- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Networking
- How do I configure ACE30 to allow server to server and server to
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2012 02:37 PM
I have a ACE30 with 2 client vlans and 2 server vlans in a 2-arm routed mode. I want to allow server initiated traffic from either server vlan to access both client vlans via a VIP and also allow server to server traffic between the 2 server vlans via the server IP address. This is all in a single context. Attached is a diagram of the environment. The server's gateway is the ACE interface for that particular vlan.
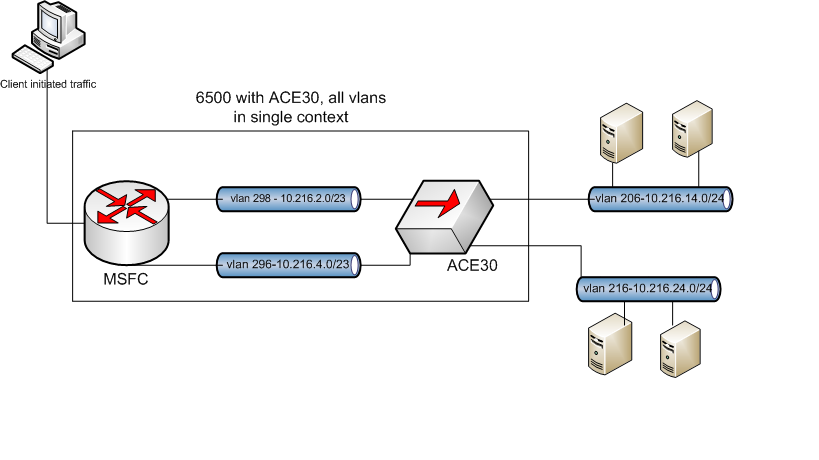
so servers on vlan 206 will initiate traffic to either vlan 296 or 298 and therefore load balance to servers on either vlan 206 or 216. same goes for server vlan 216.
In conjunction with that how do i configure the ACE so that the servers in one vlan can talk to the servers in the other via directly via their IP address. for instance the source would be vlan 206 and the destination would be vlan.
Thank you
Tony.
Solved! Go to Solution.
- Labels:
-
Application Networking
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 10:18 AM
Tony-
All you need to do is create a nat pool on each of the server vlans. Create a new policy map multimatch and put the vip classes in it. Apply both nat statements to all vips in the policy. Then apply the multmatch to each of the server vlans. By doing this, only traffic headed to a VIP will be natted. Server to server communication will not apply.
Server traffic between the vlans is only blocked via ACL by default, you just need to apply an inbound ACL to permit whatever you want to allow.
Regards,
Chris Higgins
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2012 03:54 PM
Not exactly, no. This:
policy-map multi-match INTRA-server_P
class LYNCP2F_C
loadbalance vip inservice
loadbalance policy LYNCP2F_P
loadbalance vip icmp-reply active
nat dynamic 2 vlan 246
nat dynamic 1 vlan 226
class LYNCP-FE_C
loadbalance vip inservice
loadbalance policy LYNCP-FE_P
loadbalance vip icmp-reply active
nat dynamic 2 vlan 246
nat dynamic 1 vlan 226
interface vlan 226
description Intranet Services Server Vlan 226
ip address 10.192.34.2 255.255.255.0
alias 10.192.34.1 255.255.255.0
peer ip address 10.192.34.3 255.255.255.0
no icmp-guard
access-group input ALL-IN
nat-pool 1 10.192.34.254 10.192.34.254 netmask 255.255.255.0 pat
service-policy input INTRA-server_P
no shutdown
interface vlan 246
description Intranet Services Server Vlan 246
ip address 10.192.44.2 255.255.255.0
alias 10.192.44.1 255.255.255.0
peer ip address 10.192.44.3 255.255.255.0
no icmp-guard
access-group input ALL-IN
nat-pool 2 10.192.44.254 10.192.44.254 netmask 255.255.255.0 pat
service-policy input INTRA-server_P
no shutdown
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 10:18 AM
Tony-
All you need to do is create a nat pool on each of the server vlans. Create a new policy map multimatch and put the vip classes in it. Apply both nat statements to all vips in the policy. Then apply the multmatch to each of the server vlans. By doing this, only traffic headed to a VIP will be natted. Server to server communication will not apply.
Server traffic between the vlans is only blocked via ACL by default, you just need to apply an inbound ACL to permit whatever you want to allow.
Regards,
Chris Higgins
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2012 07:50 AM
Chris, does this look correct based on your description of how to configure:
class-map match-all REAL-SERVERS-VL226
2 match source-address 10.192.34.0 255.255.255.0
class-map match-all REAL-SERVERS-VL246
2 match source-address 10.192.44.0 255.255.255.0
policy-map multi-match INTRA-server_P
class LYNCP2F_C
loadbalance vip inservice
loadbalance policy LYNCP2F_P
loadbalance vip icmp-reply active
nat dynamic 5 vlan 246
class LYNCP-FE_C
loadbalance vip inservice
loadbalance policy LYNCP-FE_P
loadbalance vip icmp-reply active
class REAL-SERVERS-VL226
nat dynamic 1 vlan 226
class REAL-SERVERS-VL246
nat dynamic 2 vlan 246
interface vlan 226
description Intranet Services Server Vlan 226
ip address 10.192.34.2 255.255.255.0
alias 10.192.34.1 255.255.255.0
peer ip address 10.192.34.3 255.255.255.0
no icmp-guard
access-group input ALL-IN
nat-pool 1 10.192.34.254 10.192.34.254 netmask 255.255.255.0 pat
service-policy input INTRA-server_P
no shutdown
interface vlan 246
description Intranet Services Server Vlan 246
ip address 10.192.44.2 255.255.255.0
alias 10.192.44.1 255.255.255.0
peer ip address 10.192.44.3 255.255.255.0
no icmp-guard
access-group input ALL-IN
nat-pool 2 10.192.44.254 10.192.44.254 netmask 255.255.255.0 pat
service-policy input INTRA-server_P
no shutdown
interface vlan 292
description Intranet Services Client Vlan 292
ip address 10.192.8.4 255.255.254.0
alias 10.192.8.6 255.255.254.0
peer ip address 10.192.8.5 255.255.254.0
mac-sticky enable
no icmp-guard
access-group input ALL-IN
no shutdown
interface vlan 294
description Intranet Services Client Vlan 294
ip address 10.192.6.4 255.255.254.0
alias 10.192.6.6 255.255.254.0
peer ip address 10.192.6.5 255.255.254.0
mac-sticky enable
no icmp-guard
access-group input ALL-IN
no shutdown
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2012 03:54 PM
Not exactly, no. This:
policy-map multi-match INTRA-server_P
class LYNCP2F_C
loadbalance vip inservice
loadbalance policy LYNCP2F_P
loadbalance vip icmp-reply active
nat dynamic 2 vlan 246
nat dynamic 1 vlan 226
class LYNCP-FE_C
loadbalance vip inservice
loadbalance policy LYNCP-FE_P
loadbalance vip icmp-reply active
nat dynamic 2 vlan 246
nat dynamic 1 vlan 226
interface vlan 226
description Intranet Services Server Vlan 226
ip address 10.192.34.2 255.255.255.0
alias 10.192.34.1 255.255.255.0
peer ip address 10.192.34.3 255.255.255.0
no icmp-guard
access-group input ALL-IN
nat-pool 1 10.192.34.254 10.192.34.254 netmask 255.255.255.0 pat
service-policy input INTRA-server_P
no shutdown
interface vlan 246
description Intranet Services Server Vlan 246
ip address 10.192.44.2 255.255.255.0
alias 10.192.44.1 255.255.255.0
peer ip address 10.192.44.3 255.255.255.0
no icmp-guard
access-group input ALL-IN
nat-pool 2 10.192.44.254 10.192.44.254 netmask 255.255.255.0 pat
service-policy input INTRA-server_P
no shutdown
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2012 07:06 AM
Thanks Chris.
I get it now.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
