- Cisco Community
- シスコ コミュニティ
- セキュリティ
- [TKB] セキュリティ ドキュメント
- IBNSとIBNS 2.0
- RSS フィードを購読する
- 新着としてマーク
- 既読としてマーク
- ブックマーク
- 購読
- 印刷用ページ
- 不適切なコンテンツを報告
- RSS フィードを購読する
- 新着としてマーク
- 既読としてマーク
- ブックマーク
- 購読
- 印刷用ページ
- 不適切なコンテンツを報告
2020-09-19 03:19 AM
はじめに
IBNS2.0はFlex-auth等を含むIBNS(Identity-Based Networking Services)の新バージョンです。
旧来のものはIdentity-Based Networking Services(IBNS)[無印]か1.0と呼ばれています。
IBNS2.0はdocumentが比較的少ないため、本稿で旧来のものとの違いを中心に紹介します。詳しい情報は最後の参考文献やcommand referenceを参照ください。
本稿では
Switch Ports Model SW Version SW Image Mode
------ ----- ----- ---------- ---------- ----
* 1 40 C9300-24T 16.9.3 CAT9K_IOSXE BUNDLE
での出力例を使用します。
IBNSからIBNS 2.0へのconfigurationの変換
IBNSのconfig例
長くなりますが、変換前の状態のconfig例の関連部分を抜粋します。
C9300#sho run
(snip)
hostname C9300
(snip)
enable password cisco
!
aaa new-model
!
!
aaa group server radius ise24r
server name ise24a
!
aaa group server radius ise22r
server name ise22a
!
aaa authentication login default none
aaa authentication enable default none
aaa authentication dot1x default group ise24r
aaa authorization exec default none
aaa authorization network default group ise24r
aaa accounting dot1x default start-stop group ise24r
!
!
!
aaa session-id common
boot system switch all flash:cat9k_iosxe.16.06.06.SPA.bin
switch 1 provision c9300-24t
!
(snip)
ip routing
!
!
ip dhcp snooping vlan 1331
ip dhcp snooping
login on-success log
!
!
device-tracking tracking
!
device-tracking policy test1
no protocol udp
tracking enable
!
authentication mac-move permit
!
crypto pki trustpoint SLA-TrustPoint
(snip)
spanning-tree mode rapid-pvst
spanning-tree extend system-id
dot1x system-auth-control
dot1x critical eapol
!
(snip)
!
vlan 1331
!
!
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, L2 LVX data, LOGGING
(snip)
!
policy-map system-cpp-policy
class system-cpp-police-control-low-priority
!
(snip)
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
switchport access vlan 1331
switchport mode access
switchport voice vlan 101
device-tracking attach-policy test1
ip access-group ipv4preauthacl in
authentication control-direction in
authentication event fail action authorize vlan 100
authentication event server dead action authorize vlan 100
authentication event no-response action authorize vlan 100
authentication host-mode multi-auth
authentication open
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication timer inactivity server dynamic
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 5
dot1x max-reauth-req 3
spanning-tree portfast
!
interface GigabitEthernet1/0/6
switchport access vlan 1331
switchport mode access
authentication open
authentication port-control auto
mab
dot1x pae authenticator
spanning-tree portfast
!
interface GigabitEthernet1/0/7
(snip)
!
interface Vlan1331
ip address 172.31.1.25 255.255.255.0
!
(snip)
!
ip access-list extended ipv4preauthacl
permit ip any any
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
radius-server dead-criteria time 5 tries 3
radius-server deadtime 3
!
radius server ise24a
address ipv4 172.31.1.120 auth-port 1812 acct-port 1813
key cisco
!
radius server ise22a
address ipv4 172.31.1.100 auth-port 1812 acct-port 1813
key cisco
!
(snip)
!
end
IBNSかIBNS 2.0かの確認
Execでauthentication displayコマンドの実行が可能なIOS(-XE)では
C9300#authentication display ?
config-mode Display current config-mode
legacy Legacy configuration
new-style New style (c3pl) configuration
C9300#authentication display config-mode
Current configuration mode is legacy
のようにどちらを使用中か確認ができます。
legacyであればIBNS、new-styleであればIBNS 2.0と確認出来ます。
IBNS 2.0への変換
IBNS 無印で運用中のswitchは
C9300#authentication display new-style
Please note that while you can revert to legacy style
configuration at any time unless you have explicitly
entered new-style configuration, the following caveats
should be carefully read and understood.
(1) If you save the config in this mode, it will be written
to NVRAM in NEW-style config, and if you subsequently
reload the router without reverting to legacy config and
saving that, you will no longer be able to revert.
(2) In this and legacy mode, Webauth is not IPv6-capable. It
will only become IPv6-capable once you have entered new-
style config manually, or have reloaded with config saved
in 'authentication display new' mode.
(3) 'Default' and 'rollback' commands should not be used in this
display mode. Either remain in legacy display mode or switch
to new-style configuration mode before use.
c9300#
で、2.0のconfigに変換できます。
特定の作業をすると元には戻れなくなるので変換前configは別途flashに保存しておくのが無難です。
変換後のconfigには
class-map type control subscriber match-all AAA_SVR_DOWN_AUTHD_HOST
match result-type aaa-timeout
match authorization-status authorized
のような設定が含まれているので変換されたことがわかります(変換後の全体は後程触れます)。
しかし、既存のconfigが変換されただけでまだ
C9300#authentication display config-mode
Current configuration mode is legacy
C9300#
と、legacyのままなため、config modeで
C9300#conf t
Enter configuration commands, one per line. End with CNTL/Z.
C9300(config)#authentication convert-to new-style
This operation will permanently convert all relevant authentication commands to their CPL control-policy equivalents. As this conversion is irreversible and will disable the conversion CLI 'authentication display [legacy|new-style]', you are strongly advised to back up your current configuration before proceeding.
Do you wish to continue? [yes]: yes
C9300(config)#
とすると、
C9300#authentication display config-mode
Current configuration mode is new-style
C9300#
new-styleとなっており完全に切替わったことになります。
今回の例ではauthentication convert-to new-style前後でconfigの変更点はauthentication mac-move permitが消えたという点のにみになります。これは、IBNS 2.0ではaccess-session mac-move denyというコマンドに変わり、元の設定がpermitであったためdefaultであるno access-session mac-move denyがshow runで表示されなかったことによります。
こちらも長くなりますが、変換後(convert-toの前)の状態のconfig例の関連部分を抜粋します。
C9300#sho run
(snip)
hostname C9300
(snip)
enable password cisco
!
aaa new-model
!
!
aaa group server radius ise24r
server name ise24a
!
aaa group server radius ise22r
server name ise22a
!
aaa authentication login default none
aaa authentication enable default none
aaa authentication dot1x default group ise24r
aaa authorization exec default none
aaa authorization network default group ise24r
aaa accounting identity default start-stop group ise24r
!
!
!
!
!
!
aaa session-id common
boot system switch all flash:cat9k_iosxe.16.06.06.SPA.bin
switch 1 provision c9300-24t
!
(snip)
ip routing
!
!
ip dhcp snooping vlan 1331
ip dhcp snooping
login on-success log
!
!
device-tracking tracking
!
device-tracking policy test1
no protocol udp
tracking enable
!
authentication mac-move permit
!
crypto pki trustpoint SLA-TrustPoint
(snip)
spanning-tree mode rapid-pvst
spanning-tree extend system-id
service-template webauth-global-inactive
inactivity-timer 3600
service-template DEFAULT_LINKSEC_POLICY_MUST_SECURE
linksec policy must-secure
service-template DEFAULT_LINKSEC_POLICY_SHOULD_SECURE
linksec policy should-secure
service-template DEFAULT_CRITICAL_VOICE_TEMPLATE
voice vlan
service-template AUTH_FAIL_VLAN_Gi1/0/5
vlan 100
service-template CRITICAL_AUTH_VLAN_Gi1/0/5
vlan 100
service-template GUEST_VLAN_Gi1/0/5
vlan 100
dot1x system-auth-control
dot1x critical eapol
!
(snip)
!
vlan 1331
!
!
class-map type control subscriber match-all AAA_SVR_DOWN_AUTHD_HOST
match result-type aaa-timeout
match authorization-status authorized
!
class-map type control subscriber match-all AAA_SVR_DOWN_UNAUTHD_HOST
match result-type aaa-timeout
match authorization-status unauthorized
!
class-map type control subscriber match-all DOT1X
match method dot1x
!
class-map type control subscriber match-all DOT1X_FAILED
match method dot1x
match result-type method dot1x authoritative
!
class-map type control subscriber match-all DOT1X_MEDIUM_PRIO
match authorizing-method-priority gt 20
!
class-map type control subscriber match-all DOT1X_NO_RESP
match method dot1x
match result-type method dot1x agent-not-found
!
class-map type control subscriber match-all DOT1X_TIMEOUT
match method dot1x
match result-type method dot1x method-timeout
!
class-map type control subscriber match-all MAB
match method mab
!
class-map type control subscriber match-all MAB_FAILED
match method mab
match result-type method mab authoritative
!
!
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, L2 LVX data, LOGGING
(snip)
!
policy-map type control subscriber POLICY_Gi1/0/5
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x retries 2 retry-time 0 priority 10
event authentication-failure match-first
5 class DOT1X_FAILED do-until-failure
10 activate service-template AUTH_FAIL_VLAN_Gi1/0/5
20 authorize
10 class AAA_SVR_DOWN_UNAUTHD_HOST do-until-failure
10 activate service-template CRITICAL_AUTH_VLAN_Gi1/0/5
20 authorize
30 pause reauthentication
20 class AAA_SVR_DOWN_AUTHD_HOST do-until-failure
10 pause reauthentication
20 authorize
30 class DOT1X_NO_RESP do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
40 class MAB_FAILED do-until-failure
10 terminate mab
20 activate service-template GUEST_VLAN_Gi1/0/5
30 authorize
60 class DOT1X_TIMEOUT do-until-failure
10 terminate dot1x
20 activate service-template AUTH_FAIL_VLAN_Gi1/0/5
30 authorize
70 class always do-until-failure
10 terminate dot1x
20 terminate mab
30 authentication-restart 60
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x retries 2 retry-time 0 priority 10
event inactivity-timeout match-all
10 class always do-until-failure
10 clear-session
event authentication-success match-all
10 class always do-until-failure
10 activate service-template DEFAULT_LINKSEC_POLICY_SHOULD_SECURE
event violation match-all
10 class always do-until-failure
10 restrict
!
policy-map type control subscriber POLICY_Gi1/0/6
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x priority 10
event authentication-failure match-first
5 class DOT1X_FAILED do-until-failure
10 terminate dot1x
20 authentication-restart 60
10 class DOT1X_NO_RESP do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
20 class MAB_FAILED do-until-failure
10 terminate mab
20 authentication-restart 60
40 class always do-until-failure
10 terminate dot1x
20 terminate mab
30 authentication-restart 60
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x priority 10
event authentication-success match-all
10 class always do-until-failure
10 activate service-template DEFAULT_LINKSEC_POLICY_SHOULD_SECURE
!
policy-map system-cpp-policy
class system-cpp-police-control-low-priority
!
(snip)
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
switchport access vlan 1331
switchport mode access
switchport voice vlan 101
device-tracking attach-policy test1
ip access-group ipv4preauthacl in
authentication periodic
authentication timer reauthenticate server
access-session control-direction in
access-session port-control auto
mab
dot1x pae authenticator
dot1x timeout tx-period 5
dot1x max-reauth-req 3
spanning-tree portfast
service-policy type control subscriber POLICY_Gi1/0/5
!
interface GigabitEthernet1/0/6
switchport access vlan 1331
switchport mode access
access-session host-mode single-host
access-session port-control auto
mab
dot1x pae authenticator
spanning-tree portfast
service-policy type control subscriber POLICY_Gi1/0/6
!
interface GigabitEthernet1/0/7
(snip)
!
interface Vlan1331
ip address 172.31.1.25 255.255.255.0
!
(snip)
!
ip access-list extended ipv4preauthacl
permit ip any any
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
radius-server dead-criteria time 5 tries 3
radius-server deadtime 3
!
radius server ise24a
address ipv4 172.31.1.120 auth-port 1812 acct-port 1813
key cisco
!
radius server ise22a
address ipv4 172.31.1.100 auth-port 1812 acct-port 1813
key cisco
!
(snip)
!
end
IBNS[無印]とのconfigurationの違い
比較すると以下のような特徴が見えてきます。
-
aaa accounting dot1xがaaa accounting identityに変わっている。
-
service-template,class-map type control subscriber,policy-map type control subscriberが作られている。
-
interface内authentication commandが一部access-sessionに変わっている。
-
interface内にservice-policy type control subscriberとしてpolicy-mapが適用されている。
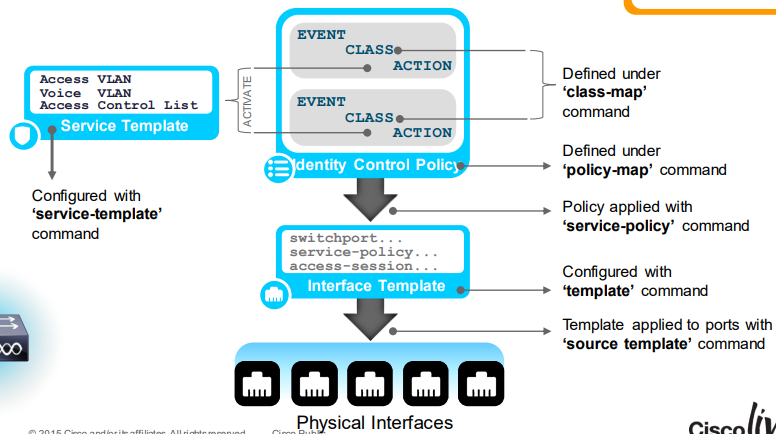
IBNS 2.0の3要素(Service-Template, Class-Map, Policy-Map)
IBNS 2.0で出てくるService-Template,Class-Map, Policy-MapはConfigurationで以下のような関係になっています。

今回の変換例を使用して説明します。
変換前の
interface GigabitEthernet1/0/5
switchport access vlan 1331
switchport mode access
switchport voice vlan 101
device-tracking attach-policy test1
ip access-group ipv4preauthacl in
authentication control-direction in
authentication event fail action authorize vlan 100
authentication event server dead action authorize vlan 100
authentication event no-response action authorize vlan 100
authentication host-mode multi-auth
authentication open
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication timer inactivity server dynamic
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 5
dot1x max-reauth-req 3
spanning-tree portfast
から、変換後のGI1/0/5用のpolicy-mapが
policy-map type control subscriber POLICY_Gi1/0/5
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x retries 2 retry-time 0 priority 10
event authentication-failure match-first
5 class DOT1X_FAILED do-until-failure
10 activate service-template AUTH_FAIL_VLAN_Gi1/0/5
20 authorize
10 class AAA_SVR_DOWN_UNAUTHD_HOST do-until-failure
10 activate service-template CRITICAL_AUTH_VLAN_Gi1/0/5
20 authorize
30 pause reauthentication
20 class AAA_SVR_DOWN_AUTHD_HOST do-until-failure
10 pause reauthentication
20 authorize
30 class DOT1X_NO_RESP do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
40 class MAB_FAILED do-until-failure
10 terminate mab
20 activate service-template GUEST_VLAN_Gi1/0/5
30 authorize
60 class DOT1X_TIMEOUT do-until-failure
10 terminate dot1x
20 activate service-template AUTH_FAIL_VLAN_Gi1/0/5
30 authorize
70 class always do-until-failure
10 terminate dot1x
20 terminate mab
30 authentication-restart 60
event agent-found match-all
(snip)
のように作成されます。上から2番目のauthentication-failureというEventに着目すると、各Class(DOT1X_FAILED, AAA_SVR_DOWN_UNAUTHOD_HOST,...)に対応するclass-mapが
class-map type control subscriber match-all DOT1X_FAILED
match method dot1x
match result-type method dot1x authoritative
class-map type control subscriber match-all AAA_SVR_DOWN_UNAUTHD_HOST
match result-type aaa-timeout
match authorization-status unauthorized
(snip)
のように作成されており、class-mapの中ではそのClassに該当するための条件がmatch文で定義され、Eventの中でそのClassに該当した場合のActionがpolicy-map内のclass内に定義されます。
例: (AAA serverがdownし認可されていない端末は、"再認証processを止め/CRITICAL_AUTH_VLAN_GI1/0/5に元づいたservice-templateが有効化され/認可される"というActionを実行する)
10 class AAA_SVR_DOWN_UNAUTHD_HOST do-until-failure
10 activate service-template CRITICAL_AUTH_VLAN_Gi1/0/5
20 authorize
30 pause reauthentication
Service-Templateは変換後のconfig内に
service-template CRITICAL_AUTH_VLAN_Gi1/0/5
vlan 100
のように定義されており、interface内service-policy文
interface GigabitEthernet1/0/5
(snip)
service-policy type control subscriber POLICY_Gi1/0/5
からgi1/0/5のいわゆるcritical vlanの動作となる流れとなります。
なお、policy-map内で使用できるeventには
C9300(config)#policy-map type control subscriber POLICY_Gi1/0/5
%Warning, modifying policy-map "POLICY_Gi1/0/5" may impact sessions hosted on ports for which "POLICY_Gi1/0/5" has already been applied.
C9300(config-event-control-policymap)#event ?
aaa-available aaa-available event
absolute-timeout absolute timeout event
agent-found agent found event
authentication-failure authentication failure event
authentication-success authentication success event
authorization-failure authorization failure event
authorization-success authorization success event
identity-update identity update event
inactivity-timeout inactivity timeout event
remote-authentication-failure authentication failure event
remote-authentication-success authentication remote success event
session-disconnected session disconnected event
session-started session started event
tag-added tag to apply event
tag-removed tag to remove event
template-activated template activated event
template-activation-failed template activation failed event
template-deactivated template deactivated event
template-deactivation-failed template deactivation failed event
timer-expiry timer-expiry event
violation session violation event
のものがあります。
複数のinterfaceでauth-manager関連の設定がされている場合、そのinterface毎にpolicy-mapが作成されるため、変換後のconfigは膨大になります。
上記の例で多くのEventやClassが出てきているのでどのようなものがあるか確認下さい。
IBNS 2.0にはconfig sizeを小さくする目的もあり、変換後のconfigはそのまま使用することも可能ですが同じ内容のpolicy-mapは共用すればconfig sizeを減らすことも可能です。変換後のconfigはあくまで変換後のconfigがどのようなものになるか想定するためのものと考えておくとよいと思います。
Interface-Template
config sizeを減らすという意味では上記の3要素以外にInterface-Templateというものがあります。
現在、変換後のconfigは
interface GigabitEthernet1/0/5
switchport access vlan 1331
switchport mode access
switchport voice vlan 101
device-tracking attach-policy test1
ip access-group ipv4preauthacl in
authentication periodic
authentication timer reauthenticate server
access-session control-direction in
access-session port-control auto
mab
dot1x pae authenticator
dot1x timeout tx-period 5
dot1x max-reauth-req 3
spanning-tree portfast
service-policy type control subscriber POLICY_Gi1/0/5
!
interface GigabitEthernet1/0/6
switchport access vlan 1331
switchport mode access
access-session host-mode single-host
access-session port-control auto
mab
dot1x pae authenticator
spanning-tree portfast
service-policy type control subscriber POLICY_Gi1/0/6
!
となっていますが、
template AUTHPORT1
spanning-tree portfast
dot1x pae authenticator
switchport access vlan 1331
switchport mode access
switchport voice vlan 101
mab
access-session port-control auto
authentication periodic
authentication timer reauthenticate server
なtemplateを作成しておくと、
interface GigabitEthernet1/0/5
device-tracking attach-policy test1
ip access-group ipv4preauthacl in
access-session control-direction in
dot1x timeout tx-period 5
dot1x max-reauth-req 3
source template AUTHPORT1
service-policy type control subscriber POLICY_Gi1/0/5
!
interface GigabitEthernet1/0/6
access-session host-mode single-host
source template AUTHPORT1
service-policy type control subscriber POLICY_Gi1/0/6
!
となります。この例では対象interfaceが二つしかないので効果はあまり感じませんが、数十のinterfaceで設定されていると効果が出てきます。
templateを展開後のconfigは
C9300(config-if)#do sho derived-config int gi1/0/5
Building configuration...
Derived configuration : 490 bytes
!
interface GigabitEthernet1/0/5
switchport access vlan 1331
switchport mode access
switchport voice vlan 101
device-tracking attach-policy test1
ip access-group ipv4preauthacl in
authentication periodic
authentication timer reauthenticate server
access-session control-direction in
access-session port-control auto
mab
dot1x pae authenticator
dot1x timeout tx-period 5
dot1x max-reauth-req 3
spanning-tree portfast
service-policy type control subscriber POLICY_Gi1/0/5
end
で、確認可能です。Interface-Templateにservice-policy type control subscriberコマンドを入れることも可能です。
Service-TemplateとInterface-Templateで違うconfigをまとめています。
IBNS[無印]との動作の違い
IBNSとIBNS 2.0で動作の違いや新機能がありますので簡単に上げておきます。詳細は参考資料をご覧ください。
-
Concurrent Authentication
IBNSではflexauthは設定された順番(802.1x -> MAB等)で必ず実施されるため、後の順番のものは接続できるまでに時間がかかってしまいます。IBNS 2.0では特定の端末の接続に関して802.1xとMABを同時に試行可能です。(ただし、本来は不要なrequestがRADIUS serverに飛ぶためRADIUS serverから見ると高負荷になりうる点とのトレードオフになります) -
Critical Authorization
IBNSではcritical vlanという用語になっていましたが、IBNS 2.0ではAAA serverとの通信が全滅の場合、vlan以外にACL,SGTの指定やNAD localで指定したMAC addressの通信を許すといった幅広い認可の内容になり、またNADがcritical状態になる以前の端末の認可状況によって動作を変えることが可能になっています。 -
Differentiated Authentication
port毎にどのAAA serverを使った認証/認可にするかや802.1xやMABといったAuthentication method毎にどのAAA serverを使用するかを設定できます。
参考資料
BRKSEC-2691 :IBNS 2.0: New-style 802.1X and More
(弊社サイトでの公開が終了しているようなので、本稿に添付します。)
ISE Secure Wired Access Prescriptive Deployment Guide
検索バーにキーワード、フレーズ、または質問を入力し、お探しのものを見つけましょう
シスコ コミュニティをいち早く使いこなしていただけるよう役立つリンクをまとめました。みなさんのジャーニーがより良いものとなるようお手伝いします
下記より関連するコンテンツにアクセスできます