- Cisco Community
- Technology and Support
- Security
- VPN
- Certificate Mismatch on ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Certificate Mismatch on ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 07:54 AM
Hi All,
I just received a new certificate from Globalsign and I installed it on my ASA.
When I browse to the site in IE, Chrome, or Firefox the browser accurately shows the site with the correct certificate installed. None of the browsers show certificate errors. When I launch AnyConnect and connect to the ASA it connects fine with no certificate error.
However when I use SSL Labs to 'check' the ASA \ Certificate it states the ASA is using 'ASA Temporary Self Signed Certificate'.
https://globalsign.ssllabs.com/analyze.html?d=lab-asa.asicentral.com&latest
The URL to the ASA is https://lab-asa.asicentral.com
Its really confusing to me, why all the browsers and AnyConnect say the cert is fine and this widely recognized tool says I'm using a Self Signed Cert. Can someone can help me understand what's up?
When I look at the certificate and the trustpoint on the ASA I think it also looks incorrect.


Thank you
Tim
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 11:19 AM
Hi Tim,
I think the ASA is presenting the correct certificate.
I tried it from my end and I was able to see the Globalsign third party certificate.
I have attached the screenshot for the same.
What is the output of show run all
Regards,
Aditya
please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 11:41 AM
Thank you for replying. Please see below.
lab-asa5525x# sh runn all ssl
ssl server-version tlsv1
ssl client-version tlsv1.2
ssl cipher default medium
ssl cipher tlsv1 medium
ssl cipher tlsv1.1 medium
ssl cipher tlsv1.2 medium
ssl cipher dtlsv1 medium
ssl dh-group group2
ssl ecdh-group group19
ssl trust-point ASA_2016 Outside
ssl certificate-authentication fca-timeout 2
lab-asa5525x#
I found this Known Issue on Qualys Website and wonder if its explains what is occurring.
https://community.qualys.com/docs/DOC-4865
- SSL Labs currently shows only one certificate, even with servers that have more than one. This is a limitation of the UI, which shows the first encountered certificate. Internally, SSL Labs collects all certificates. All will be shown in a future release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 12:08 PM
Hi Tim,
It seems the
Have you installed the full certificate
If it is a production unit please do this in a change window.
Can you try to re-authenticate the
Authenticate the Trustpoint: Use the CA certificate to authenticate this
then you will get this message to enter the CA certificate, manually paste the certificate into CLI and end that with the word "quit":
Enter the base 64 encoded CA certificate.
End with the word "quit" on a line by itself
-Import the certificate: now you need to import the ASA certificate also provided from the CA
ciscoasa(config)#crypto ca import ASA_2016 certificate
After this reapply the trust point on the outside interface.
Regards,
Aditya
Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 12:36 PM
Good Afternoon,
I have followed your advise and authenticated the trustpoint.
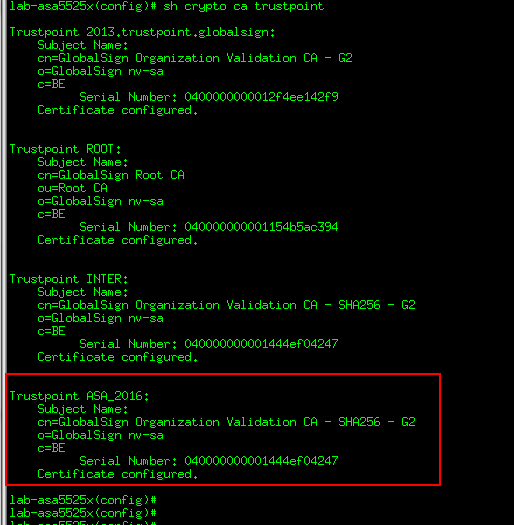
However Qualys still reports the ASA is presenting an ASA Temporary Self Signed Certificate.
https://www.ssllabs.com/ssltest/analyze.html?d=lab-asa.asicentral.com
How can I see the ASA Self Signed Certificate that is built in ? I don't see it in show runn all crypto.
Thanks again, I appreciate your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 12:48 PM
Hi,
I tried using two different tools:
https://www.digicert.com/help/ and https://www.sslchecker.com/sslchecker
They are showing the correct certificate chain for the URL.
So you can ignore the https://www.ssllabs.com validation. :)
Regards,
Aditya
Please rate helpful posts and mark the correct answers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2016 01:10 PM
One more question...
I've used openssl to query the ASA as well and openssl also states that the ASA is sending the Self Signed Certificate...

Should I really just ignore this?
Thanks
Tim
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



