- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco AnyConnect unable to connect with Apple devices
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco AnyConnect unable to connect with Apple devices
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 10:56 AM
Up until a couple weeks ago we had no issues connecting Apple devices (iPhones and iPads) to our VPN using Cisco AnyConnect. It seems now we cannot connect unless we are on a PC or Android device (tablet or smartphone). So all VPN connections are working fine except on Apple. Does anybody know of anything going on recently with Cisco and Apple? Thank you for any help.
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:20 AM
Have the AnyConnect clients on the apple devices been automatically upgraded recently? On newer anyconnect versions cisco have depreciated support for certain crypto algorithms, which stops devices connecting.
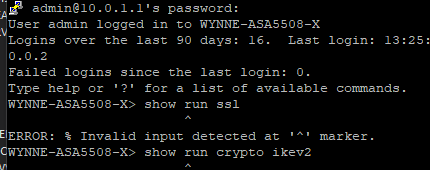
Can you provide the output of:-
- show run ssl
- show run crypto ikev2
- show run crypto ipsec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:31 AM
Result of the command: "show run ssl"
ssl client-version tlsv1.2
ssl trust-point outside-self outside
ssl trust-point inside-self inside
Result of the command: "show run crypto ikev2"
crypto ikev2 policy 1
encryption aes-gcm-256 aes-gcm-192 aes-gcm
integrity null
group 21 20 19 24 14 5 2
prf sha512 sha384 sha256 sha
lifetime seconds 28800
crypto ikev2 policy 2
encryption aes-gcm-256 aes-gcm-192 aes-gcm
integrity null
group 21 20 19 24 14 5 2
prf sha512 sha384 sha256 sha
lifetime seconds 86400
crypto ikev2 policy 3
encryption aes-gcm-256 aes-gcm-192 aes-gcm
integrity null
group 21 20 19 24 14 5 2
prf sha512 sha384 sha256 sha
lifetime seconds 3600
crypto ikev2 policy 11
encryption aes-256 aes-192 aes 3des
integrity sha512 sha384 sha256 sha
group 21 20 19 24 14 5 2
prf sha512 sha384 sha256 sha md5
lifetime seconds 86400
crypto ikev2 policy 12
encryption aes-256 aes-192 aes 3des
integrity sha512 sha384 sha256 sha
group 21 20 19 24 14 5 2
prf sha512 sha384 sha256 sha md5
lifetime seconds 28800
crypto ikev2 policy 13
encryption aes-256 aes-192 aes 3des
integrity sha512 sha384 sha256 sha
group 21 20 19 24 14 5 2
prf sha512 sha384 sha256 sha md5
lifetime seconds 3600
crypto ikev2 enable outside
crypto ikev2 cookie-challenge always
Result of the command: "show run crypto ipsec"
crypto ipsec ikev1 transform-set wynnetr esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set AES128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256-SHA
protocol esp encryption aes-256
protocol esp integrity sha-512 sha-384 sha-256 sha-1
crypto ipsec ikev2 ipsec-proposal AES128-SHA
protocol esp encryption aes
protocol esp integrity sha-512 sha-384 sha-256 sha-1
crypto ipsec security-association pmtu-aging infinite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:31 AM
Rhe prompt would then add # and change to WYNNE-ASA5508-X #
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:42 AM
Are you using SSL or IKEv2/IPSec Remote Access VPN?
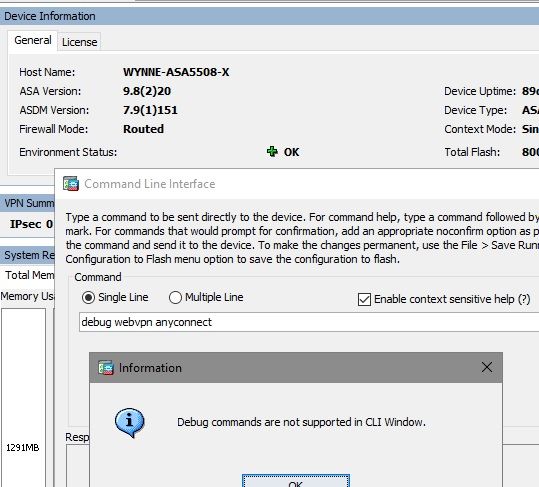
Run the following debugs from the CLI of the ASA
"debug webvpn anyconnect"
"debug crypto ikev2 platform"
"debug crypto ikev2 protocol"
And then connect to the VPN from the apple devices, provide the output of the debugs here for review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:48 AM
Do I need to physically plug into the ASA Firewall? It seems the CLI in ASDM doesn't like debug commands.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:50 AM
Once you have run the debugs, make sure you turn off debugging using the command "undebug all"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:56 AM
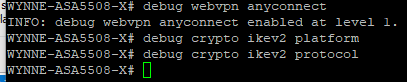
I entered the debug commands. I still cannot login to VPN on Apple device. The log on AnyConnect shows the same errors fromt he beginning of this post. Are there logs on ASDM Firewall I need to gather?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 11:59 AM
- logging enable
- logging console notifications
- logging monitor notifications
Once you connect, I expect the connection to fail, but the output in the debug should give an indication where the is might be.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 12:07 PM
I was able to enable logging but still not seeing any results in Putty. What step did I miss?
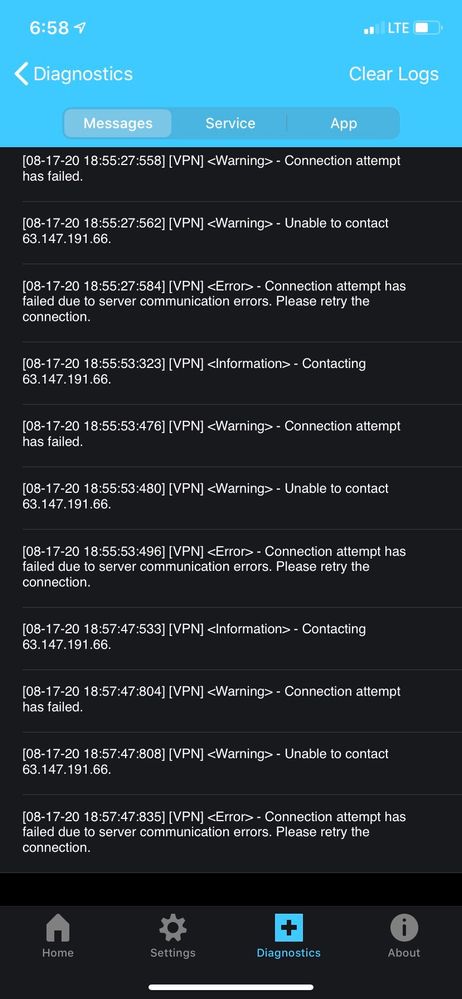
I could not logon to VPN. There are logs on iPad. There are 3 logs: Messages, Services and App. But it just shows same errors as it did before.
Thank you for your assistance, I appreciate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 12:12 PM
With all of these commands it should display IKEv2 or SSL connections to the console.
logging enable
logging console notifications
logging monitor notifications
debug webvpn anyconnect
debug crypto ikev2 protocol
debug crypto ikev2 platform
Try connecting from a device that does work and see if you get any debug output then.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2020 12:15 PM
So I just connected to VPN using my Android phone and I see debug info populate on Putty.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide