- Cisco Community
- Technology and Support
- Security
- VPN
- I know this is kind of an old
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA to Juniper IPSec vpn tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2011 07:56 AM - edited 02-21-2020 05:18 PM
I have a IPSec VPN tunnel to another company where they do not have a network engineer, the are using a netscreen for their end of the tunnel. I'm having an issue where both ends can bring up the tunnel but only my end seems to be able to bring up the tunnel and then pass traffic. There are a total of 4 endpoints that ride the tunnel 2 servers on my end a 2 on their end. On my ASA logs i see the error:
<164>Apr 15 2011 13:20:05: %ASA-4-402116: IPSEC: Received an ESP packet (SPI= 0x9C48D104, sequence number= 0xBA) from 2.1.1.1 (user= 21.1.1.1) to 2.2.2.2.
The decapsulated inner packet doesn't match the negotiated policy in the SA. The packet specifies its destination as 2.2.2.2, its source as 2.1.1.1, and its protocol as 1.
The SA specifies its local proxy as 192.168.202.127/255.255.255.255/0/0 and its remote_proxy as 10.2.2.88/255.255.255.255/0/0.
(I have replaced the external addresses with made up ones, 2.1.1.1 is the remote public, 2.2.2.2 would be my end)
I have sent the techs managing the juniper there guides on how to set this up with an asa and we are still getting the error above. Any ideas? I have included 2 screen shots of what they have configured on their end
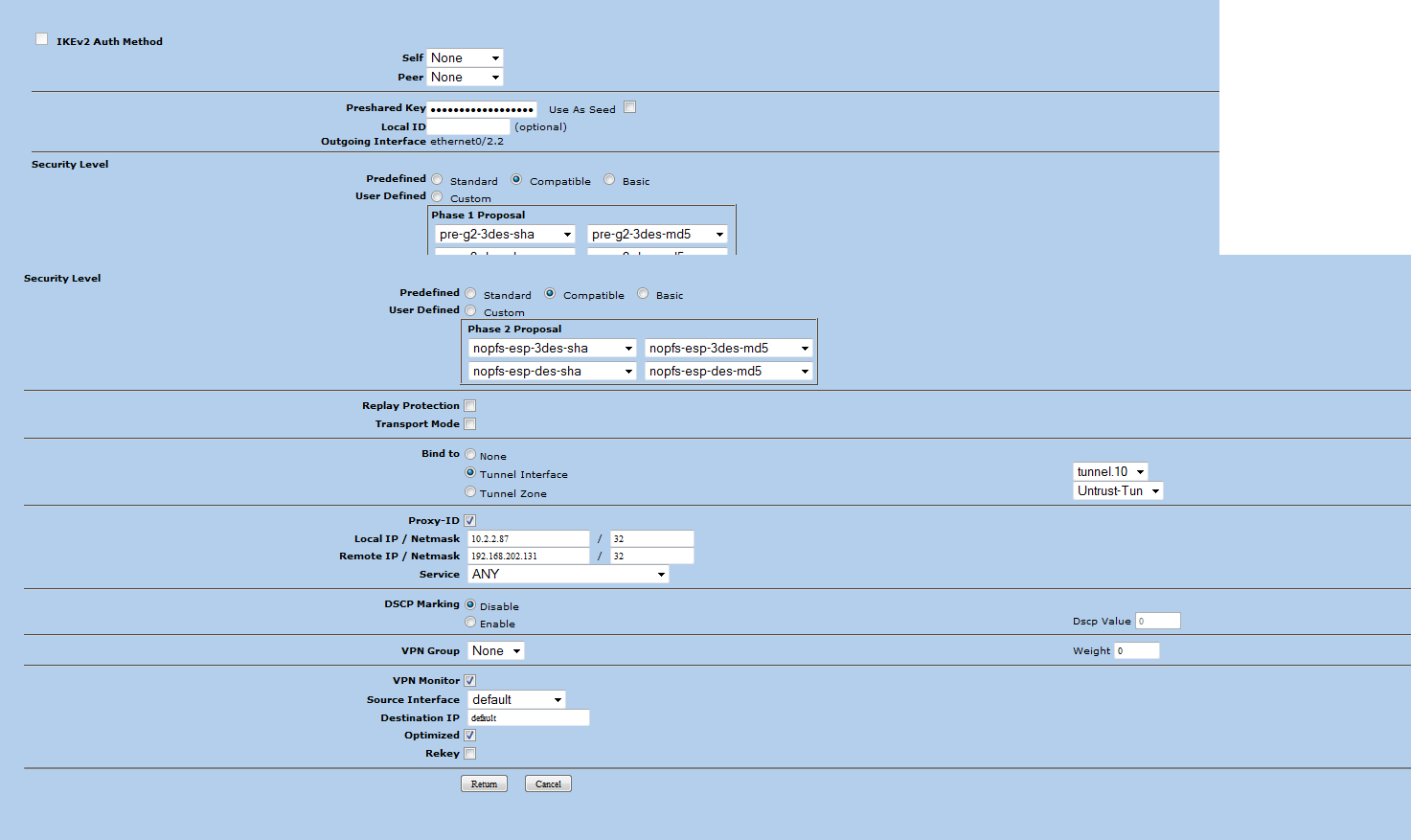
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2011 11:04 PM
I can't see the picture you posted very well.
Anyway, ASA VPNs are policy-based (that means they use Access-lists). Do you know if Juniper VPNs is also policy-based? or is it route-based? If it's route-based, then it's not compatible with Cisco ASA. If both ASA and Juniper are policy-based, then you should check if the access-lists are correct.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2015 09:07 AM
I know this is kind of an old thread, but I just wanted to note that it's quite possible to set up a Juniper route-based VPN to a Cisco ASA. I've got one set up as we speak and it's been running fine. The main thing to take into account is how proxy ID's are generated on the Juniper, and in the case of a route-based VPN you can just set them statically, ensuring they match the ACL on the Cisco side.
Other than the standard route-based VPN Juniper setup, you just have to create a separate Autokey IKE configuration on the Juniper side for each ACL that you have configured on the Cisco side. You will also need to create an additional tunnel interface for each IKE config as well as the usual static routes for each tunnel.You still need only one gateway config on the Juniper since they can be used with multiple IKE configs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2015 04:18 AM
Hello ,
can you post working config for route based vpns ( ASA --- Juniper) for reference ?
I am also in same kind of situation.
Thank you,
Dwarakanath
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2011 07:16 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide