- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Applications
- Jabber Revoked certificate warning
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Jabber Revoked certificate warning
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2018 04:44 PM - edited 03-17-2019 07:25 PM
Hi Folks,
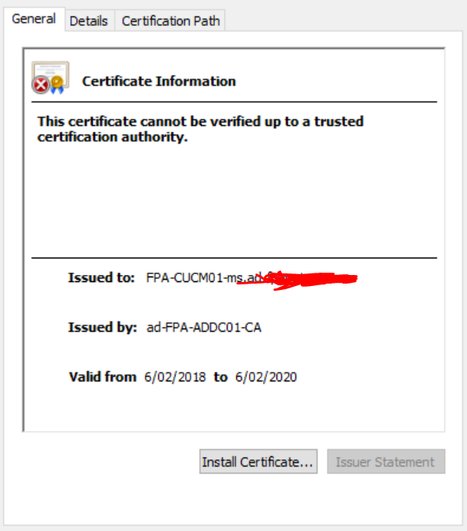
We have implemented Jabber for one of our customer, and everything works properly. However when we try to login internally, it gives an error that the current server certificate is revoked, however i can confirm that certificate is valid.
2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\utils\AltNameParserImpl.cpp(162)] [csf.cert.utils] [csf::cert::parseSubjectCNField] - Subject CN field: 'FPA-CUCM01-ms.ad.fpapatents.com'
2018-03-16 13:59:35,639 INFO [0x000019fc] [rc\cert\utils\AltNameParserImpl.cpp(255)] [csf.cert.utils] [csf::cert::AltNameParserImpl::parse] - number of Subject Alt Name fields : 5
2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\utils\AltNameParserImpl.cpp(102)] [csf.cert.utils] [csf::cert::parseDNSField] - parsed dnsName : FPA-IMP02.domain.com2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\utils\AltNameParserImpl.cpp(102)] [csf.cert.utils] [csf::cert::parseDNSField] - parsed dnsName : FPA-CUCM01.domain.com2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\utils\AltNameParserImpl.cpp(102)] [csf.cert.utils] [csf::cert::parseDNSField] - parsed dnsName : FPA-IMP01.domain.com2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\utils\AltNameParserImpl.cpp(102)] [csf.cert.utils] [csf::cert::parseDNSField] - parsed dnsName : domain.com2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\utils\AltNameParserImpl.cpp(102)] [csf.cert.utils] [csf::cert::parseDNSField] - parsed dnsName : FPA-CUCM02.domain.com2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\utils\KeyUsageParserImpl.cpp(62)] [csf.cert.utils] [csf::cert::KeyUsageParserImpl::parse] - Basic Key Usage in cert: [DIGITAL_SIGNATURE, KEY_ENCIPHERMENT], Extended Key Usage in cert: [SERVER_AUTH, CLIENT_AUTH]
2018-03-16 13:59:35,639 DEBUG [0x000019fc] [rc\cert\common\BaseCertVerifier.cpp(161)] [csf.cert.] [csf::cert::BaseCertVerifier::doVerifyCertificate] - About to verify the certificate.
2018-03-16 13:59:35,640 INFO [0x000019fc] [rc\cert\win32\Win32CertVerifier.cpp(262)] [csf.cert.win32] [csf::cert::Win32CertVerifier::loadCertificateChain] - Certificate Chain status 0x4
2018-03-16 13:59:35,640 INFO [0x000019fc] [rc\cert\win32\Win32CertVerifier.cpp(327)] [csf.cert.win32] [csf::cert::Win32CertVerifier::verifySslPolicy] - Ignoring errors due to Invalid CN
2018-03-16 13:59:35,640 INFO [0x000019fc] [rc\cert\win32\Win32CertVerifier.cpp(300)] [csf.cert.win32] [csf::cert::Win32CertVerifier::verifyPolicies] - SSL Policy status 0x2148081680
2018-03-16 13:59:35,640 INFO [0x000019fc] [rc\cert\win32\Win32CertVerifier.cpp(311)] [csf.cert.win32] [csf::cert::Win32CertVerifier::verifyPolicies] - Basic Constraints Policy status 0x0
2018-03-16 13:59:35,640 DEBUG [0x000019fc] [rc\cert\win32\Win32CertVerifier.cpp(146)] [csf.cert.win32] [csf::cert::Win32CertVerifier::verifyCertificate] - Certificate validation response is 'invalid'
2018-03-16 13:59:35,641 DEBUG [0x000019fc] [n\CertVerificationFailureManager.cpp(81)] [csf.cert] [csf::cert::CertVerificationFailureManager::canBeAccepted] - About to check if the Invalid Cert can be accepted.
2018-03-16 13:59:35,641 DEBUG [0x000019fc] [\CertVerificationFailureManager.cpp(105)] [csf.cert] [csf::cert::CertVerificationFailureManager::canBeAccepted] - About to enforce UserInteractingInvalidCertManagementPolicy.
2018-03-16 13:59:35,641 WARN [0x000019fc] [ctingInvalidCertManagementPolicy.cpp(56)] [csf.cert] [csf::cert::UserInteractingInvalidCertManagementPolicy::enforce] - Invalid certificate management policy enforcement does not manage failures reporting INVALID_REVOKED error
2018-03-16 13:59:35,641 DEBUG [0x000019fc] [\CertVerificationFailureManager.cpp(107)] [csf.cert] [csf::cert::CertVerificationFailureManager::canBeAccepted] - UserInteractingInvalidCertManagementPolicy enforced with result: SUCCESS
2018-03-16 13:59:35,641 DEBUG [0x000019fc] [mon\PlatformVerificationHandler.cpp(211)] [csf.cert] [csf::cert::PlatformVerificationHandler::showErrorNotification] - Notifying the InvalidCertListener about certificate rejection
2018-03-16 13:59:35,641 DEBUG [0x000019fc] [\InvalidCertNotificationManager.cpp(205)] [csf.cert] [csf::cert::InvalidCertNotificationManager::reportRejectedCert] - Sending a rejected invalid cert event to the InvalidCertListener for cert with fingerprint 76 8c 7b fa 52 97 39 ef 5b 77 f4 68 a5 f4 31 5f 3b 89 98 f2
2018-03-16 13:59:35,641 DEBUG [0x000019fc] [l\InvalidCertificateHandlerImpl.cpp(234)] [invalid-certificate-handler] [CSFUnified::InvalidCertificateHandlerImpl::OnRejectedInvalidCert] - About to queue a ServiceEvent reporting "invalid certificate rejected" to Dispatcher Thread
2018-03-16 13:59:35,641 DEBUG [0x000019fc] [mmon\PlatformVerificationHandler.cpp(62)] [csf.cert] [csf::cert::PlatformVerificationHandler::handlePlatformVerificationResultSynchronously] - finalResult: FAILURE
2018-03-16 13:59:35,641 INFO [0x000019fc] [etutils\adapters\HttpCertAdapter.cpp(93)] [csf.httpclient] [csf::netutils::adapters::HttpCertAdapter::verifyCertificate] - *-----* Certificate Verification Result: FAILURE
Its complaining about the certificate while connecting to CUCM. However if you see below it has validity till 2020.
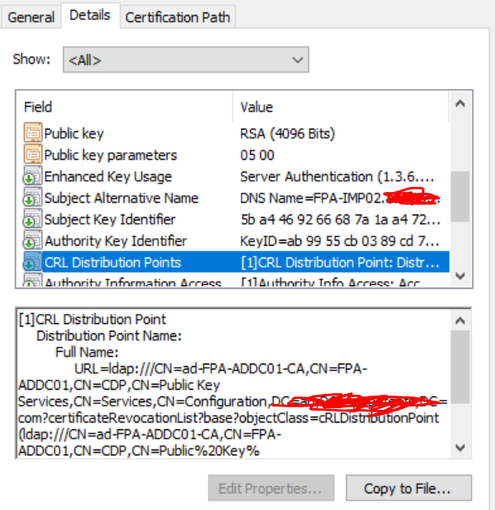
But if you look at the CRL Distribution point here, it is in LDAP format, but when i search through Jabber document i think you need the CRL point in https/http format, as mentioned in below document.
I think i am missing that
Has anyone witnessed it before? I just want to verify if my understanding is correct before it go to customer.
Regards,
Alok
- Labels:
-
Other Collaboration Applications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2025 02:01 AM
Yes Alok we have seen this issue.
While generating a new CA Certificate, the Public CA Revoked the old certificate lead failure of Jabber Login, when Jabber logged in, its checking the CRL (where the URL of the Revocation) list is mentioned, as the SN of the current certificate matches in the Revocation list , the cert failure happen and jabber stops the login process.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide