- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Site to Site tunnel - Allow VPN clients to access the other
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2011 07:10 AM
Hi
How do i get this to work?
I want to allow the VPN clientens connecting into the Cisco ASA to access the 10.50.50.0 network.
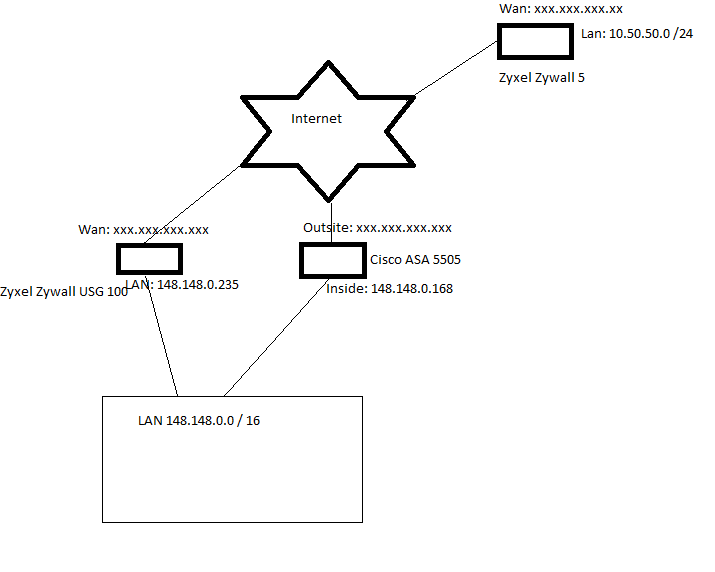
Infomation about the network:
I have a Site to Site IPSec VPN connection that the Zywall 5 and USG 100 makes(148.148.0.0 and 10.50.50.0). Working fine both ways.
I have the Cisco ASA for VPN clients, clients gets a 10.210.210.0 /24 ip-adresse, and its working fine for accessing the 148.148.0.0 /16 network.
The 148.148.0.235 is the main firewall/router for the 148.148.0.0 network.
I have created a static route in the 148.148.0.235, telling that for access to the 10.210.210.0 network goto 148.148.0.168.
I have created a static route in the 148.148.0.168, telling that for access to the 10.50.50.0 network goto 148.148.0.235(I can ping 10.50.50.1 from the Cisco box)
I have created a secound site to site on the Zywall 5 and USG 100 that tunnels the 10.50.50.0 and 10.210.210.0.
In the Cisco ASA splittunneling i have allowed access to the 148.148.0.0 /16 network and the 10.50.50.0 /24 network.
When i open up the VPN client and connects to the network, and try to ping the 10.50.50.0 network i am getting the following error:
(Here i am trying to ping 10.50.50.1)
5 Sep 11 2011 12:36:09 305013 10.50.50.1 Asymmetric NAT rules matched for forward and reverse flows; Connection for icmp src outside:10.210.210.34 dst inside:10.50.50.1 (type 8, code 0) denied due to NAT reverse path failure
I have try to make different NAT rules, but it dont change a thing.
Can any help me, what to do, to make it working?
Thanks.
Simon
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2011 08:24 AM
hi ,
add this :
nat (inside,outside) source static Vejle Vejle destination static obj-10.210.210.0 obj-10.210.210.0
and let me know if it works
HTH
Mohammad.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2011 07:43 AM
Hi Simon ,
thanks for posting this here .
you have done most of the job , can you please post your NAT configuration here since that NAT RPF is responsible for dropping the packet !
cheers !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2011 07:52 AM
Here is the full conf, some parts are removed(Ip-adresses and secrets)
ASA Version 8.3(1)
!
hostname ciscoasa
domain-name test.local
enable password xxxxxxxxxxxxxx encrypted
passwd xxxxxxxxxxxxxxx encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 148.148.0.163 255.255.0.0
ospf cost 10
!
interface Vlan2
nameif outside
security-level 0
ip address xxx.xxx.xxx.xxx xxx.xxx.xxx.xxx
ospf cost 10
!
interface Vlan3
shutdown
nameif dmz
security-level 50
ip address dhcp
ospf cost 10
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
boot system disk0:/asa831-k8.bin
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns server-group DefaultDNS
domain-name test.local
object network obj-148.148.0.0
subnet 148.148.0.0 255.255.0.0
object network obj-10.210.210.0
subnet 10.210.210.0 255.255.255.0
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network Vejle
subnet 10.50.50.0 255.255.255.0
object network VPN
subnet 10.210.210.0 255.255.255.0
description VPN
access-list Test_VPN_splitTunnelAcl standard permit 148.148.0.0 255.255.0.0
access-list Test_LAN_splitTunnelAcl standard permit 148.148.0.0 255.255.0.0
access-list Test_VPN_splitTunnelAcl_1 standard permit 148.148.0.0 255.255.0.0
access-list Test_VPN_splitTunnelAcl_2 standard permit 148.148.0.0 255.255.0.0
access-list Test_VPN_splitTunnelAcl_2 remark Vejle
access-list Test_VPN_splitTunnelAcl_2 standard permit 10.50.50.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 148.148.0.0 255.255.0.0 10.210.210.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 10.50.50.0 255.255.255.0 10.210.210.0 255.255.255.0
pager lines 24
mtu inside 1500
mtu outside 1500
mtu dmz 1500
ip local pool Test_VPN_IP 10.210.210.1-10.210.210.254 mask 255.255.255.0
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-631.bin
no asdm history enable
arp timeout 14400
nat (inside,any) source static obj-148.148.0.0 obj-148.148.0.0 destination static obj-10.210.210.0 obj-10.210.210.0
!
object network obj_any
nat (inside,outside) dynamic interface
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx 255
route inside 10.50.50.0 255.255.255.0 148.148.0.235 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 148.148.0.0 255.255.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map outside_dyn_map 20 set pfs group1
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp ipsec-over-tcp port 10000
ssh timeout 5
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy Test_VPN internal
group-policy Test_VPN attributes
wins-server none
dns-server value xxx.xxx.xxx.xxx xxx.xxx.xxx.xxx
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Test_VPN_splitTunnelAcl_2
default-domain value Test.net
split-dns value Test.net
tunnel-group Test_VPN type remote-access
tunnel-group Test_VPN general-attributes
address-pool Test_VPN_IP
authentication-server-group Test
default-group-policy Test_VPN
tunnel-group Test_VPN ipsec-attributes
pre-shared-key XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
!
!
prompt hostname context
Cryptochecksum:ef40a92065ff3064a61b9872bacd9abe
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2011 08:24 AM
hi ,
add this :
nat (inside,outside) source static Vejle Vejle destination static obj-10.210.210.0 obj-10.210.210.0
and let me know if it works
HTH
Mohammad.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2011 11:14 AM
Works great
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2011 11:22 AM
thanks for the confirmation
anytime mate!!!!!!!!!!!!!!!!!!!!!!!!!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2012 08:38 AM
Hello. I am working on getting site to site vpn tunnel built between a 2811 router and UC-540. I have some issues with defining access-lists. The private ip's on both the ends are in same range. Not sure on how to define access-lists and got an error while defining these access-lists.
2811 privae ip's- 10.1.0.0 0.0.255.255, 192.168.0.0 0.0.255.255
UC-540 private ip's- 10.1.1.0 0.0.0.255 192.168.10.0 0.0.0.255
Ho can i define valid access-lists in this case.
As of now i tried doing this
ip access-list extended VPN_To_XXXXX_Allowed
permit ip 192.168.0.0 0.0.255.255 10.1.1.0 0.0.0.255
permit ip 10.1.0.0 0.0.255.255 10.1.1.0 0.0.0.255
permit ip 192.168.0.0 0.0.255.255 192.168.10.0 0.0.0.255
permit ip 10.1.0.0 0.0.255.255 192.168.10.0 0.0.0.255
permit ip 10.1.1.0 0.0.0.255 192.168.0.0 0.0.255.255
permit ip 10.1.1.0 0.0.0.255 10.1.0.0 0.0.255.255
permit ip 192.168.10.0 0.0.0.255 192.168.0.0 0.0.255.255
permit ip 192.168.10.0 0.0.0.255 10.1.0.0 0.0.255.255
deny ip any any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2013 07:26 PM
Can anyone please tell me the order of operation for these:
inbound ACL, NAT, interesting traffic, routing, outbound ACL.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide