- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Remote Access VPN - Unable to Access LAN / Inside Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Remote Access VPN - Unable to Access LAN / Inside Network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2013 04:55 AM - edited 02-21-2020 06:36 PM
Hi,
I am facing a problem with Cisco ASA remote access VPN, the remote client is connected to VPN and receiving IP address but the client is not able to ping or telnet any internal network.
I have attached running configuration for your reference. Please let me know I miss any configuartion.
FW : ASA5510
Version : 8.0
Note : Site to Site VPN is working without any issues
Thanks
Jamal
- Labels:
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2013 05:18 AM
Hi,
Can you add the following configuration
policy-map global_policy
class inspection_default
inspect icmp
It should atleast handle the ICMP Echo-Reply messages to get through the firewall automatically.
Other than that the configurations seem pretty normal. Although you have added useless lines to the NAT0 and FILTER. NAT0 only needs the line with LAN as source and RAS as destination. FILTER should only need RAS as source and LAN as destination.
Have you checked the logs related to the Telnet connections you are attempting?
Also do you have a router infront of your ASA doing public NAT for the ASAs outside interface or what kind of setup is this? Seeing that the L2L VPN peer IP address is private (or is it just changed for the purpose of the post?) I guess the ASA in this version also has "no nat-control" as default if you say that your S2S VPN is working as I cant see any NAT0 configurations for it. I can't see any default PAT rules either. (then again after configuring PAT rule it would require NAT0 for the S2S traffic)
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2013 06:37 AM
Thanks Jouni for your immediate response.
This is LAB setup used for training purpose, I tried ICMP inspect but still no luck.
Yes, there are two routers in between firewalls. It’s just for IP routing purpose NO NAT involved in routers.
Firewall ICMP debug clearly shows that the ICMP echo packets are coming from Remote client and Reply from the inside host.
ICMP echo request from outside:20.20.20.11 to inside:192.168.10.1 ID=1024 seq=2560 len=32
ICMP echo reply from inside:192.168.10.1 to outside:20.20.20.11 ID=1024 seq=2560 len=32
ICMP echo request from outside:20.20.20.11 to inside:192.168.10.1 ID=1024 seq=2816 len=32
ICMP echo reply from inside:192.168.10.1 to outside:20.20.20.11 ID=1024 seq=2816 len=32
ICMP echo request from outside:20.20.20.11 to inside:192.168.10.1 ID=1024 seq=3072 len=32
ICMP echo reply from inside:192.168.10.1 to outside:20.20.20.11 ID=1024 seq=3072 len=32
ICMP echo request from outside:20.20.20.11 to inside:192.168.10.1 ID=1024 seq=3328 len=32
ICMP echo reply from inside:192.168.10.1 to outside:20.20.20.11 ID=1024 seq=3328 len=32
undebug allICMP echo request from outside:20.20.20.11 to inside:192.168.10.1 ID=1024 seq=3584 len=32
ICMP echo reply from inside:192.168.10.1 to outside:20.20.20.11 ID=1024 seq=3584 len=32
Cisco VPN client software statistics show the packets are send/ encrypted but 0 (zero) received/ decrypted packets.
For the site to site VPN we are not using any NAT in the firewalls, I could see the packets are encrypted / decrypted in #show crypto ipsec sa command.
Thanks
Jamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2013 06:43 AM
Hi,
What is the IP address of the VPN Client user BEFORE attempting to connect to the ASA and hosts behind it with the VPN Client? (Where is the VPN Client connected regard to your setup?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2013 11:48 PM
Hi Jouni,
IP address of the remote client before connecting to VPN 100.100.100.10. Below is the setup diagram. (The remote
client behind firewall)
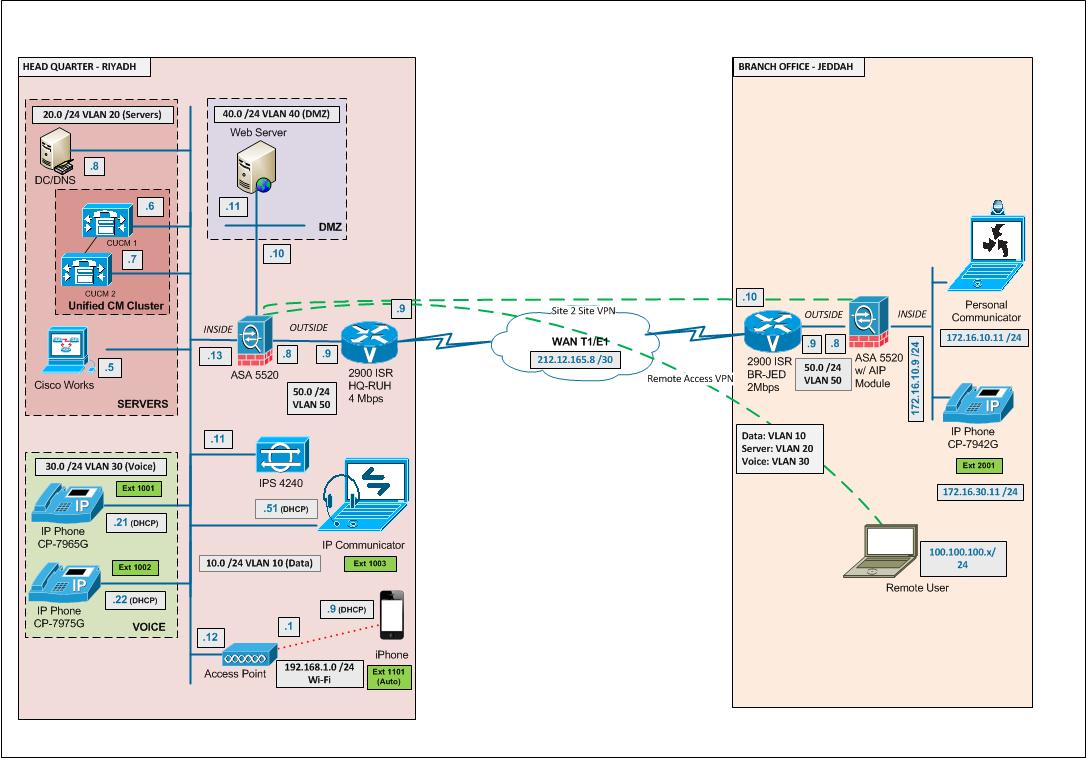
Now I moved the remote client in between router and ASA (Branch Office) and it's started working....
No idea why the remote client is not working when we place it behind ASA.
Thanks a lot for your reply, your question (Where is the VPN Client connected regard to your setup?) made me think of this.
Thanks
Jamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2013 12:53 AM
Hi,
Very nice network diagram
Are you saying that originally the VPN Client user is behind the Jeddah ASA?
If this is true wouldnt it be wiser to just use the already existing L2L VPN between these sites?
In real situation I think the VPN Client would only be needed when you are outside either Head Quarter or Jeddah Network. And since you tested it infront of the ASA and it worked there shouldnt be any problem.
Now to the reason why the VPN Client isnt working from behind the Jeddah ASA.
Can you check that the following configuration is found on the Jeddah ASA (Depending on the software level of the ASA the format of the command might change. I'm not 100% sure)
isakmp nat-traversal
To enable NAT traversal globally, check that ISAKMP is enabled (you can enable it with the isakmp enable command) in global configuration mode and then use the isakmp nat-traversal command. If you have enabled NAT traversal, you can disable it with the no form of this command.
isakmp nat-traversal natkeepalive
no isakmp nat-traversal natkeepalive
Syntax Description
Defaults
By default, NAT traversal (isakmp nat-traversal) is disabled.
Command Modes
The following table shows the modes in which you can enter the command:
Global configuration
•

—
•

—
—
Command History
Preexisting
This command was preexisting.
7.2(1)
This command was deprecated. The crypto isakmp nat-traversal command replaces it.
Usage Guidelines
Network Address Translation (NAT), including Port Address Translation (PAT), is used in many networks where IPSec is also used, but there are a number of incompatibilities that prevent IPSec packets from successfully traversing NAT devices. NAT traversal enables ESP packets to pass through one or more NAT devices.
The security appliance supports NAT traversal as described by Version 2 and Version 3 of the IETF "UDP Encapsulation of IPsec Packets" draft, available at http://www.ietf.org/html.charters/ipsec-charter.html, and NAT traversal is supported for both dynamic and static crypto maps.
This command enables NAT-T globally on the security appliance. To disable in a crypto-map entry, use the crypto map set nat-t-disable command.
Examples
The following example, entered in global configuration mode, enables ISAKMP and then enables NAT traversal with an interval of 30 seconds:
hostname(config)# isakmp enablehostname(config)# isakmp nat-traversal 30
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2013 06:14 AM
Hi Jouni,
Yes, originally the client was behind Jeddah ASA.
You are correct it’s good to use the existing VPN tunnel in real time scenario. Since it’s Lab Just setup to explain them how to build site to site and remote access VPN on ASA firewall.
I don’t see any configuration for NAT traversal (isakmp nat-traversal) in Jeddah ASA...Configuring this will fix the problem ?
Thanks
Jamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2013 06:29 AM
Hi,
To my understanding the NAT Traversal is something that might help with the VPN Client connections initiated from behind the Jeddah ASA firewall. I'm under the impression that on some software version this is enabled by default and on some softwares not.
You could try it out since the current network is only an Lab environment. So should be no problem?
After enabling the command could try again with the VPN Client and see if there is any difference.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2013 06:05 AM
Hi Jouni,
We aer in week ned off now (Thursday, Firday) I will try this next week and update you.
Thanks
Jamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2013 06:48 AM
you should exempt the network that are tunneled becasue it my enter in game the dynamic nat and modify the source.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2013 12:06 AM
Hi,
Today I moved the client back to original position (behind Jeddah Firewall) and I am able to successfully connect to VPN. No changes were made on the firewall...
I am really not sure what went wrong before, how it’s started working
Thanks
Jamal
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

