- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center and Cloud Knowledge Base
- ACI Service Graph: L4-L7 integration of ASA in multi-context mode
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-28-2018 08:56 PM - edited 03-01-2019 06:07 AM
Introduction
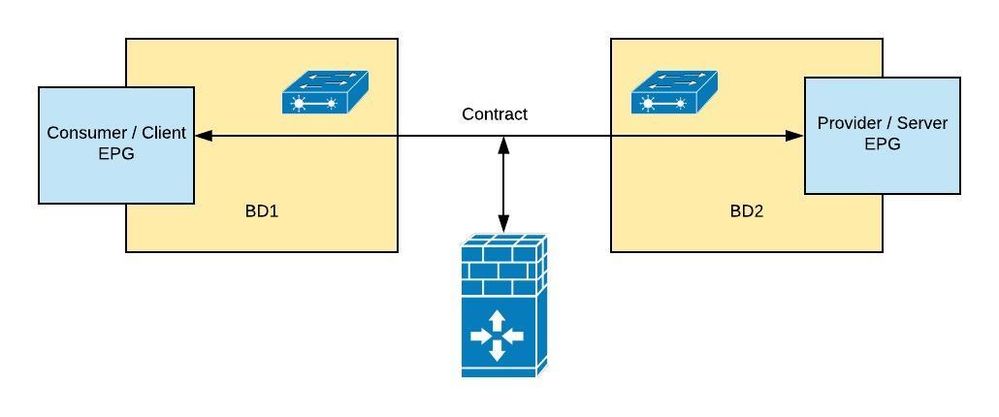
In this article, we will learn the ASA Service graph integration in GoTo / Routed mode deployment (managed mode) when ASA is in the multi-context mode.
Prerequisites
This configuration uses the follownig setup
- Hardware: ASA5555 / ASA version: 9.4(4) / Device manager version: 7.9(1)
- ACI version: 2.2(2q)
Requirements
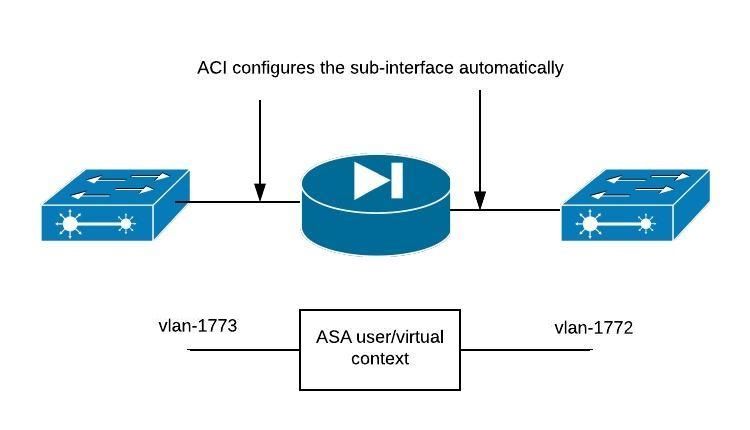
ASA Multicontext support enables the same physical appliance to be used for multiple tenants. With ASA, you can partition a single physical ASA into multiple virtual firewalls, known as security/virtual contexts. Each context acts as an independent device with its own security policy, interfaces, and management IP address. The APIC does not create the ASA contexts; they must be pre-created and the management interface shall be configured in the ASA prior to creating the L4-L7 device from APIC. The allocate-interface shall be done on the system context, the firewall configuration shall be done on a virtual/user context, and the ACI fabric policy shall be done by the APIC. The APIC needs to communicate to ASA with the system context and each virtual context.
Here is the sample topology
ASA Configuration
The ASA contexts shall be created directly through the ASA CLI. The following shall be carried out to create an ASA context and prepare before starting to create L4-L7 device in ACI.
1. Creating and context "dummies"
ASAFab3(config)# context dummies
Creating context 'dummies'... Done. (14)
2. Allocate management interface to the new context, this is required for APIC to manage the virtual/user context
ASAFab3(config-ctx)# allocate-interface management0/0
ASAFab3(config-ctx)# config-url disk0:/dummies.cfg
WARNING: Could not fetch the URL disk0:/dummies.cfg
INFO: Creating context with default config
3. Changeto context to carryout the required config
ASAFab3(config-ctx)# changeto context dummies
ASAFab3/dummies(config)# show int
Interface Management0/0 "", is up, line protocol is up
Available but not configured via nameif
4. Make sure that the management interface is configured appropriately
ASAFab3/dummies(config)# int Management 0/0
ASAFab3/dummies(config-if)# nameif management <<<< use name management >>>
INFO: Security level for "management" set to 0 by default.
ASAFab3/dummies(config-if)# security-level 100
ASAFab3/dummies(config-if)# ip address 10.66.88.22 255.255.255.224
ASAFab3/dummies(config-if)# no shut
ASAFab3/dummies(config-if)# route management 0.0.0.0 0.0.0.0 10.66.88.1 1
ASAFab3/dummies(config)#
5. Verify the management interface status
ASAFab3/dummies(config)# show int
Interface Management0/0 "management", is up, line protocol is up
MAC address 84b2.6191.8929, MTU 1500
IP address 10.66.88.22, subnet mask 255.255.255.224
Traffic Statistics for "management":
36 packets input, 15420 bytes
4 packets output, 168 bytes
26 packets dropped
Management-only interface. Blocked 0 through-the-device packets
ASAFab3/dummies(config)#
7. Create the admin user for virtual/user context
ASAFab3/dummies(config)# username admin password p@$$w0rd privilege 15
ASAFab3/dummies(config)# aaa authentication ssh console LOCAL
8. enable ssh for virtual/user context
ASAFab3/dummies(config)# ssh timeout 60
ASAFab3/dummies(config)# no ssh stricthostkeycheck
ASAFab3/dummies(config)# access-list all extended permit ip any any
ASAFab3/dummies(config)# crypto key generate rsa modulus 2048 noconfirm
INFO: The name for the keys will be: <Default-RSA-Key>
Keypair generation process begin. Please wait...
ASAFab3/dummies(config)# ssh 0.0.0.0 0.0.0.0 management
9. Enable http server for virtual/user context
ASAFab3/dummies(config)# http server enable
ASAFab3/dummies(config)# http 0.0.0.0 0.0.0.0 management
ASAFab3/dummies(config)#
10. make sure that you can do ssh from your desktop to ASA virtual/user context through the context maagement IP
ABEGEORG-M-31UY:BD_CREATE abeygeorge$ ssh admin@10.66.88.22
The authenticity of host '10.66.88.22 (10.66.88.22)' can't be established.
RSA key fingerprint is SHA256:QfCuhq4QKJzjKyMlg53soGrU9js6stRRIMiDLwmv2Ik.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.66.88.22' (RSA) to the list of known hosts.
admin@10.66.88.22's password:
Type help or '?' for a list of available commands.
ASAFab3/dummies>
11. Make sure that you can login to virual/user context using ADSM
12. Make sure that the data interface is created at the ASA (context: system)
ASAFab3# show port-channel summary
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
U - in use N - not in use, no aggregation/nameif
M - not in use, no aggregation due to minimum links not met
w - waiting to be aggregated
Number of channel-groups in use: 1
Group Port-channel Protocol Span-cluster Ports
------+-------------+---------+------------+------------------------------------
10 Po10(U) LACP No Gi0/3(P) Gi0/4(P)
ASAFab3#
Components Used
- Hardware: ASA5555 / ASA version: 9.4(4) / Device manager version: 7.9(1)
- ACI version: 2.2(2q)
Configure
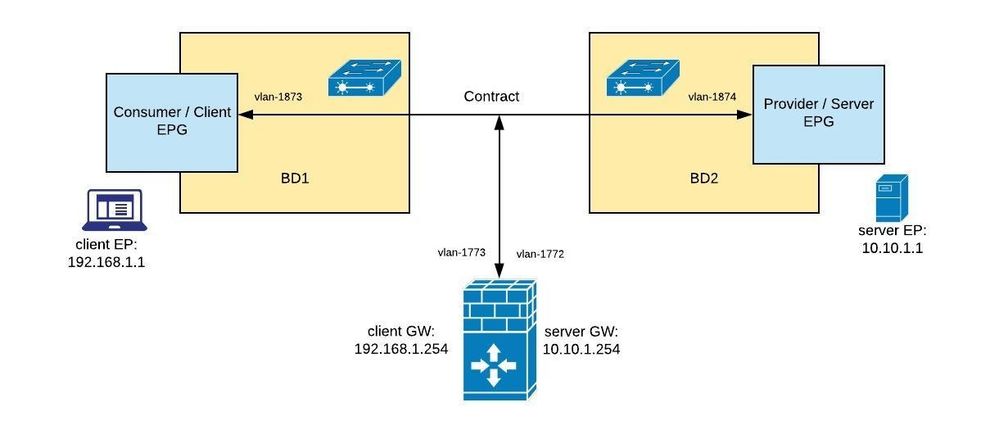
Network Diagram
The following diagram describes the endpint IP, gateway IP, vlan(s) and its relationships.
Configurations
The following steps shall be carried out to create the client/consumer and server/provider EPG
1. In this example, we used the following information to create internal/server/provider & external/client/consumer BD and EPG
EPG (external) -> name: external, domain: abegeorg-asa-phyDom, encap: vlan-1783
BD (external) -> name: external, unicast routing: disabled
External endpoint IP -> 192.168.1.1/24, default GW: 192.168.1.254/24 (gateway is expected to be at firewall outside)
EPG (internal) -> name: internal, domain: abegeorg-asa-phyDom, encap: vlan-1784
BD (internal) -> name: internal, unicast routing: disabled
Internal endpoint IP -> 10.10.1.1/24, default GW: 10.10.1.254/24 (gateway is expected to be at firewall inside)
2. Check the vlan is deployed to the leaf swich
leaf101# show vlan extended
< snip >
45 dummies:external active Eth1/35, Po4
46 dummies:asa:external active Eth1/35, Po4
47 dummies:internal active Eth1/35, Po4
48 dummies:asa:internal active Eth1/35, Po4
< snip >
45 enet CE vxlan-16187321
46 enet CE vlan-1783
47 enet CE vxlan-16580490
48 enet CE vlan-1784
leaf101#
3. Verify the endpoints are learned
leaf101# show system internal epm endpoint vrf dummies:dummies
VRF : dummies:dummies ::: Context id : 34 ::: Vnid : 2916354
MAC : dcce.c15b.1e44 ::: Num IPs : 0
Vlan id : 48 ::: Vlan vnid : 10496 ::: VRF name : dummies:dummies
BD vnid : 16580490 ::: VRF vnid : 2916354
Phy If : 0x16000003 ::: Tunnel If : 0
Interface : port-channel4
Flags : 0x80004805 ::: sclass : 32770 ::: Ref count : 4
EP Create Timestamp : 01/18/2018 11:30:00.219492
EP Update Timestamp : 01/18/2018 11:30:00.219492
EP Flags : local|vPC|MAC|sclass|timer|
::::
MAC : dcce.c15b.1e44 ::: Num IPs : 0
Vlan id : 46 ::: Vlan vnid : 10495 ::: VRF name : dummies:dummies
BD vnid : 16187321 ::: VRF vnid : 2916354
Phy If : 0x16000003 ::: Tunnel If : 0
Interface : port-channel4
Flags : 0x80004805 ::: sclass : 16388 ::: Ref count : 4
EP Create Timestamp : 01/18/2018 11:29:22.720012
EP Update Timestamp : 01/18/2018 11:29:48.662199
EP Flags : local|vPC|MAC|sclass|timer|
::::
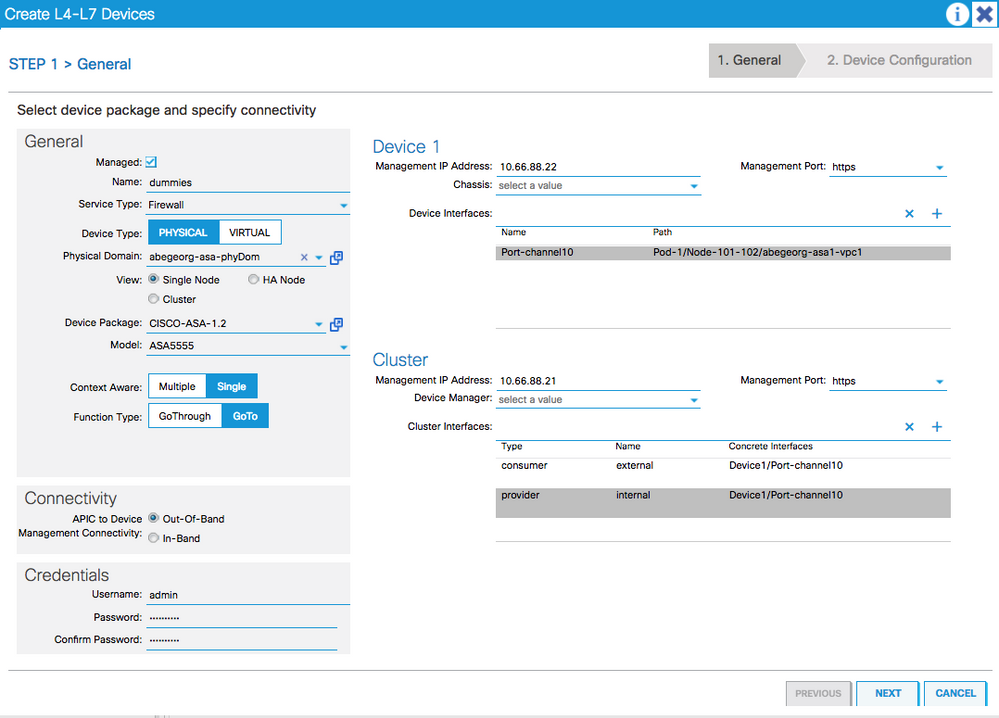
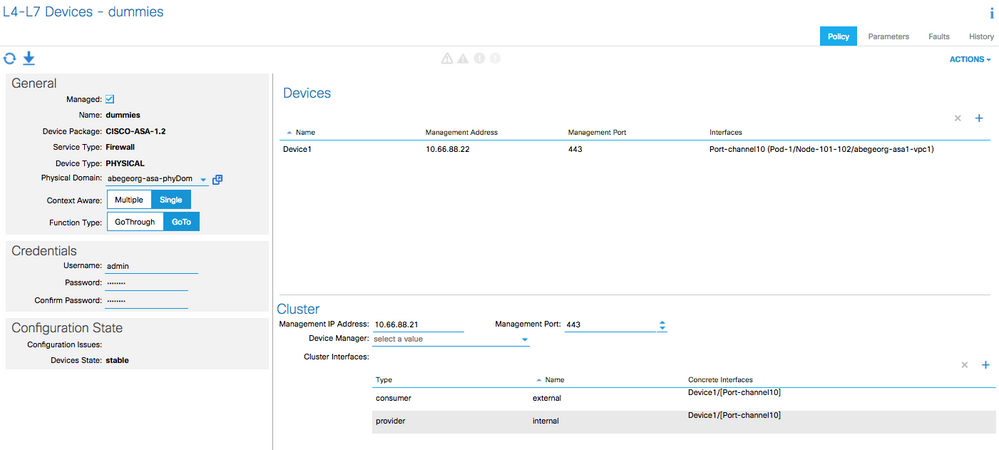
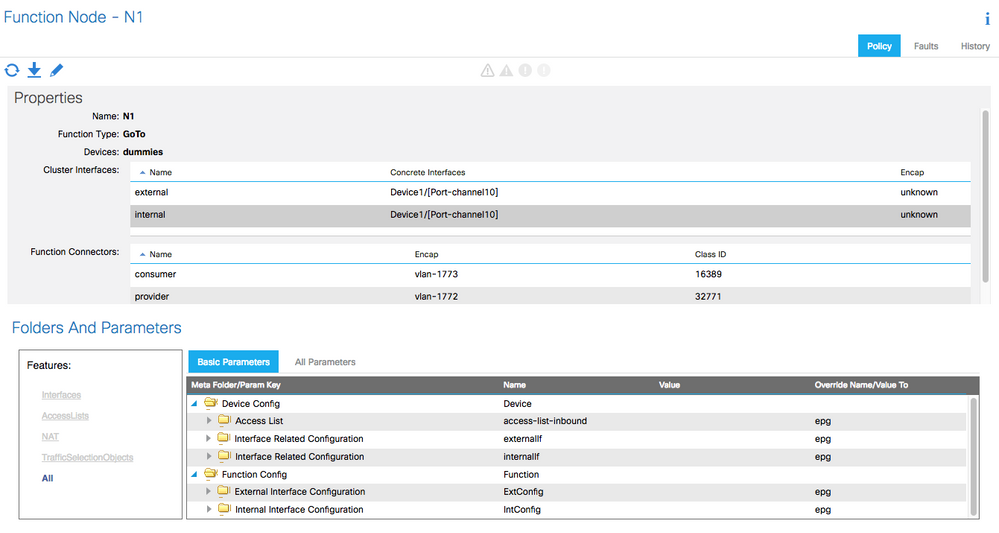
4. Create the L4-L7 device
The ASA device can be installed once and deploy it multiple times in different logical topologies. Each time the graph is deployed, ACI takes care of changing the configuration on the firewall to enable the forwarding in the new logical topology.
Note:
- The "Device" management IP address shall be the ASA user context management IP address
- The "Cluster" management IP address shall be the ASA admin context management IP address
5. Once the device is created, make sure that the device state is "Stable"
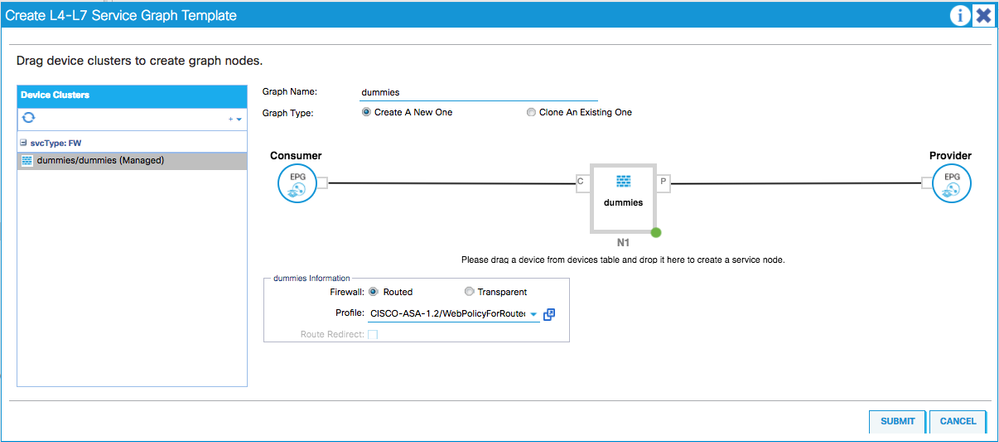
6. Create L4-L7 service graph template
- drag and drop the created devices to the template pane"
- Select the approproate "L4-L7 service function profile". In this exampled, we used "WebPolicyForRoutedModeIPv4"
- Select the Firewall mode "Routed"
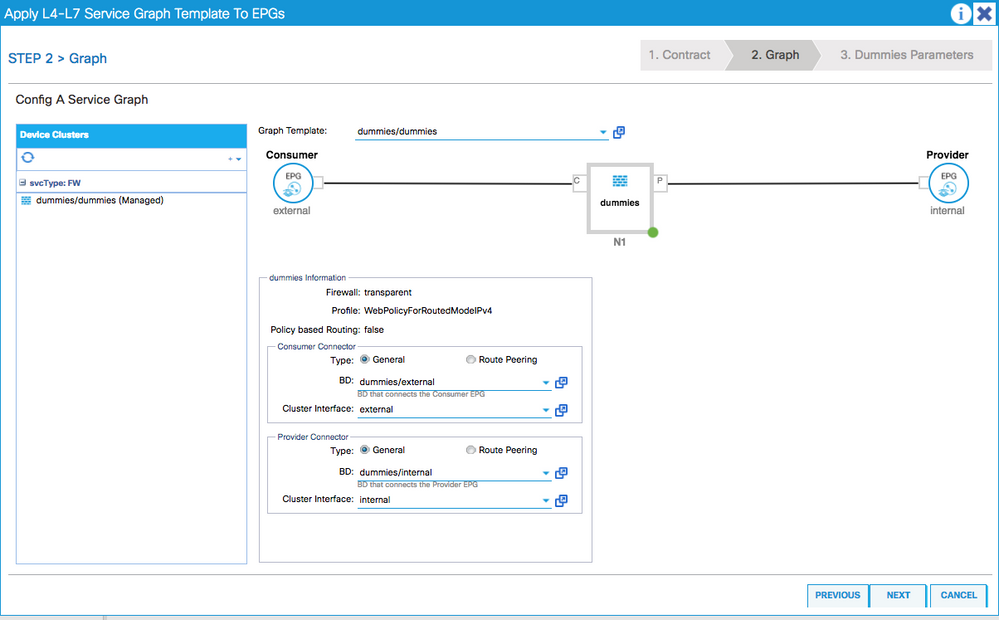
7. Apply the L4-L7 Service graph template
- Select the consumer and provider EPG appropriately.
- Create a new contract. In this example, we are not using any specific filter (allow-all)
- Select the appropriate the BD & cluster interfaces
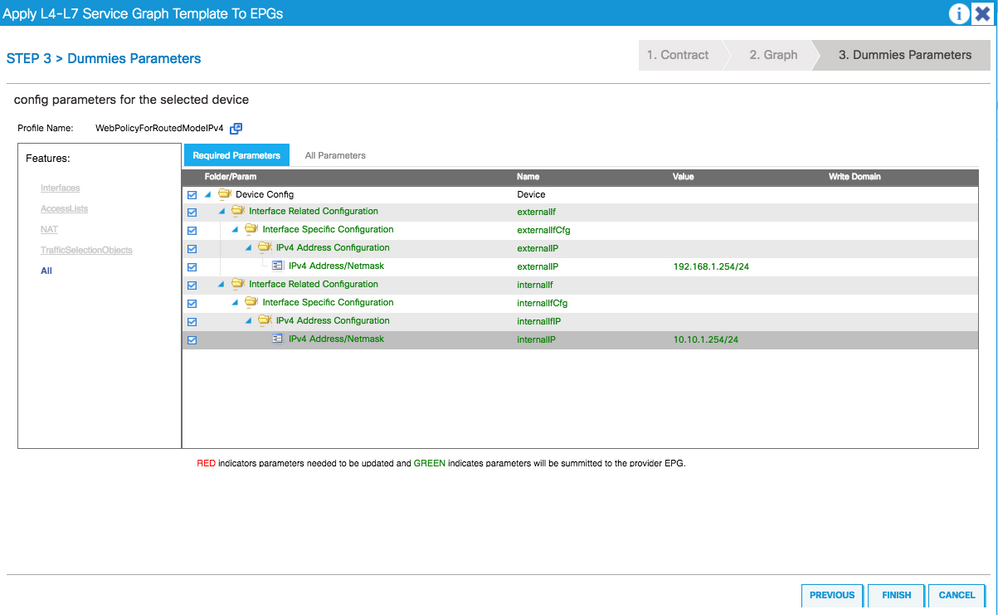
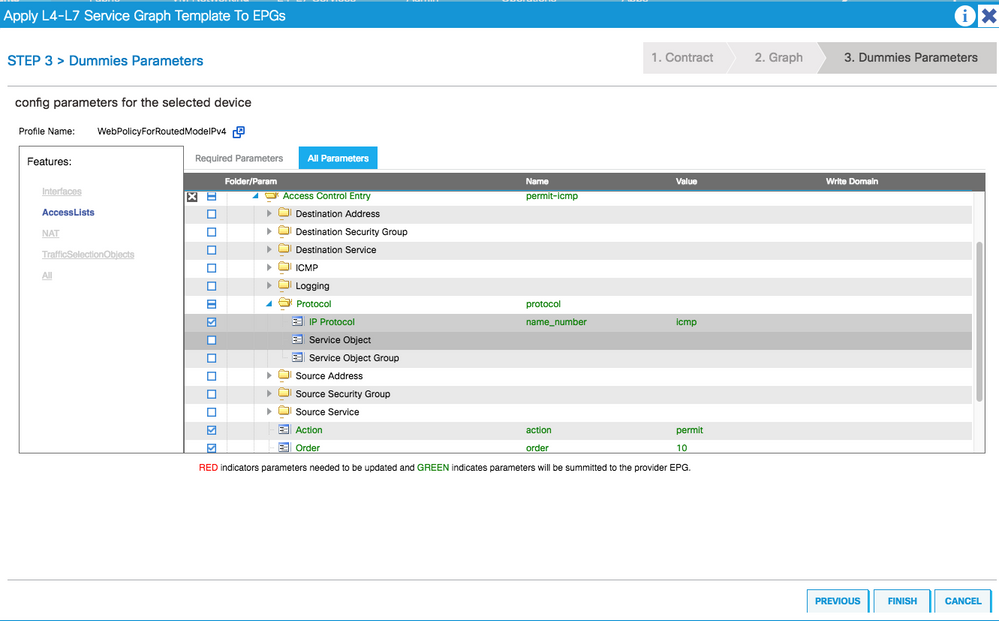
8. Configure the parameters
- Make sure that the internal & external interace IP address are configured, these will act as the default gateway for internal and external EPG(s) respectively
- Make sure that the access-lists are configured correctly. In this case, we are testing icmp
Verify
1. Ensure that the internal & external interfaces are created in the ASA user context with correct vlan sub-interface
ASAFab3/dummies# show interface summary
< snip >
Interface Port-channel10.1772 "externalIf", is up, line protocol is up
MAC address 84b2.6191.892b, MTU 1500
IP address 192.168.1.254, subnet mask 255.255.255.0
Interface Port-channel10.1773 "internalIf", is up, line protocol is up
MAC address 84b2.6191.892b, MTU 1500
IP address 10.10.1.254, subnet mask 255.255.255.0
ASAFab3/dummies#
2. Ensure that the access-list are pushed to the ASA user context
ASAFab3/dummies# show run access-list
access-list access-list-inbound extended permit tcp any any eq www
access-list access-list-inbound extended permit tcp any any eq https
access-list access-list-inbound extended permit icmp any any
ASAFab3/dummies# show run access-group
access-group access-list-inbound in interface externalIf
ASAFab3/dummies#
ASAFab3/dummies# show access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list access-list-inbound; 3 elements; name hash: 0xcb5bd6c7
access-list access-list-inbound line 1 extended permit tcp any any eq www (hitcnt=0) 0xc873a747
access-list access-list-inbound line 2 extended permit tcp any any eq https (hitcnt=0) 0x48bedbdd
access-list access-list-inbound line 3 extended permit icmp any any (hitcnt=0) 0xe4b5a75d
ASAFab3/dummies#
3. Ensure that ping from external endpoint to default GW works
fab2-pod4#
fab2-pod4# ping 192.168.1.254 vrf external
PING 192.168.1.254 (192.168.1.254): 56 data bytes
64 bytes from 192.168.1.254: icmp_seq=0 ttl=254 time=0.91 ms
64 bytes from 192.168.1.254: icmp_seq=1 ttl=254 time=0.641 ms
64 bytes from 192.168.1.254: icmp_seq=2 ttl=254 time=0.652 ms
64 bytes from 192.168.1.254: icmp_seq=3 ttl=254 time=0.666 ms
64 bytes from 192.168.1.254: icmp_seq=4 ttl=254 time=0.652 ms
--- 192.168.1.254 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 0.641/0.704/0.91 ms
fab2-pod4#
4. Ensure that ping from internal endpoint to default GW works
fab2-pod4# ping 10.10.1.254 vrf internal
PING 10.10.1.254 (10.10.1.254): 56 data bytes
64 bytes from 10.10.1.254: icmp_seq=0 ttl=254 time=1.021 ms
64 bytes from 10.10.1.254: icmp_seq=1 ttl=254 time=0.732 ms
64 bytes from 10.10.1.254: icmp_seq=2 ttl=254 time=0.727 ms
64 bytes from 10.10.1.254: icmp_seq=3 ttl=254 time=0.732 ms
64 bytes from 10.10.1.254: icmp_seq=4 ttl=254 time=0.732 ms
--- 10.10.1.254 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 0.727/0.788/1.021 ms
fab2-pod4#
5. Ensure that ping from external endpoint to internal endpoint works
fab2-pod4# ping 10.10.1.1 vrf external
PING 10.10.1.1 (10.10.1.1): 56 data bytes
64 bytes from 10.10.1.1: icmp_seq=0 ttl=254 time=1.309 ms
64 bytes from 10.10.1.1: icmp_seq=1 ttl=254 time=1.061 ms
64 bytes from 10.10.1.1: icmp_seq=2 ttl=254 time=1.079 ms
64 bytes from 10.10.1.1: icmp_seq=3 ttl=254 time=1.049 ms
64 bytes from 10.10.1.1: icmp_seq=4 ttl=254 time=1.064 ms
--- 10.10.1.1 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 1.049/1.112/1.309 ms
fab2-pod4#
Troubleshoot
Issue #1:
If you experience the fault "F0324: Cluster configuration resulted in *Major script error : Device parameter error for multi-context ASA : The context specified by cluster IP address 10.66.88.21 is not admin context. It must be admin context.* for dummies on cluster ctx-abegeorg in tenant dummies" during the L4-L4 device creation, click here to find the solution
Issue #2:
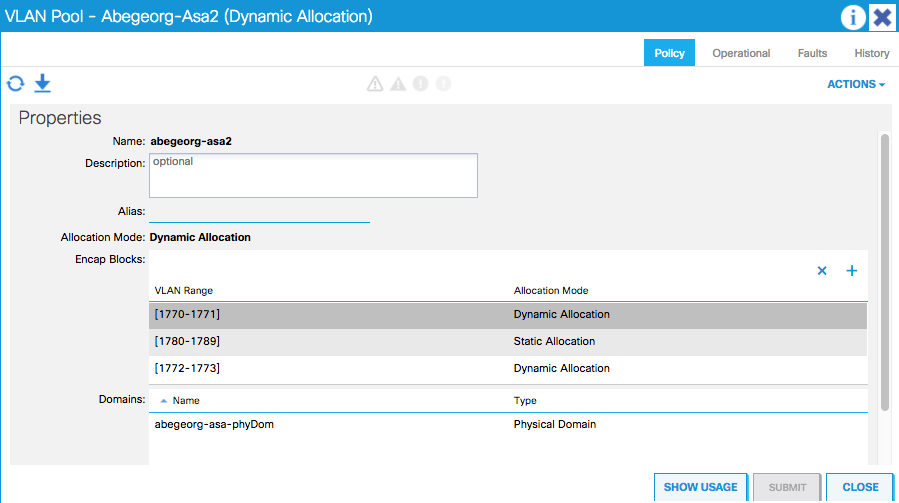
If you experience the issue of assigning VLAN(s) while applying the service graph template, review the following and validate..
The physical domains used for the BD shall contain a dynamic VLAN pool to allow the APIC to allocate for ASA device deployment. The APIC creates sub-interfaces based on a dynamically allocated VLAN from a pool, and in the system context it assigns port-channel sub-interfaces to appropriate user contexts.
>>> You can verify the vlan usage @ deployed service graph.
>>> verify the vlan deployed in leaf switch
leaf101# show vlan extended
< snip >
45 dummies:external active Eth1/35, Eth1/40, Po1, Po4
46 dummies:asa:external active Eth1/35, Po4
47 dummies:internal active Eth1/35, Eth1/40, Po1, Po4
48 dummies:asa:internal active Eth1/35, Po4
51 dummies:dummiesctxdummies:external: active Eth1/40, Po1
52 dummies:dummiesctxdummies:internal: active Eth1/40, Po1
< snip >
45 enet CE vxlan-16187321
46 enet CE vlan-1783
47 enet CE vxlan-16580490
48 enet CE vlan-1784
51 enet CE vlan-1773
52 enet CE vlan-1772
leaf101#
leaf101# show vlan id 51 extended
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
51 dummies:dummiesctxdummies:extern active Eth1/40, Po1
al:
VLAN Type Vlan-mode Encap
---- ----- ---------- -------------------------------
51 enet CE vlan-1773
leaf101# show vlan id 52 extended
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
52 dummies:dummiesctxdummies:intern active Eth1/40, Po1
al:
VLAN Type Vlan-mode Encap
---- ----- ---------- -------------------------------
52 enet CE vlan-1772
leaf101#
>>> verify endpoint learning / ASA defullt gateway.
leaf101# show system internal epm endpoint vrf dummies:dummies
MAC : dcce.c15b.1e44 ::: Num IPs : 0
Vlan id : 46 ::: Vlan vnid : 10495 ::: VRF name : dummies:dummies
BD vnid : 16187321 ::: VRF vnid : 2916354
Phy If : 0x16000003 ::: Tunnel If : 0
Interface : port-channel4
Flags : 0x80004825 ::: sclass : 16388 ::: Ref count : 4
EP Create Timestamp : 01/18/2018 11:58:39.419763
EP Update Timestamp : 01/18/2018 12:34:52.649405
EP Flags : local|vPC|peer-aged|MAC|sclass|timer|
::::
VRF : dummies:dummies ::: Context id : 34 ::: Vnid : 2916354
MAC : 84b2.6191.892b ::: Num IPs : 0
Vlan id : 51 ::: Vlan vnid : 10593 ::: VRF name : dummies:dummies
BD vnid : 16187321 ::: VRF vnid : 2916354
Phy If : 0x16000000 ::: Tunnel If : 0
Interface : port-channel1
Flags : 0x80004805 ::: sclass : 16389 ::: Ref count : 4
EP Create Timestamp : 01/18/2018 12:32:13.518710
EP Update Timestamp : 01/18/2018 12:34:52.648131
EP Flags : local|vPC|MAC|sclass|timer|
::::
MAC : dcce.c15b.1e44 ::: Num IPs : 0
Vlan id : 48 ::: Vlan vnid : 10496 ::: VRF name : dummies:dummies
BD vnid : 16580490 ::: VRF vnid : 2916354
Phy If : 0x16000003 ::: Tunnel If : 0
Interface : port-channel4
Flags : 0x80004825 ::: sclass : 32770 ::: Ref count : 4
EP Create Timestamp : 01/18/2018 11:59:12.819625
EP Update Timestamp : 01/18/2018 12:34:52.648245
EP Flags : local|vPC|peer-aged|MAC|sclass|timer|
::::
MAC : 84b2.6191.892b ::: Num IPs : 0
Vlan id : 52 ::: Vlan vnid : 10592 ::: VRF name : dummies:dummies
BD vnid : 16580490 ::: VRF vnid : 2916354
Phy If : 0x16000000 ::: Tunnel If : 0
Interface : port-channel1
Flags : 0x80004805 ::: sclass : 32771 ::: Ref count : 4
EP Create Timestamp : 01/18/2018 12:32:13.518588
EP Update Timestamp : 01/18/2018 12:34:52.649673
EP Flags : local|vPC|MAC|sclass|timer|
::::
>>> verify the zoning-rule
leaf101# show zoning-rule scope 2916354
Rule ID SrcEPG DstEPG FilterID operSt Scope Action Priority
======= ====== ====== ======== ====== ===== ====== ========
4322 0 16386 implicit enabled 2916354 permit any_dest_any(15)
4325 0 0 implicit enabled 2916354 deny,log any_any_any(20)
4326 0 0 implarp enabled 2916354 permit any_any_filter(16)
4330 0 15 implicit enabled 2916354 deny,log any_vrf_any_deny(21)
4331 0 16387 implicit enabled 2916354 permit any_dest_any(15)
4332 16388 16389 default enabled 2916354 permit src_dst_any(8)
4334 16389 16388 default enabled 2916354 permit src_dst_any(8)
4335 32770 32771 default enabled 2916354 permit src_dst_any(8)
4333 32771 32770 default enabled 2916354 permit src_dst_any(8)
leaf101#
Reference
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: