- Cisco Community
- Technology and Support
- Security
- Web Security
- open ssh 9.3 multiple vulnerability in cisco sma
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:39 AM
Hi folks recently our audit team have scanned our WSA and SMA for VApt and they have found that wsa(asyncos 14.5) and SMA (15.0) is having openssh version prior to 9.3 and should be upgraded .
IS it possible to upgrade openssh alone? i searched documents but couldn't find any document related to this any idea folks?
Solved! Go to Solution.
- Labels:
-
Web Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:43 AM
I would open a TAC case to make sure its recorded, and get bug number that you can watch.
Ken
________________________________
This email is intended solely for the use of the individual to whom it is addressed and may contain information that is privileged, confidential or otherwise exempt from disclosure under applicable law. If the reader of this email is not the intended recipient or the employee or agent responsible for delivering the message to the intended recipient, you are hereby notified that any dissemination, distribution, or copying of this communication is strictly prohibited.
If you have received this communication in error, please immediately notify us by telephone and return the original message to us at the listed email address.
Thank You.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 11:08 AM
I believe you are referring to : CVE-2023-51385
NVD - CVE-2023-51385 (nist.gov)
if so you can review the CVEs from this link
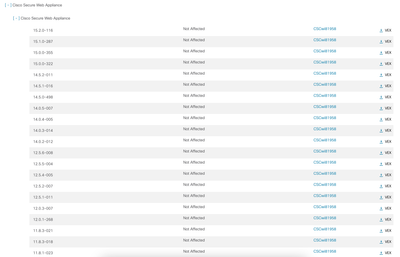
Cisco Vulnerability Repository
you can filter by disposition
here is the status for WSA
if you are referring to any other CVE, you can check them in above link.
Regards,
Amirhossein Mojarrad
+++++++++++++++++++++++++++++++++++++++++++++++++++
++++ If you find this answer helpful, please rate it as such ++++
+++++++++++++++++++++++++++++++++++++++++++++++++++
Amirhossein Mojarrad
+++++++++++++++++++++++++++++++++++++++++++++++++++
++++ If you find this answer helpful, please rate it as such ++++
+++++++++++++++++++++++++++++++++++++++++++++++++++
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:43 AM
I would open a TAC case to make sure its recorded, and get bug number that you can watch.
Ken
________________________________
This email is intended solely for the use of the individual to whom it is addressed and may contain information that is privileged, confidential or otherwise exempt from disclosure under applicable law. If the reader of this email is not the intended recipient or the employee or agent responsible for delivering the message to the intended recipient, you are hereby notified that any dissemination, distribution, or copying of this communication is strictly prohibited.
If you have received this communication in error, please immediately notify us by telephone and return the original message to us at the listed email address.
Thank You.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:46 AM
oh ok so only tac can help ok will open a case thanks a lot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 10:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 10:22 AM
you mean 15.x will resolve the issue? but 15.0 version is having proxy service hang bug which will be more severe ryt?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 11:10 AM
I don't know that 15.x will fix it. My ESA and SMA are on 15.0.1/15.0.0, and they show the vulnerability... BUT often the vuln scanners see "OpenSSH version X" is vulnerable, and so report that you're vulnerable, except Cisco would fix the specific bug that in the code they shipped, but not upgrade the whole package.
That's why you need to open a TAC case, to find if that is the case here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 03:08 AM
Regarding the high load on the proxy in version 15, you can check the defect from here: CSCwh60833
It has not been fixed yet, but it is not appearing for all customers. If you are able to perform the test in an isolated situation and you do not encounter the problem, you can upgrade WSA to version 15.x.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 11:08 AM
I believe you are referring to : CVE-2023-51385
NVD - CVE-2023-51385 (nist.gov)
if so you can review the CVEs from this link
Cisco Vulnerability Repository
you can filter by disposition
here is the status for WSA
if you are referring to any other CVE, you can check them in above link.
Regards,
Amirhossein Mojarrad
+++++++++++++++++++++++++++++++++++++++++++++++++++
++++ If you find this answer helpful, please rate it as such ++++
+++++++++++++++++++++++++++++++++++++++++++++++++++
Amirhossein Mojarrad
+++++++++++++++++++++++++++++++++++++++++++++++++++
++++ If you find this answer helpful, please rate it as such ++++
+++++++++++++++++++++++++++++++++++++++++++++++++++
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide