- Cisco Community
- Technology and Support
- Security
- VPN
- Re: I'm Newbie for VPN Site to Site Cisco, Need Helps !
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2019 08:21 AM - edited 02-21-2020 09:36 PM
hostname R-VN
!
!
!
!
ip dhcp excluded-address 192.168.1.1
ip dhcp excluded-address 192.168.2.1
!
ip dhcp pool Vlan10
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
dns-server 8.8.8.8
ip dhcp pool Vlan20
network 192.168.2.0 255.255.255.0
default-router 192.168.2.1
dns-server 8.8.8.8
!
!
!
ip cef
no ipv6 cef
!
!
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
!
crypto isakmp key !Cisco@23@ address 20.20.20.2
!
!
!
crypto ipsec transform-set VPNSet esp-3des esp-md5-hmac
!
crypto map VPN-VN-US 10 ipsec-isakmp
set peer 20.20.20.2
set transform-set VPNSet
match address VPN-Tunnel
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
ip address 10.10.10.2 255.255.255.252
ip access-group Internet out
ip nat outside
duplex auto
speed auto
crypto map VPN-VN-US
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.1
encapsulation dot1Q 10
ip address 192.168.1.1 255.255.255.0
ip nat inside
!
interface FastEthernet0/1.2
encapsulation dot1Q 20
ip address 192.168.2.1 255.255.255.0
ip nat inside
!
interface Vlan1
no ip address
shutdown
!
ip nat inside source list Internet interface FastEthernet0/0 overload
ip classless
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
!
ip flow-export version 9
!
!
ip access-list extended VPN-Tunnel
permit ip 192.168.0.0 0.0.255.255 172.16.0.0 0.0.255.255
ip access-list extended Internet
deny ip 192.168.0.0 0.0.255.255 172.16.0.0 0.0.255.255
permit ip any any
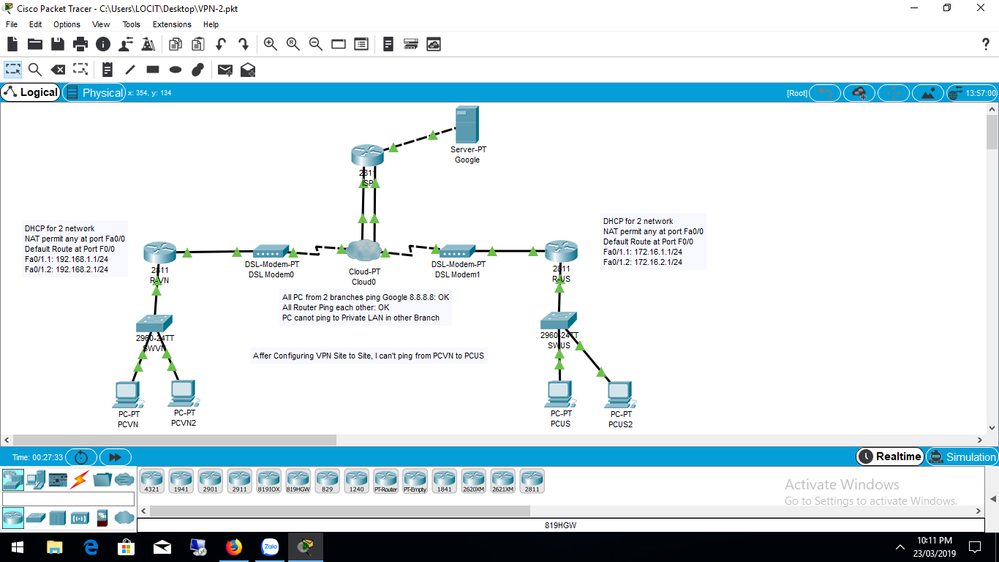
When I show crypto isakmp sa, there is nothing, it's empty, and I can't Ping PCVN to PCUS
What do I miss ?, Plz help me
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2019 04:52 AM
You should not need to specifically route the remote LAN subnets. The default route should be sufficient for that. You should take my advice about specifying the next hop in your static default route, though this is probably not what is preventing your vpn from working. The problem with the vpn is probably the fact that you are using the same access list to control address translation and as a packet filter on your outside interface. You should configure a different access list for your outside interface.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2019 01:07 PM
Can you post the configuration of the other router for comparison please?
