- Cisco Community
- Technology and Support
- Online Tools and Resources
- Cisco Bug Discussions
- Re: CSCvg10793%20-%20Key%20Reinstallation%20attacks%20against%20WPA%20protocol
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CSCvg10793%20-%20Key%20Reinstallation%20attacks%20against%20WPA%20protocol
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2017 07:56 AM - edited 03-20-2019 09:36 PM
Looking at the Description of the bug report it is very clear this affects ALL AP's and ALL current software versions, because is it vulnerability in WPA. But ... if I look at the details of this report, I only see the 1850 and two software versions listed as affected, and several fixed software versions and the bug status of "fixed". It looks really stupid.
- Labels:
-
Cisco Bugs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2017 09:01 AM - edited 10-16-2017 09:03 AM
Yeah, I'm also curious how it was "fixed" and whether going to the "fixed" version will cause issues with client compatibility. I also don't see any of the fixed" releases as available for download from CCO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2017 11:37 PM - edited 10-17-2017 12:53 AM
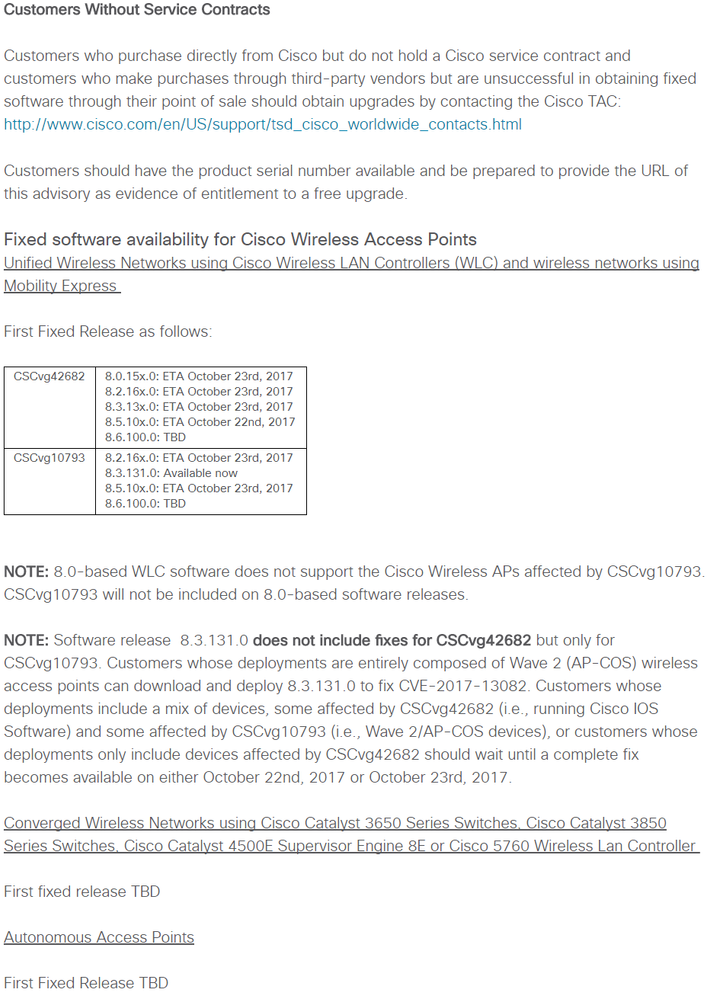
Did you take a look at the relevant security advisory? You can see the fixed AireOS software versions within the "vulnerable products"paragraph.
Summarize
In case you have a 1800/2800/3800 access-points you have to wait for 8.2.170.0 / 8.3.131.0 or contact TAC for an escalation image. For the access-points based on IOS code (2600,3700 etc.) you can already go to 8.3.130.0. Cisco will also publish a fixed 8.0 release for customers with older access-point types like the 1242 (8.0.15x.0).
Keep in mind that the attacker needs to be able to perform MAC spoofing, which is something you should already monitor on as wireless network administrator with the help of wIPS. One exception is CVE-2017-13082 which hits 802.11r, the workaround for this specific CVE is to disable 802.11r. This is the only CVE for which the software on the infrastructure side needs to be really fixed, for all the other CVEs the end-point software need to be fixed. However, these CVEs can be mitigated within the software on the infrastructure side which is the what Cisco does with these releases.
I would stick to the regular software upgrade schedule/process for both the infrastructure and end-point side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 05:40 AM
I did.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvg10793
Known Fixed Releases:
8.0.150.0(ED)
8.2.161.0(ED)
8.5.103.0(ED)
Not much overlap there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2017 12:02 PM
It would also be nice to have some mention of WLC if affected and versions that include fixed firmware for APs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 12:11 AM
This vulnerability affects anything with a wireless NIC. It's not just wireless AP but also wireless clients. Patching the client will fix 9 out of 10 vulnerabilities but not CVE-2017-13082.
Perspective About the Recent WPA Vulnerabilities (KRACK Attacks)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 03:56 PM - edited 10-20-2017 05:07 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 01:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2017 12:50 AM
Correct, there is 8.3.132.0 and again the information in the bug report is therefore incorrect/outdated, because the 8.3(130.6) release is still mentioned in there, but that is a TAC release only. The mentioned affected releases start at 8.2, but that is also not correct. The 802.11r functionality was introduced in 7.2, so all releases as of 7.2 are vulnerable. It is my first experience with bug reports and PSIRT, but to me it looks like Cisco was caught by surprise and has problems keeping different sources correct and up-to-date at the same time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2017 01:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2017 03:46 AM
@Martin2m2 wrote:
Correct, there is 8.3.132.0 and again the information in the bug report is therefore incorrect/outdated, because the 8.3(130.6) release is still mentioned in there, but that is a TAC release only. The mentioned affected releases start at 8.2, but that is also not correct. The 802.11r functionality was introduced in 7.2, so all releases as of 7.2 are vulnerable. It is my first experience with bug reports and PSIRT, but to me it looks like Cisco was caught by surprise and has problems keeping different sources correct and up-to-date at the same time.
A quick update to anyone reading this thread and intending to upgrade to 8.3.132.0:
Cisco TAC has recommended anyone to HOLD OFF upgrading to 8.3.132.0. TAC has identified a Severity 1 bug which causes the controller to crash after upgrading to 8.3.132.0.
There are no reported issues in regards to other versions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2017 04:27 AM
To summarize the current situation: stick with your current AireOS release, make sure to patch your clients ASAP and if you are really worried you can change the EAPoL key retry timers and disable 802.11r on your controller to mitigate all the CVE's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2017 02:29 AM
So what now if you are a 8.3 customer?
The PSIRT notes this new bug: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20171016-wpa
NOTE: As of October 25, 2017, all published 8.3.13x.0 releases are impacted by Cisco bug ID CSCvf87731. Customers should work with their support provider to determine if this bug may impact their deployment and if they should postpone a software upgrade until a fix becomes available.
? When is "until a fix becomes available"?
The bug report is useless for 8.3 customers. The bug is listed as fixed without mentioning 8.3.132.0 as affected and without having a fix in a 8.3 release.
It leaves the big question: Will there be a 8.3.x fix to both the wifi WPA bug and this new bug? And when?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2017 02:35 AM - edited 10-30-2017 02:36 AM
Based on the "TAC Recommended AireOS Builds" technote, a new version for both 8.2 and 8.3 will be published on CCO tomorrow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2017 02:42 AM
Thanks for the help. Should I have known about this troubleshoot technote?
It maybe a good idea if Cisco updates the PSIRT and the bug report to mention this new information.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide