- Cisco Community
- Technology and Support
- Security
- VPN
- Tunnel Authorize Fail no connection has beenauthorized with policy=PSK
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Tunnel Authorize Fail no connection has beenauthorized with policy=PSK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 09:39 AM
Hello
I have 2 Cisco RV325 Dual Wan router on a site to site VPN
I recently started monitoring the VPN Logs on both devices to try to figure out some disconnections we were having and to be more proactive in thwarting off brute force attempt by blocking IP ranges.
The device at my location is operating perfectly with expected log entries.
The off site device is showing a log entry like the subject of this post ...
VPN Log: packet from 72.142.112.2:27152: [Tunnel Authorize Fail] no connection has been authorized with policy=PSK
I am posting the IP because I am suspecting that this is not actually an attempt by an actual intruder.
I receive this log entry then continuously get the following entry at the rate of 1 per minute which means it is being logged exactly every 10 seconds.
Jan 6 10:43:58 2022 (router name) last message repeated 6 times
I have attempted to block the IP as I have with many others through using the access rules
I set this IP to block all ports from WAN1 and also tried from Anywhere and the logs are still there.
I have tried every suggestion I can find on the web to no avail.
This pollution of the logs makes me think the router is busy with these attempts using processor unnecessarily and possibly causing the connection interruptions. Regardless I want to stop it.
The IP traces to a Park in Laval Quebec so possibly someone is using Public WIFI but then why can't I block it?
Is this an internal bug in the RV325?
had anyone here had something like this and solved it?
Any help would be appreciated.
Since this router is in a remote location I cannot reset it to factory without having someone there ship it to me and then they are without networking for a week before I could get it back to them.
I can provide any details needed to assist me if you ask.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 10:17 PM
Can you share your ACL and interfaces config.? Also, can you confirm that
ACL is applied on the right interface.
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2022 05:27 AM
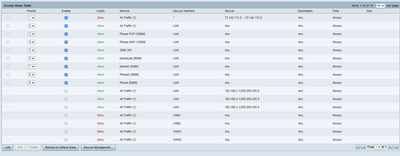
I hope this is what you are asking for.
This is an office with 3 employees with IP Phone system so until I discovered this issue nothing was blocked.
I am not sure what you mean by the wrong interface.
Here is a sample of the log showing normal Site to Site logs and the log in question.
Jan 7 07:17:49 2022 router45ebac VPN Log: [g2gips0] #79: [Tunnel Established] sent QI2, IPsec SA established {ESP=>0xcf749a9f < 0xc19d766c}
Jan 7 07:17:49 2022 router45ebac VPN Log: [g2gips0] #78: [Tunnel Authorize Fail] ignoring Delete SA payload: PROTO_IPSEC_ESP SA(0xc84e16f9) not found (maybe expired)
Jan 7 07:17:52 2022 router45ebac VPN Log: packet from 72.142.112.2:27152: [Tunnel Authorize Fail] no connection has been authorized with policy=PSK
Jan 7 07:18:23 2022 router45ebac last message repeated 2 times
Jan 7 07:19:23 2022 router45ebac last message repeated 6 times
Jan 7 07:20:23 2022 router45ebac last message repeated 6 times
Jan 7 07:21:23 2022 router45ebac last message repeated 6 times
Jan 7 07:22:23 2022 router45ebac last message repeated 6 times
Jan 7 07:22:53 2022 router45ebac last message repeated 3 times
Jan 7 07:23:01 2022 router45ebac VPN Log: [g2gips0] #80: [Tunnel Established] sent AI2, ISAKMP SA established
Jan 7 07:23:03 2022 router45ebac VPN Log: packet from 72.142.112.2:27152: [Tunnel Authorize Fail] no connection has been authorized with policy=PSK
Jan 7 07:23:34 2022 router45ebac last message repeated 3 times
Jan 7 07:24:44 2022 router45ebac last message repeated 7 times
I hope that is the information you need.
I am not versed in the router lingo so please be clear of exactly what information you need if this is not it.
Terry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2022 02:33 PM
There are a couple of things here from your original post. Lets start with the first thing of someone trying to access your public facing VPN. You will not be able to stop this and you will get these logs when they fail. That is a good thing.
Next when you applied an access rule to block the IP range did you select to log the entry (Check documentation https://www.cisco.com/c/en/us/support/docs/smb/routers/cisco-rv-series-small-business-routers/smb4286-access-rules-configuration-on-rv320-and-rv325-vpn-routers.html). You can disable the entry from being logged but it is really not a good security practice to do so. You want to see the failures along with successful attempts. Additionally only apply an ACL to the affected interface. It is bad practice to apply it to all interfaces. this causes each interface to process that rule each time a packet goes through the router eating up resources. You should only apply it to the outside interface in this case.
lastly if users are being disconnected from the VPN there are multiple reasons why and each one will most likely be different. If it is continual problem with a single user then troubleshoot that one user.. Given they are not sitting in a coffee shop using free WIFI while other people have no issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2022 11:14 AM
Keibler
Below is from the link you sent me...
Access Rules
Access rules limit access to the subnetwork by allowing or denying access by specific services or devices identified by their IP address.
I have to disagree with your first statement.
I have Open VPN setup on my Samsung phone so I can quickly access our network securely.
I connected to our network and checked the public IP my phone was using to connect.
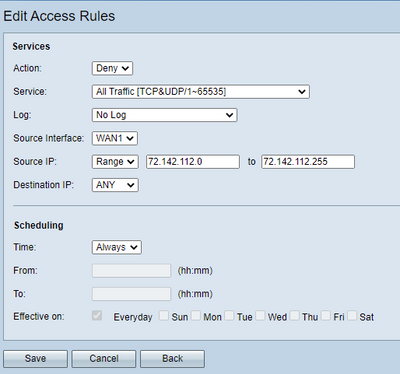
I then created an access rule to deny that IP access to any IP on our network.
I tried to reconnect with my phone and it could not connect.
However I was still able to log into the router admin so it doesn't block that access. I see that the router logs my IP as my ISP's IP so that is why it isn't being blocked.
For blocking WAN access to the router UI I know I can just set it to only be accessed from LAN and if the ACL is blocking the IP they cannot access VPN even with credentials. (which I am considering doing, unfortunately this limits me when VPN is the issue and I need to reboot the router because then I would have to drive to work and physically reboot the router or use another remote access software to control a PC on the network ie TeamViewer)
So this does block the IP from accessing network but not Router Admin (an oversight I hope) how am I supposed to figure out who is logging into the admin from WAN if it only shows the ISP IP address this is unbelievably stupid.
Now You can forget about my disconnecting VPN issue I already fixed that .... It was the ISP that caused the problem but was insisting that it was our router that was at fault. I found what I needed in the logs to prove to them it was not our router then suddenly the problem disappeared. Likely they discovered their issue and corrected it without admitting it.
But in doing this I turned on emailing me the logs from the router and that was when I discovered this IP bombarding our router every 10 seconds.
Please note, if you didn't catch it in my OP, that I have 2 of these routers One in Toronto the other in Montreal I have been able to stop all offending IP's in Toronto Router but not in the Montreal one.
So with that in mind then you should be able to focus on the issue I am presenting.
Before I created the rule to block the IP it is logging attempt every 10 seconds.
After I created the rule for WAN interface from this IP to any IP the log entry still occurs "without the logging checked off on this rule" this doesn't happen on my other router and I have recently blocked another IP on the Montreal router and it doesn't appear in the logs any more but this one still does.
I tried doing an IP range covering this IP - no change
I tried picking from any source * to any destination - no change
I tried deleting and recreating the rule - no change
I really think it is something in the router that is stuck in a loop because what computer or router would be in the middle of a public park trying to access our IP SEC VPN every 10 seconds 24x7 .... really?!?
If I have to I will report the IP to Roger Communications and provide my logs as proof and Rogers will shut them down .... I've done it before ... but I think this is a false positive.
I am really trying to avoid resetting the router to factory and shutting down that office for a week but as I am typing this I am realizing that is likely exactly what I have to do before I will know if it is real or a glitch.
I am still open to any Ideas anyone has on this.
Thanks for your input.
Terry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2022 01:03 PM
Terry,
I looked through the docs for the RV325 and from what I can tell is there is no ACL for the management of the device. The management of the device https://<wan-ip>:<remote-management-port>. Normally a router or firewall has a different ACL for the data and control planes. That is why the VPN is blocked and the management traffic is not. A couple of suggestions I can give you is to 1) Open a TAC case to see if there is a CLI option to modify the management ACL. 2) Change the port number and see if that reduces the amount of hits to the management interface. 3) see if there is a way to put in static routes to route the unwanted traffic to null. This will work on the VPN side for sure but not sure about the management interface. 4) Add a remote machine at the site and only permit management from the LAN address space. VPN in then connect to the remote machine which would have management access to the router.
I did find this solution on another post: Hope it helps
Cisco TAC response:
This would work only if you use a non-HTTPS port, e.g. 5000 and you need to explicitly uncheck the “HTTPS” option under “Firewall” -> “General”. HTTPS remote management would not allow you to configure ACL rules for this type of access. This is a product limitation and we can only provide a workaround.
https://community.cisco.com/t5/small-business-routers/rv325-remote-management-acl/td-p/2682510
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2022 01:41 PM
Keibler
Thanks but that isn't my problem.
The problem is that my VPN log is filled with this fake attempt to access IP SEC VPN.
That's it !! Thanks for all the advice but that's not helping me.
72.142.112.2:27152
Jan 7 07:17:49 2022 router45ebac VPN Log: [g2gips0] #79: [Tunnel Established] sent QI2, IPsec SA established {ESP=>0xcf749a9f < 0xc19d766c}
Jan 7 07:17:49 2022 router45ebac VPN Log: [g2gips0] #78: [Tunnel Authorize Fail] ignoring Delete SA payload: PROTO_IPSEC_ESP SA(0xc84e16f9) not found (maybe expired)
Jan 7 07:17:52 2022 router45ebac VPN Log: packet from 72.142.112.2:27152: [Tunnel Authorize Fail] no connection has been authorized with policy=PSK
Jan 7 07:18:23 2022 router45ebac last message repeated 2 times
Jan 7 07:19:23 2022 router45ebac last message repeated 6 times
Jan 7 07:20:23 2022 router45ebac last message repeated 6 times
Jan 7 07:21:23 2022 router45ebac last message repeated 6 times
Jan 7 07:22:23 2022 router45ebac last message repeated 6 times
Jan 7 07:22:53 2022 router45ebac last message repeated 3 times
Jan 7 07:23:01 2022 router45ebac VPN Log: [g2gips0] #80: [Tunnel Established] sent AI2, ISAKMP SA established
Jan 7 07:23:03 2022 router45ebac VPN Log: packet from 72.142.112.2:27152: [Tunnel Authorize Fail] no connection has been authorized with policy=PSK
Jan 7 07:23:34 2022 router45ebac last message repeated 3 times
Jan 7 07:24:44 2022 router45ebac last message repeated 7 times
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2022 05:56 AM
Terry,
As I stated previously you can choose to not log the ACL hit. Other than that cisco does not provide a way to filter log events without changing the level. If you are concerned about loosing the logs then you have 2 choices. Change the logging buffer size or following best practices by sending your logs to a logging server. If you are relying on only the internal buffer of the router you are not following best practices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2022 06:19 AM
Keibler
I really don't know what to say to you anymore to get you to understand the situation.
I am not trying to stop the log but stop what is causing the log.
You have not made 1 statement that addresses the problem in all the posts you have made so far !!!
I am tired of repeating the question and you are clearly not understanding my question please stop responding to this post so I might be able to get help from someone who will read, understand and answers my question. You obviously do not have any experience with this router. I vote your responses are completely not helpful and worse yet inaccurate. Thanks for wasting my time and yours.
Is there someone else that can assist me that will answer why I cant block this 1 IP when I have blocked many previously in both routers. this 1 IP in this 1 router.
Please answer that question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2022 06:36 AM
Terry,
This will be my last post to ease your pain. However, you cannot stop the public IP from attempting to connect to your router and creating a log unless you either contact your ISP and have them block it or do what I suggested in previous posts. I will leave this up to you. Have a great Cisco Day ;).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2022 11:20 AM - edited 01-14-2022 11:47 AM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2022 12:40 PM
Keibler I thought you said you were done then you post .... You are a piece of work.
I am going to give you 1 last chance to understand the issue.
As you stated that I can create the ACL and not check off the logging checkbox and therefore it will not appear in the any more.
I have done this for every IP range I have blocked and once I do they are no longer in the log just as you said.
BUT this IP appears in the log no matter how I block it I even made a port block for UDP & TCP because it is always the same port and that doesn't keep it out of the log.
ALL THE OTHER IP'S I BLOCKED DO NOT APPEAR IN THE LOG ANY MORE WHY IS THIS DIFFERENT
I have resigned to having to buy another router set it up for the location's PPoE and send it to them to replace theirs with zero down time.
This is the first time I have ever gone to any forum in my 40 years of experience to get help. I go to forums and read the crap people post trying to find my answers but this is the exact reason I have refrained from it and thanks to you I will never post again.
Thank you so much you have your self the worse cisco day possible. You have ruined any chance of someone with actual intelligence helping me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2022 01:04 PM
Terry,
The post you saw come in that I changed to "..." was originally sent from my phone two days ago. For some reason it just showed up now. Since it was no longer relevant and I was unable to delete the post I wiped out the text to keep the confusion down. Please consider opening a TAC case to resolve your issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2022 10:19 AM
Mohammed
Any Ideas yet?
Terry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2022 12:24 PM - edited 02-22-2022 12:24 PM
I got the offending IP address shut down by Rogers ISP today, logs are clear again!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide