- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Central Web Authentication (CWA) for guests with ISE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-11-2012 12:04 AM - edited 11-18-2020 02:59 AM
Introduction
There are multiple ways of doing Web Authentication on the WLC. The first one is Local Web Authentication. In this case, the WLC will redirect the HTTP Traffic to an internal or external server where the user will be prompted to authenticate. The WLC will then fetch this credentials (sent back via HTTP GET Request in case of external server), and make a radius authentication. In case of guest user, we need an external server (like ISE or NGS), as the portal can provide some feature like Device Registering, Self Provisionning, ...
The flow would be the following:
-User associate to the Web Auth SSID
-User starts its browser
-The WLC Redirect to the guest portal (ISE/NGS)
-The user authenticate on the portal
-The Guest Portal redirect back to the WLC with the credentials entered
-The WLC Authenticate the guest user via Radius
-The WLC Redirects back to the original URL.
That makes a lot of redirection. The new approach is to use Central Web Authentication. This works with ISE > 1.1 and WLC > 7.2.
The flow in this case would be:
-User associate to the Web Auth SSID
-User starts its browser
-The WLC Redirect to the guest portal (ISE)
-The user authenticate on the portal
-The ISE send a Radius Change Of Authorization (CoA - UDP Port 3799) to indicate to the controller that the user is valid, and eventually push radius attributes (ACL for example).
-The User is prompted to retry his original URL
Setup Used
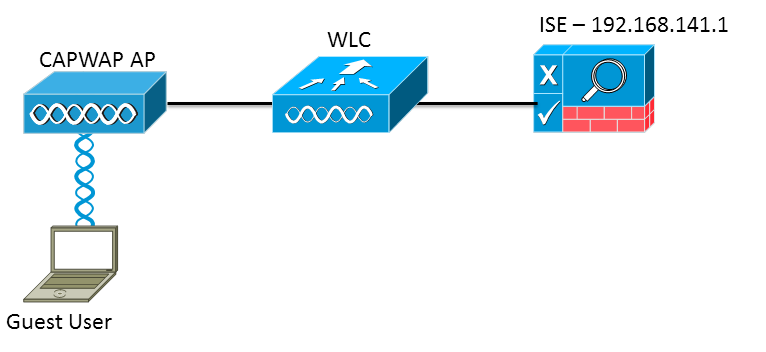
The version used are:
ISE: 1.1.1.268
WLC: 7.2.110.0
WLC Configuration
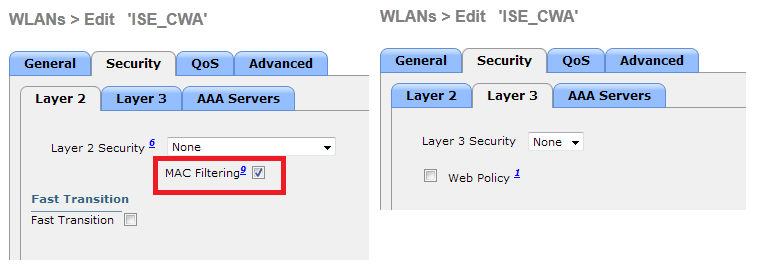
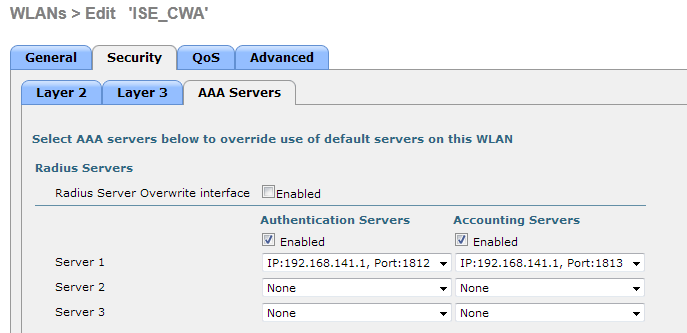
The WLC Configuration is pretty straight-forward. We uses a "trick" (same as on Switches) to get the dynamic authentication URL from the ISE (as it is using CoA, a session needs to be created, and the session ID is part of the URL). We need to configure the SSID to use MAC Filtering. We will configure the ISE to return an access-accept even if the mac address is not found, so that it will sends the redirection URL for all users.
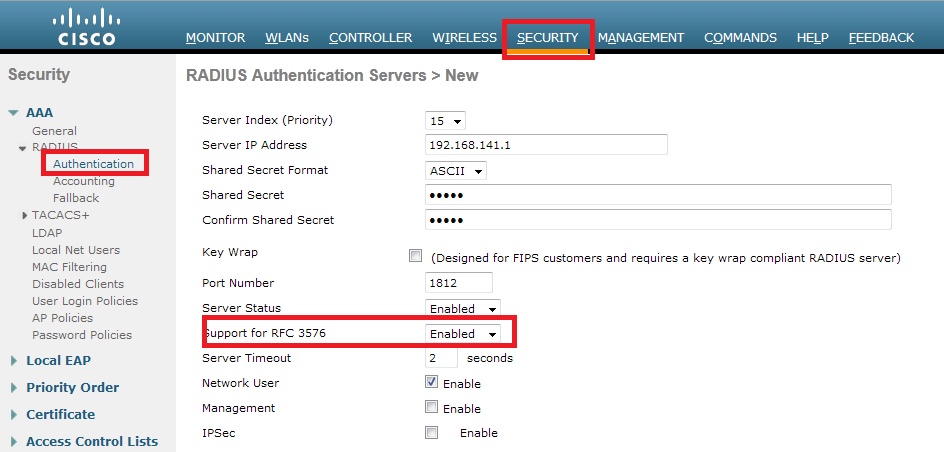
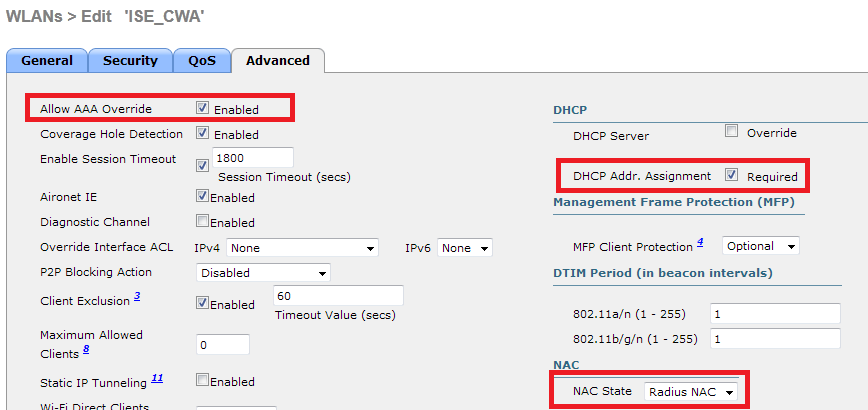
In addition to this, we need to enable Radius NAC and AAA Override. The Radius NAC allows the ISE to send a CoA Request to indicate that the user is now authenticated and can access the network. It is also used for Posture Assessment, in which case the ISE would change the user profile based on posture result.
We need also to be sure that the radius server have RFC 3576 (CoA) enabled, which is by default.
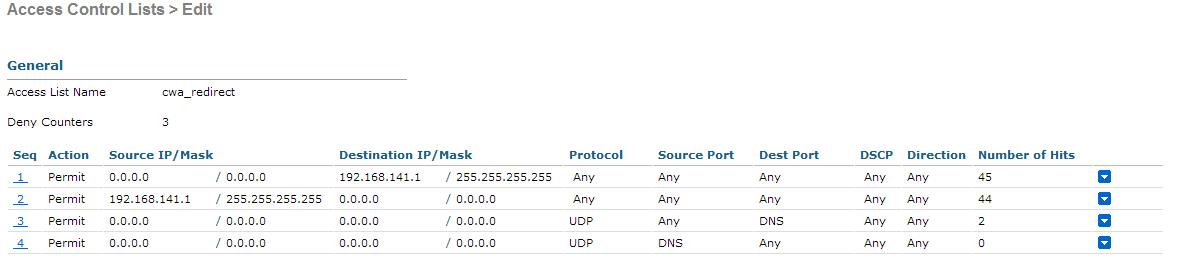
The final step is to create a Redirect-ACL. This ACL will be referenced in the access-accept of the ISE and will define what traffic should be redirected (denied by ACL), and what traffic shouldn't (permitted by the ACL). Basically, we need to permit DNS and traffic to/from ISE.
Everthing is now complete on the WLC. Let's configure the ISE
ISE Configuration
On the ISE, we need to make authorization profile, and then we can configure authentication and authorization. The WLC should already configured as a network device.
In the authorization profile, we need to put the name of the ACL has been created earlier on the WLC:
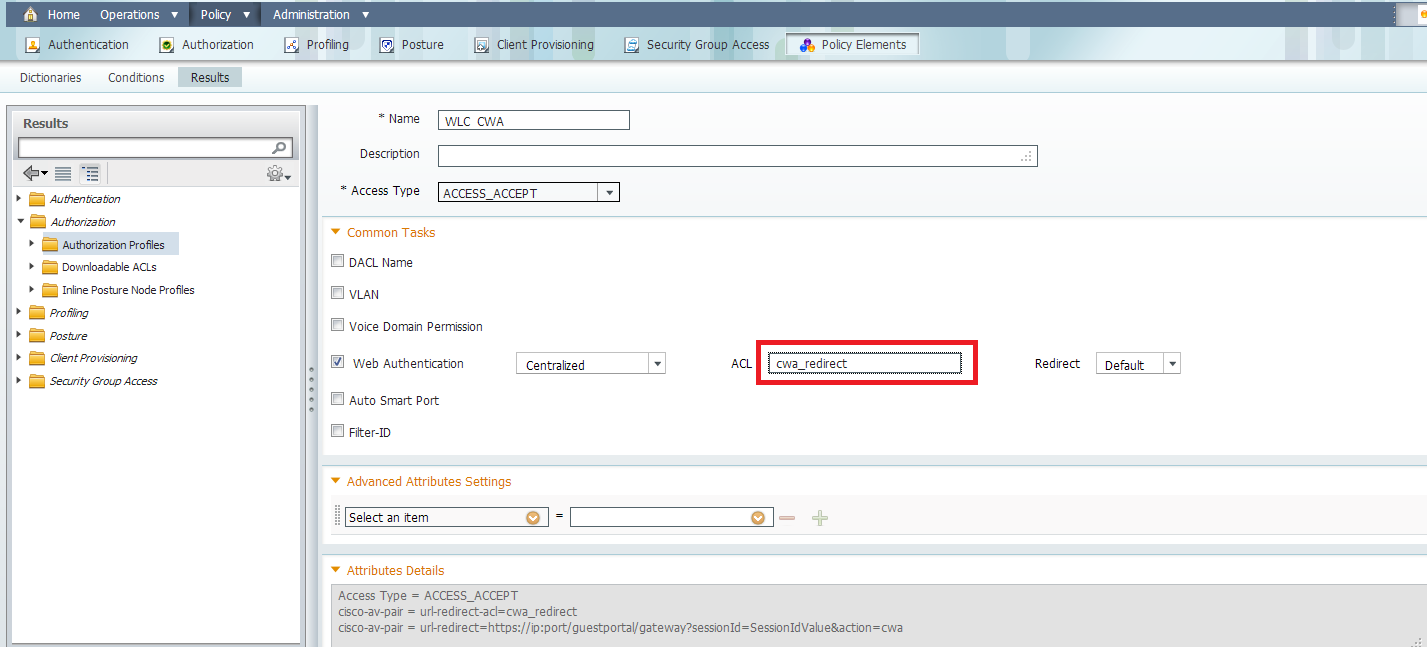
Now, we need to make sure the ISE is accepting all the MAC Authentication from the WLC and return the profile:

We can use the Built-In Wireless MAB condition, which match :
-Radius:Service-Type : Call Check (Mac Authorization use Call Check on WLC and Switches).
-Radius:NAS-Port-Type: Wireless - IEEE 802.11
Now, we need to configure the authorization. One important thing to understand is that there will be 2 authentication / authorization:
-One when the user associate to the SSID, and when we need to return the cwa profile
-Another when the user authenticate on the web portal. This one will match the default rule (internal users), in my situation (you can configure it as you want). What is important is that the authorization part doesn't match the CWA Profile again, otherwise we would have a redirection loop. We can use the attribute "Network Access:UseCase Equals Guest Flow" to match this second authentication.
The result looks like this:
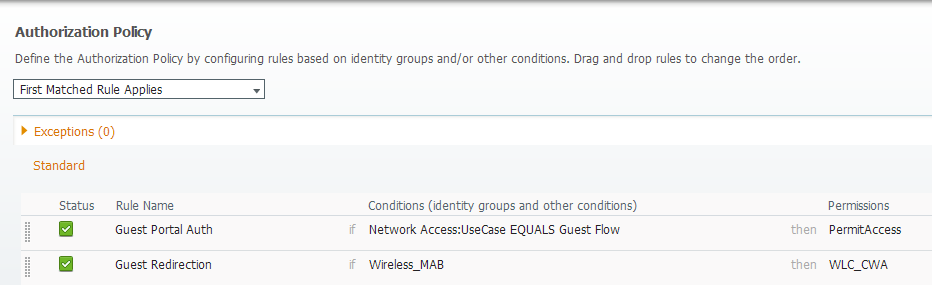
Test
Once we associate to the SSID, we can see the auth in the ISE page:
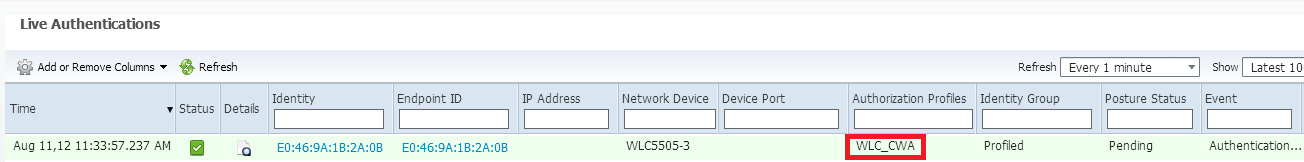
And if we check the client details in the WLC, we can see the Redirection URL and ACL are applied:
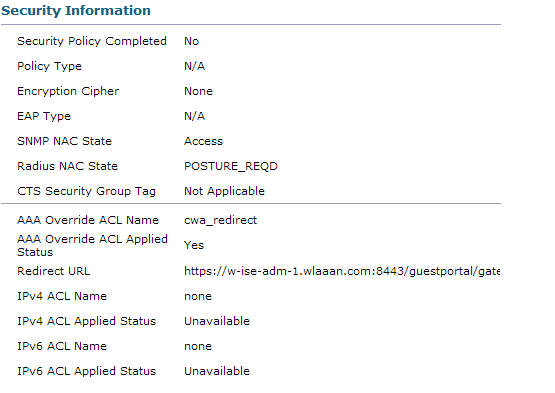
Now, when we open any address on the client, we are redirected to our ISE (be careful to have DNS setup correctly).
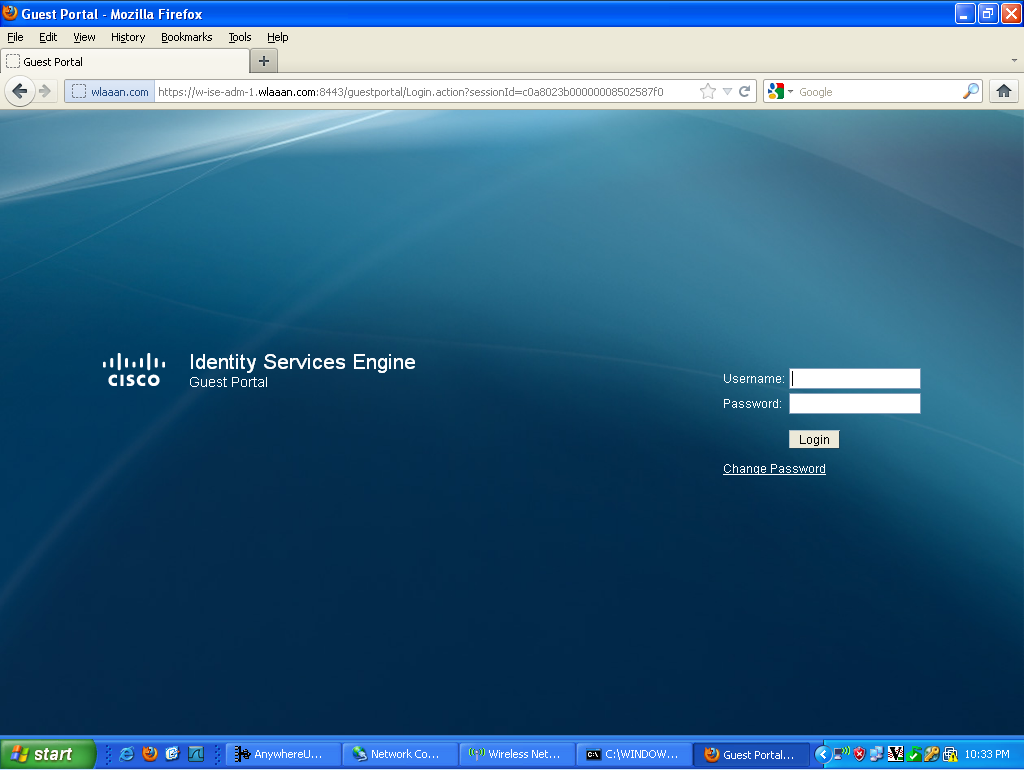
Then the user needs to accept the policies, and then it will be granted access to the network.
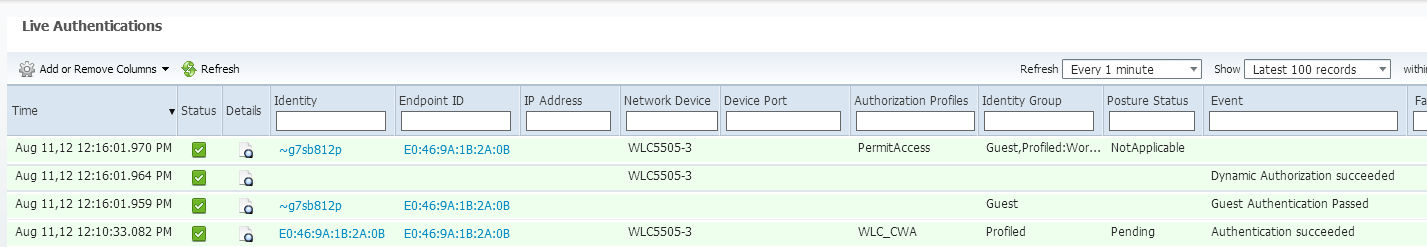
If we look back at my ISE, we can now see the authentication, the change of authorization, and that the profile applied is permitAccess:
On the controller, the Policy Manager State and Radius NAC State should change from "POSTURE_REQD" to "RUN"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Do we have a sample seutp for the IOS controllers running IOS-XE 3.2.0SE release with ISE ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
I´m trying to configure a certificate in order to gain access to the Internet for a guest wvlan, the problem is that an error message says that the certificate isn´t trusted and click next to continue... i´m using a certificate from the www.digicert.com.
Could you gave me a tip or document explain how to configure a certificate on Ise.
I have a WLC that redirect to a web pagen login on Cisco ISE.
Tks for the help
Adriano Porcaro
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Helllo Adriano,
You can find help to install the certificates on ISE here:
http://www.cisco.com/en/US/docs/security/ise/1.1.1/user_guide/ise_man_cert.html
Basically, you need to have the digicert in the Server Certificates session, and enabled for HTTP.
Regards,
Bastien.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
Has anyone tested web authentication for wireless guest access using WS 3850?
Regards,
Chris
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Christos,
From my head I believe the current NGWC image have no support or no full support for CoA, therefore you should be able get redirected to the ISE, but the CoA wouldn't work. This will be fixed in the next release.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Bastien,
Thanks for your response.
I don't need CoA for wireless guest access.I managed to setup ISE + WLC 2504 for web authentication but the same scenario using ISE + SW 3850 failed.
I used as reference the folowing guide:
It's not very clear how web authentication works on 3850 wlan.
Best regards,
Chris
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
If I do not see Wireless_Mab under conditions for the Authorization Policy, how do I add it?
thanks,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jerry,
It should be by default in later ISE version (starting 1.1.2 I think).
Otherwise you can match service-type = call-check (10) and nas-port-type=802.11
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Guys,
I have some problems with this design.
First: My WLC is 7.0.240 IOS version. obs: I can´t search 7.2 WLC IOS to download int cisco website.
My ISE version is 1.2.
Wired authentication is ok for 802.1x with Digital certificate and Guest wired too, with redirect page + acl on switch port.
The problem is WIFI:
802.1x wifi ok
BUT Guest redirect isn´t Working.
In the Client logs i can´t see Url Redirect - none and I see just the ACL.
In the SSID Guest - Radius Nac State I cant put to enable cuz the WLC show the message : "
radius nac is available only for wlan with 802.1x/WPA/WPA2 Layer 2 security"
My WebAuth Athorization profile is correct. My access-list in WLC permit DNS and all ip to ISE.
Somebody have some Idea why can´t redirect to the guest portal????
I need this Help for a important implementation.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have the same problem. I think it is becuase i am still running 7.0.230.0, i think i have to go to > 7.2
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Mac Authentication Bypass is only supported from 7.2 and above. Hence it's only supported on WLC 5508 and higher controllers.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
When using MAC Filtering on the Controller, as in the example above, the guest sessions where not visible anymore in Operations->Catalog->Session Directory.
After reverting back to WLC L3 web redirect with external authentication, the sessions were once again available.
Is there anything else that could be done to have the Session feature available? We really need it for controlling the guests...
The current design with L3 web auth on the WLC and the link statically configured on WLC has some problems with redirection after sunccessful login - some browser don't accept the WLC page with the virtual ip framed in a page form the ISE server.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Cristian,
As far as I know, the guest sessions should be visible once the guest users logs in. You may open a TAC case to sort this if you can reproduce this behaviour.
Otherwise, ISE 1.2 has greatly improved the redirection process for external Web Auth on WLC, as it pushes back credentials over POST, and no longer via iFrames as depending on certificate trust and browser configuration, this used to have some issues.
Note: I have also tested this in ISE 1.2, I could see my guest users in the active sessions with CWA:
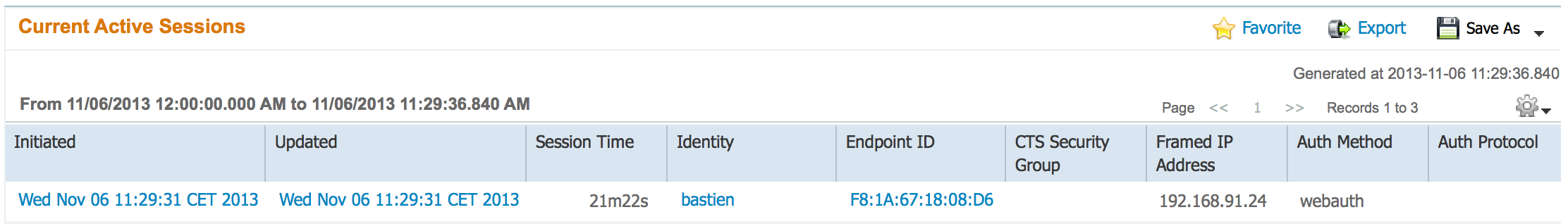
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
"
Hello Tarik, You are right, with CWA, the ISE shows a message indicating the user he can retry his original URL. This is a current limitation, as the ISE doesn't know the original URL.
What you can do is to create a custom portal with HTML Files and modify the success page to redirect to an arbitrary web page."
When is this limitation being overcome? It seems very clunky to have users not directly go to their homepage or the URL they specified initially or to have to force a user to go to a landing page.
Thanks
John
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Guillerm
I now you posted this long time ago, but I'm having the same issue, I'm just wondering if you got it resolved and how.
Thanks
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

