- Cisco Community
- Technology and Support
- Service Providers
- Service Providers Knowledge Base
- ASR9000/XR Flexible VLAN matching, EVC, VLAN-Tag rewriting, IRB/BVI and defining L2 services
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-07-2011 07:18 AM
Introduction
In this article we'll be discussing the EVC (Ethernet Virtual Circuit) infrastructure that the ASR9000 and IOS-XR use to define L2 services.
You'll find in this article how packets coming in on an interface are being matched against an EFP (Ethernet Flow Point), how to manipulate the vlan tags and use them in XCONNECT (VPWS) or Bridging (eg VPLS) scenarios with the optional L3 endpoint to provide IRB (Integrated Route Bridging)
Core Issue
The way that IOS-XR handles EVC's is a bit different then the way that IOS handles it when for instance using the 7600.
When starting with IOS-XR and the ASR9000 there are a few things that you will want to be aware of when defining L2 services.
A couple of the key differences are:
- XR does have the concept of a trunk interface
- therefore XR cannot do vlan pruning
- XR does not strip vlan tags by default.
- XR does not have the concept of an "interface VLAN" a.k.a. SVI's (Switch Virtual Interface), instead it uses a BVI (Bridge Virtual Interface) that can be inserted into the bridge-domain.
Flexible VLAN matching
How the ASR9000 matches traffic to an EFP
TAG rewriting
how to modify the vlan headers and how that works
Defining L2 services
and a comparison with IOS
Providing L3 services in L2VPN
using IRB/BVI interfaces
Resolution
In order to define an L2 service, we need to match traffic to a particular interface. In IOS-XR and the ASR9000 we use the Ethernet Flow Point (EFP) to match this traffic. An EFP is effectively a subinterface of a physical interface with the keyword "l2transport" attached to it. This l2transport defines that we are going to use this (sub) interface for L2 Services. We can match L2 and L3 interfaces on a single physical port:
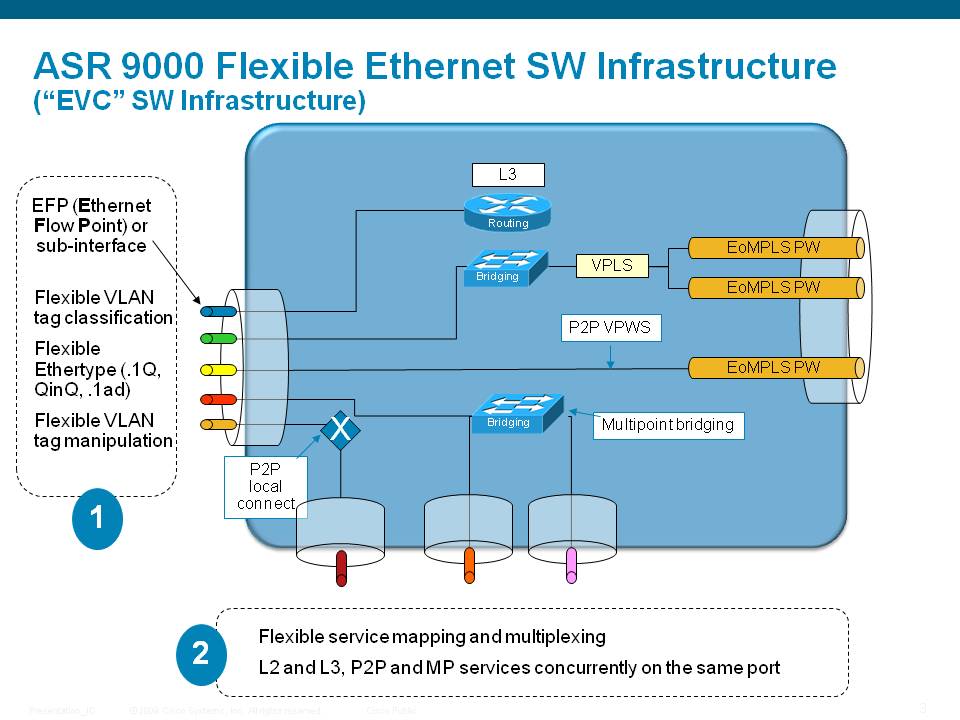
Flexible VLAN matching
When traffic is coming in on a port, we use the TCAM to find out which particular subinterface this traffic matches on. With that in mind there are a couple of rules as to how traffic is matched.
An EFP is defined as follows:
RP/0/RSP0/CPU0:asr(config)#int gig 0/0/0/4.100 l2transport
RP/0/RSP0/CPU0:asr(config-subif)#encapsulation ?
default Packets unmatched by other service instances
If a particular packet is not matching any other specific EFP on this physical port, this "Default" will capture all unmatched traffic.
dot1ad IEEE 802.1ad VLAN-tagged packets
dot1q IEEE 802.1Q VLAN-tagged packets
untagged Packets with no explicit VLAN tag
If there is no vlan tag on the packet, the "untagged" EFP will capture this traffic, this is effectively plain ethernet and useful for instance to capture
BPDU's for instance.
When we are going to match on say dot1q encapsulated traffic we have a variaty of how we can match vlan tagged traffic (see also foot note below in the "Related Information" section on the ethertypes used).
RP/0/RSP1/CPU0:A9K-BOTTOM(config-subif)#encapsulation dot1q ?
<1-4094> Start of VLAN range
<1-4094> Single VLAN id
any Match any VLAN id
priority-tagged IEEE 802.1ad priority-tagged packets
At the first level of dot1q classification we can select a vlan, vlan-range or any. These are obvious. The option "Priority tagged" allows us to capture vlan encapped traffic that is with a vlan id of 0.
RP/0/RSP1/CPU0:A9K-BOTTOM(config-subif)#encapsulation dot1q 100 ?
comma comma
exact Do not allow further inner tags
ingress Perform MAC-based matching
second-dot1q IEEE 802.1Q VLAN-tagged packets
Here is an important concept that is to be highlighted. You see the "word" exact" here. What that means is, in the absence of the keyword exact, if the outter vlan header is "100" in this example, this EFP is matched. so that means that also qinq frames that are of the 100 outter and 200 inner kind (if there is no specific EFP for the qiq combo 100/200 available) will match this EFP.
Just a few examples:
encapsulation dot1q 100: will match any number of vlan headers as long as the outter vlan id is 100
encapsulation dot1q 100 second any: will match any qiq frame where the outter vlan is 100
encapsulation dot1q 100 second 200: will match vlan tagged packets whereby the outter is 100, the inner is 200 and also a potential vlan combo of 100/200/300
encapsulation dot1q 100 second 200 exact: will match vlan tagged packets whereby the outter is 100, the inner is 200 and no other vlan tags are on the packet then these 2 specified.
Normally "longest match" will win, or better put, the most specific match will win.
ASR9000 doesn't support best match for VLAN ranges, but we do support best match if the "any" keyword is used.
So the configuration :
EFP 1 VLAN: S-VLAN=1000, C-VLAN_range=1-4095
EFP 2 VLAN= S-VLAN=1000, C-VLAN=2000
isn't allowed because the more specific C-vlan is part of the range. The parser will reject this config upon commit.
The following options A and B, achieving the same, are allowed :
A)
EFP 1) VLAN: S-VLAN=1000, C-VLAN_range=1-1999,2001-4095
EFP 2) VLAN= S-VLAN=1000, C-VLAN=2000
B)
EFP 1) VLAN: S-VLAN=1000, C-VLAN=any
EFP 2) VLAN= S-VLAN=1000, C-VLAN=2000,
VLAN TAG rewriting
The ASR9000/XR is capable of doing many translations on vlan to a packet.
The behavior is always symmetric (though this keyword is to be provided as part of that config command). The symmetry means that if we pop a tag on ingress, we push it back on egress.
the following rewrites are possible:
RP/0/RSP0/CPU0:A9K(config)#int gig 0/0/0/4.100 l2transport
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag ?
pop Remove one or more tags
push Push one or more tags
translate Replace tags with other tags
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag pop ?
1 Remove outer tag only
2 Remove two outermost tags
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag push ?
dot1ad Push a Dot1ad tag (ethertype 88a8)
dot1q Push a Dot1Q tag (ethertype 8100 by default, or 9100/9200 is specied on the main interface for the outter most tag)
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag push dot1q 100 ?
second-dot1q Push another Dot1Q tag
symmetric All rewrites must be symmetric
RP/0/RSP0/CPU0:A9K(config-subif)#rewrite ingress tag translate ?
1-to-1 Replace the outermost tag with another tag
1-to-2 Replace the outermost tag with two tags
2-to-1 Replace the outermost two tags with one tag
2-to-2 Replace the outermost two tags with two other tags
If you want to make a cross connect or bridge between two EFP's where one EFP is vlan 100 and the other EFP is vlan 200,
you need to make sure you pop the tags so that the vlan 100 is removed from the packet so it, by means of symmetry, will get vlan 200 on the egress
of the other EFP.
L2VPN configuration examples and comparison to 7600
The following picture highlights how to create L2 services on the ASR9000.
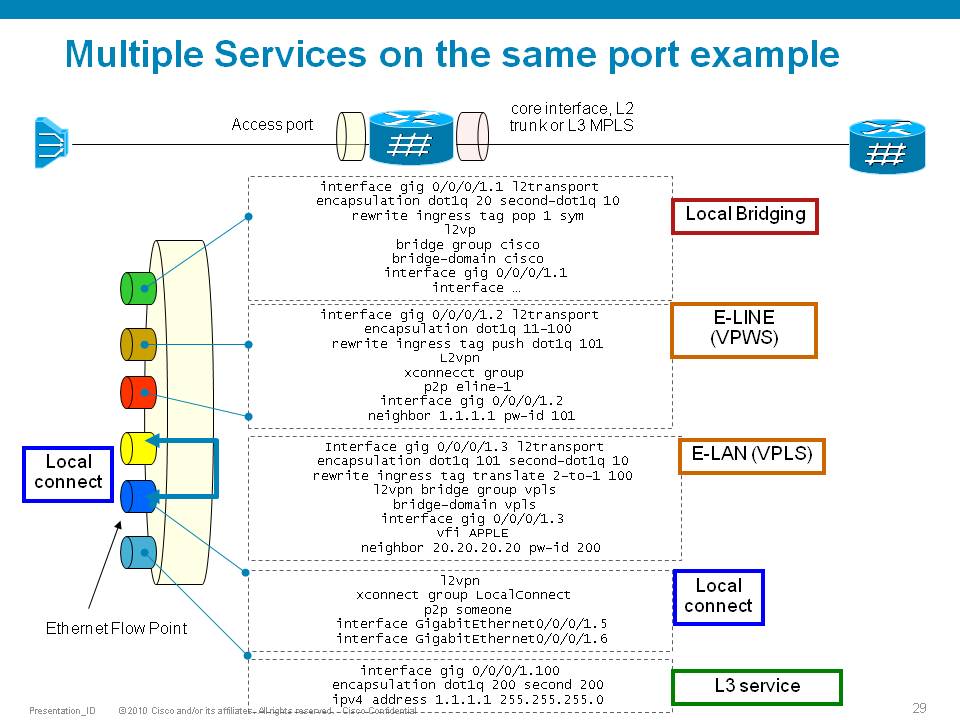
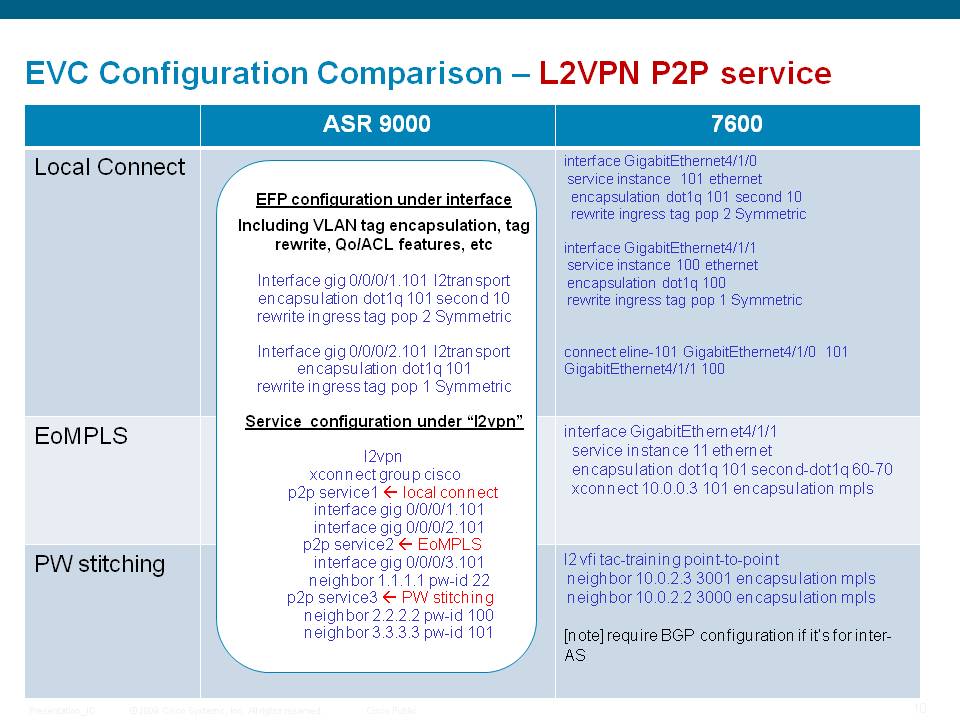
Using IRB/BVI
To provide L3 services in a bridge-domain, you can add a routed interface to the bridge domain.
What is important here is that the BVI is not vlan tagged. So in order for the EFP's to talk to the BVI, we need to pop ALL Tags on ingress!!
This means that frames with more then 2 tags cannot be natively using the BVI, unless we do some workarounds such as loopback cables to
pop more tags.
interface BVI5
ipv4 address 31.1.1.1 255.255.255.0
mac-address 0.4343.3434
! when creating the bvi verify the show int bvi to see if the mac address is correctly programmed, these macs are coming from the backplane mac table, ! if we ran out because of so many bundle interfaces etc, you may need to provide a mac manually.
interface TenGigE0/7/0/3.100 l2transport
encapsulation dot1q 100
rewrite ingress tag pop 1 symmetric
l2vpn
bridge group testing
bridge-domain testing
interface TenGigE0/7/0/3.100
!
interface GigabitEthernet0/1/0/14
!
routed interface BVI5
!
Related Information
Dot1q, Dot1ad and configuring "dot1q tunneling ethertype on the physical interface:
Xander Thuijs, CCIE #6775
Sr. Tech Lead ASR9000
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi TDA,
encap dot1ad X will match ANY frame whose only or outer vlan tag is X.
unless you use the word "exact" then it wants to see a single tagged frame only.
encap dot1ad X second any will match any dual tagged frame whereby the outer is X.
what I understand from your requirement you could best do with the first statement so you capture both single and dual tagged frames that are outer X.
regards
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
one addition:
the encap dot1q statement on the tengig subinterface using any can't be used in conjuction with BVI. there is no state maintenance on the "any"/inner vlan, so for BVI will need to define the actual qiq combination.
regards
xander
encapsulation dot1q 300 second-dot1q any
rewrite ingress tag pop 1 symmetric - See more at: https://supportforums.cisco.com/document/59741/asr9000xr-flexible-vlan-matching-evc-vlan-tag-rewriting-irbbvi-and-defining-l2?page=1#comment-10485651
encapsulation dot1q 300 second-dot1q any
rewrite ingress tag pop 1 symmetric - See more at: https://supportforums.cisco.com/document/59741/asr9000xr-flexible-vlan-matching-evc-vlan-tag-rewriting-irbbvi-and-defining-l2?page=1#comment-10485651
encapsulation dot1q 300 second-dot1q any
rewrite ingress tag pop 1 symmetric - See more at: https://supportforums.cisco.com/document/59741/asr9000xr-flexible-vlan-matching-evc-vlan-tag-rewriting-irbbvi-and-defining-l2?page=1#comment-10485651
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Alexander, Good Morning,
Here's is the backgroud what I am trying to achieve.
My project and requirement to run Q-in-Q using EVPL and EPL Circuits:
300+ Customer Sites to design for Q-in-Q.
The national providers are saying that for each site there will be a Separate Outer VLAN so that means for 300 sites the INNER VLANS remain the same (5 VLANS 601-605) but for OUTER Vlan's there will be 300 vlans as Outer to make each
site dintinguish and seperate.
We are also wholsale Service Provider so the Circuit and topology looks like this:
Customer Site: (UNI-Trunk with 5 vlans 802.1Q) ----> Termination END (My Data Center) ENNI Circuit 10GB multiple links (ENNI - EVPL and EPL Circuits)
I should be able to strip off the Outer tags for each site 300 sites and to trunk the Inner VLAN's (601-605) that is directly connected to Nexus 7010 as etherchannel 40GB throughput.
I tried this configuration as per your document and so far it's my understanding If I am missing some configuration please advice.
Thanks,
Sal
This confiuration is represting for one site only so I belive it should be same for rest of the sites with there own BVI's/Subnets and etc....
300 is the outer VLAN provided by the National Service provider and it will be in sequence for other sites like 301, 302 and so on.
interface TenGigE0/0/2/1
mtu 1596
load-interval 30
transceiver permit pid all
!
interface TenGigE0/0/2/1.300 l2transport
encapsulation dot1q 300 second-dot1q any
rewrite ingress tag pop 1 symmetric
!
interface TenGigE0/0/2/1.780 l2transport
encapsulation dot1q 780
rewrite ingress tag pop 1 symmetric
!
interface TenGigE0/0/2/1.781 l2transport
encapsulation dot1q 781
rewrite ingress tag pop 1 symmetric
!
!
interface TenGigE0/0/2/1.782 l2transport
encapsulation dot1q 782
rewrite ingress tag pop 1 symmetric
!
!
interface TenGigE0/0/2/1.783 l2transport
encapsulation dot1q 783
rewrite ingress tag pop 1 symmetric
!
!
interface TenGigE0/0/2/1.784 l2transport
encapsulation dot1q 784
rewrite ingress tag pop 1 symmetric
!
interface BVI780
ipv4 address 192.168.1.100 255.255.255.0
!
interface BVI781
ipv4 address 192.168.2.100 255.255.255.0
!
interface BVI782
ipv4 address 192.168.3.100 255.255.255.0
!
interface BVI783
ipv4 address 192.168.4.100 255.255.255.0
!
interface BVI784
ipv4 address 192.168.5.100 255.255.255.0
!
l2vpn
bridge group F780
bridge-domain F780
interface TenGigE0/0/2/1.780
!
routed interface BVI780
!
!
bridge group F781
bridge-domain F781
interface TenGigE0/0/2/1.781
!
routed interface BVI781
!
!
bridge group F782
bridge-domain F782
interface TenGigE0/0/2/1.782
!
routed interface BVI782
!
!
bridge group F783
bridge-domain F783
interface TenGigE0/0/2/1.783
!
routed interface BVI783
!
!
bridge group F784
bridge-domain F784
interface TenGigE0/0/2/1.784
!
routed interface BVI784
!
!
!
end
RP/0/RSP0/CPU0:EDGE2.151#
RP/0/RSP0/CPU0:EDGE2.151#ping 192.168.1.100
Fri May 8 08:01:25.805 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.100, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/42/207 ms
RP/0/RSP0/CPU0:EDGE2.151#ping 192.168.2.100
Fri May 8 08:01:33.311 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.100, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
RP/0/RSP0/CPU0:EDGE2.151#ping 192.168.3.100
Fri May 8 08:01:39.527 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.3.100, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
RP/0/RSP0/CPU0:EDGE2.151#ping 192.168.4.100
Fri May 8 08:01:43.536 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.4.100, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
RP/0/RSP0/CPU0:EDGE2.151#ping 192.168.5.100
Fri May 8 08:01:47.840 UTC
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.5.100, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
RP/0/RSP0/CPU0:EDGE2.151#
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Does it look rite Alexender would it work ?
interface TenGigE0/0/2/1.300 l2transport
encapsulation dot1ad 300 exact
rewrite ingress tag pop 1 symmetric
!
Regards,
Sal
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hey sal, that config would match only single tagged dot1ad frames with value 300.
so yeah if the frames match that, it will work just fine, and you could pull in other qiq combo's with their designated EFP's, but they have to be explicit, meaning:
EFP-1:
encap dot1ad 300 second 10
EFP-2:
encap dot1ad 300 second 20
efp being a subinterface with l2transport keyword.
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Alexender,
Last question on this and I hope I will be good now. Your last reply was:
EFP-1:
encap dot1ad 300 second 10
EFP-2:
encap dot1ad 300 second 20
efp being a subinterface with l2transport keyword.
It's taking these two configurations only just want to validate with you which one is correct way to do it if i do
encap dot1ad 300 (the second ) option is not available so i believe from the two configs below which one is the correct.
interface TenGigE0/0/2/1.601 l2transport
encapsulation dot1ad 300 dot1q 601
OR
interface TenGigE0/0/2/1.601 l2transport
encapsulation dot1q 300 second-dot1q 601
Thanks and Best Regards,
Sal
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hey sal, this:
interface TenGigE0/0/2/1.601 l2transport
encapsulation dot1q 300 second-dot1q 601
that is the correct syntax.
my bad, my brain doesnt run XR parser, or well close to, and I typed the commands out of my head, but I could have been more detailed, apologies!
cheers
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thankd Alexander it worked.
have a great weekend my friend.
Best Regards,
Sal
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander,
Great document, I have a problem that keeps happening and I wonder if you saw something like it before, I have a number of L2vpn circuits throughout my network, the circuits start and terminate on ASR9K platforms, some circuits go down from time to time because the AC changes state from UP to unresolved for no obvious reason, I usually restore the service by deleting the interface from the bridge domain and the global config mode and restoring them again, if that doesn't work, I have to do a redundancy switchover to bring its status to up again, have you seen a problem like this before ? is it related to software license ? (I couldn't find a similar problem using cisco Bug tracking tool)
one ASR that keeps showing this is running SW 5.1.1 with the following RSP/LCs:
0/RSP0/CPU0 A9K-RSP440-TR(Standby) IOS XR RUN PWR,NSHUT,MON
0/RSP1/CPU0 A9K-RSP440-TR(Active) IOS XR RUN PWR,NSHUT,MON
0/0/CPU0 A9K-2T20GE-B IOS XR RUN PWR,NSHUT,MON
0/3/CPU0 A9K-8T-L IOS XR RUN PWR,NSHUT,MON
0/5/CPU0 A9K-24x10GE-TR IOS XR RUN PWR,NSHUT,MON
0/6/CPU0 A9K-24x10GE-TR IOS XR RUN PWR,NSHUT,MON
Thanks again,
Regards,
Sarmed
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi sarmed,
thank you!! :)
that particular issue I have not seen before, other then an AC being unresolved when for instance it doesnt exist or is not of the l2transport kind. Possibly the l2vpn trace may hold some detail for that interface explaining what the event was that led to it being unresolved. Based on that info/detail we can suggest maybe the right course of action..
I dont want to say oh hey upgrade to 513, the only point here is that 513 is a hardened maintenance release which is definitely a good one to go with, but I can't guarantee that this issue wouldnt exist there.
any case lets look at the l2vpn trace first.
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Xander
Real great explanation.
I cannot try this configuration, because I have a 'silly' problem with ambigious vlan configuration.
So I try to locate the problem using using basic static IPoE configuration.
So when i configure specifically outer/inner vlan, each side can ping succesfully :
encapsulation dot1q 301 second-dot1q 10
But when I try to do same with ambigious command, all ping fail from each side:
encapsulation ambiguous dot1q 301 second-dot1q any
or
encapsulation ambiguous dot1q 301 second-dot1q 10-50
Can you explain that ?
My release is 5.1.3, perhaps old release ?
Thanks for your feedback.
Jean
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi jean,
if you have static bng subscribers (so set up without a trigger) then you will want a fixed qiq combo.
this because when the static sub is created or any subscr for that matter, then a full qiq combo needs to be known in order to know what l2 encap to use on the egress direction.
so while you can use amb vlans for dhcp triggered or packet triggered subscr, for the static you need to have a fixed combo.
cheers!
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander
so this configuration should work:
interface GigabitEthernet0/0/1/3.301
description >>> QinQ DHCP
ipv4 point-to-point
ipv4 unnumbered Loopback1
ipv6 enable
service-policy type control subscriber IPOE_PM
ipsubscriber ipv4 l2-connected
initiator dhcp
initiator unclassified-source
!
ipsubscriber ipv6 l2-connected
initiator dhcp
!
encapsulation ambiguous dot1q 301 second-dot1q any
!
jean
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hey jean, yeah with that config you'll be able to take a dhcp v4 discover or a v6 dhcp solicit on any outer Q of 301 with any inner to create a subscriber session.
this is not what "we" call a static session but a dhcp triggered subscriber. just to get the termnilology straight :)
when you set this up and if you have an issue, for visibility purposes (so that more people see this/can contribute) it might be a good idea to raise a new discussion on the xr os forum so you can get the amplified result of everyone that looks at this forum.
(since it this scenario is beyond the flex vlan scope possibly and to have more eyes from this besides the people watching activity on this doc).
cheers
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander,
You've made a point a couple of times in this thread that the BNG function can actually use ambigious VLAN since the DHCP process is snooping the actual VLANs to be able to build the egress packets. I see this is working with something like "encap ambig dot1q 2000-2001 second-dot1q any", but only with the default broadcast-flag policy of converting every client-bound DHCP package to broadcast, disregarding the actual broadcast flag of the packet.
This breaks some devices, and I would like the BNG to obey the broadcast flag with the 'broadcast-flag policy check' command, this however breaks the DHCP replies with the said ambiguous VLAN config. Why is that? Since the BNG have egress VLAN info and MAC it should be able to build the egress packet for unicast, when it is able to do so for broadcast?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

