- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN tunnel from Cisco Client to ASA 5505 up but internal net
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN tunnel from Cisco Client to ASA 5505 up but internal network not reachable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 02:17 AM
Hello,
I need advice from the experts. I have a site-to-site VPN tunnel running between two of our branches and also need remote access for our users with cisco vpn clients. The site-to-site VPN works like a charm, I was even able to get the remote access tunnel up but I'm not able to reach any IP in the internal LAN 10.0.0.0 but split tunnel traffic is separated correctly. I have attached a little image of the network design plus the running config of both ASA devices. Any help on this is much appreciated. Thanks,
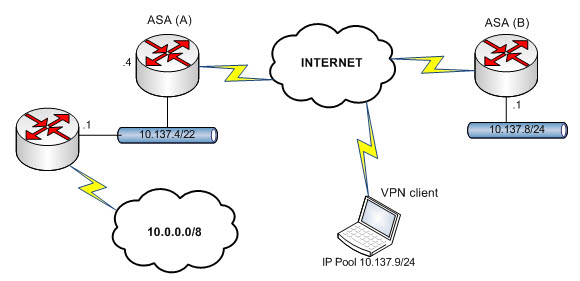
There is a static route on router .1 to the ASA (A) to .4
route inside 10.137.8.0 255.255.252.0 10.137.4.4
I have also ripped away parts of the config which are not relevant to the VPN config
CISCO ASA (A) CONFIG
:
ASA Version 7.2(3)
!
hostname EAZRHFW01
!
interface Vlan1
nameif inside
security-level 100
ip address 10.137.4.4 255.255.252.0
!
interface Vlan2
nameif outside
security-level 0
ip address xxx.xxx.53.98 255.255.255.248
!
interface Ethernet0/0
switchport access vlan 2
!
same-security-traffic permit intra-interface
access-list outside_access_in extended permit icmp any any
access-list outside_1_cryptomap extended permit ip 10.0.0.0 255.0.0.0 10.0.0.0 255.0.0.0
access-list inside_nat0_outbound extended permit ip 10.0.0.0 255.0.0.0 10.0.0.0 255.0.0.0
access-list Split_Tunnel_List standard permit 10.0.0.0 255.0.0.0
access-list outside_cryptoap_dyn_20 extended permit ip any 10.0.0.0 255.0.0.0
ip local pool 10.137.9/24 10.137.9.50-10.137.9.150 mask 255.255.255.0
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 xxx.xxx.53.97 255
route inside 10.32.0.0 255.255.0.0 10.137.4.1 1
route inside 10.128.0.0 255.255.0.0 10.137.4.1 1
route inside 10.137.12.0 255.255.252.0 10.137.4.1 1
route inside 10.137.16.0 255.255.252.0 10.137.4.1 1
route inside 10.137.20.0 255.255.252.0 10.137.4.1 1
route inside 10.193.0.0 255.255.0.0 10.137.4.1 1
aaa-server EAZRHDC1 protocol nt
aaa-server EAZRHDC1 host 10.137.4.10
nt-auth-domain-controller eazrhdc1
aaa-server EAZRHAUT protocol radius
aaa-server EAZRHAUT host 10.137.6.24
key hard2get4u
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto dynamic-map outside_dyn_map 10 set transform-set ESP-3DES-SHA
crypto dynamic-map outside_dyn_map 10 set security-association lifetime seconds 288000
crypto dynamic-map outside_dyn_map 10 set reverse-route
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs group1
crypto map outside_map 1 set peer xxx.xxx.53.99 157.161.230.155
crypto map outside_map 1 set transform-set ESP-3DES-SHA
crypto map outside_map 10 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 20
!
class-map inspection_default
match default-inspection-traffic
!
service-policy global_policy global
group-policy ZurichRAS internal
group-policy ZurichRAS attributes
dns-server value 10.137.4.10
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split_Tunnel_List
default-domain value eazrh.ch
username atonina password IfQDIRGV5C0dXHUa encrypted
tunnel-group 157.161.230.155 type ipsec-l2l
tunnel-group 157.161.230.155 ipsec-attributes
pre-shared-key *
tunnel-group ZurichRAS type ipsec-ra
tunnel-group ZurichRAS general-attributes
address-pool 10.137.9/24
authentication-server-group EAZRHAUT
default-group-policy ZurichRAS
tunnel-group ZurichRAS ipsec-attributes
pre-shared-key *
CISCO ASA (B) CONFIG
:
ASA Version 7.2(4)
!
hostname EABSLFW01
!
interface Vlan1
nameif inside
security-level 100
ip address 10.137.8.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address xxx.xxx.230.155 255.255.255.248
!
interface Ethernet0/0
switchport access vlan 2
!
access-list outside_1_cryptomap extended permit ip 10.0.0.0 255.0.0.0 10.0.0.0 255.0.0.0
access-list inside_nat0_outbound extended permit ip 10.0.0.0 255.0.0.0 10.0.0.0 255.0.0.0
access-list outside_access_in extended permit icmp any any
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 xxx.xxx.230.153 255
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs group1
crypto map outside_map 1 set peer xxx.xxx.53.98
crypto map outside_map 1 set transform-set ESP-3DES-SHA
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
tunnel-group xxx.xxx.53.98 type ipsec-l2l
tunnel-group xxx.xxx.53.98 ipsec-attributes
pre-shared-key *
!
class-map inspection_default
match default-inspection-traffic
!!
service-policy global_policy global
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 03:41 AM
Hello,
I'm no an expert but I think I might found something!
When you connect with vpn remote access (cisco VPN client software) you
got the ip address from local pool :
ip local pool 10.137.9/24 10.137.9.50-10.137.9.150 mask 255.255.255.0
than you for example try to ping remote subnetworks (in cloud 10.0.0./8),
when Asa decrypts packets from you it see that you have address from
local pool (source address), and that is in 10.0.0.0/8 network range, and because
you try to ping 10.0.0.0/8 network cloud (destination address), in my opinion that traffic
will go via site-to-site tunnell because in your interesting traffic you said :
access-list outside_1_cryptomap extended permit ip 10.0.0.0 255.0.0.0 10.0.0.0 255.0.0.0
crypto map outside_map 1 match address outside_1_cryptomap
I think the solution will be to change your address pool for vpn clients to something
that is not in 10.0.0.0/8 network range, of course you have to adjust nat exemption
to new pool and that stuff...
I hope it helps,
sorry, I'm not an expert!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 05:49 AM
Hello, experts!
unfortunately I'm not, too
ASA ver7.x dose not support an asymmetric routing. ( There's another gateway inside, right? )
It was supported in version 8.2(1) or later.
http://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_qanda_item09186a00805b87d8.shtml#asym
http://inetpro.org/wiki/ASA_Asymmetric_Routing
I hope this could be some help to you, but please forgive me if my post is missing the point..
deyass
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 07:02 AM
Hello deyassccna,
yeah, you right, it could be asymmetric routing isue if it is the case!
But I can not see that from the image or configurations!
Thanks for your suggestion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 07:43 AM
You are right with the second gateway. Frankly, I had to google the meaning of asymetric routing first when I read your post but I think asymetric routing is not really the issue. I cannot reach any IP of our subnets over remote access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 07:35 AM
Thanks for your reply. I think the problem is somewhere with routing and ACL. Problem is, remote access alone without site-to-site VPN is working, but together it is not. I will try to define separate cryptomaps for the site-to-site and remote access VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 08:00 AM
Hello again,
considering your reply where you say that remote access is working
when there is not site-to-site I'm even more convinced that your traffic
is going through site-to-site tunnel, look at my first reply!
You have already two diferent cryptomaps :
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs group1
crypto map outside_map 1 set peer xxx.xxx.53.99 157.161.230.155
crypto map outside_map 1 set transform-set ESP-3DES-SHA
crypto map outside_map 10 ipsec-isakmp dynamic outside_dyn_map
outside_map 1 and outside_map 10 are 2 diferent crypto maps! You just have to adjust interesting traffic
for site-to-site tunnel and remote access. Try to change address pool for remote access, like I said before!
Good Luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 08:12 AM
Sorry, I dind't read your email carefully enough. Will try as you suggested.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 08:50 AM
You were right regarding interessting traffic. After I changed the IP pool to something outside 10.0.0.0/8 the remote access works. Thanks a lot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2010 11:46 PM
Hello again,
I'm glad that my help was usefull,
see you again on support community :-)!
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2010 05:30 PM
Hello, Vladimir !
That was great news and wonderful assistance of you.
I'm looking forward to seeing you two again somewhere in this forum...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide