AnyConnect VPN Error - No Extended Key Usages
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2015 08:20 AM - edited 02-21-2020 08:10 PM
Hi, Everyone,
This is my first time posting here, so thanks in advance for everything you all have contributed in this forum. It gave me a great place to start working on this issue.
I'm getting a strange error when one of my users is trying to connect to via VPN with my new AD CS PKI certificates, which are using SHA 256 hashes.
CERTIFICATE_ERROR_VERIFY_ENHKEYUSAGE_NOT_FOUND
The problem is, the certificate does have the EKU extensions appropriate for the client...
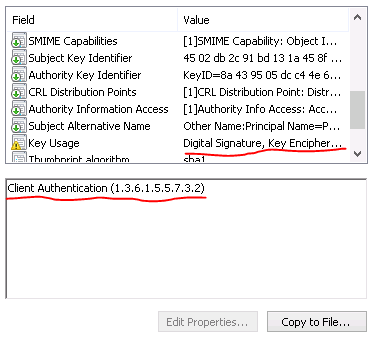
...and only this one user is experiencing the error. I connect myself with the same type of certificate and everything is fine; in fact, my entire beta group of about 20-30 users has yet to report an issue other than this.
It seems like the AnyConnect client cannot see the EKU values on the certificate for some reason.
The only thing different about this certificate from the previous versions we use in production is that it is from a new CA chain (which is loaded on the ASA as a Trust Point), and it uses a SHA256 signature, which is working for everyone else.
I can't post specific AnyConnect or ASA versions but suffice it to say they're very up-to-date, and the newer versions' release notes don't give any indication of an error of this type being fixed, unless I missed something.
Thanks!
EDIT:
I thought I would add, in case anyone saw the yellow "warning" triangle on the Key Usage field, that it indicates the certificate has that extension marked as critical, meaning if an application is checking the certificate and doesn't know how to check for EKU, it should fail validation. Obviously, AnyConnect knows how to check EKU fields since they are now required for connectivity.
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2015 12:18 PM
Resolved my own issue today. The error does nothing to describe the actual cause. The user's private key was corrupted (uncertain as to how). The certificate GUI in Windows showed it was okay, but running "certutil -store -user my" showed the error "Missing stored keyset" on the certificate in question.
The resolution was to delete the certificate and enroll for a new one, with a new key pair.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2022 03:25 AM
We have experienced similar issue recently. In our case the issue was only present with Windows 11 users.
DART logs: Description: CERTIFICATE_ERROR_VERIFY_ENHKEYUSAGE_FAILED:The certificate did not contain the required Extended Key Usages
The GUI was showing cert as active, we have not checked it via cli though.
Any suggestions how to prevent it from happening again?
Thank you.
Regards,
Daniel