- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Digital Certificates based Site-2-Site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Digital Certificates based Site-2-Site VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2010 09:58 PM
Hi
I currently have this set up in my Lab.
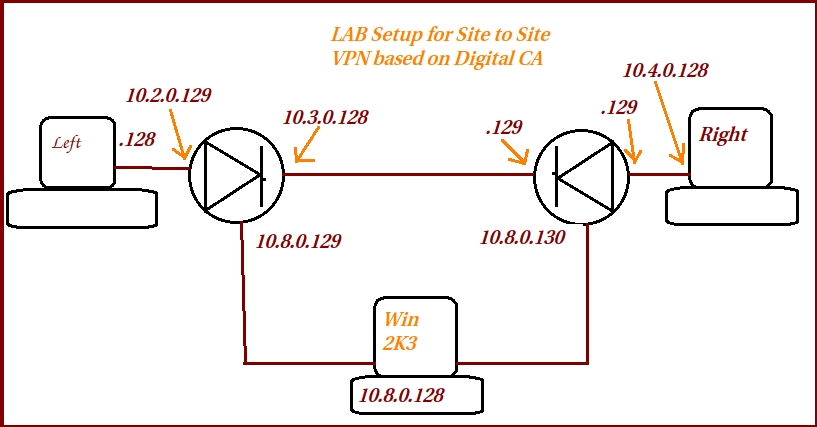
I am able to get a VPN established when I use PRE-shared key when I ping from 10.4.0.128 to 10.2.0.128, however it fails when it comes to digital certificate. Some one tell me what I am missing in my configuration.
When I tried to import CA Certificate the ASA accepted it without any errors and there were no errors when requesting for Identity certificate as well.
I am not able to establish VPN connection by pinging from 10.2.0.128 to 10.4.0.128, cos this is the error I am getting.
debug crypto isakmp 200
debug crypto ipsec 200
Apr 01 21:20:36 [IKEv1 DEBUG]: Pitcher: received a key acquire message, spi 0x0
Apr 01 21:20:36 [IKEv1]: There is no valid IKE proposal available, check IPSec SA configuration!
Apr 01 21:20:36 [IKEv1]: Removing peer from peer table failed, no match!
Apr 01 21:20:36 [IKEv1]: Error: Unable to remove PeerTblEntry
LEFT CONFIGURATION
Left(config)# sh run
: Saved
:
PIX Version 8.0(2)
!
hostname Left
domain-name local.domain
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif inside
security-level 100
ip address 10.2.0.129 255.255.255.0
!
interface Ethernet1
nameif outside
security-level 0
ip address 10.3.0.128 255.255.255.0
!
interface Ethernet2
nameif CA
security-level 0
ip address 10.8.0.129 255.255.255.0
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
clock timezone IST 5 30
dns server-group DefaultDNS
domain-name local.domain
object-group service redirectDMZ0 tcp
port-object eq 8080
access-list outside_cryptomap extended permit ip 10.2.0.0 255.255.255.0 10.4.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 10.2.0.0 255.255.255.0 10.4.0.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu CA 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
nat (inside) 0 access-list inside_nat0_outbound
route outside 0.0.0.0 0.0.0.0 10.3.0.129 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 10.2.0.128 255.255.255.255 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set MyTransform esp-3des esp-md5-hmac
crypto map outside_map0 1 match address outside_cryptomap
crypto map outside_map0 1 set peer 10.3.0.129
crypto map outside_map0 1 set transform-set MyTransform
crypto map outside_map0 interface outside
crypto ca trustpoint ASDM_TrustPoint0
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
fqdn Left
subject-name OU=LEFTASA,O=LEFT
password *
keypair RSAKEY
no client-types
crl configure
crypto ca certificate chain ASDM_TrustPoint0
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
....DELETED......
c5d9654c 7556dc4d 5c3c6589 d71f745d 89626278 ee61a707 8b5cffa5 6c495e71
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate 615dc64900000000000a
308203fd 308202e5 a0030201 02020a61 5dc64900 00000000 0a300d06 092a8648
.....DELETED..........
1f36f98a 3410f97e 9924f0b8 e974c898 8d5bbfcb dbe274c5 d9eaa601 d395f23f fa
quit
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
....DELETED
830563c2 7270cdea e28f60f7 2d256ed3 38bb
quit
crypto isakmp enable outside
crypto isakmp policy 10
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
!
policy-map global-policy
class class-default
inspect icmp
!
service-policy global-policy global
tunnel-group 10.3.0.129 type ipsec-l2l
tunnel-group 10.3.0.129 ipsec-attributes
trust-point ASDM_TrustPoint1
prompt hostname context
Cryptochecksum:1448be26807cf84eec2d48e2abf638a2
: end
Left(config)#
RIGHT CONFIGURATION
Right(config)# sh run
: Saved
:
PIX Version 8.0(2)
!
hostname Right
domain-name local.domain
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif inside
security-level 100
ip address 10.4.0.129 255.255.255.0
!
interface Ethernet1
nameif outside
security-level 0
ip address 10.3.0.129 255.255.255.0
!
interface Ethernet2
nameif CA
security-level 0
ip address 10.8.0.130 255.255.255.0
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
clock timezone IST 5 30
dns server-group DefaultDNS
domain-name local.domain
object-group service redirectDMZ0 tcp
port-object eq 8080
object-group network Remote-Network
description Remote Network
network-object 10.2.0.0 255.255.255.0
access-list outside_cryptomap extended permit ip 10.4.0.0 255.255.255.0 10.2.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 10.4.0.0 255.255.255.0 10.2.0.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu CA 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
nat (inside) 0 access-list inside_nat0_outbound
route outside 0.0.0.0 0.0.0.0 10.3.0.128 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 10.4.0.128 255.255.255.255 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set MyTransform esp-3des esp-md5-hmac
crypto map outside_map0 1 match address outside_cryptomap
crypto map outside_map0 1 set peer 10.3.0.128
crypto map outside_map0 1 set transform-set MyTransform
crypto map outside_map0 interface outside
crypto ca trustpoint ASDM_TrustPoint0
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
fqdn Right
subject-name OU=RightASA,O=Right
password *
keypair RSAKEY
no client-types
crl configure
crypto ca certificate chain ASDM_TrustPoint0
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
............DELETED............
830563c2 7270cdea e28f60f7 2d256ed3 38bb
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate 616286f600000000000b
30820401 308202e9 a0030201 02020a61 6286f600 00000000 0b300d06 092a8648
........DELETED..........
c8d598d8 1078f0ee ac8c5148 ee1eb4e9 061a0687 b7983ab0 0e422af0 e5c776eb
a7d1fdf5 26
quit
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
.....................DELETED......................
830563c2 7270cdea e28f60f7 2d256ed3 38bb
quit
crypto isakmp enable outside
crypto isakmp policy 10
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
!
policy-map global-policy
class class-default
inspect icmp
!
service-policy global-policy global
tunnel-group 10.3.0.128 type ipsec-l2l
tunnel-group 10.3.0.128 ipsec-attributes
trust-point ASDM_TrustPoint1
prompt hostname context
Cryptochecksum:5a4c4c100d7017ae46c1185e4b1d4541
: end
Right(config)#
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2010 02:43 AM
Can you please share output of "show crypto ca cert" from both LEFT and RIGHT. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2010 05:07 AM
Left# sh crypto ca certificates
Certificate
Status: Available
Certificate Serial Number: 615dc64900000000000a
Certificate Usage: General Purpose
Public Key Type: RSA (1024 bits)
Issuer Name:
cn=certsrv
Subject Name:
ou=LEFTASA
o=LEFT
hostname=Left
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 20:41:04 IST Apr 1 2010
end date: 20:51:04 IST Apr 1 2011
Associated Trustpoints: ASDM_TrustPoint1
CA Certificate
Status: Available
Certificate Serial Number: 4ee37460ea2c17a145e011675b0f8b08
Certificate Usage: Signature
Public Key Type: RSA (2048 bits)
Issuer Name:
cn=certsrv
Subject Name:
cn=certsrv
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 09:50:10 IST Apr 1 2010
end date: 09:59:20 IST Apr 1 2015
Associated Trustpoints: ASDM_TrustPoint1 ASDM_TrustPoint0
Left#
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Right# sh crypto ca certificates
Certificate
Status: Available
Certificate Serial Number: 616286f600000000000b
Certificate Usage: General Purpose
Public Key Type: RSA (1024 bits)
Issuer Name:
cn=certsrv
Subject Name:
ou=RightASA
o=Right
hostname=Right
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 20:46:16 IST Apr 1 2010
end date: 20:56:16 IST Apr 1 2011
Associated Trustpoints: ASDM_TrustPoint1
CA Certificate
Status: Available
Certificate Serial Number: 4ee37460ea2c17a145e011675b0f8b08
Certificate Usage: Signature
Public Key Type: RSA (2048 bits)
Issuer Name:
cn=certsrv
Subject Name:
cn=certsrv
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 09:50:10 IST Apr 1 2010
end date: 09:59:20 IST Apr 1 2015
Associated Trustpoints: ASDM_TrustPoint1 ASDM_TrustPoint0
Right#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2010 05:41 AM
Please add the following:
LEFT: crypto map outside_map0 1 set trustpoint ASDM_TrustPoint1
RIGHT: crypto map outside_map0 1 set trustpoint ASDM_TrustPoint1
If that still doesn't work, please run the debug (debug crypto isa, and debug crypto ipsec), and make sure that the logging is turned on to debugging for either buffer or terminal, depending on how you access the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2010 08:45 AM
I did try to add them still no luck, I was surprised to see that Certificate based remote access VPN is working perfectly fine, however this Site-2-Site VPN is not working .
These were the debug output I got at RightPix while pinging from Right 10.4.0.128 to Left 10.2.0.128.
Apr 02 20:59:37 [IKEv1]: Removing peer from peer table failed, no match!
Apr 02 20:59:37 [IKEv1]: Error: Unable to remove PeerTblEntry
Apr 02 20:59:42 [IKEv1]: Removing peer from peer table failed, no match!
Apr 02 20:59:42 [IKEv1]: Error: Unable to remove PeerTblEntry
Apr 02 20:59:47 [IKEv1]: Removing peer from peer table failed, no match!
Apr 02 20:59:47 [IKEv1]: Error: Unable to remove PeerTblEntry
Apr 02 20:59:52 [IKEv1]: Removing peer from peer table failed, no match!
Apr 02 20:59:52 [IKEv1]: Error: Unable to remove PeerTblEntry
While there was no debug logs which appeared on the LeftPix.
I have attached my Running config once again.
LeftPix Config
LeftPix(config)# sh run
: Saved
:
PIX Version 8.0(2)
!
hostname LeftPix
domain-name local.domain
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif inside
security-level 100
ip address 10.2.0.129 255.255.255.0
!
interface Ethernet1
nameif outside
security-level 0
ip address 10.3.0.128 255.255.255.0
!
interface Ethernet2
nameif CA
security-level 50
ip address 10.8.0.129 255.255.255.0
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
clock timezone IST 5 30
dns server-group DefaultDNS
domain-name local.domain
access-list outside_cryptomap extended permit ip 10.2.0.0 255.255.255.0 10.4.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 10.2.0.0 255.255.255.0 10.4.0.0 255.255.255.0
pager lines 24
mtu inside 1500
mtu outside 1500
mtu CA 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
nat (inside) 0 access-list inside_nat0_outbound
route outside 0.0.0.0 0.0.0.0 10.3.0.129 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 10.2.0.128 255.255.255.255 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto map outside_map0 1 match address outside_cryptomap
crypto map outside_map0 1 set peer 10.3.0.129
crypto map outside_map0 1 set transform-set ESP-AES-128-SHA
crypto map outside_map0 1 set trustpoint ASDM_TrustPoint1
crypto map outside_map0 interface outside
crypto ca trustpoint ASDM_TrustPoint0
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
fqdn LeftPix.local.domain
subject-name OU=LeftDept,O=Left
password *
keypair VPNKEY
no client-types
crl configure
crypto ca certificate chain ASDM_TrustPoint0
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
..........DELETED....................
830563c2 7270cdea e28f60f7 2d256ed3 38bb
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate 610e9af300000000000f
3082041e 30820306 a0030201 02020a61 0e9af300 00000000 0f300d06 092a8648
..........DELETED....................
f1cdd594 f513e585 16fd11de 74864ddc 5d089cea 52e53a64 dfd2abbf 984f142d 156f
quit
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
..........DELETED....................
830563c2 7270cdea e28f60f7 2d256ed3 38bb
quit
crypto isakmp enable outside
crypto isakmp policy 1
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto isakmp policy 5
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 10
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
!
policy-map global-policy
class class-default
inspect icmp
!
service-policy global-policy global
tunnel-group 10.3.0.129 type ipsec-l2l
tunnel-group 10.3.0.129 ipsec-attributes
trust-point ASDM_TrustPoint1
prompt hostname context
Cryptochecksum:d40ea677873d85f78ec329de69fffde7
: end
LeftPix(config)#
LeftPix(config)# sh crypto ca certificates
Certificate
Status: Available
Certificate Serial Number: 610e9af300000000000f
Certificate Usage: General Purpose
Public Key Type: RSA (1024 bits)
Issuer Name:
cn=certsrv
Subject Name:
ou=LeftDept
o=Left
hostname=LeftPix.local.domain
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 20:09:17 IST Apr 2 2010
end date: 20:19:17 IST Apr 2 2011
Associated Trustpoints: ASDM_TrustPoint1
CA Certificate
Status: Available
Certificate Serial Number: 4ee37460ea2c17a145e011675b0f8b08
Certificate Usage: Signature
Public Key Type: RSA (2048 bits)
Issuer Name:
cn=certsrv
Subject Name:
cn=certsrv
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 09:50:10 IST Apr 1 2010
end date: 09:59:20 IST Apr 1 2015
Associated Trustpoints: ASDM_TrustPoint1 ASDM_TrustPoint0
LeftPix(config)#
RightPix Config
RightPix(config)# sh run
: Saved
:
PIX Version 8.0(2)
!
hostname RightPix
domain-name local.domain
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif inside
security-level 100
ip address 10.4.0.129 255.255.255.0
!
interface Ethernet1
nameif outside
security-level 0
ip address 10.3.0.129 255.255.255.0
!
interface Ethernet2
nameif CA
security-level 50
ip address 10.8.0.130 255.255.255.0
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
clock timezone IST 5 30
dns server-group DefaultDNS
domain-name local.domain
access-list outside_cryptomap extended permit ip 10.4.0.0 255.255.255.0 10.2.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 10.4.0.0 255.255.255.0 10.2.0.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu CA 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
nat (inside) 0 access-list inside_nat0_outbound
route outside 0.0.0.0 0.0.0.0 10.3.0.128 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 10.4.0.128 255.255.255.255 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto map outside_map0 1 match address outside_cryptomap
crypto map outside_map0 1 set peer 10.3.0.128
crypto map outside_map0 1 set transform-set ESP-AES-128-SHA
crypto map outside_map0 1 set trustpoint ASDM_TrustPoint1
crypto map outside_map0 interface outside
crypto ca trustpoint ASDM_TrustPoint0
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment url http://10.8.0.128:80/certsrv/mscep/mscep.dll
fqdn RightPix.local.domain
subject-name OU=RightDept,O=Right
password *
keypair VPNKEY
no client-types
crl configure
crypto ca certificate chain ASDM_TrustPoint0
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
..........DELETED....................
830563c2 7270cdea e28f60f7 2d256ed3 38bb
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate 610b167000000000000e
30820422 3082030a a0030201 02020a61 0b167000 00000000 0e300d06 092a8648
..........DELETED....................
f9bde8b1 a3815ec5 30fe2c50 5885dafa b19afe6c c1aaab28 7405b5d0 45774c87
06168579 5a8a
quit
certificate ca 4ee37460ea2c17a145e011675b0f8b08
3082036e 30820256 a0030201 0202104e e37460ea 2c17a145 e011675b 0f8b0830
..........DELETED....................
830563c2 7270cdea e28f60f7 2d256ed3 38bb
quit
crypto isakmp enable outside
crypto isakmp policy 1
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto isakmp policy 5
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 10
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
!
policy-map global-policy
class class-default
inspect icmp
!
service-policy global-policy global
tunnel-group 10.3.0.128 type ipsec-l2l
tunnel-group 10.3.0.128 ipsec-attributes
trust-point ASDM_TrustPoint1
prompt hostname context
Cryptochecksum:c9aa31872bd96300ad61f307e931ba3f
: end
RightPix(config)#
RightPix(config)# sh crypto ca certificates
Certificate
Status: Available
Certificate Serial Number: 610b167000000000000e
Certificate Usage: General Purpose
Public Key Type: RSA (1024 bits)
Issuer Name:
cn=certsrv
Subject Name:
ou=RightDept
o=Right
hostname=RightPix.local.domain
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 20:05:26 IST Apr 2 2010
end date: 20:15:26 IST Apr 2 2011
Associated Trustpoints: ASDM_TrustPoint1
CA Certificate
Status: Available
Certificate Serial Number: 4ee37460ea2c17a145e011675b0f8b08
Certificate Usage: Signature
Public Key Type: RSA (2048 bits)
Issuer Name:
cn=certsrv
Subject Name:
cn=certsrv
CRL Distribution Points:
[1] http://bullet-win2k3/CertEnroll/certsrv.crl
[2] file://\\bullet-win2k3\CertEnroll\certsrv.crl
Validity Date:
start date: 09:50:10 IST Apr 1 2010
end date: 09:59:20 IST Apr 1 2015
Associated Trustpoints: ASDM_TrustPoint1 ASDM_TrustPoint0
RightPix(config)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2010 11:18 AM
I did exactlly as given in this link and still no luck http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080aa5be1.shtml
However when I followed the process for RemoteAccess VPN it worked without a glitch. So I can be pretty sure that my Digital Certificates are correct however I will still be breaking my head over this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2010 03:41 PM
Last resort, I will try saving both configs and reload both PIXes.
Config looks absolutely correct. I had experienced before where changing from pre-shared key to certificate just wouldn't work until i reload the devices. Hopefully it would be the same case for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2010 11:59 PM
I tried rebooting the pix serveral time before with no effect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2010 12:14 AM
Try to add this under your crypto trustpoint: ignore-ipsec-keyusage
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2010 06:26 AM
Hi,
In case if the issue persists after adding the command "ignore-ipsec-keyusage" under the TP then get the output of "debug crypto ca transactions 200" "debug crypto ca messages 200" and "debug cry ca 100".
Regards,
Naveen
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