Can you enable debugs, ping from a PC and upload the output here please? command is - debug crypto isakmp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2019 11:44 PM
hostname R-VN ! ip dhcp excluded-address 192.168.1.1 ip dhcp excluded-address 192.168.2.1 ! ip dhcp pool Vlan10 network 192.168.1.0 255.255.255.0 default-router 192.168.1.1 dns-server 8.8.8.8 ip dhcp pool Vlan20 network 192.168.2.0 255.255.255.0 default-router 192.168.2.1 dns-server 8.8.8.8 ! crypto isakmp policy 1 encr 3des authentication pre-share group 2 ! crypto isakmp key !Cisco@23@ address 20.20.20.2 ! ! crypto ipsec transform-set VPNSet esp-3des esp-md5-hmac ! crypto map VPN-VN-US 10 ipsec-isakmp set peer 20.20.20.2 set transform-set VPNSet match address VPN-Tunnel ! spanning-tree mode pvst ! ! interface FastEthernet0/0 ip address 10.10.10.2 255.255.255.252 ip access-group Internet out ip nat outside duplex auto speed auto crypto map VPN-VN-US ! interface FastEthernet0/1 no ip address duplex auto speed auto ! interface FastEthernet0/1.1 encapsulation dot1Q 10 ip address 192.168.1.1 255.255.255.0 ip nat inside ! interface FastEthernet0/1.2 encapsulation dot1Q 20 ip address 192.168.2.1 255.255.255.0 ip nat inside ! interface Vlan1 no ip address shutdown ! ip nat inside source list Internet interface FastEthernet0/0 overload ip classless ip route 0.0.0.0 0.0.0.0 FastEthernet0/0 ! ip access-list extended VPN-Tunnel permit ip 192.168.0.0 0.0.255.255 172.16.0.0 0.0.255.255 ip access-list extended Internet deny ip 192.168.0.0 0.0.255.255 172.16.0.0 0.0.255.255 permit ip any any | hostname R-US ! ip dhcp excluded-address 172.16.1.1 ip dhcp excluded-address 172.16.2.1 ! ip dhcp pool Vlan30 network 172.16.1.0 255.255.255.0 default-router 172.16.1.1 dns-server 8.8.8.8 ip dhcp pool Vlan40 network 172.16.2.0 255.255.255.0 default-router 172.16.2.1 dns-server 8.8.8.8 ! crypto isakmp policy 1 encr 3des authentication pre-share group 2 ! crypto isakmp key !Cisco@23@ address 10.10.10.2 ! ! crypto ipsec transform-set VPNSet esp-3des esp-md5-hmac ! crypto map VPN-US-VN 10 ipsec-isakmp set peer 10.10.10.2 set transform-set VPNSet match address VPN-Tunnel ! spanning-tree mode pvst ! ! interface FastEthernet0/0 ip address 20.20.20.2 255.255.255.252 ip access-group Internet out ip nat outside duplex auto speed auto crypto map VPN-US-VN ! interface FastEthernet0/1 no ip address duplex auto speed auto ! interface FastEthernet0/1.3 encapsulation dot1Q 30 ip address 172.16.1.1 255.255.255.0 ip nat inside ! interface FastEthernet0/1.4 encapsulation dot1Q 40 ip address 172.16.2.1 255.255.255.0 ip nat inside ! interface Vlan1 no ip address shutdown ! ip nat inside source list Internet interface FastEthernet0/0 overload ip classless ip route 0.0.0.0 0.0.0.0 FastEthernet0/0 ! ip access-list extended VPN-Tunnel permit ip 172.16.0.0 0.0.255.255 192.168.0.0 0.0.255.255 ip access-list extended Internet deny ip 172.16.0.0 0.0.255.255 192.168.0.0 0.0.255.255 permit ip any any |
Do I have to route 192.168.0.0 255.255.0.0 20.20.20.2 in Router VN and route 172.16.0.0 255.255.0.0 10.10.10.2 in Router US ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2019 01:23 PM
Can you verify that there is IP connectivity between your router and the vpn peer router? Can your router ping the peer address specifying a source address of the ping as 10.10.10.2?
I notice a couple of things in the config that you might want to address.
1) your static default route specifies the outbound interface but not the next hop. There are several things that make this not desirable. It would be beneficial (and easy) to specify the next hop which according to the /30 subnet mask must be 10.10.10.1.
2) You are using the extended access list Internet for two things. You use it to control address translation. And for that purpose it is appropriate that you deny traffic whose source is 192.168.0.0/16 and whose destination is 172.16.0.0/16. You also use that access list to control outbound traffic on your outside interface. For that purpose you probably do not want to deny traffic from your LAN to the remote LAN.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2019 11:50 PM
From the Branch VN, PCVN can ping 8.8.8.8 in the internet, can ping Public IP of Router US (20.20.20.2), and can do the same in Branch US
Router ISP, I dont configure anything
and Do i have to route 192.168.0.0 255.255.0.0 20.20.20.2 in Router VN, and 172.16.0.0 255.255.0.0 10.10.10.2 in Router US, right ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2019 04:52 AM
You should not need to specifically route the remote LAN subnets. The default route should be sufficient for that. You should take my advice about specifying the next hop in your static default route, though this is probably not what is preventing your vpn from working. The problem with the vpn is probably the fact that you are using the same access list to control address translation and as a packet filter on your outside interface. You should configure a different access list for your outside interface.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2019 08:32 AM
Hi, Richard, You gave me a best advice
First I just need to remove ACL Internet in Fa0/0 by no ip access-group Internet out
Then, specifying the next hop in the Default Route on both Branches, and reload the Routers
So PCVN can Ping PCUS from other site (ping to 2 Private LAN of the Branch US), dont need to route anything more
So, Thanks too much Richard
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2019 07:46 PM
Thanks for the update that after making the changes that I suggest it now works. I am glad that my suggestions were helpful. Thanks for marking this question as solved. This will help other participants in the community to identify discussions that have helpful content. This community is an excellent place to ask questions and to learn about networking. I hope to see you continue to be active in the community.
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide