- Cisco Community
- Technology and Support
- Security
- VPN
- Re: FMC, AnyConnect, and RADIUS - assign conection profile?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 08:57 AM - edited 02-21-2020 09:27 PM
Setting up remote access VPN from FMC - I'm authenticating to my Windows NPS server ok, and I can use 3076 / 85 to group lock the user to the right connection profile. I want to take it one step further and disable the ability to choose a connection profile and just assign it based on AD group membership. I can't find how to do that with FMC. Can anyone point me in the right direction? Bonus points if you can also explain how to use DHCP server and assign the scope based on connection profile. I remember doing it with ASA.... FMC is a little different and I'm trying to catch up with it.
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 09:57 AM - edited 08-30-2018 09:58 AM
Do you mean assigning a group-policy based on AD membership? You cannot choose Connection profile based on AAA credentials because that is where the Firepower/ASA defines what auth mechanism to use. But you can get the same behavior with assigning different group-policies to users based on their AD credentials. A few things to do this and I believe you already have major portions completed.
1) Choose a tunnel-group/connection profile where you want all users to fall into
2) Assign a group-url for that CP and set it to "https://<FQDN>"
3) Find the default group-policy assigned to the CP. Under that group-policy settings, set simulataneous logins to 0.
4) Create different group-policies for different sets of users.
5) On NPS, create conditions to Assign Radius Class attribute as "Group-policy-Name". The conditions can be based on your AD group membership.
6) Inside the group-policy, add scope under the general tab
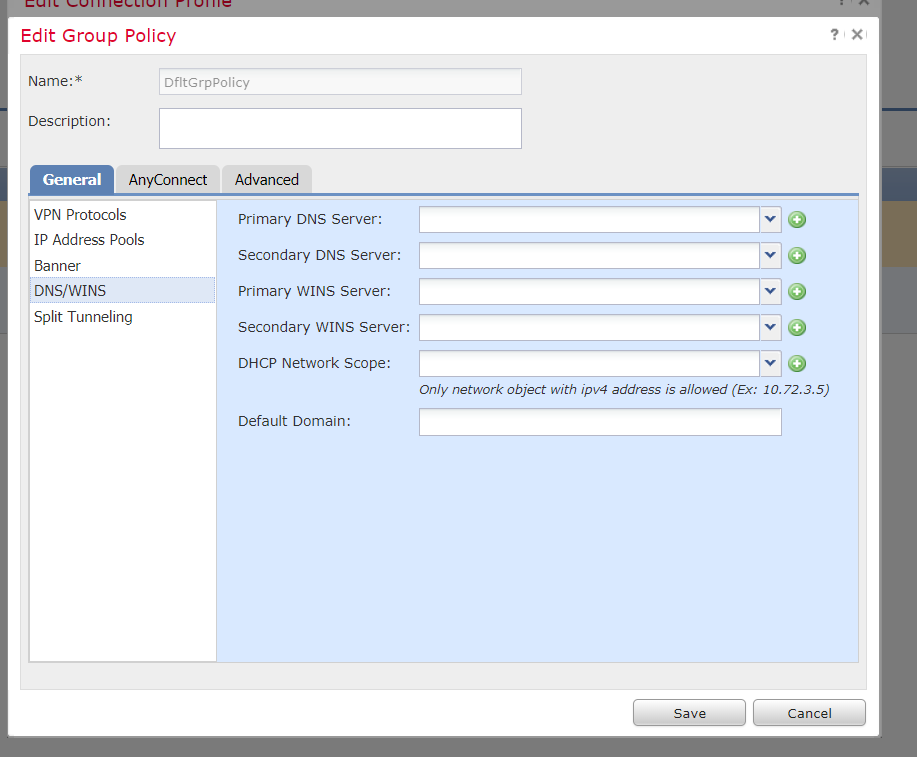
User goes to https://vpn[dot]domain[dot]com. No dropdown or list to choose from. They enter their AD credentials. Based on AD credentials, NPS returns Access-Accept with group-policy name set as Radius Class atribute. FTD then uses this info and automatically maps this user to that group-policy. Based on the group-policy, the DHCP scope and other options are applied to the user. If the user is not part of any of the NPS conditoons, you can send a Reject from NPS or send an accept with no Class attribute. They will fall into the Default group policy for that CP and be dropped (simultaneous logins =0).
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 09:57 AM - edited 08-30-2018 09:58 AM
Do you mean assigning a group-policy based on AD membership? You cannot choose Connection profile based on AAA credentials because that is where the Firepower/ASA defines what auth mechanism to use. But you can get the same behavior with assigning different group-policies to users based on their AD credentials. A few things to do this and I believe you already have major portions completed.
1) Choose a tunnel-group/connection profile where you want all users to fall into
2) Assign a group-url for that CP and set it to "https://<FQDN>"
3) Find the default group-policy assigned to the CP. Under that group-policy settings, set simulataneous logins to 0.
4) Create different group-policies for different sets of users.
5) On NPS, create conditions to Assign Radius Class attribute as "Group-policy-Name". The conditions can be based on your AD group membership.
6) Inside the group-policy, add scope under the general tab

User goes to https://vpn[dot]domain[dot]com. No dropdown or list to choose from. They enter their AD credentials. Based on AD credentials, NPS returns Access-Accept with group-policy name set as Radius Class atribute. FTD then uses this info and automatically maps this user to that group-policy. Based on the group-policy, the DHCP scope and other options are applied to the user. If the user is not part of any of the NPS conditoons, you can send a Reject from NPS or send an accept with no Class attribute. They will fall into the Default group policy for that CP and be dropped (simultaneous logins =0).
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 12:59 PM
That's exactly what I needed - thank you!
I think I'm still missing something simple with my scope selection, but it does use group-policy based on AD group membership now.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide