- Cisco Community
- Technology and Support
- Security
- VPN
- Split tunneling by adding static routing entries on Cisco VPN client workstations
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Split tunneling by adding static routing entries on Cisco VPN client workstations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2015 06:40 AM
Hi,
Our users have Windows 7 SP1 workstations with Cisco Systems VPN Client Version 5.0.07.0440 installed. The local desktops and local networks are managed by our local IT. And we use the Cisco VPN client to connect to our partner's internal network. The VPN server is managed by the partner which is out of our control. Once the users connect to the VPN and get into the partner's internet network, they are not able to access our local network any more unless disconnecting the VPN. I tried to add static routing entries on our local desktops, but it's not working. Even the default gateway of local connectivity is not working. That means, when I performed tracert to a local network destination or even local default gateway on local desktops, it's showing going via VPN tunnel to the remote network. There is a requirement to access both local network and remote network. Is there a workaround to split tunneling from local desktop perspective? We do not have any control on the partner.
Thanks very much for your help!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2015 08:44 AM
You need to enable the Local LAN access feature in order to accomplish this.
Hope it helps
-Randy-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2015 08:52 PM
Hi Randy,
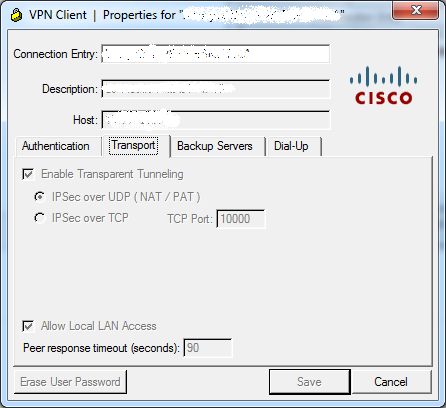
Thanks for your quick reply. I have already enabled "Allow Local LAN Access" on the Cisco VPN client on our local desktops (see 2rd screenshot), and I also added the static routing entries of local networks on local desktops. But it's not working. We do NOT have any control on the partner or ASA firewall.
We also have many other partners in our orgnization. Some of the partners are using Juniper or Microsoft remote access VPN solution. That means some of our local desktops are using Juniper/Microsoft VPN client to connect to these partners by remote access VPN. These partners have also enabled the default gateway on remote network by default. But we do be able to access our local networks by adding the static routing entries of our local networks on our local desktops (e.g. by DHCP option 249 on our local DHCP servers).
In addtional, we have not only one subnet in our local network, but multiple subnets. For example, the desktops are in the local subnet 192.168.1.0/24, but the desktops require to access the server subnet 192.168.0.0/24 for local Domain Controller/print server/etc access while the Cisco VPN client is conneted. I tried to add the static routing entrie for 192.168.0.0/24 on the local desktops, but it's not working. All the traffic went via the VPN tunnel.
Regards,
Jun Gao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2015 12:11 PM
Hi Jun,
As the document point, you need to configure the Local LAN access on the ASA as well with an "exclude-specify" policy under the group-policy. Otherwise the checkbox on the VPN client won't take effect.
A friendly reminder this VPN client is currently out of support and is not compatible with Windows 8 or 10.
http://www.cisco.com/c/en/us/products/collateral/security/vpn-client/end_of_life_c51-680819.html
-Randy-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2015 09:09 PM
Hi Randy,
First of all, thank you very much for your quick reply again. Actually I did check that document. But we do not have any controls on the ASA firewall which is managed by our partner. This is an internal requirement inside our orgnization. It's IMPOSSIBLE to talk with our partner to configure an "exclude-specify" policy on their end for whatever reasons. I'm asking the question here to look for a workaround on our local desktops instead of a solution on our partner's firewall. Actually we have many partners in our orgnization, and we have the workaround with other VPN solutions (e.g. Juniper/Microsoft) for other partners. That means, we can add the static routing entries of our local subnets (e.g. DHCP option 249) on our local desktops to access our local networks as a workaround while we use Juniper or Microsoft VPN client.
Thanks very much for your reminding. We can upgrade the VPN client to the laster version like Cisco AnyConnect. But could this fix my issue?
Thanks,
Jun Gao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2015 05:46 PM
Hi Jun,
This seems to be hard to accomplish due to the limitations of the management part.
If you could give a try to the Anyconnect client , specially if you're using Windows 8 or 10.
Among that, it seems unfortunately we might be hitting a roadblock here for this set up.
Cheers,
-Randy-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2015 07:10 PM
Hi Randy,
Thanks again for your reply. Let me try the latest AnyConnect on the desktops and also try Windows 8 or 10 on a testing machine if I can have the chance. Hope it will work out.
Regards,
Jun Gao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2016 11:31 PM
Hi Randy,
I had installed Windows 10 with the latest AnyConnect and I was going to connect to the VPN. However, the AnyConnect was asking me for second username & password. What is it? I never saw it on Cisco Systems VPN Client in the past. I only saw the VPN client asked me for username and passcode. I tried the same username & passcode, but it didn't work.
Thanks,
Jun Gao


Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide