- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Understanding HTTPS Redirect over Web-auth
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-17-2015 08:48 PM - edited 11-18-2020 03:09 AM
Introduction
Dhiresh Yadav is a wireless expert and working for the Cisco's High Touch Technical Support (HTTS) team, a team that provides reactive technical support to majority of Cisco’s premium customers. In this document Dhiresh provides the configuration and explain about the web-auth redirection over the HTTPS. This is a feature introduced in the CUWN 8.0.
Prerequisites
- Basic Knowledge of WLC Web-auth
- How to configure Wireless LAN Controller (WLC) for Web-authentication.
Components used
The information in this document is based on these software and Hardware versions:
- Cisco 5500 series WLC that runs firmware 8.0.100.0 CUWN version.
Note: The Configuration and web-auth explanation provided below is applicable to all WLC models and any CUWN image equal to or above 8.0.100.0.
Overview
Before CUWN 8.0 release i.e up to 7.6 , if you try HTTPS://page , the page was not getting redirected using web-authentication. In CUWN 8.0 and onwards ,this is supported. So if any client tries https://page , it will be redirected to the web-auth login page which was not possible earlier.Basically, if you go to port 443 , there was no redirection for web authentication. As more and more websites have started using HTTPS, so this feature will support that HTTPS redirect, which means if you go to HTTPS:// during web-auth , you would be redirected to the controller. Also this feature is very useful for the devices that send https requests with an application ( but not using browser ) to see if it can join anywhere based on response.
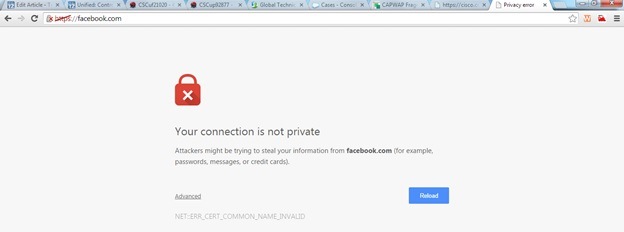
You might get the message “certificate is not issued by a trusted certificate authority.” on your browser after configuring https-redirect feature even if you have a valid root or chained certificate on the Controller as shown in the Figure-1 and Figure-2.The certificate you installed on the controller is issued to your virtual IP address. So during HTTP-Redirect, if you have this certificate on the WLC , you will not get Security certificate warning error .However in the case of HTTPS-redirect, you would still get the error . Some browser's because of the use of HTTPS://page , expect a certificate issued to the IP address of the site resolved by the DNS but what they are returned is a redirect page from the WLC and having certificate issued to the Internal web server (virtual ip address). Hence they might still throw this error. This is purely because of the way HTTPS works and will always happen if you try to intercept the HTTPS session for web-auth redirection to work.
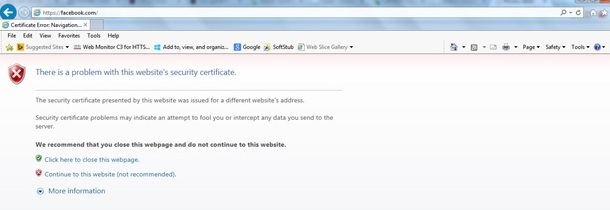
In the Chrome , You might see like below:
Configuration
Configure the WLC
(WLC)>config wlan security web-auth enable 10
(WLC)> config network web-auth https-redirect enable
WARNING! - You have chosen to enable https-redirect. This might impact performance significantly
So as you see , this might impact throughput while doing https redirection than http redirection
For more understanding and information on the web authentication , Please refer to the below link:
Web Authentication on WLAN Controller
Verify
(WLC)>show network summary
Web Auth Secure Web ....................... Enable
Web Auth Secure Redirection ............... Enable
(WLC) >show debug
MAC Addr 1.................................. 24:77:03:52:56:80
Debug Flags Enabled:
webauth redirect enabled.
*webauthRedirect: Jan 16 03:35:35.678: 24:77:3:52:56:80- received connection. client socket = 9
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- trying to read on socket 95
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- calling parser with bytes = 204
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- bytes parsed = 204
*webauthRedirect: Jan 16 03:35:35.679: captive-bypass detection enabled, checking for wispr in HTTP GET, client mac=24:77:3:52:56:80
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- Preparing redirect URL according to configured Web-Auth type
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- got the hostName for virtual IP(wirelessguest.test.com)
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- Checking custom-web config for WLAN ID:10
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- Global status is enabled, checking on web-auth type
*webauthRedirect: Jan 16 03:35:35.679: 24:77:3:52:56:80- Web-auth type Customized, using URL:https://wirelessguest.test.com/fs/customwebauth/login.htmlNote:
- Secure web (config network secureweb enable/disable) and web-auth secure (config network web-auth secureweb enable/disable), either of them should be enabled to make HTTPS redirect work.
- There might be slight reduction in the throughput when using redirection over https.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Reference
- 1000
- 1040
- 1100
- 1100_ap
- 1100_lap
- 1130_AG
- 1130_ap
- 1130_lap
- 1140
- 1140_ap
- 1140_lap
- 1200
- 1200_ap
- 1200_lap
- 1230_AG
- 1230_ap
- 1230_lap
- 1240_AG
- 1240_ap
- 1240_lap
- 1250
- 1250_ap
- 1250_lap
- 1260
- 1300
- 1300_bridge
- 1400
- 1400_bridge
- 1500
- 1500_map
- 1520
- 1550
- 1600
- 2000_wlc
- 2100_wlc
- 2500
- 2600
- 3300_Series_Mobility_Services_Engine
- 340_ap
- 3500
- 350_ap
- 3600
- 3750_wlc
- 3850
- 4400_wlc
- 4400_wlc ldap
- 500_lap
- 5500
- 5500_wlc
- 5505
- 5508
- 5700
- 5760
- 600_Series OfficeExtend_AP
- 7900_ip_phone
- 802.11a
- 802.11b
- 802.11g
- 802.1x
- 8500
- aaa
- active_directory
- air_cb21ag
- aironet
- aironet_antennas
- ap
- autonomous
- catalyst_3850
- cisco_5760_wlc
- cisco_prime_ncs
- converged_access
- eap
- eap_fast
- external_server
- hwic_ap
- lap
- leap
- lo
- lwapp
- ncs
- ngwc
- peap
- prime
- Prime_Network_Control_System
- radio
- radius
- roaming
- ssid
- tacacs
- virtual_wireless_controller
- wcs
- wgb
- wireless_lan_controller
- wireless_lan_controllers
- wism
- wlan
- wlc
- wlc_5500
- wlc_5508
- wlcm
- wlse
- wlsm
- wpa
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
It is really a headache for everybody, can you explain what type of perfomance impact happen ? it is because of cipher calculation in https or what ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Kamran,
As you see the warning while configuring this...it might hit the performance because of the reasons you mentioned....https will require ssl handshake etc. The impact might be negligible is some networks having less number of guest clients doing login simultaneously. There is no impact on any other stuff for example traffic forwarding/processes etc.
Regards
Dhiresh
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Do you know if WLC CWA with ISE supports to intercept https traffic and redirect to guest portal?
If not, any roadmap?
Thank you,
Bancha
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Vinay,
Thank you for the post. I wanted to add while it states web-auth secure. I also find it works with web-passthrough as well. Is it suppose to ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
After this command the redirection works, though the browser shows the certificate error("this connection is untrusted, google.com uses an invalid security certificate"). Is this normal?
I guess it is as the browser shows the wrong certificate(guest certificate) for the requested site(https://google.com).
Web Auth Secure Web ....................... Enable
Web Auth Secure Redirection ............... Enable
WLC version:WLC 5508
Product Version.................................. 8.0.121.0
Bootloader Version............................... 1.0.20
Field Recovery Image Version..................... 7.6.101.1
Can't this be solved so that for the user is transparent?
Thanks in advance for your help
Diego
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Diego,
I dont think there is any solution to this issue since there is no problem. We are trying to stop an HTTPS connection and presenting our page having certificate tied up to the virtual interface of the WLC. When client did DNS initially for goofle.com , it also noted its ip address. Now when HTTPS connection is hijacked , and WLC or some other page is presented , it doesnt have the ip address which it resolved for google, hence the error. This is because of come clients having high security and is by normal process.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks,
This link is very usefull
He wore quite some time looking for the solution to this error
I am very happy
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Dhiresh.
do we have already any solution for Certificate Error if using HTTPS Redirect?
our scenario is Secure Web Disable + HTTPS redirect while HTTP redirect working fine but
HTTPS redirect working with a Certificate error.
do you know if verisign certificate installed on the controller will help with get rid the certificate error while doing https redirect?
thanks a lot.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: