- Cisco Community
- Technology and Support
- Security
- VPN
- IPSEC towards Barracuda
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPSEC towards Barracuda
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2021 11:13 AM
Hello,
someone can help please.
I try to establish an IPSEC tunnel towards a Barracuda but so far no success. I can not send any data in the tunnel. They are all dropped
Inbound: #pkts dec'ed 0 drop 0 life (KB/Sec) 0/0
Outbound: #pkts enc'ed 0 drop 288 life (KB/Sec) 0/0
I get following debug result:
Log Buffer (4096 bytes):
Mar 24 18:08:55.734: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP...
Mar 24 18:08:55.734: ISAKMP: (0):: incrementing error counter on sa, attempt 3 of 5: retransmit phase 1
Mar 24 18:08:55.734: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP
Mar 24 18:08:55.734: ISAKMP-PAK: (0):sending packet to 212.152.177.234 my_port 500 peer_port 500 (R) MM_SA_SETUP
Mar 24 18:08:55.734: ISAKMP: (0):Sending an IKE IPv4 Packet.
Mar 24 18:08:55.734: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP...
Mar 24 18:08:55.734: ISAKMP: (0):: incrementing error counter on sa, attempt 1 of 5: retransmit phase 1
Mar 24 18:08:55.734: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP
Mar 24 18:08:55.734: ISAKMP-PAK: (0):sending packet to 212.152.177.234 my_port 500 peer_port 500 (R) MM_SA_SETUP
Mar 24 18:08:55.734: ISAKMP: (0):Sending an IKE IPv4 Packet.
Mar 24 18:08:55.734: IPSec: Key engine got a KEY_MGR_CHECK_MORE_SAS message
Mar 24 18:08:55.734: ISAKMP (0): IPSec has no more SA's with this peer. Won't keepalive phase 1.
Mar 24 18:08:55.734: ISAKMP: (0):constructed NAT-T vendor-rfc3947 ID
Mar 24 18:08:55.734: ISAKMP-PAK: (0):sending packet to 212.152.177.234 my_port 500 peer_port 500 (R) MM_SA_SETUP
Mar 24 18:08:55.734: ISAKMP: (0):Sending an IKE IPv4 Packet.
Mar 24 18:08:55.735: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Mar 24 18:08:55.735: ISAKMP: (0):Old State = IKE_R_MM1 New State = IKE_R_MM2
Mar 24 18:08:55.743: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP...
Mar 24 18:08:55.743: ISAKMP: (0):: incrementing error counter on sa, attempt 2 of 5: retransmit phase 1
Mar 24 18:08:55.743: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP
Mar 24 18:08:55.743: ISAKMP-PAK: (0):sending packet to 212.152.177.234 my_port 500 peer_port 500 (R) MM_SA_SETUP
Mar 24 18:08:55.743: ISAKMP: (0):Sending an IKE IPv4 Packet.
Mar 24 18:08:55.743: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP...
Mar 24 18:08:55.743: ISAKMP: (0):: incrementing error counter on sa, attempt 4 of 5: retransmit phase 1
Mar 24 18:08:55.743: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP
Mar 24 18:08:55.743: ISAKMP-PAK: (0):sending packet to 212.152.177.234 my_port 500 peer_port 500 (R) MM_SA_SETUP
Mar 24 18:08:55.743: ISAKMP: (0):Sending an IKE IPv4 Packet.
Mar 24 18:08:55.744: ISAKMP-ERROR: (0):deleting SA reason "Death by retransmission P1" state (R) MM_SA_SETUP (peer 212.152.177.234)
Mar 24 18:08:55.744: ISAKMP: (0):Deleting the unauthenticated sa
Mar 24 18:08:55.745: ISAKMP: (0):Unlocking peer struct 0x80007F809FD7DB08 for isadb_mark_sa_deleted(), count 0
Mar 24 18:08:55.745: ISAKMP: (0):Deleting the peer struct for unauthenticated sa
Mar 24 18:08:55.745: ISAKMP: (0):Deleting peer node by peer_reap for 212.152.177.234: 80007F809FD7DB08
Mar 24 18:08:55.745: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
Mar 24 18:08:55.745: ISAKMP: (0):Old State = IKE_R_MM2 New State = IKE_DEST_SA
Mar 24 18:08:55.882 MEZ: %FMANFP-6-IPACCESSLOGP: R0/0: fman_fp_image: list VPNACL_IN denied tcp 91.132.58.17(54681) -> 194.24.131.50(3030), 1 packet
Mar 24 18:08:56.496: ISAKMP: (0):retransmitting phase 1 MM_NO_STATE...
Mar 24 18:08:56.496: ISAKMP: (0):peer does not do paranoid keepalives.
Mar 24 18:08:56.496: ISAKMP-ERROR: (0):deleting SA reason "Death by retransmission P1" state (I) MM_NO_STATE (peer 212.152.177.234)
Mar 24 18:08:56.496: ISAKMP-ERROR: (0):deleting SA reason "Death by retransmission P1" state (I) MM_NO_STATE (peer 212.152.177.234)
Mar 24 18:08:56.496: ISAKMP: (0):Unlocking peer struct 0x80007F809AA41C00 for isadb_mark_sa_deleted(), count 0
Mar 24 18:08:56.496: ISAKMP: (0):Deleting peer node by peer_reap for 212.152.177.234: 80007F809AA41C00
Mar 24 18:08:56.497: ISAKMP: (0):deleting node 434387125 error FALSE reason "IKE deleted"
Mar 24 18:08:56.497: ISAKMP: (0):deleting node 708602397 error FALSE reason "IKE deleted"
Mar 24 18:08:56.497: ISAKMP: (0):deleting node 1548226412 error FALSE reason "IKE deleted"
Mar 24 18:08:56.497: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
.738: ISAKMP: (0):retransmitting phase 1 MM_SA_SETUP...
Mar 24 18:09:05.738: ISAK
thanks in advance, Selcuk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2021 11:32 AM
looks like you not establish the phase 1. have you exchange the pahse 1 and phase2 setting withy your remote network. could you also share your configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2021 02:46 AM
Thank you for your support. Yes, I exchanged phase 1 and 2 settings with the remote end but somehow we are not able to trigger the tunnel. Here is my config. That is actually the similar config I always do. Just for security, I replaced IP and name with dummy credentials
!
ip vrf C-Wxx
rd 25255:3819
route-target export 25255:819
route-target import 25255:819
!
vpdn-group Wxx
description Wxx
accept-dialin
protocol l2tp
virtual-template 1119
terminate-from hostname lac_Wxx
vpn vrf corpgi
source-ip 5.6.7.8
local name SmartFlo01
l2tp tunnel hello 120
l2tp tunnel password 7 yyy
l2tp tunnel receive-window 256
ip mtu adjust
!
crypto keyring C-Wxx
pre-shared-key address 1.2.3.4 key test1234
!
crypto isakmp profile C-Wxx
vrf C-Wxx
keyring C-Wxx
match identity address 1.2.3.4 255.255.255.255
!
crypto map vpn 119 ipsec-isakmp
set peer 1.2.3.4
set security-association lifetime seconds 28800
set transform-set TS-AES-SHA
set pfs group5
set isakmp-profile C-Wxx
match address C-Wxx
reverse-route static
!
interface Loopback10119
description Monitoring IP for C-Wxx VPN
ip vrf forwarding C-Wxx
ip address 10.2.20.254 255.255.255.255
!
interface Virtual-Template1119
description Wxx DNS over AAA
ip vrf forwarding C-Wxx
ip unnumbered Loopback10119
ip tcp adjust-mss 1380
no peer default ip address
ppp mtu adaptive
ppp mru match
ppp authentication chap pap callin proxy-aaa
ppp authorization proxy-aaa
ppp ipcp dns reject
ppp ipcp mask 255.255.255.255
!
router bgp 25255
address-family ipv4 vrf C-Wxx
exit-address-family
!
ip access-list extended C-Wxx
permit ip 10.2.20.0 0.0.3.255 10.8.0.0 0.0.255.255
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2021 03:36 AM
Hi noted your crypto map
crypto map vpn 119 ipsec-isakmp set peer 1.2.3.4 set security-association lifetime seconds 28800 set transform-set TS-AES-SHA set pfs group5 set isakmp-profile C-Wxx match address C-Wxx reverse-route static
But i do not see where you calling this crypto map on your interface.
it has so be something like this
Interface ABC
crypto map vpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2021 08:43 AM
hello,
for terminating the crypto map, we use internet uplinks.
sh run int Gi0/0/0.4
Building configuration...
Current configuration : 255 bytes
!
interface GigabitEthernet0/0/0.4
description To_L3SPflo05_BB-Subint
encapsulation dot1Q 4
ip address x.x.x.x 255.255.255.254
ip nat outside
ip access-group VPNACL_IN in
ip ospf network point-to-point
ip ospf cost 11000
crypto map vpn
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2021 11:53 AM
Going through you logs and you configuration we only see MM_SA_SETUP we do not see anything else. now it could be your route some how does not go on to the wan.
you have not mentioned what is the router model or software version you using. therefore I highly recommand you to caputer the dump packets.
ip access-list extended MYCAP-ACL permit ip host x.x.x.x host y.y.y.y.y permit ip host y.y.y.y host x.x.x.x ! monitor capture MYCAP buffer circular size 100 monitor capture MYCAP interface interface GigabitEthernet0/0/0.4 both ! show monitor capture MYCAP ! monitor capture MYCAP start monitor capture MYCAP stop ! show monitor capture MYCAP buffer brief ! monitor capture MYCAP export tftp://192.168.11.1/MYCAP.pcap ! monitor capture MYCAP clear
share the caputer file.
also could you please confirm from the cli least you can ping the peer (remote public) ip address?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2021 06:38 AM
Hallo Sheraz Salim,
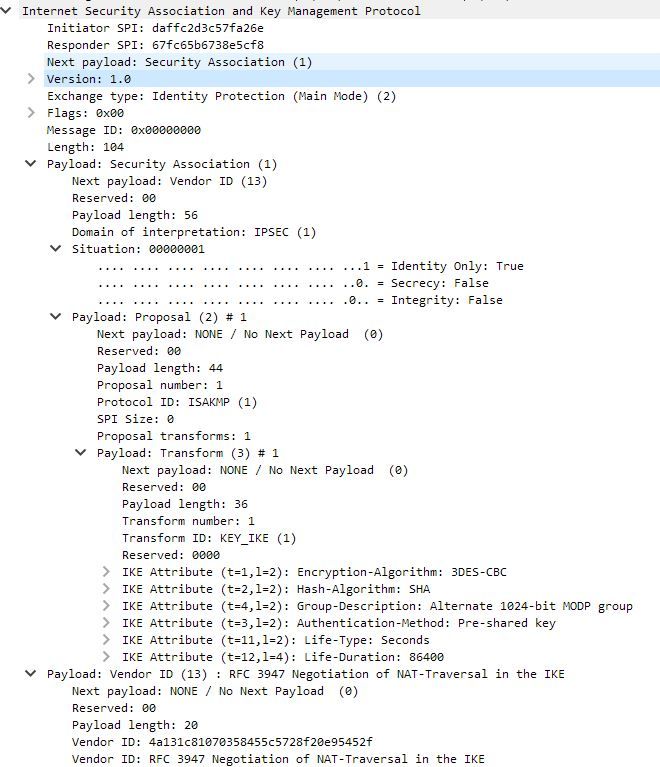
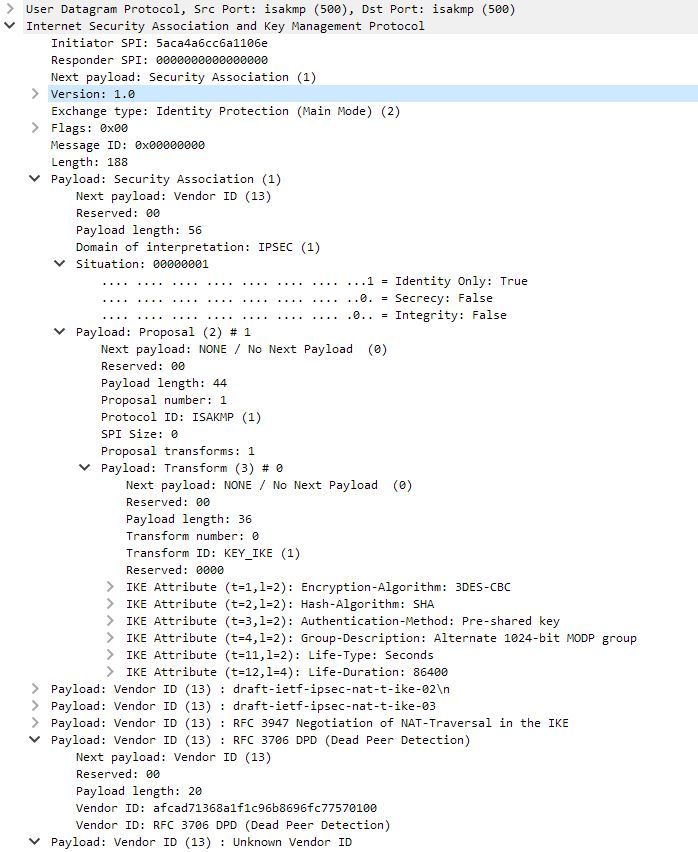
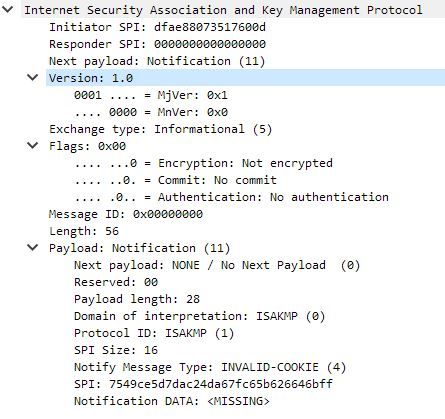
thanks for your advise. I get the capture. But due to company rules, I am not sure if I can send it to you. Therefore I decided to make snapshots and sent them here.
As I see it is always busy in the main mode. I can not proceed much. I am able to make a successful data session but the traffic sent to the tunnel is totally dropped.
I checked the ping as you proposed. ping to customer Barracuda works, it is reachable.
My router is this one
Cisco IOS XE Software, Version 16.09.05
Cisco IOS Software [Fuji], ASR1000 Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 16.9.5, RELEASE SOFTWARE (fc1)
thanks alot for your support, regards, Selcuk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2021 06:54 AM
yes I can see the SPI are building and the phase 1 control plane data in action.
could you please get more debug and upload them and change the public ip addresses. from the logs could you confirm where you failing your tunnel MM-5?? I beleive you must see the DH key exchange (and all the proposals) could you please confirm this?
could you please run these command and share the output.
show crypto isakmp sa detail
show eli
debug platform condition ipv4 x.x.x.x
debug crypto isakmp
debug crypto ipsec
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide