- Cisco Community
- Comunidad de Cisco
- Seguridad
- Discusiones Seguridad
- ICMP Inspect Bypass
- Suscribirse a un feed RSS
- Marcar tema como nuevo
- Marcar tema como leído
- Flotar este Tema para el usuario actual
- Favorito
- Suscribir
- Silenciar
- Página de impresión sencilla
ICMP Inspect Bypass
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 04-04-2023 04:54 PM
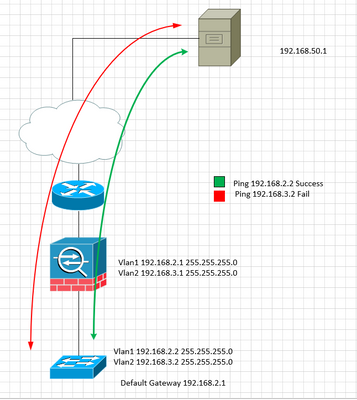
Tengo un switch que esta monitoreado via ping e snmp. Sobre la vlan 1 y recientemente configure una vlan 2 nueva para monitorear.
Al validar localmente alcanzo las dos ip pero no reemplace el default-gateway en el switch sigue estando sobre la vlan 1 el switch esta en capa 2. al momento de validar en el asa observo que la conexion se establece, sin embargo cuando el switch contesta con la ip nueva se regresa por la vlan1. el asa no ve una conexion por esta interface y tira el paquete. Necesito saber una forma de realizar un bypass de icmp para que me pueda contestar el switch con la ip nueva. Sin deshabilitar el inspect icmp.
Saludos.
anexo error
----------------------------------
ICMP packets were dropped by the ASA because of security checks added by the stateful ICMP feature that are usually either ICMP echo replies without a valid echo request already passed across the ASA or ICMP error messages not related to any TCP, UDP, or ICMP session already established in the ASA.
An ICMP session is removed in the fast-path when stateful ICMP is enabled using the inspect icmp command.
-----------------------------------------------------------------
- Etiquetas:
-
Firewalls
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 04-04-2023 05:12 PM
Hello
Question, it is required to keep vlan 1 on the switch? Why dont you keep only vlan 2 ?
Do you have ICMP inspection on the ASA?
TEST-ASA(config)# policy-map global_policy
TEST-ASA(config-pmap)# class inspection_default
TEST-ASA(config-pmap-c)# inspect icmp
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 04-04-2023 05:21 PM
Question, it is required to keep vlan 1 on the switch? Why dont you keep only vlan 2 ?
Because, before change on monitoring tool, I need rechable the new ip. We are talking about 500 switch.
Yes, I have inspection active on global policy.
Regards.
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 04-04-2023 05:56 PM
There is way to bypass icmp inspection but I need to check it first'
The way is using specific acl for inspection not use global defualt one.
- Marcar como nuevo
- Favorito
- Suscribir
- Silenciar
- Suscribirse a un feed RSS
- Resaltar
- Imprimir
- Informe de contenido inapropiado
el 04-05-2023 10:52 AM
I applied
------------------------
access-list passInside extended permit tcp host 192.168.50.1 host 192.168.3.1
access-list passInside extended permit icmp host 192.168.50.1 host 192.168.3.1
!
class-map passTCP
match access-list passInside
!
policy-map passInsTrue
class passTCP
set connection advanced-options tcp-state-bypass
!
service-policy passInsTrue interface Inside
access-list passVlan1 extended permit tcp host 192.168.3.1 host 192.168.50.1
access-list passVlan1 extended permit icmp host 192.168.3.1 host 192.168.50.1
!
class-map passTCPV1
match access-list passVlan1
!
policy-map passV1True
class passTCPV1
set connection advanced-options tcp-state-bypass
service-policy passV1True interface vlan1
------------------------------------------------------
Currently I can already open telnet or ssh to the swtich. however the ping command does not respond to me.
if I disable the inspect if I reach it. but for best practices it is recommended not to disable it
Regards.
Descubra y salve sus notas favoritas. Vuelva a encontrar las respuestas de los expertos, guías paso a paso, temas recientes y mucho más.
¿Es nuevo por aquí? Empiece con estos tips. Cómo usar la comunidad Guía para nuevos miembros
Navegue y encuentre contenido personalizado de la comunidad