I am interested if that interface ServiceApp3 should be in ivrf2 like in command in ACL for nexthop1?
I presume that IP address 6.1.1.2 (from ACL) is some other end of P2P link of a ServiceApp3 interface?
And one other question about VSMs, if I put a two VSM in one ASR9k chassis, with a full utillization of VSM,
which ServiceApp ports should be there?
ServiceApp1-2, ServiceApp3-4 on VSM1 and ServiceApp5-6, ServiceApp7-8 on VSM2?
What about an inside VRFs in that redundant scenario?
ivrf1 - ServiceApp1, ServiceApp3
ivrf2 - ServiceApp5, ServiceApp7
OR
ivrf1 - ServiceApp1
ivrf2 - ServiceApp3
ivrf3 - ServiceApp5
ivrf4 - ServiceApp7
BR,
Antonio
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Regarding the logical partitioning section: it is my understanding that for me to use full VSM throughput, I would have to configure, at least, two inside serviceapp interfaces (plus 2 corresponding outside serviceapps). Is this correct? What would be the expected behavior if I just configure SA1/SA2? Would only half the throughput be available to me?
The reason I ask is that I currently have a setup with single in/out serviceapps and yet the VSM is processing around 30G in peak hours (2G in2out, 28G out2in), which is about what I expected full throughput to be around.
Can you please clarify this section (with an example if possible)?
Thanks!
c.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes, you are right, per guide if you have only one pair in input/output ServiceApp interfaces it should be some lower performance.
You said that it achieves about 30G throughput, what about a number of sessions?
Does it reach a maximum sessions per license, Nx 5 millions of sessions?
What is MTU of packets flowing through?
Just curious, did you put SA1 and SA2 interfaces in the same VRF or different ones?
BR,
Antonio
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
MTU for serviceapps is 9216, but since it’s a DOCSIS access network, I don’t expect anything above 1500.
SA1 is in default vrf, SA2 is in a different VRF. That’s about it.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Carlos,
One thing which is maybe weird, if you put SA1 in default vrf, how did you configure a NAT in this portion, what is your inside-vrf parameter (here in example is inside-vrf ivrf1):
service cgn cgn1 service-location preferred-active 0/1/CPU0 service-type nat44 nat1 inside-vrf ivrf1 map outside-vrf ovrf1 address-pool 100.1.1.0/24
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
service cgn CGN1
service-location preferred-active 0/7/CPU0
service-type nat44 NAT44
portlimit 2048
inside-vrf XXXXXXX
map address-pool X.X.X.X/YY
I’d just like to confirm that since I only have one vrf configured, I’m very close to the maximum performance allowed with only one vrf. I’m assuming one vrf = ½ total throughput (half of 60G)
Can anyone confirm this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Carlos,
Did you maybe get a successful test about your confusion if one vrf = ½ total throughput (half of 60G)?
BR,
Antonio
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Guys,
I have some issues with VSM configurations. My previous version was 5.3.4 where i had successfully configured vsm and other related configs. But later it was upgraded to 6.2.3 but then Nat was not in use.
Now on the same version i.e 6.2.3, I am trying to configure Nat configurations and i am unable to add "service cgn cgnat service-type nat44" in ServiceApp2.
interface ServiceApp1
vrf wifivrf
ipv4 address 10.66.66.1 255.255.255.252
service cgn cgnat service-type nat44
!
interface ServiceApp2
ipv4 address 10.77.77.1 255.255.255.252
!
interface ServiceInfra1
ipv4 address 10.166.166.1 255.255.255.0
service-location 0/1/CPU0
!
RP/0/RSP0/CPU0:gw-jwl-nettv-04(config)#interface ServiceApp2
RP/0/RSP0/CPU0:gw-jwl-nettv-04(config-if)# service cgn cgnat service-type nat44
RP/0/RSP0/CPU0:gw-jwl-nettv-04(config-if)#commit
Fri Sep 13 11:33:02.128 Kathmandu
% Failed to commit one or more configuration items during a pseudo-atomic operation. All changes made have been reverted. Please issue 'show configuration failed [inheritance]' from this session to view the errors
RP/0/RSP0/CPU0:gw-jwl-nettv-04(config-if)#sho configuration failed
Fri Sep 13 11:33:05.804 Kathmandu
!! SEMANTIC ERRORS: This configuration was rejected by
!! the system due to semantic errors. The individual
!! errors with each failed configuration command can be
!! found below.
interface ServiceApp2
service cgn cgnat service-type nat44
!!% 'SESVI' detected the 'warning' condition 'An invalid interface id was specified'
!
end
Please suggest why this error was noticed.
- « Previous
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: