- Cisco Community
- Technology and Support
- Security
- VPN
- VPN connection between ASA5520 and RV215w
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN connection between ASA5520 and RV215w
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 04:37 AM
Hello everyone,
I am trying to setup a vpn connection between ASA5520 with 9.1.(3) and rv215w 1.1.0.6
Here is my setup ...
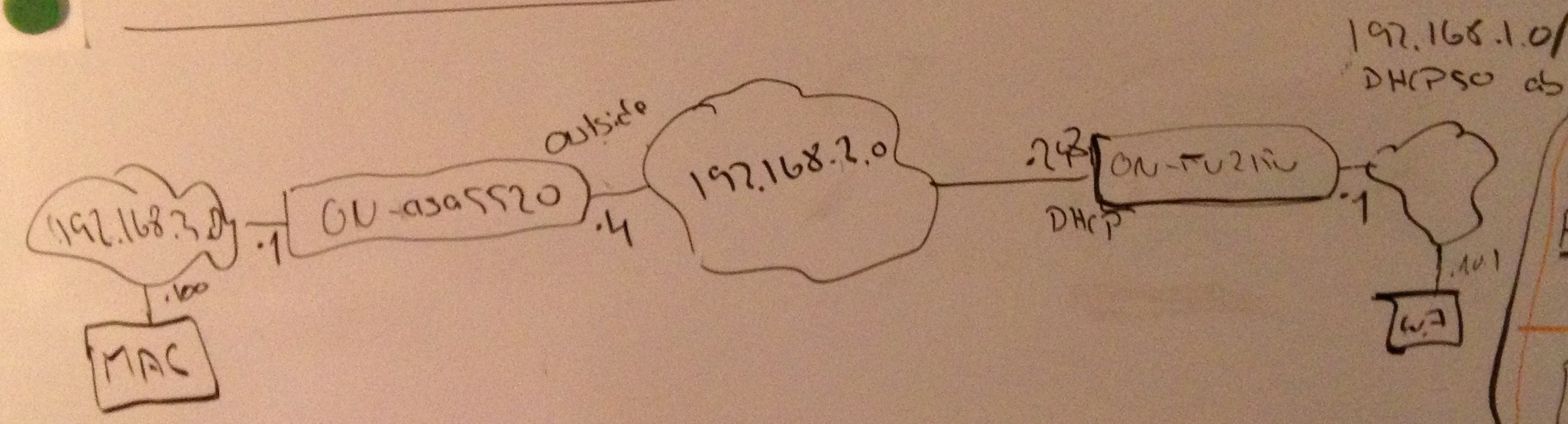
But the vpn connection fails with an error message on ASA.
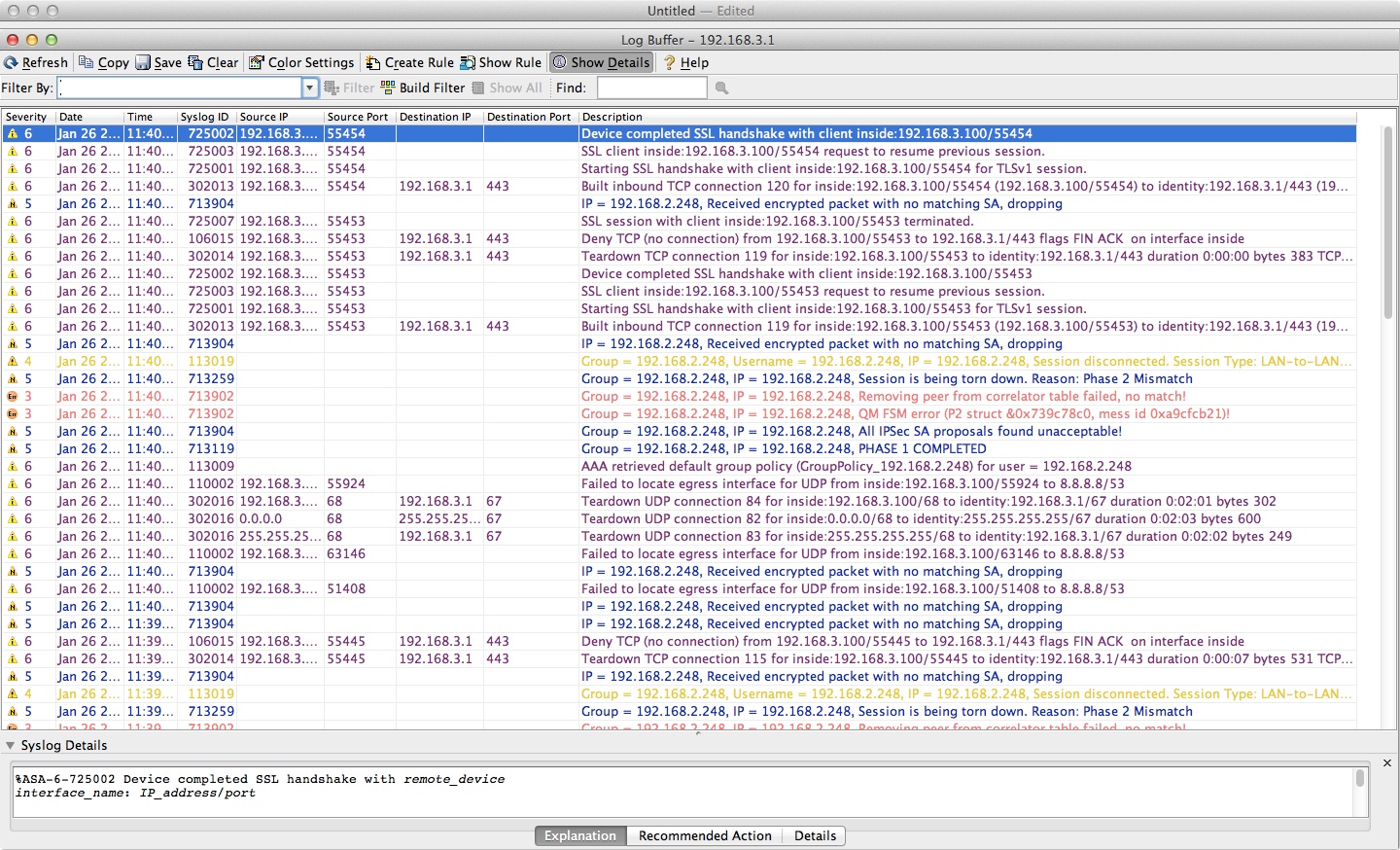
RV215w shows ipsec established but i cannot ping the network behind.
You can find asa-config and show-tech as attachment. I have added also some screenshots from RV215w.
Any hint or help is appreciated.
Cengiz
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 05:54 AM
Hi,
regarding configuration you provided it seems you tried to configure a lot of tunnels because there is huge list of ipsec policy.(10-130)
So question is. Are you trying to configure just this tunnel betwee ASA nad router or want to use more tunnels?
In config I noticed you are using mix of ikev1 and ikev2 next thing what is wrong is on router you are using PFS DH2 but on ASA you are using PFS Group1(DH1).
Also could you please post running-config from router cmd it is better compareable than screenshots.
Thanks,
Best regards,
Jan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 06:15 AM
Jan is absolutely correct, your config has different PFS for phase 2 .
please share the output of following commands from your ASA:
1. show crypto debug-condition
2. show crypto ipsec df-bit
3. show crypto ipsec fragmentation
4. show crypto ipsec sa
5. show crypto ipsec stats
6. show crypto isakmp stats
7. show crypto isakmp sa
8. show crypto isakmp stats
9. show crypto protocol statistics
Also you are using transport mode for all your transform sets and so many transform sets will slow down the phase 2 negotiation :
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
2. Please share the output of the running configuration of router.
3. Please sahre the output of commands from your router:
show crypto ipsec sa
show crypto ipsec sa
show crypto ipsec summary
show crypto ipsec transform-set
show crypto engine connections active
show crypto engine brief
show crypto engine connections
Best Regards
Sachin Garg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2014 07:34 AM
Hello,
thanks a lot for your response ... it really helped. I was able to to setup the site2site tunnel it was just a mismatch
ok ike and ipsec paramters.
Here is now the next challange : )))
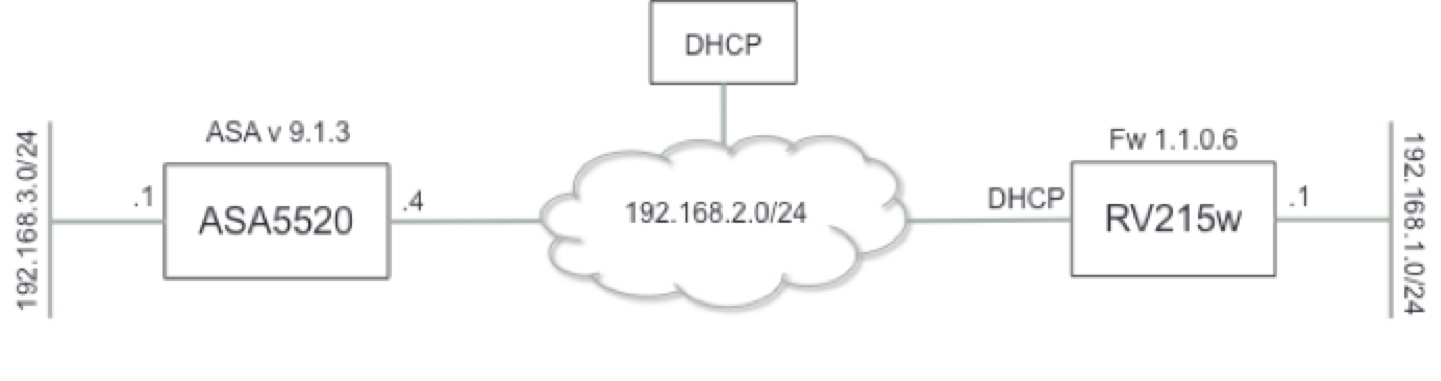
It is the same setup the only change here is outside ip from RV215w which is a dynamic ip.
In this case i need dynamic crypto map for ASA ... do you guys have an example config maybe for me.
What is the easiest way to configure it. Any hints are welcome : )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2014 09:17 AM
Hi Cengiz,
Dynamic CRYPTO maps mostly used in a Remote Access or Client to site VPN because end users working from home can have IP address new every time or like different whcn connect from home or from Internet cafe , hence ASA cant make a fix IP as Peer.
But for site to site also Dynamic Crypto Map can be used but only at one side , else if you use Dynamic crypto map at both ends , both peer will wait for each other to initiate a tunnel Request as the device n this case ASA) configured with Dynamic Crypto map can only REPLY for a tunnel initiation , it can never send tunned initilaization request as it never know the IP address of the peer. Hence never make both device as dynamic crypto map or else they both never initiate and wait for each pther and tunnel will never happen.
The main steps to be configured on the ASA end in order to establish dynamic tunnel:
Phase 1 ISAKMP related configuration
Nat exemption configuration
Dynamic crypto map configuration
The Cisco IOS router has a static crypto map configured because the ASA is assumed to have a static public IP address. Now this is the list of main steps to be configured on the Cisco IOS Router end to establish dynamic IPSEC tunnel.
Phase 1 ISAKMP related configuration
Static crypto map related configuration
!---1. Configure the IPsec transform-set
crypto ipsec transform-set myset esp-des esp-md5-hmac
!
!
!--- 2. Configure the dynamic crypto map. Always rememeber to bind a dynamic crypto map to a blank static crypto map and then call that static crypto map to a ASA OUTSIDE Interface as Dynamic Crypto maps cannot be bind directly to ASA OUTSIDE Interface or say any interface.
crypto dynamic-map MY_DYNAMIC_MAP 1 set transform-set myset
crypto dynamic-map MY_DYNAMIC_MAP 1 set reverse-route
!--- Enable Reverse Route Injection (RRI), which allows the ASA
!--- to learn routing information for connected clients hence the static route will come above defaut route and hence
!... will make the routing decision fast else every time for the other side router dynamic IP , default route have to get a hit but only after checking the entire routing table and when no match then use default route , so to save this entire route matchin process always good to use reverse route enjection so that other side non dynamic crypt peer can insert a static route enrty in ASA.
!--- 2A. Always Bind dynamic crypto map named MY_DYNAMIC_MAP to a static crypto map named STATIC_MAP_CALLING_DYMANIC_MAP using a keyword dynamic in the last
crypto map STATIC_MAP_CALLING_DYMANIC_MAP 10 IPSec-isakmp dynamic MY_DYNAMIC_MAP
!--- 2B.now apply static map on ASA OUTSIDE Interface
crypto map STATIC_MAP_CALLING_DYMANIC_MAP interface outside
!
!--- 3. Configure the phase I ISAKMP policy
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
!
!
!--- 4. Configure the default L2L tunnel group parameters
tunnel-group DefaultL2LGroup IPSec-attributes
pre-shared-key *
Plase rate if you like my post.
Best Regards
Sachin Garg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 05:11 AM
Hi Sachin,
thanks a lot for you detailed answer ... but you probably din'T check my setup what i have send in my last post.
There is no IOS device in my setup.
So my setup is between a Cisco ASA5520 (headend) and a RV215w which is the remote office.
I need config support for the headend (ASA5520) with static IP which has to terminate a site2site connection
coming from RV215w (remote) with a dynamic IP.
Cengiz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 05:33 AM
Hi Cengiz,
please read Sachin reply properly. He just guide you how to configure ASA for dynamic L2L tunnel and it is correct. Because as you say you have DHCP on router side so outside IP of router can change in time and then ASA tunnel have to be configured dynamically to accept IPSEC connection from any IP address(outside interface).
Regards,
Jan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 07:49 AM
Jan,
your are right man ... I was missing the important part. My mistake
I will try to configure it and let you guys know how i proceed !!!
Sorry again.
Cengiz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 09:24 AM
Hi Sachin,
sorry again for the confusion
Your post was really helpful ... I configured everything as you posted, but i am still missing the last part of the puzzle
I am getting following error message on ASDM logging site:
4 Feb 12 2014 17:24:03 713903 Group = 192.168.2.249, IP = 192.168.2.249, Can't find a valid tunnel group, aborting...!
| 4 | Feb 12 2014 | 17:23:23 | 713903 | IP = 192.168.2.249, Header invalid, missing SA payload! (next payload = 4) |
The asa-config and "debug crypto ikev1 255" is attached to this post. I haven't changed the RV215w config its still the same.
I only configured dynamic crypto map on ASA. With static crypto map on ASA the connection was working. I probably have a misconfiguration
and not able to find it out. Would be great if you check the config and debugs.
Thanks in advance,
Cengiz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 09:53 AM
On the end with the static ip, assign the pre-shared key to the DefaultL2L group
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2014 12:44 AM
Hi Sachin
the pre-shared key is assigned to the group:
tunnel-group test02 type ipsec-l2l
tunnel-group test02 general-attributes
default-group-policy GroupPolicy1
tunnel-group test02 ipsec-attributes
ikev1 pre-shared-key *****
Maybe i misunderstood what you mean.
Cengiz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2014 12:55 AM
Have you tried testing the tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2014 12:57 AM
Yes i did but its not working ... i have sent you the debugs in my post before
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2014 01:14 AM
Seems like ASA is not able to fid the tunnel group. Here is another debug output:
ON-asa5520# Feb 13 10:13:20 [IKEv1]Group = 192.168.2.249, IP = 192.168.2.249, Can't find a valid tunnel group, aborting...!
Feb 13 10:13:30 [IKEv1]IP = 192.168.2.249, Header invalid, missing SA payload! (next payload = 4)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 03:16 AM
I fixed the problem !!!
After enabling reverse route injection everything was fine : )
I have a last question regarding scalability ... how many l2l session can i terminate on one dynamic cryptomap/tunnelgroup?
Are there any limits?
Thanks in advance.
Cengiz
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide