Summary:
CloudCenter treats user credentials and keys as sensitive information, storing and encrypting such data in the CloudCenter database as:
- Cloud authentication credentials
- VM authentication SSH key pair
- Storage authentication key pair
- REST API access key
- Storage encryption key
By default, CloudCenter generates a unique RSA-2048 PKI-based SSH key pair for each user per each cloud region to which that user is entitled and imports the resultant public key signature to the cloud provider. This occurs as part of the account initialization process. The key pair is used to provide browser-based secure VNC and SSH-based terminal access to VMs from the CloudCenter Manager UI. One example can be seen on the Amazon Web Service management console, where the Key Pair for the CloudCenter user is represented by one named cliqr-user-key_<user_id>. In certain scenarios, a user may want to obtain that private pair to interact directly with the VM. Though end users cannot download these keys directly, there is a way to gather that information through the API interface. The goal of this document is to demonstrate this process and the process to connect to the VM.
Viewing a user's private key information:
- As an administrative user (in this case the administrator is searching for another user's information)
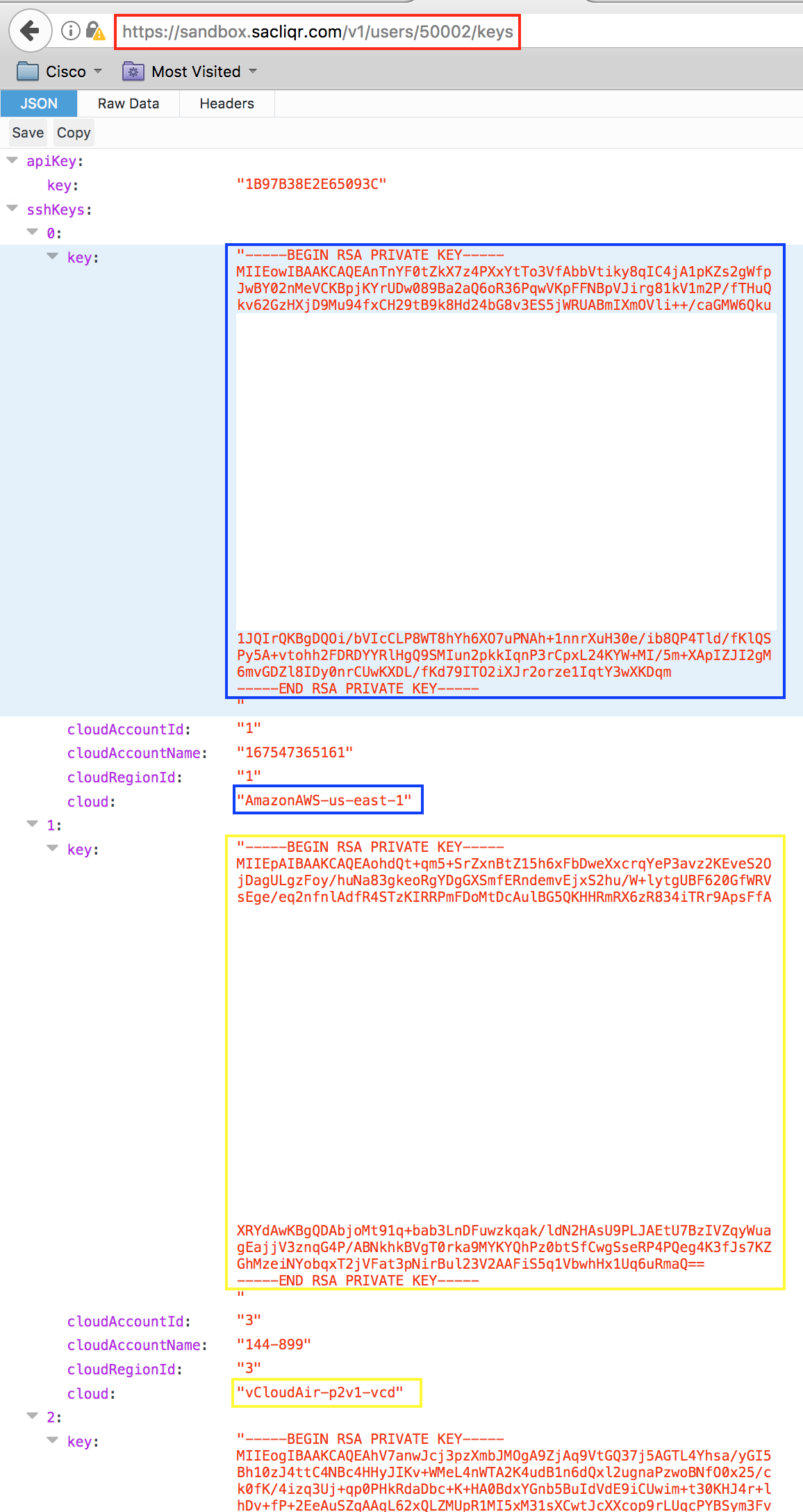
- In this example, the user with user_ID 50002 can deploy to multiple cloud targets and has corresponding private keys (color-coded)
- Select the desired target and copy the text between -----BEGIN RSA PRIVATE KEY----- and -----END RSA PRIVATE KEY----- and paste it into a file
- Save the file with a *.pem extension - this format is standard and will allow certificate based authentication to the VM (e.g. cliqr-user.pem)
- Optional - change the file permissions: chmod 600 cliqr-user.pem (assuming a Linux CLI)

- In this example, the authenticated user can deploy to multiple cloud targets and has corresponding private keys (color-coded)
- Select the desired target and copy the text between -----BEGIN RSA PRIVATE KEY----- and -----END RSA PRIVATE KEY----- and paste it into a file
- Save the file with a *.pem extension - this format is standard and will allow certificate based authentication to the VM (e.g. cliqr-user.pem)
- Optional - change the file permissions: chmod 600 cliqr-user.pem (assuming a Linux CLI)
- NOTE: For versions of CloudCenter that display this information in a simple text format, find the text corresponding to the desired cloud target wherein the application node will be deployed and similarly copy the text between ----BEGIN RSA PRIVATE KEY----- and -----END RSA PRIVATE KEY-----. To create the *.pem file, insert the text into a named file: echo -e -n "----BEGIN RSA PRIVATE KEY----- ... -----END RSA PRIVATE KEY-----" >> cliqr-user.pem (assuming a Linux CLI)
Connecting to the virtual machine:
- Assuming a Linux CLI, type:
- ssh -i <file_location>/<file_name>.pem cliqruser@<VM_IP_Address>
- (e.g. ssh -i /keys/cliqr-user.pem cliqruser@ec2-52-23-222-196.compute-1.amazonaws.com)