- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Good CCIE question: Can multiple site-2-site VPNs support dy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Good CCIE question: Can multiple site-2-site VPNs support dynamic routing protocols?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2012 06:47 AM
Hi All,
Was not sure if this should be posted in LAN routing, WAN routing or VPN forums: I have posted here as the VPN tunnels are the limiting factors...
I am trying to understand if it is possible to have dynamic routing between LANs when using site to site VPNs on three or more ASA55x5-x (9.0).
To best explain the question I have put together an example scenario:
- Lets say we have three sites, which are all connected via a separate site-2-site IKEv2 VPNs, in a full mesh topology (6 x SAs).
- Across the whole system there would be a 192.168.0.0/16 subnet which is divided up by VLSM across all sites.
- The inside / outside interfaces of the ASA would be static IPs from a /30 subnet.
- Routing on the outside interface is not of concern in this scenario.
- The inside interface of the ASA connects directly to a router, which further uses VLSM to assign additional subnets.
- VLSM is not cleanly summarised per site. (I know this flys against VLSM best practice, but makes the scenario clearer...)
- New subnets are added and removed at each site on a frequent basis.
- EIGRP will be running on each core router, and any stub routers at each site.
So this results in the following example topology, of which I have exaggerated the VLSM position:
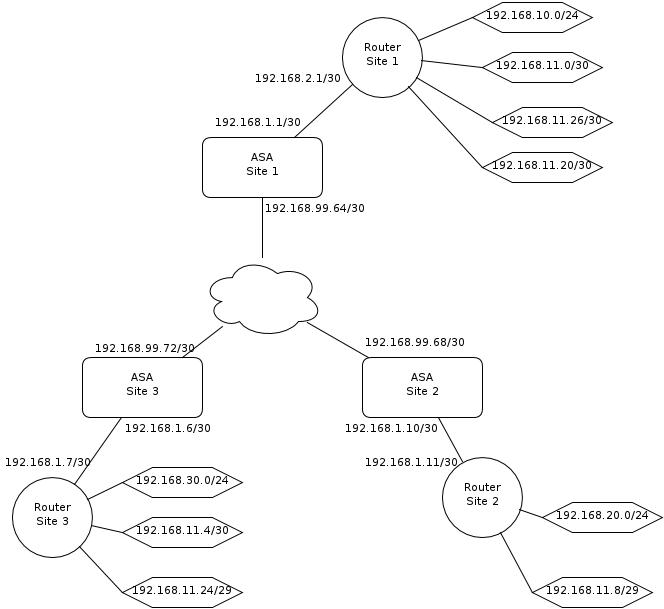
(http://www.diagram.ly/?share=#OtprIYuOeKRb3HBV6Qy8CL8ZUE6Bkc2FPg2gKHnzVliaJBhuIG)
Now, using static route redistribution from the ASAs into EIGRP and making the ASAs to be an EIGRP neighbour, would be one way. This would mean an isolated EIGRP AS per site, but each site would only learn about a new remote subnet if the crypto map match ACL was altered. But the bit that I am confused over, is the potential to have new subnets added or removed which would require EIGRP routing processes on the relevant site X router to be altered as well as crypto map ACLs being altered at all sites. This doesn't seem a sensible approach...
The second method could be to have the 192.168.0.0/16 network defined in the crypto map on all tunnels and allow the ASAs routing table to chose which tunnel to send the traffic over. This would require multiple neighbours for the ASA, but for example in OSPF, it can only support one neighbour over a S2S VPN when manually defined (point-to-point). The only way round this I can see is to share our internal routing tables with the IP cloud, but this then discloses information that would be otherwise protected by the IPSEC tunnel...
Is there a better method to propagate the routing information dynamically around the example scenario above?
Is there a way to have dynamic crypto maps based on router information?
P.S. Diagram above produced via http://www.diagram.ly/
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2012 07:57 AM
James,
Look into RPs based on unicast.
One such would be iBGP orrrr OSPF in point-to-point scenario, which allows you to create neighbors and echange routes over unistcast. Described here:
M.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2012 09:24 AM
You're making the problem much more difficult than it really needs to be. In your situation, you need
to do this:
- terminate IPSec on ASA devices which look like you already did,
- Create GRE tunnel between routers at each location and use the GRE tunnel to establish your dynamic routing protocol
Now because you're NOT terminating GRE and IPSec on the same interface because you have ASA device, the problem is little bit tricky; however, this scenario has been around for at least ten years. Cisco has a configuration scenario for it:
http://www.cisco.com/en/US/tech/tk583/tk372/technologies_configuration_example09186a0080094bff.shtml
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2012 01:10 PM
Hi Guys,
Thanks for your responses! I am learning here, hence the post.
David: I had looked in to the potential for GRE tunnels, but the side-effects could out weight the benifits. The link provided shows how to pass IKEv1 and ISAKMP traffic through the ASA. In my example (maybe not too clear?) the IPSEC traffic would be terminated on the ASA and not the core router behind.
Marcin: Was looking at OSPF, but is that not limited to one neighbour, due to the "ospf network point-to-point non-broadcast" command in the example (needed to force the unicast over the IPSEC tunnel)? Have had a look in the ASA CLI 9.0 config guide and it is still limited to one neighbour per interface when in point-to-point:
ospf network point-to-point non-broadcastSpecifies the interface as a point-to-point, non-broadcast network.
When you designate an interface as point-to-point and non-broadcast, you must manually define the OSPF neighbor; dynamic neighbor discovery is not possible. See the "Defining Static OSPFv2 Neighbors" section for more information. Additionally, you can only define one OSPF neighbor on that interface.
Otherwise I would agree it would be happy days...
Any other ideas (maybe around iBGPs like OSPF) which do not envolve GRE tunnels or terminating the IPSEC on the core router please?
Kindest Regards,
James.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2012 01:59 PM
As a follow on:
Can you define an OSPF neighbors without issuing an "ospf network point-to-point non-broadcast" command on the interface on an ASA, ergo have multiple neighbours within a fragmented area 0?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2012 02:12 PM
james,
In your scenario, it is a much easier implementation because you're:
1- terminate IPSec on the ASA,
2- terminate GRE on the router,
Just modify your encryption domain to for GRE traffics between these routers and tunnel everything over GRE which will encrypt everything inside an IPSec tunnel via ASA. In fact, your encryption domain (aka interesting traffics) will reduce to only three IP addresses (site 1, site 2 and site 3 router). that is because all the networks behind the routers will be tunneled through GRE. Your dynamic routing will work great and multicast will work well as well due to GRE
By the way, this solution is vendor independent because your firewall could be ASA, Checkpoint or Juniper. it does not matter. As long as the firewall can terminate IPSec, GRE on the router will take care of the rest.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2012 03:09 PM
James,
David's suggestion is quite popular and well tested indeed. Truth me told I would rather suggest IOS routers here rather than ASA - like any routing scenario requiring flexability.
Regarding our discussion about network types. point-to-multipoint is what you're looking for. But from what I see ASA does not have that mode of operation.
M.
edit: although you will be using ASA as encryption device - without some of the more advanced features for traffic between sites.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide