- Cisco Community
- Technology and Support
- Security
- VPN
- Re: RAVPN - Allow local (LAN) access - 1010 using FDM
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2023 07:03 AM
Hi all,
I have a client that needs to tunnel all traffic from VPN clients to reach the internet using the public IP from the office.
This works - BUT some of the VPN clients need access to their printer on their local network.
I have tried to follow this guide, and correct for FDM and not ASA:
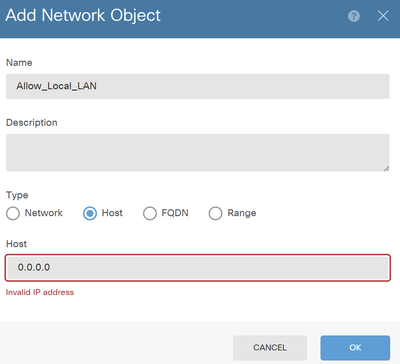
https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/70847-local-lan-pix-asa.html When I get to the part of creating an object with the IP of 0.0.0.0/32, the FDM is not having it - and here I am stuck.
I've searched around but can't find much info on how to fix this problem (not just my object problem, but my entire challenge).
Does anyone have a good idea on how I can solve this challenge?
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2023 07:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2023 07:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2023 07:27 AM
Tested and working!
My local lan is now on the non-secured routers list.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2023 07:24 AM
Split Tunneling—Enable split-tunneling to allow users access to their local networks or the Internet directly at the same time they are using a secure VPN tunnel. Keep split-tunneling disabled for a more secure VPN connection. If you enable split tunneling, you must also select the network objects that represent internal networks remote users will be accessing in the Inside Networks list. The networks list must contain the same IP types as the address pools you are supporting. For any networks outside the ones specified, the user's ISP gateway is used for transmitting traffic.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide