- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Service Provider Wi-Fi - MAC-Auth-Failover Feature Support
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-14-2012 03:12 AM - edited 11-18-2020 03:00 AM
Introduction
Mac-Auth-Failover feature allows to associate wireless clients with Dynamic-WEP security even if MAC-Auth fails.
Pre-requirement
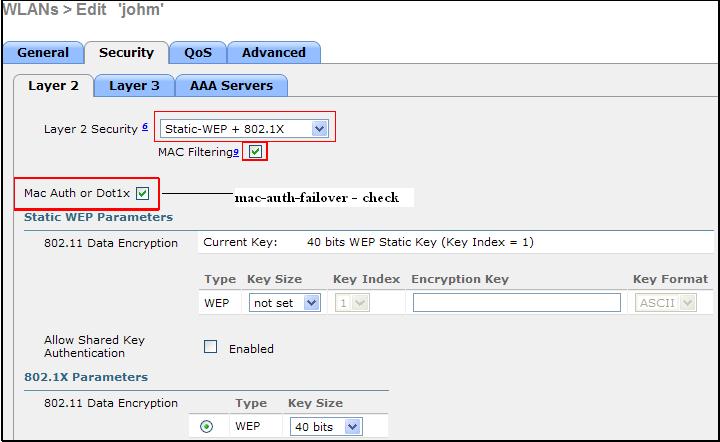
- Security Type on WLAN has to be “Static-WEP + Dynamic-WEP (802.1x)”.
- Mac-Filter has to be enabled on the same WLAN.
NOTE – Mac-auth-failover is not applicable for Static-WEP wireless client. Mac-Address of Static-WEP client has to be present in the local-database (on wlc) or AAA server.
NOTE – If the feature is disabled then Wireless Controller will de-auth the client if mac-auth fails.
How it works - Static-WEP client
- Client comes with Static-WEP security type.
- WLC checks the local-database first if it does not find client’s MAC entry then WLC sends “radius_request” to AAA server and AAA server send “radius_accept” if MAC is present otherwise “radius_reject”.
- When MAC-auth is completed then WLC moves the client into RUN state.
- If MAC-auth is failed then client will be in “802.1X_REQD”.
Note – if “mac-auth-failover” feature is enabled WLC does not de-auth client (with static-wep security) when client fails “mac-auth”. WLC allows client to be associated but client will be in “802.1X_REQD” state and not get IP Address.
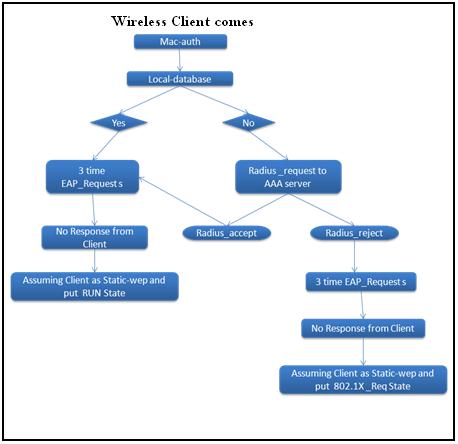
Dynamic-WEP (802.1x) client
- Client comes with Dynamic-WEP (802.1x) security type.
- WLC checks the local-database first if it does not find client’s MAC entry then WLC sends “radius_request” to AAA server and AAA server send “radius_accept” if MAC is present otherwise “radius_reject”.
- Since “Mac-auth-failover” feature is enabled WLC will send “EAP_Request” to client whether AAA server sends “radius_accept” or “radius_reject”.
- And then Dynamic-WEP procedure takes place in order to put client into RUN state.

NOTE – After EAP_Request, Four-way hand shake happens as part of Dynamic-wep security and after successful authentication WLC put the client into RUN state.
Configuration - GUI
CLI Commands
config wlan mac-filtering enable <wlan_id> config wlan security static-wep-key enable <wlan_id> config wlan security static-wep-key encryption <wlan_id> 40/104 ascii/Hex <key> <key_index> config wlan security 802.1X enable <wlan_id> config wlan security 802.1X on-macfilter-failure enable <wlan_id>
NOTE – By default, 802.1X uses key index value 1 hence we need to use some other key index value for “static-wep” but some wireless utility does not have option to configure index value. In that case, 802.1X key index value can be changed through CLI.
(WLC-5500) >config advanced eap key-index ? <key-index> Enter the key index value, 0 or 3.
Commands to verify
Show wlan <wlan_id> Example - (sp-wifi-wlc) >show wlan sp-wlan WLAN Identifier.................................. 6 Profile Name..................................... sp-wlan Network Name (SSID).............................. sp-wlan Status........................................... Disabled MAC Filtering.................................... Enabled Broadcast SSID................................... Enabled AAA Policy Override.............................. Enabled | | Security 802.11 Authentication:........................ Open System FT Support.................................... Disabled Static WEP Keys............................... Enabled Key Index:...................................... 1 Encryption:..................................... 40-bit WEP 802.1X........................................ Enabled Encryption:..................................... 40-bit WEP 802.1X on MAC Auth failure:..................... Enabled | -----------xxxx--------------
Debug Commands
- Debug client <client_mac_address>
- Debug aaa all enable
Debug that will help in troubleshooting
(WLC-5500) >*apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 Adding mobile on LWAPP AP 64:d9:89:47:f7:e0(1) *apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 Association received from mobile on AP 64:d9:89:47:f7:e0 *apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 Global 200 Clients are allowed to AP radio *apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 Max Client Trap Threshold: 0 cur: 0 *apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 Applying Interface policy on Mobile, role Unassociated. Ms NAC State 0 Quarantine Vlan 0 Access Vlan 0 *apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 Re-applying interface policy for client *apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:1839) *apfMsConnTask_4: Aug 09 18:00:57.015: 00:24:d7:42:46:e4 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2006) *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 In processSsidIE:3883 setting Central switched to TRUE *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 In processSsidIE:3886 apVapId = 1 and Split Acl Id = 65535 *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 Applying site-specific Local Bridging override for station 00:24:d7:42:46:e4 - vapId 5, site 'apg', interface 'dyn59' *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 Applying Local Bridging Interface Policy for station 00:24:d7:42:46:e4 - vlan 59, interface id 12, interface 'dyn59' *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 Applying site-specific override for station 00:24:d7:42:46:e4 - vapId 5, site 'apg', interface 'dyn59' *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 Applying Interface policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 59 *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 Re-applying interface policy for client *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:1839) *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2006) *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 processSsidIE statusCode is 0 and status is 0 *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 processSsidIE ssid_done_flag is 0 finish_flag is 0 *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 STA - rates (8): 140 18 152 36 176 72 96 108 0 0 0 0 0 0 0 0 *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 suppRates statusCode is 0 and gotSuppRatesElement is 1 *apfMsConnTask_4: Aug 09 18:00:57.016: apfVapRadiusClientInfoGet: Client 00:24:D7:42:46:E4 dynamic int attributes srcAddr: 9.10.59.10 , gw: 9.10.59.1 mask: 255.255.255.0 , vlan:59, dpPort:13, srcPort:32769 *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 apfProcessAssocReq (apf_80211.c:6585) Changing state for mobile 00:24:d7:42:46:e4 on AP 64:d9:89:47:f7:e0 from Idle to AAA Pending *aaaQueueReader: Aug 09 18:00:57.016: Unable to find requested user entry for 0024d74246e4 -------------- >>>[when client mac is not there in the local-database (on wlc)] *aaaQueueReader: Aug 09 18:00:57.016: ReProcessAuthentication previous proto 8, next proto 40000001 *apfMsConnTask_4: Aug 09 18:00:57.016: 00:24:d7:42:46:e4 Scheduling deletion of Mobile Station: (callerId: 20) in 10 seconds *aaaQueueReader: Aug 09 18:00:57.016: AuthenticationRequest: 0x2b7c4fac *aaaQueueReader: Aug 09 18:00:57.016: Callback.....................................0x10119c88 *aaaQueueReader: Aug 09 18:00:57.016: protocolType.................................0x40000001 *aaaQueueReader: Aug 09 18:00:57.016: proxyState...................................00:24:D7:42:46:E4-00:00 *aaaQueueReader: Aug 09 18:00:57.016: Packet contains 14 AVPs (not shown) *aaaQueueReader: Aug 09 18:00:57.017: 00:24:d7:42:46:e4 AAARadiusSendPktToDtl actual port MTU :1430 *aaaQueueReader: Aug 09 18:00:57.017: 00:24:d7:42:46:e4 AAARadiusSendPktToDtl:Sending PDU to DTL SRC MAC: 68:EF:BD:8F:14:4F *aaaQueueReader: Aug 09 18:00:57.017: 00:24:d7:42:46:e4 Successful transmission of Authentication Packet (id 16) to 9.1.0.100:1812, proxy state 00:24:d7:42:46:e4-00:01 -------------------------------------- >>> [When WLC IP address is there in AAA server] *aaaQueueReader: Aug 09 18:00:57.017: 00000000: 01 10 00 b8 00 00 00 00 00 00 00 00 00 00 00 00 ................ *aaaQueueReader: Aug 09 18:00:57.017: 00000010: 00 00 00 00 01 13 30 30 3a 32 34 3a 64 37 3a 34 ......00:24:d7:4 *aaaQueueReader: Aug 09 18:00:57.017: 00000020: 32 3a 34 36 3a 65 34 1e 18 36 34 3a 64 39 3a 38 2:46:e4..64:d9:8 *aaaQueueReader: Aug 09 18:00:57.017: 00000030: 39 3a 34 37 3a 66 37 3a 65 30 3a 6a 6f 68 6d 1f 9:47:f7:e0:johm. *aaaQueueReader: Aug 09 18:00:57.017: 00000040: 13 30 30 3a 32 34 3a 64 37 3a 34 32 3a 34 36 3a .00:24:d7:42:46: *aaaQueueReader: Aug 09 18:00:57.017: 00000050: 65 34 05 06 00 00 00 0d 04 06 09 0a 3b 0a 20 0a e4..........;... *aaaQueueReader: Aug 09 18:00:57.017: 00000060: 48 53 52 50 35 35 5f 31 1a 0c 00 00 37 63 01 06 HSRP55_1....7c.. *aaaQueueReader: Aug 09 18:00:57.017: 00000070: 00 00 00 05 02 22 4f d3 fe e3 8b 10 a2 b9 ae da ....."O......... *aaaQueueReader: Aug 09 18:00:57.017: 00000080: ad 11 c3 6d ac 64 1b 71 c5 b8 50 ed c1 6f b5 fd ...m.d.q..P..o.. *aaaQueueReader: Aug 09 18:00:57.017: 00000090: c1 59 9e 3d d8 29 06 06 00 00 00 0a 0c 06 00 00 .Y.=.).......... *aaaQueueReader: Aug 09 18:00:57.017: 000000a0: 05 14 3d 06 00 00 00 13 40 06 00 00 00 0d 41 06 ..=.....@.....A. *aaaQueueReader: Aug 09 18:00:57.017: 000000b0: 00 00 00 06 51 04 35 39 ....Q.59 *radiusTransportThread: Aug 09 18:00:57.020: 00000000: 03 10 00 20 4e 86 b3 ae 7d 6e 6c be 65 4a 8f 16 ....N...}nl.eJ.. *radiusTransportThread: Aug 09 18:00:57.020: 00000010: ee da 41 56 12 0c 52 65 6a 65 63 74 65 64 0a 0d ..AV..Rejected.. *radiusTransportThread: Aug 09 18:00:57.020: ****Enter processIncomingMessages: response code=3 *radiusTransportThread: Aug 09 18:00:57.020: ****Enter processRadiusResponse: response code=3 *radiusTransportThread: Aug 09 18:00:57.020: 00:24:d7:42:46:e4 Access-Reject received from RADIUS server 9.1.0.100 for mobile 00:24:d7:42:46:e4 receiveId = 0 ---------------------- >>> [ when client’s mac is NOT there in AAA server ] *radiusTransportThread: Aug 09 18:00:57.021: 00:24:d7:42:46:e4 Returning AAA Error 'Authentication Failed' (-4) for mobile 00:24:d7:42:46:e4 *radiusTransportThread: Aug 09 18:00:57.021: AuthorizationResponse: 0x45ed1984 *radiusTransportThread: Aug 09 18:00:57.021: structureSize................................32 *radiusTransportThread: Aug 09 18:00:57.021: resultCode...................................-4 *radiusTransportThread: Aug 09 18:00:57.021: protocolUsed.................................0xffffffff *radiusTransportThread: Aug 09 18:00:57.021: proxyState...................................00:24:D7:42:46:E4-00:00 *radiusTransportThread: Aug 09 18:00:57.021: Packet contains 0 AVPs: *apfReceiveTask: Aug 09 18:00:57.021: 00:24:d7:42:46:e4 Received SGT for this Client. *apfReceiveTask: Aug 09 18:00:57.021: 00:24:d7:42:46:e4 SGT received is '' with length 0 for station 00:24:d7:42:46:e4 *apfReceiveTask: Aug 09 18:00:57.021: 00:24:d7:42:46:e4 Client Mac not found in Radius DB, but sending Sucessfull Association response , since 'dot1x on-mac-failure' feature is turned on -------------------------------- >>> [ WLC sends successful association response because 'dot1x on-mac-failure' is enabled] *apfReceiveTask: Aug 09 18:00:57.021: 00:24:d7:42:46:e4 Applying new AAA override for station 00:24:d7:42:46:e4 *apfReceiveTask: Aug 09 18:00:57.021: 00:24:d7:42:46:e4 Override values for station 00:24:d7:42:46:e4
Video - SP WiFi Updates on Wireless LAN Controller - 7.3 Release
Features and Use Cases in Release 1.0
The main features supported in Release 1.0 include:
• Controlling, securing, and differentiating services through intelligent policies embedded directly in the network or received through open and standards-based control interfaces to the basic service set (BSS)
• Customizing service convergence with zero-touch provisioning across customized networks
• Authenticating and authorizing subscribers using Dynamic Host Configuration Protocol (DHCP), RADIUS-based authentication, web logon, Wireless Internet Service Provider roaming (WISPr), MAC address, and IP address
• Controlling and accounting for per-subscriber and per-service use for postpaid and prepaid billing
• Validating high availability under high scale for:
– Number of access points per controller
– Subscriber count
– Call rates
– Load balancers
Cisco SP Wi-Fi Services Overview
Our SP Wi-Fi Services portfolio is a comprehensive set of services representing a holistic approach to the total lifecycle of service provider Wi-Fi engagements. Starting with a proof of concept, it covers the end-to-end spectrum of planning, building, optimization, and operation services, each assured by Cisco service-level agreements (SLAs). These services are flexible and can be customized.
• Cisco SP Wi-Fi Proof of Concept Service
– Demonstration of a centralized management system, with zero-touch service fulfillment for rapid deployments of meshed access points, using a cloud-based architecture hosted in a Cisco data center
• Cisco SP Wi-Fi RF Plan and Build Service
– Professional services from Cisco and our Wi-Fi specialized partners
– Help in planning and deploying the RF components of the Cisco SP Wi-Fi solution
– Analysis of architectural readiness, with guidance on selecting and prioritizing locations for Wi-Fi
– RF expertise to obtain the most from your wireless access points
– Coverage and capacity planning
– Post-deployment RF analysis assistance to promote deployment success
• Cisco SP Wi-Fi Core Plan and Build Service
– Professional services from Cisco and our Wi-Fi specialized partners
– Help planning and deploying the core components of the Cisco SP Wi-Fi solution
– Analysis of architectural readiness and assistance with the SP Wi-Fi deployment design
– Start-to-finish deployment assistance, including a mobile subscriber policy enforcement system
– Pre-deployment validation to help ensure deployment success
– Post-deployment knowledge transfers to help ensure your understanding of the solution
• Cisco SP Wi-Fi Solution Support Service (Reactive)
– Expert assistance to streamline operation of the Wi-Fi architecture
– Quick isolation and remediation of unplanned service disruptions
– Tracking and identification of the root cause of disruptive incidents, which provides valuable information for design changes and to help you scale with mobile subscriber growth
• Cisco SP Wi-Fi Optimization Services (Proactive)
– Expert analysis and recommendations for transforming your Wi-Fi architecture into a high-performing, efficient environment
– Help creating a strategy for managing all the critical components of the Cisco SP Wi-Fi architecture using a suite of Cisco hosted network management applications
– Availability and performance optimization expertise to validate your planned design changes
– Collaboration in developing a strategy for managing software releases and changes
– Continuous learning activities that help your IT staff become more self-sufficient
• Cisco SP Wi-Fi Assurance Service (Preemptive)
– Extension of the measurement and analytical capabilities provided by your Cisco SP Wi-Fi architecture
– Real-time monitoring of various key performance indicators (KPIs) from Cisco network operations center
– Comprehensive analytics using fault, capacity, availability, and performance information to help ensure reliable operations
• Cisco SP Wi-Fi Operate Service (End-to-End Platform Management)
– Monitoring of the managed devices in the your environment to help ensure access points and controllers are properly activated and provisioned
– Management of incident and problem resolution
– Identification of operational trends to continually improve performance
Cisco Service Provider Wi-Fi Solution 3.0 Data Sheet
Reference
- Cisco Service Provider Wi-Fi - PPPoE Feature Support
- Packet Flow Between Cisco PPPoE Access Point (AP) and PPPoE server - Service Provider Wi-Fi
- Service Provider Wi-Fi - MAC-Auth-Failover Feature Support
- DHCP Option 82 - Service Provider Wi-Fi
- Service Provider Wi-Fi - Radius Enhancement Feature
- Cisco Service Provider Wi-Fi - Important Key Features
- 1000
- 1040
- 1100
- 1100_ap
- 1100_lap
- 1130_AG
- 1130_ap
- 1130_lap
- 1140
- 1140_ap
- 1140_lap
- 1200
- 1200_ap
- 1200_lap
- 1230_AG
- 1230_ap
- 1230_lap
- 1240_AG
- 1240_ap
- 1240_lap
- 1250
- 1250_ap
- 1250_lap
- 1260
- 1300
- 1300_bridge
- 1400
- 1400_bridge
- 1500
- 1500_map
- 1520
- 1550
- 1600
- 2000_wlc
- 2100_wlc
- 2500
- 2600
- 3300_Series_Mobility_Services_Engine
- 340_ap
- 3500
- 350_ap
- 3600
- 3750_wlc
- 4400_wlc
- 500_lap
- 5500
- 5500_wlc
- 5505
- 5508
- 5700
- 600_Series OfficeExtend_AP
- 7900_ip_phone
- 802.11a
- 802.11b
- 802.11g
- 8500
- aaa
- active_directory
- air_cb21ag
- aironet
- aironet_antennas
- ap
- autonomous
- cisco_prime_ncs
- eap
- eap_fast
- hwic_ap
- lap
- leap
- lwapp
- ncs
- peap
- pppoe_packet_flow service_provider_wi-fi
- prime
- Prime_Network_Control_System
- radio
- radius
- roaming
- ssid
- tacacs
- virtual_wireless_controller
- wcs
- wgb
- wireless_lan_controller
- wireless_lan_controllers
- wism
- wlan
- wlc
- wlc_5500
- wlc_5508
- wlcm
- wlse
- wlsm
- wpa
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: