- Cisco Community
- Technology and Support
- Security
- VPN
- VPN Connectivity
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 07:48 AM
We currently have a VPN setup for our users when they are on the road or working from home using Cisco AnyConnect. We have the VPN setup on our ASA 5508 Firewall.
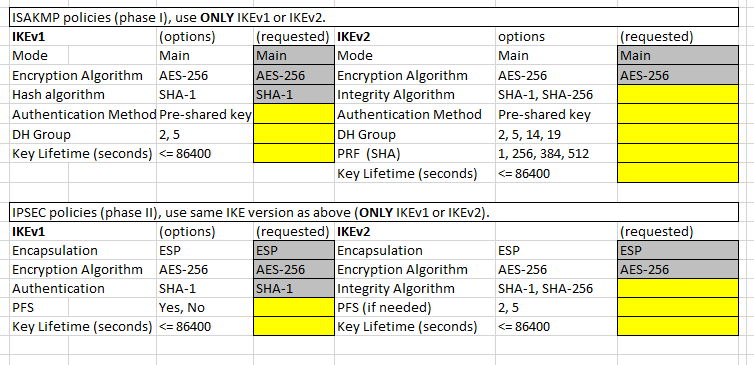
I now have a client that we send data to that needs us to setup a VPN for the connection. I was wondering if there was anyone out there that would be able to help me create the VPN (IKEv1 or IKEv2) and fill out this VPN questionnaire. Thank you in advance!!
Solved! Go to Solution.
- Labels:
-
IPSEC
-
Remote Access
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 01:29 PM
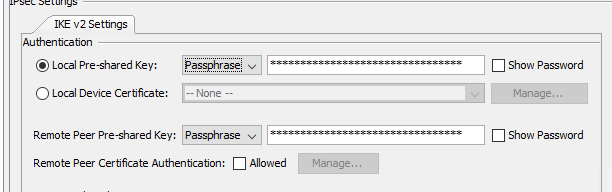
Also wondering about "Local Pre-shared Key" and "Remote Peer Pre-Shared Key". Can those be the same? They are both the same PSK right now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 01:59 PM
Yes the local and remote PSK can be the same. I assume the 3rd party is using the same for both?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 01:58 PM - edited 10-26-2020 01:59 PM
Your debug output above confirms that your ASA and the 3rd party firewall are communicating and attempting to establish the VPN tunnel...if they were to turn on debugs they'd see similar information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 03:26 PM - edited 10-26-2020 03:28 PM
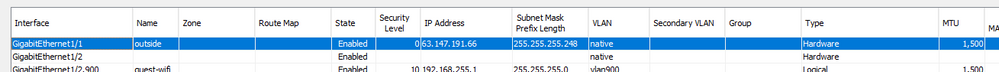
I think the third party made a typo when they configured your public IP address:
crypto map VPN 124 set peer 66.147.191.67
That should read 63.147.191.67, not 66.
Also, is there any reason why they are not using your ASA outside interface IP 63.147.191.66?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 04:35 AM
Thanks for catching that typo Aref!!!
We have Fiber internet so we actually have 5 working IPs. The machine that I am trying to ping the 3rd party from has an IP of 63.147.191.67.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 04:49 AM
You do have appear to have a static NAT for that host using that public IP address. Without the VPN all traffic from the host 10.0.0.3 would be natted behind that public IP address.
The 3rd party needs to setup their VPN to peer with the IP address of your outside interface, which ends .66 - they cannot terminate the VPN on the NAT ip address ending .67.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 05:09 AM
Thanks Rob! I guess I wasn't clear on which IP to use as our "public" IP. I had the 3rd party change our IP to 63.147.191.66. Hopefully, this will fix the issue. I will let you know as soon as I have confirmation that they changed it.
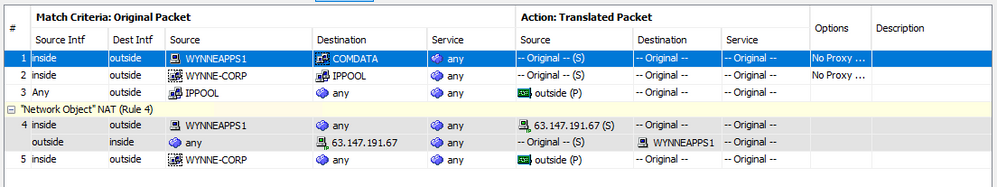
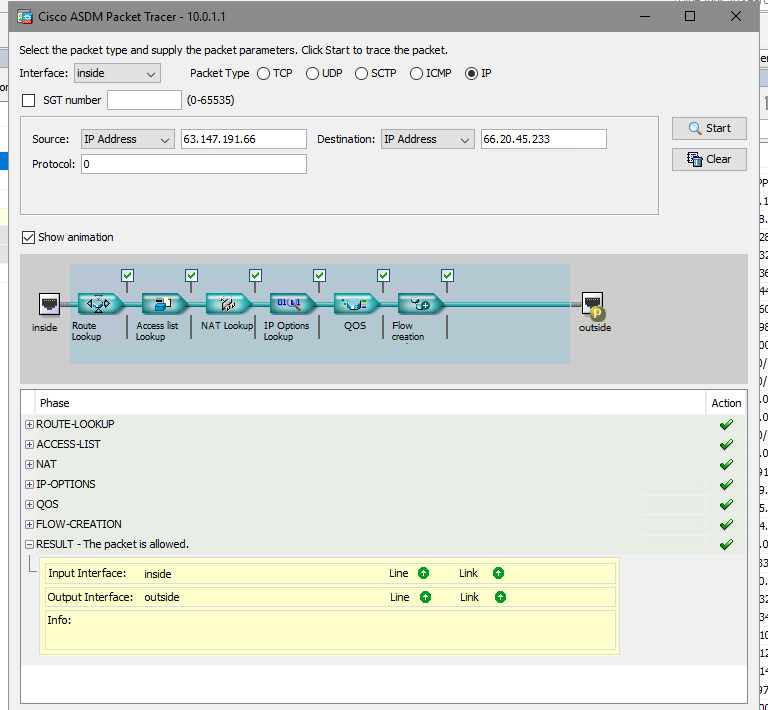
Here is what is setup in ASDM on my ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 05:15 AM
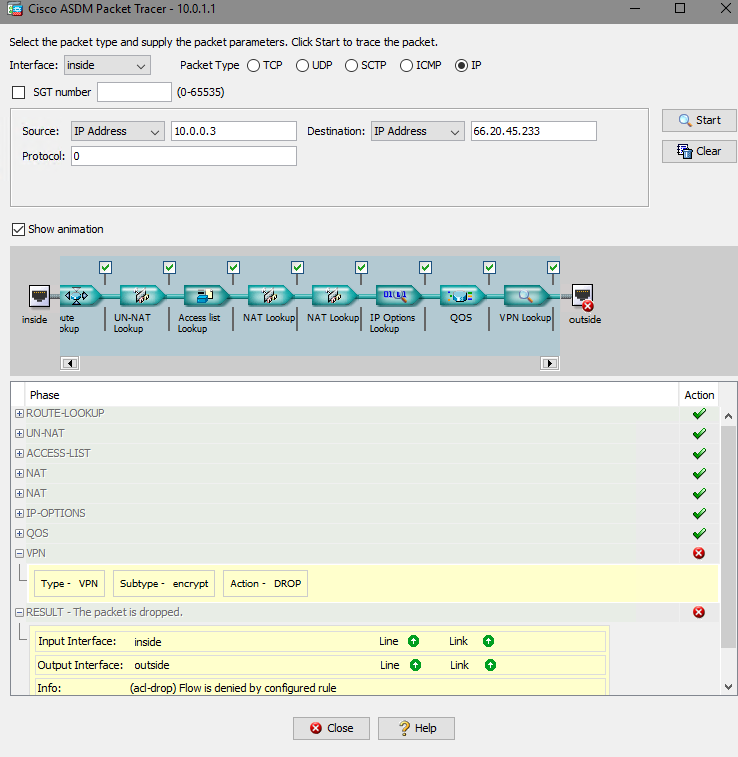
Right, so your traffic over the VPN should match the first NAT rule, which is the NAT exemption rule. Which means, traffic between 10.0.0.3 (WYNNEAPP1) and the 2 x Comdata IP address will not be natted.
The 4th NAT rule will only be used by WYNNEAPP1 for traffic destined for any other IP address other than the 2 comdata ip addresses, i.e. internet access etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 05:18 AM
Okay, our 3rd Party has updated our address to 63.147.191.66. Do I need to make any other changes? As I can still not ping their IPs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 05:23 AM
From the configuration you provided, the 3rd party is also running ASA, can you check they changed the tunnel-group to reflect the new IP address?
Turn on the debug (as before) run some pings or packet-tracer and provide the debug output for review please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 05:30 AM
Packet TRace is successful when I run it from outside interface IP but not the device IP 10.0.0.3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 05:58 AM
Here is what our 3rd Party is saying now, do you know what it means?
I am now receiving logs, phase one is failing due to a DH group mismatch. Local:148.59.168.18:500 Remote:63.147.191.66:500 Username:Unknown IKEv2 Negotiation aborted due to ERROR: The peer's KE payload contained the wrong DH group
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 06:06 AM
Yes, there is a mismatch between your IKEv2 Policies in regard to DH (diffe hellman) group, ask them to give you their IKEv2 Policy configuration and then provide your own here, so we can compare.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 06:27 AM
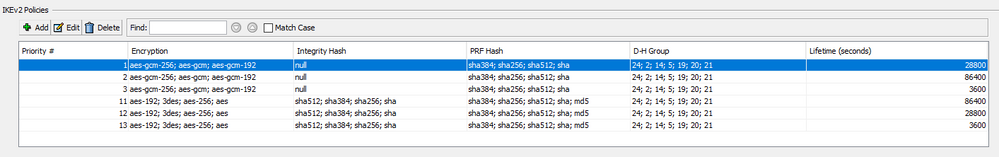
Here is our IKEv2 Policy and the 3rd Party's policy is below the screenshot
3rd Party's IKEv2 Policy:
crypto ikev2 policy 50
encryption aes-256
integrity sha256
group 19 14 5
prf sha256
lifetime seconds 86400
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 06:53 AM
You should have a match on policies 11, the peer will process policies 1,2 and 3 and fail before processing policy 11.
Run the ping and then from the CLI, can you run "show crypto ikev2 sa" and see if there is an IKEv2 SA formed please.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide