- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center and Cloud Knowledge Base
- Configure Firewall Load balancing on ACE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-27-2012 07:02 AM - edited 08-29-2017 05:34 AM
Introduction
Firewall Load Balancing (FWLB) is a technique that relies on loadbalancing devices, like ACE, to scale the use of firewalls. Firewall load balancing allows you to scale firewall protection by distributing traffic across multiple firewalls on a per-connection basis. The advantages of FWLB over common firewall clustering techniques are:
a) All the firewalls are simultaneously active.
b) It enables the use of heterogeneous firewalls.
Firewall Loadbalancing Overview
Basically there are two types of firewalls:
a) Routed Firewall: This is the standard firewall configuration in which you assign IP addresses to the firewalls, which allows other devices on the network to see and address them as devices.
b) Transparent Firewall: Also known stealth firewalls. These firewalls do not have IP address assigned to them which prevents other devices on the network from seeing or addressing them.
ACE can be configured to loadbalance traffic across firewall in same way as it does for servers in server farms. Since the firewalls are stateful in nature, the packets belonging to a given connection must always traverse the same firewall. This is usually achieved by some kind of coherence in the predictor algorithm. Cisco ACE, for example, performs a hashing that takes into account a combination of source and destination IP addresses. Using any other predictor with FWLB may fail and block traffic, especially for applications that have separate control and data channels, for example, FTP.
ACE can load balance traffic to both standard and stealth firewalls.
For routed firewalls, a single ACE or a pair of ACEs load balances traffic among firewalls that contain unique IP addresses in a manner similar to how the ACE load balances traffic among servers in a server farm. For transparent firewalls, an ACE load balances traffic among interfaces with unique alias IP addresses in different ACEs that provides paths through the firewalls. You configure a stealth firewall so that all traffic moving in both directions across a particular VLAN moves through the same firewall.
Network Diagram
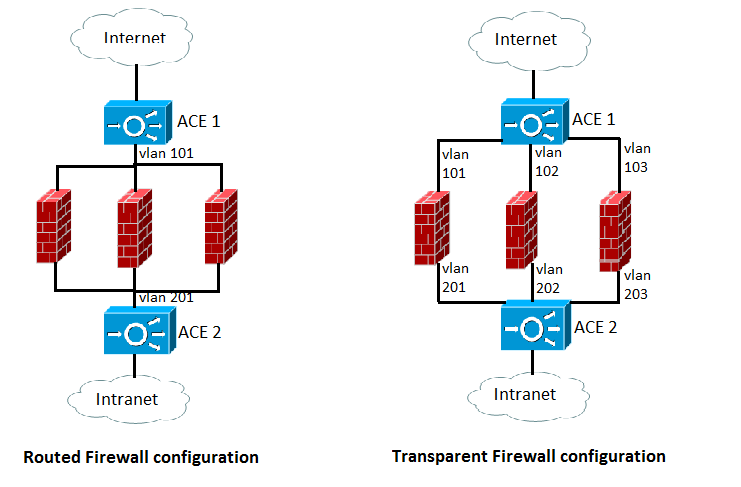
FWLB Configuration
Following is the configuration for Routed firewalls:
Configuration on ACE1:
access-list ACL1 line 10 extended permit ip any any
rserver host FW1
ip address 100.101.1.1
inservice
rserver host FW2
ip address 100.101.1.2
inservice
rserver host FW3
ip address 100.101.1.3
inservice
serverfarm INSEC_SF
transparent
predictor hash address source 255.255.255.255
rserver FW1
inservice
rserver FW2
inservice
rserver FW3
inservice
class-map match-any FW_VIP
10 match virtual-address 200.1.1.1 255.255.0.0 any
policy-map type loadbalance first-match LB_FW
class class-default
serverfarm INSEC_SF
policy-map multi-match POL_INSEC
class FW_VIP
loadbalance vip inservice
loadbalance policy LB_FW
interface vlan 100
ip addr 100.100.1.100 255.255.0.0
access-group input ACL1
service-policy input POL_INSEC
no shutdown
interface vlan 101
ip addr 100.101.1.101 255.255.0.0
access-group input ACL1
mac-sticky enable
service-policy input POL_INSEC
no shutdown
Configuration on ACE2:
access-list ACL1 line 10 extended permit ip any any
rserver FW1
ip address 100.201.1.1
inservice
rserver FW2
ip address 100.201.1.2
inservice
rserver FW3
ip address 100.201.1.3
inservice
rserver REAL1
ip address 20.1.1.1
inservice
rserver REAL2
ip address 20.1.1.2
inservice
rserver REAL3
ip address 20.1.1.3
inservice
serverfarm SEC_SF
predictor hash address destination 255.255.255.255
transparent
rserver FW1
inservice
rserver FW2
inservice
rserver FW3
inservice
serverfarm SEC_200_SF
rserver REAL1
inservice
rserver REAL2
inservice
rserver REAL3
inservice
class-map match-any SEC_200_VS
10 match virtual-address 200.1.1.1 255.255.0.0 any
class-map match any FW_VIP
10 match virtual-address 0.0.0.0 0.0.0.0 any
policy-map type loadbalance first-match SEC_200_LB
class class-default
serverfarm SEC_200_SF
policy-map multi-match POL_SEC_200
class SEC_200_VS
loadbalance vip inservice
loadbalance policy SEC_200_LB
policy-map type loadbalance first-match LB_FW_SEC
class class-default
serverfarm SEC_SF
policy-map multi-match POL_SEC
class FW_VIP
loadbalance vip inservice
loadbalance policy LB_FW_SEC
interface vlan 201
ip address 100.201.1.201 255.255.0.0
access-group input ACL1
mac-sticky enable
service-policy input POL_SEC_200
no shutdown
interface vlan 200
ip address 20.1.1.20 255.255.255.0
access-group input ACL1
service-policy input POL_SEC
no shutdown
Related Information
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Cisco has a new solution called ITD:
http://blogs.cisco.com/datacenter/itd-load-balancing-traffic-steering-clustering-using-nexus-5k6k7k
ITD (Intelligent Traffic Director) is a hardware based multi-Tbps Layer 4 load-balancing, traffic steering and clustering solution on Nexus 5K/6K/7K series of switches. It supports IP-stickiness, resiliency, NAT, (EFT), VIP, health monitoring, sophisticated failure handling policies, N+M redundancy, IPv4, IPv6, VRF, weighted load-balancing, bi-directional flow-coherency, and IPSLA probes including DNS. There is no service module or external appliance needed.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
