- Cisco Community
- Technology and Support
- Security
- VPN
- Re: One SAML for 2 AnyConnect profiles
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
One SAML for 2 AnyConnect profiles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 02:10 AM
Hi,
I have Firepower 1140 managed by FDM with RA-VPN. I configured SAML server with Azure AD.
Everything is working but only in one profiles. When I try to add SAML server for second profile I get an error:
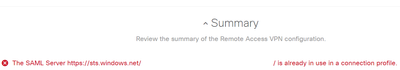
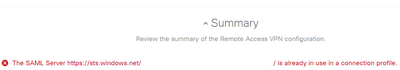
The SAML Server is already in use in a connection profile
It's possible to add one SAML server for more than 1 connection profiles?
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 03:42 AM
- FYI : https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvz40586
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 12:38 PM
In this case bug is resolved in version 7.3 - I updated FTD to version 7.3 but still get an error.
I have 2 SAML Servers with the same IDP URL. In Azure I have 2 Enterprise Aplication with different metadata.
When I try to add new SAML Server (different name) I get an error:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 01:57 AM
The two enterprise applications in Azure should have unique URLs. Trying to reuse a single URL will always result in the error you cited, no matter what version of FTD or management type (local with FDM or remote with FMC or cdFMC).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 02:07 AM - edited 01-31-2023 02:09 AM
No, the IdP URL is my Azure AD tenant URL. The URLs are the same for each enterprise application. In the CSCvz40586 error, this problem was supposed to be solved. I've currently set up over 10+ profiles with the same LDAP server and all is working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 05:20 AM - edited 01-30-2023 05:21 AM
The configuration on the iDP side (Azure in your case) relies on the metadata from Firepower that is specific to a given tunnel-group (also know ans a profile). A new profile will have different metadata.
You can create a second app instance in Azure tied to the second profile. Then add it as a second SAML server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 03:36 AM
Hey,
I have the same issue, we created another instance of cisco anyconnect in Azure but the links for Azure AD identifier is the same - because the tenant is the same
So the new instance doesn't help here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 03:56 AM
I created second app in Azure - only matadata from Firepower is different. Entity ID and login/logout URLs is the same.
I try add second SAML server in FDM - with different name but the same Entity ID and login/logout URLs.
I can save this and deploy, but if I trying to change authentication methods in second tunnel I have same error:
The SAML Server https://sts.windows.com/xxxxxxxx/ is already in use in a connection profile
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 02:14 AM
Hi,
I don't have FDM-managed device next to me, so I can't verify that it is the same as via FMC or as on ASA.
In general, you don't need to create another SAML IDP on FMD (after all, it is indeed same, for multiple applications). On ASA/FTD side, there will be only one SAML IDP created, while on Azure side you'll have multiple applications (as each one will have unique assertion consumer service URL, where tunnel-group is different). On tunnel-group, you'll need to reference this same unique SAML IDP, which means that under multiple tunnel-groups you are using same IDP.
However, since Azure by default generates separate certificate for each application (and on ASA side, since it will be only one IDP, so you can have only one certificate attached), you'll need to generate certificate externally and to upload it under each Azure app that you'll use for this VPN.
Kind regards,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 11:55 AM
Hi,
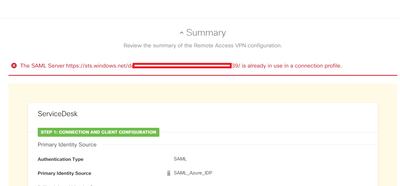
So I deleted all SAML servers on FDM. I created one SAML server with custom certificate - this certificate I added to two enterprise apps in Azure. For one RA VPN profile it's working but, when I trying to add this same SAML server for primary identity source to second profile I got this.
I tried everything but still SAML is working for only one profile - no matter which one...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2023 10:08 AM
I have a Secure Firewall running 7.3 managed with FDM and have found a workaround to get 2 VPN Profiles working with SAML to 2 Enterprise Applications in the same Azure AD tenant. When creating the second VPN Profile, create a second SAML Server Identity Source (I call it 'Dummy' at this stage) with junk Entity ID, Sign In, & Sign Out URLs (I use https://tbd). Set other settings as required (e.g. the same IdP certificate assigned to all Enterprise Applications needs to be selected as mentioned before). Using junk URLs allows FDM to create the second VPN Profile, double-check all the parameters in the VPN Profile are correct because amending them after the end of this process will encounter the bug again. Deploy this config. Now go back to the 'Dummy' SAML Server, give it a more meaningful name and edit the URLs, entering the correct values from Azure. You should be able to make this edit and deploy this without encountering the bug. You end up with 2 SAML Servers configured which are essentially identical other than the name (e.g. using same URLs & certificates) but FDM seems happy with this if you follow this process, and the VPNs work. You can make edits to the Group Policies OK with this configuration in place, but any attempts to Edit the VPN Profiles will encounter the bug, and you would have to revert to the Dummy stage and then repeat the process. This obviously is workable with 2 VPN Profiles but won't scale.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2023 05:08 AM
That's working so good! This is exactly what we need!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide