- Cisco Community
- Technology and Support
- Security
- VPN
- Private IP addressing not traversing IPSEC VPN tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Private IP addressing not traversing IPSEC VPN tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2022 04:50 AM
Hello Everyone,
I have built an IPSEC point-to-point VPN tunnel across the WAN using to 3560cx switches. The tunnel successfully forms across the WAN however, I cannot ping from my inside private network to the other inside private network. Any suggestions? Config posted below:
switch 1 provision ws-c3560cx-12pd-s
system mtu routing 1500
!
!
!
!
ip routing
!
ip dhcp pool SECRET
network 192.168.100.0 255.255.255.252
default-router 192.168.100.1
!
!
ip domain-name *.net
!
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-1745811712
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1745811712
revocation-check none
rsakeypair TP-self-signed-1745811712
!
!
crypto pki certificate chain TP-self-signed-1745811712
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 31373435 38313137 3132301E 170D3232 31303237 31343038
35345A17 0D333030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 37343538
31313731 3230819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100DD8E 9D4BF256 49CB8CB0 2D5B5457 83A19A77 DEBE3E1E 761EB606 71FE5E1B
CC30CED1 55EF8108 567D48D1 433D76BA D21BCB62 2DB58970 987C5C32 03D2B801
04A57F3A 0AB13F85 CEC04DC8 460F398D 157D53D4 DFBBFC21 E4C262FA A0617F52
2761DEBB A86C4581 61D12D65 A6883FE3 9CA9450B 9C401434 D570A5D4 257C90A4
19630203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 14AF1CAA 59719178 DE595BCA 697E272A D7FAEAB4 C6301D06
03551D0E 04160414 AF1CAA59 719178DE 595BCA69 7E272AD7 FAEAB4C6 300D0609
2A864886 F70D0101 05050003 81810047 0D8A8EFA 6152352D FED38D99 8F86421E
366BCAFB E371E5CF 019AA525 2EE46C3B B7D65A36 FFB3ED13 CE16DFC8 0A0A8192
A5E22E2E CCABA39D 0ADFB8BB D26468B8 061EAF03 17A9A34E 71EEFC16 D7657CF2
E68F9F55 B087D475 E128A8E3 D4418A8F 34818847 E837C73C 37E12A57 23CD3DDC
220B589C D37B59A8 3A8B1AEF 45C755
quit
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
crypto ikev2 proposal MY-IKEv2-PROPOSAL
encryption aes-cbc-256
integrity sha512
group 24
!
crypto ikev2 policy MY-IKEv2-POLICY
match fvrf any
proposal MY-IKEv2-PROPOSAL
!
crypto ikev2 keyring MY-KEY
peer REMOTE_ROUTER
address 129.*
identity fqdn *.NET
pre-shared-key local *
pre-shared-key remote *
!
!
!
crypto ikev2 profile MY-IKEv2-PROFILE
match identity remote fqdn *.NET
identity local fqdn *.NET
authentication local pre-share
authentication remote pre-share
keyring local MY-KEY
!
!
vlan internal allocation policy ascending
!
!
!
!
!
crypto ipsec transform-set TFORM esp-aes 256 esp-sha512-hmac
mode tunnel
crypto ipsec df-bit clear
!
crypto ipsec profile MY-IPSEC-PROFILE
set transform-set TFORM
set ikev2-profile MY-IKEv2-PROFILE
!
!
!
!
!
!
interface Loopback0
ip address 150.1.1.1 255.255.255.0
downshift disable
!
interface Tunnel1
ip address 172.0.100.2 255.255.255.252
downshift disable
tunnel source GigabitEthernet1/0/1
tunnel mode ipsec ipv4
tunnel destination 129.*.*.*
tunnel protection ipsec profile MY-IPSEC-PROFILE
!
interface GigabitEthernet1/0/1
no switchport
ip address dhcp
!
interface GigabitEthernet1/0/2
switchport access vlan 10
!
interface GigabitEthernet1/0/3
switchport access vlan 10
!
interface GigabitEthernet1/0/4
switchport access vlan 10
!
interface GigabitEthernet1/0/5
switchport access vlan 10
!
interface GigabitEthernet1/0/6
switchport access vlan 10
!
interface GigabitEthernet1/0/7
switchport access vlan 10
!
interface GigabitEthernet1/0/8
switchport access vlan 10
!
interface GigabitEthernet1/0/9
switchport access vlan 10
!
interface GigabitEthernet1/0/10
switchport access vlan 10
!
interface GigabitEthernet1/0/11
switchport access vlan 10
!
interface GigabitEthernet1/0/12
switchport access vlan 10
!
interface GigabitEthernet1/0/13
!
interface GigabitEthernet1/0/14
!
interface GigabitEthernet1/0/15
!
interface GigabitEthernet1/0/16
!
interface TenGigabitEthernet1/0/1
!
interface TenGigabitEthernet1/0/2
!
interface Vlan1
no ip address
!
interface Vlan10
description INSIDE
ip address 192.168.100.1 255.255.255.0
!
!
router eigrp 15
network 150.0.0.0 0.0.0.255
network 160.0.0.0 0.0.0.255
network 172.0.100.0 0.0.0.255
passive-interface Vlan10
eigrp stub connected summary
!
ip forward-protocol nd
!
ip http server
ip http banner
ip http secure-server
ip route 192.168.200.0 255.255.255.252 Tunnel1
ip ssh version 2
!
!
!
!
!
line con 0
line vty 0 4
login local
transport input ssh
line vty 5 15
login
transport input ssh
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2022 05:02 AM
@gunnydaman I wasn't even aware the 3560cx switches could do IPSec!
I see you've got EIGRP configured, is an adjacency formed and routes learnt on both peers?
Please run "show crypto ipsec sa" and check the encaps|decaps counters to see if they are decreasing, provide the output for us to review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2022 06:47 AM - edited 11-10-2022 06:49 AM
So, It is very interesting. I can ping the gateway across the tunnel but not the connected machines.
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Switch#ping 192.168.200.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.200.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms
Switch#ping 192.168.200.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.200.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Switch#sh crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 129.*.*.*/500 129.*.*.*/500 none/none READY
Encr: AES-CBC, keysize: 256, Hash: SHA512, DH Grp:24, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/1141 sec
IPv6 Crypto IKEv2 SA
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.0.100.1 Tu1 14 00:19:23 10 1494 0 5
172.0.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.0.100.0/30 is directly connected, Tunnel1
L 172.0.100.2/32 is directly connected, Tunnel1
192.168.100.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.100.0/24 is directly connected, Vlan10
L 192.168.100.1/32 is directly connected, Vlan10
S 192.168.200.0/24 is directly connected, Tunnel1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2022 06:48 AM - edited 11-10-2022 06:54 AM
Forgot to include EIGRP
Switch#sh ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(15)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.0.100.1 Tu1 10 00:28:27 10 1494 0 5
Switch#sh ip eigrp 15 topology
EIGRP-IPv4 Topology Table for AS(15)/ID(150.1.1.1)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 160.1.1.0/24, 1 successors, FD is 27008000
via 172.0.100.1 (27008000/128256), Tunnel1
P 172.0.100.0/30, 1 successors, FD is 26880000
via Connected, Tunnel1
P 150.1.1.0/24, 1 successors, FD is 128256
via Connected, Loopback0
Changed networks too:
router eigrp 15
network 150.1.1.0 0.0.0.255
network 160.1.1.0 0.0.0.255
network 172.0.100.0 0.0.0.255
network 172.0.200.0 0.0.0.255
passive-interface Vlan10
eigrp stub connected summary
!
ip forward-protocol nd
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2022 06:56 AM - edited 11-10-2022 07:21 AM
@gunnydaman so no you do have an EIGRP routes in the routing table, but what about the peer? What is in the peers routing table?
What about the output of "show crypto ipsec sa"?
Can you provide the configuration of the peer device
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2022 07:04 AM
Switch#sh crypto ipsec sa
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 129.*.*.*
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 129.*.*.* port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 549, #pkts encrypt: 549, #pkts digest: 549
#pkts decaps: 543, #pkts decrypt: 543, #pkts verify: 543
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 129.*.*.*, remote crypto endpt.: 129.*.*.*
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x11693945(292108613)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x537697D8(1400281048)
transform: esp-256-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 4, flow_id: 4, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4172127/1143)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x11693945(292108613)
transform: esp-256-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 3, flow_id: 3, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4172133/1143)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2022 07:39 AM - edited 11-10-2022 11:50 AM
So I moved everything to EIGRP and my endpoints still can't reach each other....
hostname Switch1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
clock timezone EET 2 0
!
ip cef
!
ip dhcp pool SECRET
network 192.168.100.0 255.255.255.0
default-router 192.168.100.1
!
!
no ipv6 cef
ipv6 multicast rpf use-bgp
!
!
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
crypto ikev2 proposal MY-IKEv2-PROPOSAL
encryption aes-cbc-256
integrity sha512
group 24
!
crypto ikev2 policy MY-IKEv2-POLICY
match fvrf any
proposal MY-IKEv2-PROPOSAL
!
crypto ikev2 keyring MY-KEY
peer REMOTE-ROUTER
address 129.*.*.*
identity fqdn *
pre-shared-key local *
pre-shared-key remote *
!
!
!
crypto ikev2 profile MY-IKEv2-PROFILE
match identity remote fqdn *
identity local fqdn *
authentication local pre-share
authentication remote pre-share
keyring MY-KEY
!
!
vlan internal allocation policy ascending
!
!
!
!
crypto ipsec transform-set TFORM esp-aes 256 esp-sha512-hmac
crypto ipsec df-bit clear
!
crypto ipsec profile MY-IPSEC-PROFILE
set transform-set TFORM
set ikev2-profile MY-IKEv2-PROFILE
!
!
!
!
!
!
!
interface Loopback0
no shutdown
ip address 150.1.1.1 255.255.255.0
!
interface Tunnel1
no shutdown
ip address 172.0.100.2 255.255.255.252
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination 129.*.*.*
tunnel protection ipsec profile MY-IPSEC-PROFILE
!
interface Ethernet0/0
no shutdown
no switchport
ip address 129.*.*.*
duplex auto
!
interface Ethernet0/1
no shutdown
switchport access vlan 10
switchport mode access
duplex auto
!
interface Ethernet0/2
no shutdown
switchport access vlan 10
switchport mode access
duplex auto
!
interface Ethernet0/3
no shutdown
switchport access vlan 10
switchport mode access
duplex auto
!
interface Vlan10
no shutdown
ip address 192.168.100.1 255.255.255.0
!
!
router eigrp 15
network 150.1.1.0 0.0.0.255
network 160.1.1.0 0.0.0.255
network 172.0.100.0 0.0.0.255
network 172.0.200.0 0.0.0.255
network 192.168.100.0
network 192.168.200.0
passive-interface Vlan10
!
!
no ip http server
!
ip route 129.*
!
!
!
!
control-plane
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
!
end
Switch#sh crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 129.*.*.*/500 129.*.*.*/500 none/none READY
Encr: AES-CBC, keysize: 256, Hash: SHA512, DH Grp:24, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/4039 sec
IPv6 Crypto IKEv2 SA
Switch#sh crypto ipsec sa
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 129.*.*.*
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 129.*.*.* port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 976, #pkts encrypt: 976, #pkts digest: 976
#pkts decaps: 980, #pkts decrypt: 980, #pkts verify: 980
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 129.*.*.*, remote crypto endpt.: 129.*.*.*
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x5C1BE410(1545331728)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xCCEB0CC3(3437956291)
transform: esp-256-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 5, flow_id: 5, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4198614/2855)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x5C1BE410(1545331728)
transform: esp-256-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 6, flow_id: 6, sibling_flags 80000040, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4198615/2855)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
Switch#
Switch#
Switch#
Switch#
Switch#sh rou
Switch#sh ip ei
Switch#sh ip eigrp ne
Switch#sh ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(15)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.0.100.1 Tu1 11 00:03:53 26 1494 0 13
Switch#
Switch#sh ip eigrp topology
EIGRP-IPv4 Topology Table for AS(15)/ID(150.1.1.1)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 192.168.200.0/24, 1 successors, FD is 26880256
via 172.0.100.1 (26880256/2816), Tunnel1
P 192.168.100.0/24, 1 successors, FD is 2816
via Connected, Vlan10
P 160.1.1.0/24, 1 successors, FD is 27008000
via 172.0.100.1 (27008000/128256), Tunnel1
P 172.0.100.0/30, 1 successors, FD is 26880000
via Connected, Tunnel1
P 150.1.1.0/24, 1 successors, FD is 128256
via Connected, Loopback0
Switch#
Switch#
Switch#
Switch#
Switch#ping 192.168.200.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.200.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms
Switch#ping 192.168.200.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.200.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2022 10:32 AM
first to check such as these tunnel you need to specify source of ping
if you not specify the source then the SW will use tunnel source and that not never build IPSec.
so what you need is
ping <remote LAN> source <local LAN>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 06:54 AM - edited 11-14-2022 06:54 AM
Sourcing the IP did not work either when I attempt to ping an endpoint. However, I can ping the VLAN interface IP which is 192.168.200.1. But when I ping a laptop that has the IP address 192.168.200.2...no dice. Also, end points can't reach one another across the tunnel either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 07:15 AM
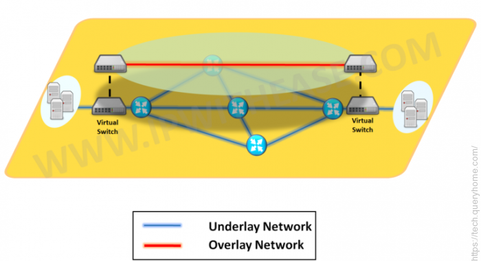
there are two layer I will talk about overlay network which as I see reach via EIGRP
interface Tunnel1
no shutdown
ip address 172.0.100.2 255.255.255.252
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination 129.*.*.*
tunnel protection ipsec profile MY-IPSEC-PROFILE
!
router eigrp 15
network 150.1.1.0 0.0.0.255
network 160.1.1.0 0.0.0.255
network 172.0.100.0 0.0.0.255
network 172.0.200.0 0.0.0.255 <<- first what is this ?? are you use different IP subnet for far end ??
network 192.168.100.0
network 192.168.200.0 <<- delete this since it represent remote LAN not your local LAN
passive-interface Vlan10
no autosummary <<- add this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 10:40 AM
Still no dice. I am thinking these 3560cx switches just don't do VPNs well. Going to get some routers instead.
Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 10:45 AM - edited 11-14-2022 10:52 AM
@gunnydaman well the datasheet for the 3560cx makes no mention of support for IPSec VPN. https://www.cisco.com/c/en/us/products/collateral/switches/catalyst-3560-cx-series-switches/datasheet-c78-733229.html
The only switch I know that does support IPSec VPN is the new-ish Catalyst 9300-X
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 10:50 AM
Yes as @Rob Ingram mention I dont think SW support IPsec but it can support GRE (you can try remove the IPSec Profile from tunnel).
anyway it better use Router.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide