- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- D285: Duo Release Notes for Mar 1, 2024
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
03-01-2024
08:56 AM
- edited on
03-08-2024
10:09 AM
by
DuoKristina
![]()
- New features, enhancements, and other improvements
- Changes in security key enrollment behavior
- Now in public preview: Automatic authentication device selection setting
- Now in public preview: Authentication device filtering
- Update to the Universal Prompt Progress report
- Update to Risk-Based Authentication reporting in the Duo Authentication Log
- Custom session timeout for Duo SSO for NetDocuments
- New and updated applications
- Two new named SAML applications with Duo SSO
- Duo Authentication for Windows Logon and RDP version 4.3.0 released
- Duo Desktop macOS Public Beta version 6.4.1.0 released
- Duo Desktop Windows Public Beta version 6.4.1 released
- Duo Mobile for Android version 4.59.0 released
- Duo Mobile for iOS version 4.59.0 released
- Bug fixes
Hello everyone! Here are the release notes for our most recent updates to Duo.
Public release notes are published on the Customer Community every other Friday, the day after the D-release is completely rolled out. You can subscribe to notifications for new release notes by following the process described here. If you have any questions about these changes, please comment below.
Check out the Guide to Duo End-of-Life and End-of-Support Plans. This guide provides an up-to-date list of current and past end-of-life plans for Duo products. We expect to reach these milestones by the end of next month:
- Effective March 30, 2024, Duo will no longer support the Duo LDAP cloud service (LDAPS) used to provide two-factor authentication for Cisco ASA, Juniper Networks Secure Access, or Pulse Secure Connect Secure SSL VPN logins.
- Effective March 30, 2024, Duo will no longer support the traditional Duo Prompt. Duo for NetScaler applications are an exception and the EOL date for existing Duo for NetScaler applications has been extended to September 30, 2024.
New features, enhancements, and other improvements
Changes in security key enrollment behavior
- When a user registers a security key, through either the self-service or the device management portal, or an admin registers a security key through the Duo Admin Panel, they may now see a browser-specific dialogue screen asking them to share the security key's make and model with Duo.
- The user or admin needs to accept this dialogue before they can proceed with registration.
- This action does not share any personal information with Duo.
Now in public preview: Automatic authentication device selection setting
- The Duo Universal Prompt has built-in automatic authentication method selection behavior that makes it easier for users to access their protected applications by automatically choosing the most-secure factor.
- If automatic selection interferes with a user's authentication experience, Administrators can turn it off for an individual user through the Users section of the Duo Admin Panel or through the Admin API.
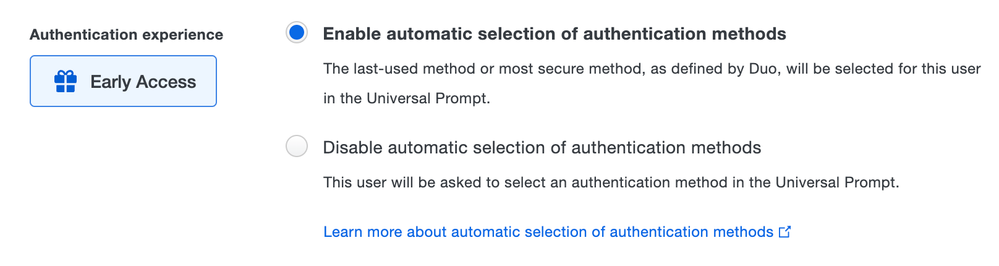 The authentication experience setting offers options to enable or disable automatic selection of authentication methods.
The authentication experience setting offers options to enable or disable automatic selection of authentication methods.
Now in public preview: Authentication device filtering
- If a user has 7 or more authentication methods available through the Universal Prompt, a new dropdown menu will allow the user to filter by authentication methods available for each specific device.
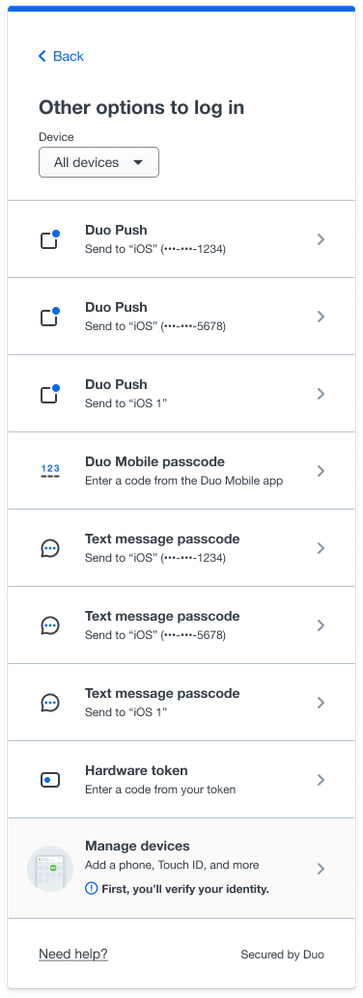
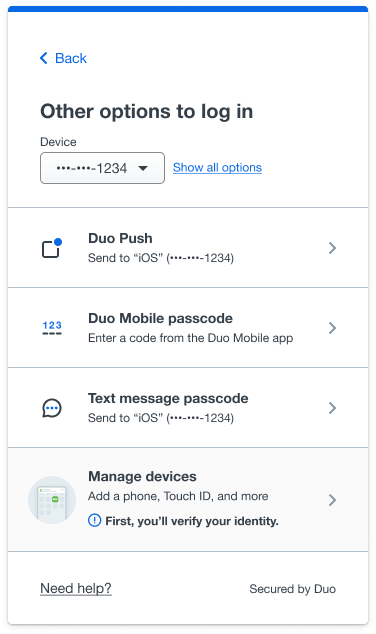 View filtered by device.
View filtered by device.
Update to the Universal Prompt Progress report
- To help Duo Administrators more easily identify which applications need to migrate from the traditional Duo Prompt to the Universal Prompt, the Universal Prompt Progress report in the Admin Panel now has clearer, consolidated tabs.
- Action required contains all applications that may be using the Traditional Prompt
- No action required contains applications already upgraded to the Universal Prompt and unaffected applications.
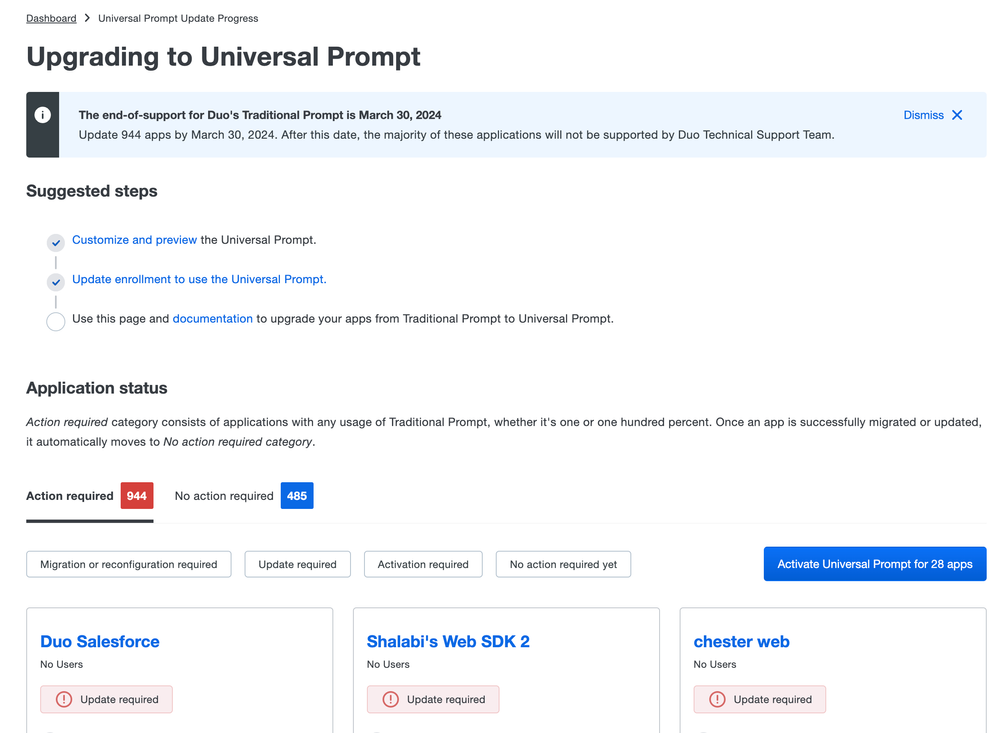 The Universal Prompt Progress report now shows Action required and No action required tabs.
The Universal Prompt Progress report now shows Action required and No action required tabs.
Update to Risk-Based Authentication reporting in the Duo Authentication Log
- The “Risk-Based Policy Assessment” column in the Authentication Log in the Admin Panel now shows Authentication stepped-up instead of User stepped-up when the user is in a stepped-up state due to a previous authentication.
- Entries in the Authentication Log with a detection from Risk-Based Factor Selection are now tagged with a clickable icon in the “Risk-Based Policy Assessment” column that displays a detection sequence.
- The detection sequence helps string together a list of authentication logs from the point where the user is initially stepped-up until they are out of step-up status.
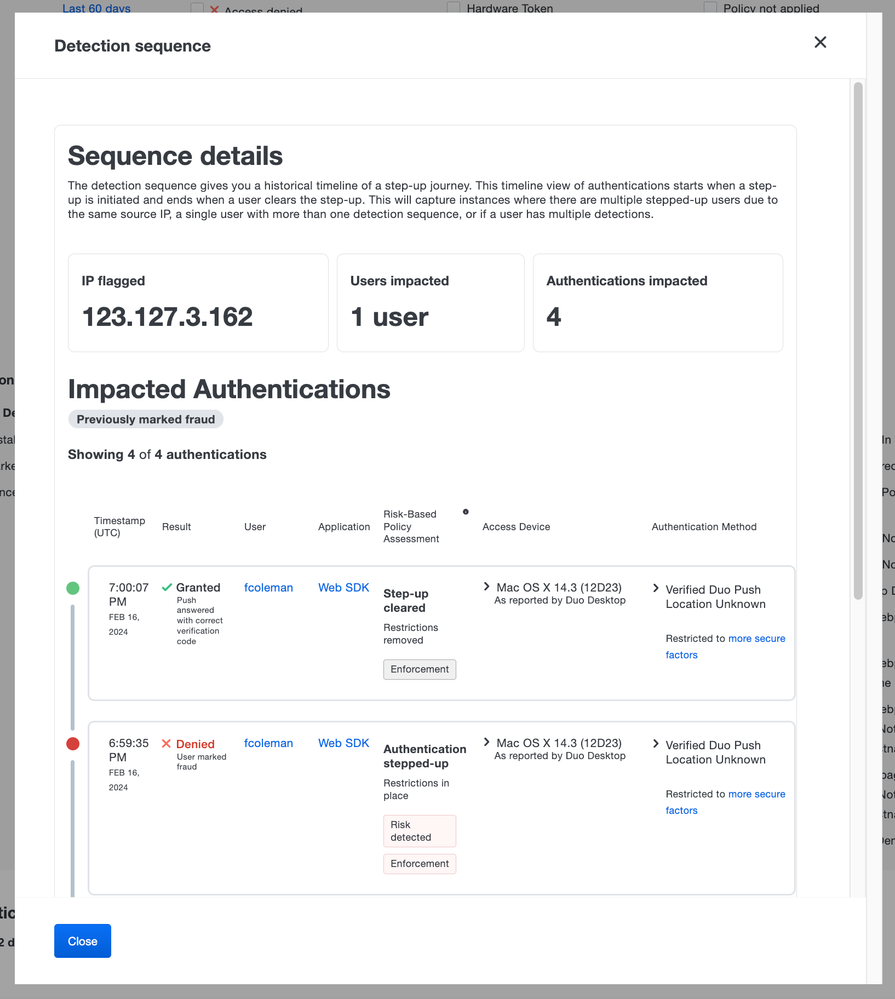 Sequence details showing impacted authentications.
Sequence details showing impacted authentications.Custom session timeout for Duo SSO for NetDocuments
- Duo SSO for NetDocuments now allows Duo admins to configure the length of sessiontimeout used in the SAML token generated by Duo.
New and updated applications
Two new named SAML applications with Duo SSO
- There are now named SAML applications to protect Amazon WorkSpaces and Palo Alto Prisma with Duo Single Sign-On (SSO), our cloud identity provider.
- Reminder: Duo Access Gateway reached the last date of support on October 26, 2023. Please see the Guide to Duo Access Gateway end of life for more details.
Duo Authentication for Windows Logon and RDP version 4.3.0 released
- Accessibility improvements.
- Design improvements and minor bug fixes in installer.
- Corrects an issue which caused occasional black or frozen screens during Duo login.
- Adds an optional registry setting ParseUsernameAndDomain which overrides Duo user/domain determination logic by parsing the username provided by the user. Refer to Why might an incorrect username get sent to Duo from a machine joined to Entra ID? for more information.
- Addresses a security vulnerability in which trusted sessions persisted after a reboot (CVE-2024-20301; Cisco Security Advisory).
- Addresses a security vulnerability where the Duo secret key value was logged in plain-text during an application upgrade (CVE-2024-20292; Cisco Security Advisory).
- We recommend you migrate to a new instance of the application to preserve the integrity of the application credentials on your client systems. Refer to Duo KB Article 8760 for step-by-step instructions and to Duo KB article What are Duo application credentials and how should I protect them? for more information.
- We recommend you migrate to a new instance of the application to preserve the integrity of the application credentials on your client systems. Refer to Duo KB Article 8760 for step-by-step instructions and to Duo KB article What are Duo application credentials and how should I protect them? for more information.
- Corrects an issue where the installer did not secure the Duo registry key so integration credentials could be read by unprivileged users until the registry key was secured by first launch of the application.
Duo Desktop macOS Public Beta version 6.4.1.0 released
- Added collection of information related to the expiration of certificates.
Duo Desktop Windows Public Beta version 6.4.1 released
- Session Logouts are now reported when the application is closed.
- Added collection of information related to registration and health reporting performance.
Duo Mobile for Android version 4.59.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
Duo Mobile for iOS version 4.59.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
Bug fixes
- Universal Prompt Progress report now lists the Duo Admin Panel - Single Sign-On application under the No action required tab of the Universal Prompt Progress report instead of the Action required tab because it doesn't require intervention.
- An error with message "Invalid Authentication Proxy" no longer occurs in the Authentication Proxy Dashboard in the Admin Panel if an Authentication Proxy was enrolled in and then later removed from SSO.
- The following text has changed in the Administrator Activity report in the Admin Panel:
- “Resend all enroll codes” is now “Resent all enrollment links”
- “Send an enroll code” is now “Sent an enrollment link”
- "Deleted an enroll code" is now “Deleted an enrollment link”
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Updated 3/1/24 to remove mentions of Duo Access Gateway (DAG) reaching end of life on March 30, 2024. We have canceled this end-of-life milestone. When we changed the traditional Duo Prompt end of life to an end-of-support milestone, we also decided to continuing letting the DAG work after March 30. The DAG did reach end of support in October 2023.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Updated 3/7/24 with additional details regarding security fixes in the Duo Authentication for Windows Logon and RDP 4.3.0 release.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Updated the details for Duo for Windows Authentication and RDP details regarding CVE-2024-20292 to link to a Duo Knowledge Base article for instructions.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: