The Cisco Intersight Service for HashiCorp Terraform (IST) helps simplify application and infrastructure deployment and delivery. IST works with Terraform Cloud for Business to securely extend Terraform capabilities to on-premises infrastructure and software. With IST, the Intersight Assist Appliance manages Terraform Cloud Agents which avoids deployment and management of additional on-premises resources that would need connections to Terraform Cloud. Be sure to check out the video overview of using the Intersight Terraform Service.
IST allows use of any Terraform Providers from Terraform Cloud and works seamlessly with Intersight's Terraform Provider. Configuration of IST is also simple with Terraform Cloud user API tokens used for secure connections and management through Terraform Cloud. Below is an overview of configuration needed to start using the Intersight Service for Terraform and Terraform Cloud for Business:
- From Terraform Cloud for Business, create a User API token by going to Settings->Tokens->Create User API token
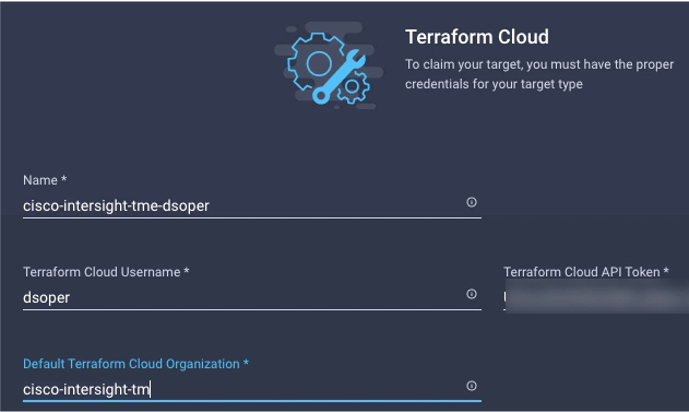
- Use the Terraform Token to claim Terraform Cloud targets in the Intersight UI by going to Admin->Targets and selection Claim Target. You can search for "Terraform" and select the Terraform Cloud target type. When claiming a Terraform target, you will need to provide a Terraform username, user API token, and default Terraform Organization
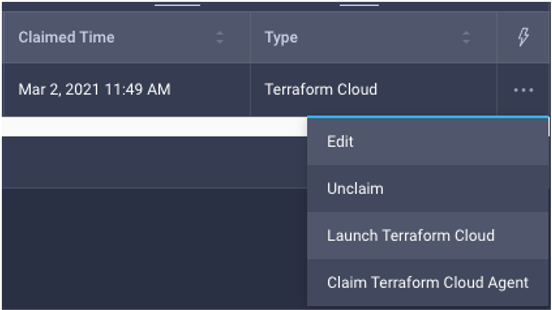
- With IST, Intersight Assist manages Terraform Agents. There is no need to configure and maintain agents on local hosts. Intersight users will “claim” a Terraform Agent in Intersight and specify the Assist Appliance that agents will run on. To claim a Terraform Agent from Intersight's UI, go to Admin->Targets and find your Terraform Cloud Target. From the ... Actions column (right side of the table), select Claim Terraform Cloud Agent
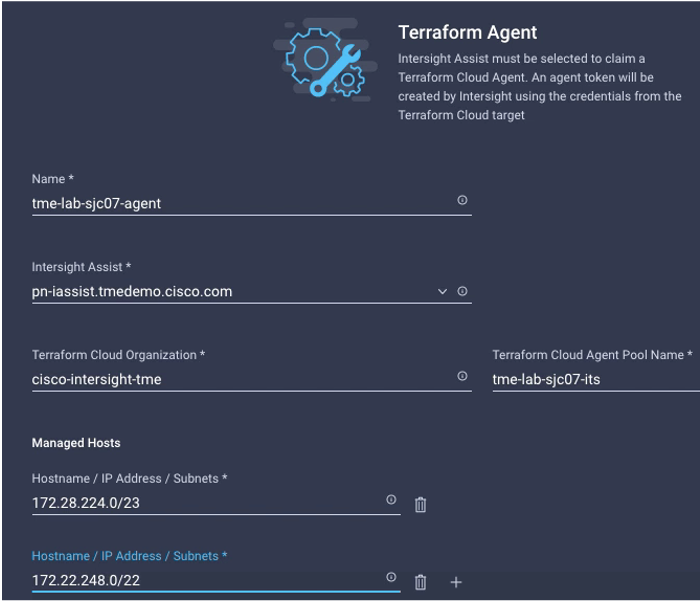
- When claiming an Agent, the user will need to provide Intersight Assist and Terraform Cloud Organization/Agent pool information. The Name provided by the user will be used for Agent naming in Terraform. Managed Hosts information is used to specify on-premises hosts/IPs or CIDR notation IP ranges
- Once targets are claimed in Intersight, Terraform Cloud Workspaces can be configured to run plans against on-premises resources. To launch Terraform from Intersight, go to Admin->Targets and find your Terraform Cloud Target. From the ... Actions column (right side of the table), select Launch Terraform Cloud
You can now use Terraform Cloud and Intersight Assist Terraform Agents will automatically pull data from from Terraform Cloud to manage resources.
Below is an overview of configuring Terraform Cloud with Version Control Systems and Agent based execution.
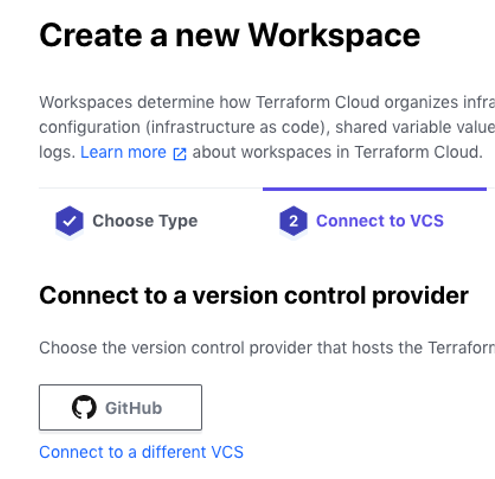
- In Terraform Cloud, you can create/manage workspaces which connect to version control providers such as GitHub. When you create a new workspace, Terraform will display options to configure version control connections
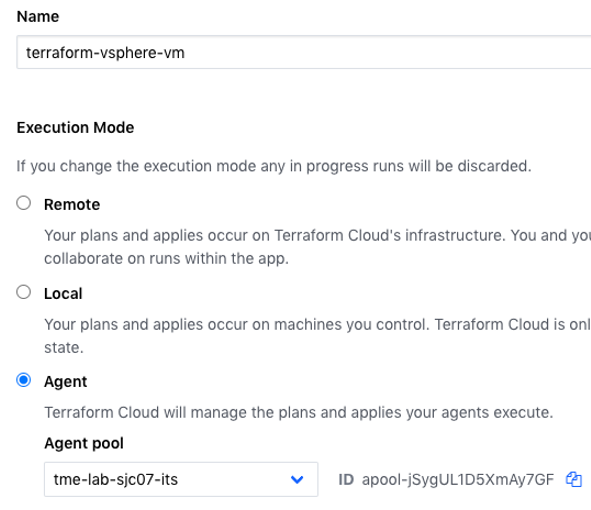
- To configure Agent based execution mode for managing on-premises resources, go to Workspaces->Settings->General in Terraform Cloud
- Terraform Cloud automatically updates workspaces when there are changes in GitHub. Pull Request (PR) runs in Terraform result in plans, but those plans can’t be applied (a merge of the PR is needed 1st)
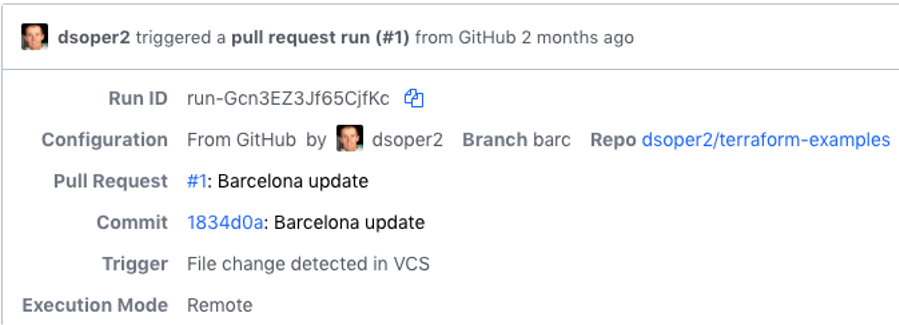
Merged PRs and direct commits in GitHub result in plans with the ability to apply changes from Terraform.
You can visit https://intersight.com/help for more information on configuring and using the Intersight Service for Terraform.