- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cisco ASA and anyconnect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 02:49 AM
Hello, we can't figure out what's wrong. We haven't been able to beat this for 2 weeks now. Help.
We have configured AnyConnect VPN Client Connections, but we encountered a problem:
When the client connects to AnyConnect VPN Client Connections, the client cannot work with the local network. It cannot ping gateways. It also cannot ping local machines and connect via RDP protocol. When connecting pass when pinging 1-1 packets - then interruption. No response
But all routes and ipaddresses from the pool come.
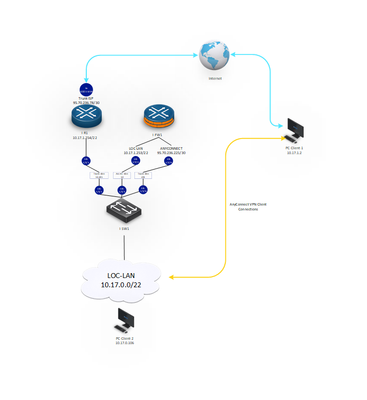
On the diagram we have shown the topology of our network and client connection via AnyConnect VPN Client Connections.
We have also provided logs and configuration of cisco asa.
Config
webvpn
enable ANYCONNECT
http-headers
hsts-server
enable
max-age 31536000
include-sub-domains
no preload
hsts-client
enable
x-content-type-options
x-xss-protection
content-security-policy
anyconnect image disk0:/anyconnect-win-4.10.08025-webdeploy-k9.pkg 1 regex "Windows NT"
anyconnect image disk0:/anyconnect-linux64-4.10.08025-webdeploy-k9.pkg 2 regex "Linux"
anyconnect image disk0:/anyconnect-macos-4.10.08025-webdeploy-k9.pkg 3
anyconnect profiles CONNECT-I_LAN_client_profile disk0:/CONNECT-I_LAN_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
ip local pool POOL-LOC-I 10.17.1.1-10.17.1.100 mask 255.255.252.0
tunnel-group CONNECT-I_LAN type remote-access
tunnel-group CONNECT-I_LAN general-attributes
address-pool POOL-LOC-I
default-group-policy GroupPolicy_CONNECT-I_LAN
tunnel-group CONNECT-I_LAN webvpn-attributes
group-alias CONNECT-I_LAN enable
group-policy GroupPolicy_CONNECT-I_LAN internal
group-policy GroupPolicy_CONNECT-I_LAN attributes
wins-server none
dns-server value 10.17.1.254
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT_CONNECT-I
default-domain value magvatech.com
split-tunnel-all-dns disable
webvpn
anyconnect profiles value CONNECT-I_LAN_client_profile type user
route ANYCONNECT 0.0.0.0 0.0.0.0 95.70.236.224 5
access-list SPLIT_CONNECT-I remark LOC-I
access-list SPLIT_CONNECT-I standard permit 10.17.0.0 255.255.252.0
interface Ethernet1/1
no switchport
no nameif
no security-level
no ip address
!
interface Ethernet1/1.201
description ANYCONNECT
vlan 201
nameif ANYCONNECT
security-level 0
ip address 95.70.236.225 255.255.255.254
interface Ethernet1/3
no switchport
nameif LOC-LAN
security-level 100
ip address 10.17.1.253 255.255.252.0
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Other VPN Topics
-
Remote Access
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 03:37 AM
@Vasiliy P do you have a NAT exemption rule to ensure the RAVPN traffic is not unintentially translated? Example below (change objects LAN/RAVPN to reflect your networks):-
nat (LOC-LAN,ANYCONNECT) source static LAN LAN destination static RAVPN RAVPN
Also create your VPN IP pool (POOL-LOC-I) from a network that is separate from the internal LAN network - as in not within 10.17.0.0/22
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 03:52 AM - edited 02-21-2024 04:37 AM
I use smart phone so I missing see vpn pool it indeed overlapping with Inside subnet
Thanks
Have a nice day
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 03:15 AM
can more elaborate about anyconnect interface ?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 03:27 AM
interface Ethernet1/1
no switchport
no nameif
no security-level
no ip address
!
interface Ethernet1/1.201
description ANYCONNECT
vlan 201
nameif ANYCONNECT
security-level 0
ip address 95.70.236.225 255.255.255.254
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 03:52 AM - edited 02-21-2024 04:37 AM
I use smart phone so I missing see vpn pool it indeed overlapping with Inside subnet
Thanks
Have a nice day
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 03:37 AM
@Vasiliy P do you have a NAT exemption rule to ensure the RAVPN traffic is not unintentially translated? Example below (change objects LAN/RAVPN to reflect your networks):-
nat (LOC-LAN,ANYCONNECT) source static LAN LAN destination static RAVPN RAVPN
Also create your VPN IP pool (POOL-LOC-I) from a network that is separate from the internal LAN network - as in not within 10.17.0.0/22
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 04:22 AM
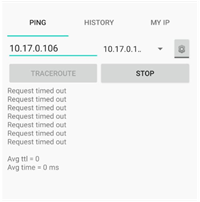
Changed the ip pool, which does not overlap with the LAN.
I made NAT and added routes with border router, immediately ping to the LAN worked, also RDP worked.
But the only thing I cannot ping ASA itself from the client AnyConnect. Otherwise, everything worked.
Thank you very much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 04:31 AM
@Vasiliy P what IP address of the ASA are you pinging?
You may need to permit ICMP "icmp permit host x.x.x.x <interface>" you can use the "management-access <interfacename>" that will allow you to ping to an ASA interface when connect to a VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
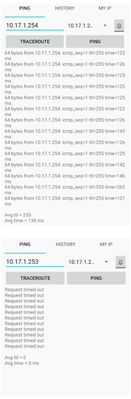
02-21-2024 06:14 AM
ASA address 10.17.1.253
From the LOC-LAN interface ip 10.17.0.106/22 I am pinging ASA ip 10.17.1.253/22
But when I connect via Annyconnect and get an ip from the pool e.g. 10.17.16.10/24.
I ping everything except the ASA itself.
In ASA I have written as you recommended
icmp permit host 10.17.16.10 ANYCONNECT
management-access ANYCONNECT
But the ping does not pass these hosts to each other
10.17.1.253/22 cannot ping 10.17.16.10/24
10.17.16.10/24 cannot ping 10.17.1.253/22
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 06:27 AM
@Vasiliy P The management_interface specifies the name of the management interface that you want to access when entering the ASA from another interface.
management-access LOC-LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2024 07:14 AM
""From the LOC-LAN interface ip 10.17.0.106/22 I am pinging ASA ip 10.17.1.253/22""
you change the Pool Subnet but still there is conflict between Anyconnect Pool and Loc-LAN
both use same 10.17.0.0/22 network-ID
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide